Legends Never Die: RaidForums Legacy Continues Despite Seizure
About RaidForums
In March 2015, a discussion forum known as RaidForums emerged on the deep web. The forum quickly gained popularity amassing hundreds of thousands of users and became a reliable resource for breached and leaked databases in addition to combolists, cracked software, and adult content. The forum’s popularity crossed various underground communities with young script kiddies, prominent darknet threat actors, and seasoned data brokers all active and aiding in the forum’s success.
The forum is recognizable by a lavender-haired female as the default avatar for members and anime persona featured on the banner of the forum.

The forum also features a real-time ‘shoutbox’, private direct messages between users, and a credit system for accessing cloud-based hosting URLs of high-valued data leaks.
RaidForums’ administrator, using moniker “Omnipotent,” has been a key figure in the forum since its inception. While Omnipotent states the United Kingdom as their location on his Github profile, their exact location is unknown. There is a possible open-source connection between Omnipotent and the real identity, “K Gopal Krishna,” but nothing concrete to solidify an association.
Unusual Activity Begins on RaidForums
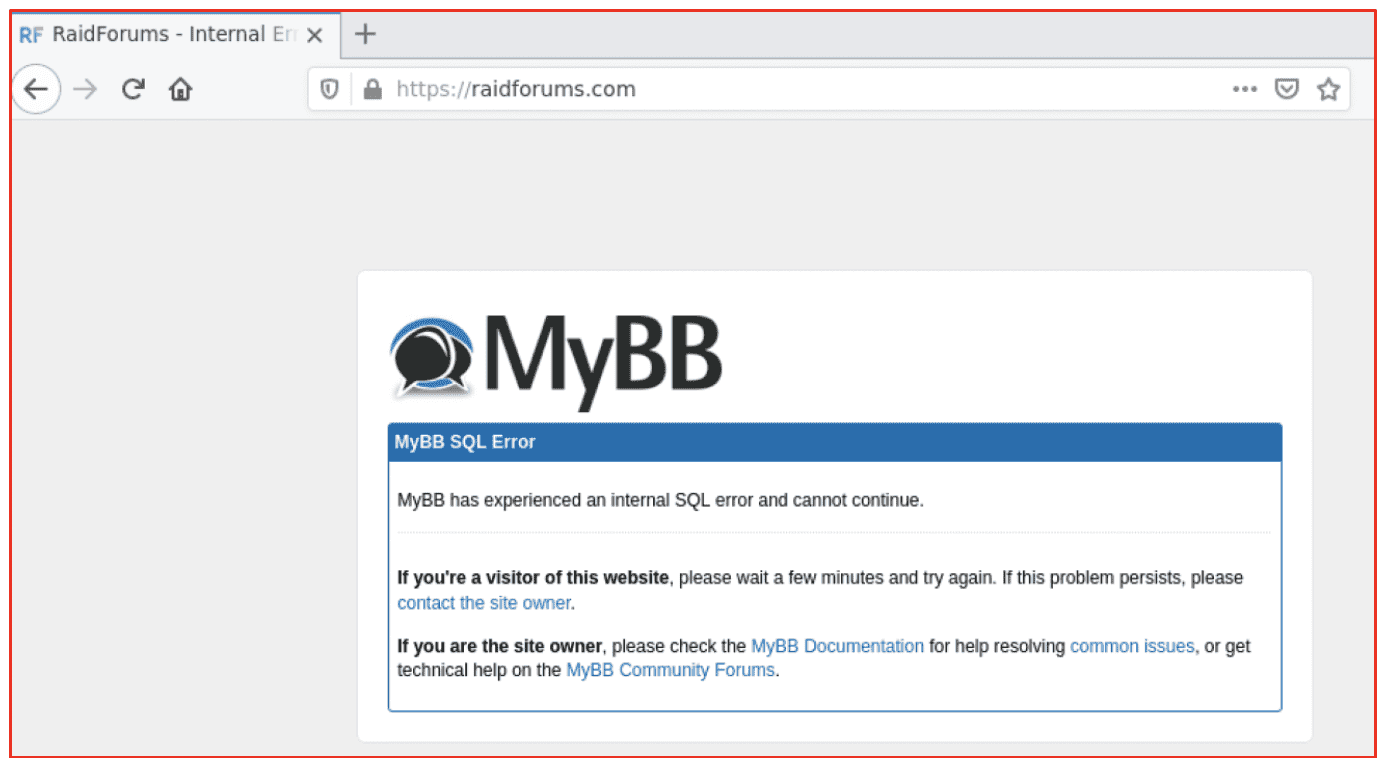
In late January and early February of this year, the forum mysteriously began experiencing connection issues and some users received an SQL internal error for the MyBB forum platform and couldn’t login. This all coincidentally occurred when Omnipotent was allegedly away for vacation (January 31st through February 7th).
On the forum’s Telegram chat, one user suggested Omnipotent “was on life support after fighting a mountain lion.” The comment sparked tremendous speculation and suspicion on the security of the forum and the whereabouts of its leadership.

According to DarkOwl Vision, less than three days later, the domain was back online and operational on February 11th, 2022.
Observation from our Analysts: Outages like those experienced in early-February was unusual, but not concerning. The website had experienced domain issues in the fall of 2021, when the Brazilian government attempted to have NameSilo – the domain’s registrar – shutdown the forum. This forced Omnipotent to setup mirror domains, like rfmirror[.]com while they migrated their services back to CloudFlare.
Key Data Leaks During RaidForums’ Short UpTime
During the weeks leading up to the invasion in Ukraine, various threat actors shared sensitive information pertaining to the Ukrainian cyberattacks from January and February. DarkOwl published an extensive analysis of Ukrainian data leaked leading up the to invasion. Several RaidForum users, like Carzita also claimed to be actively targeting Ukrainian government websites prompting alerts from the Ukrainian government. (Source: DarkOwl Vision)
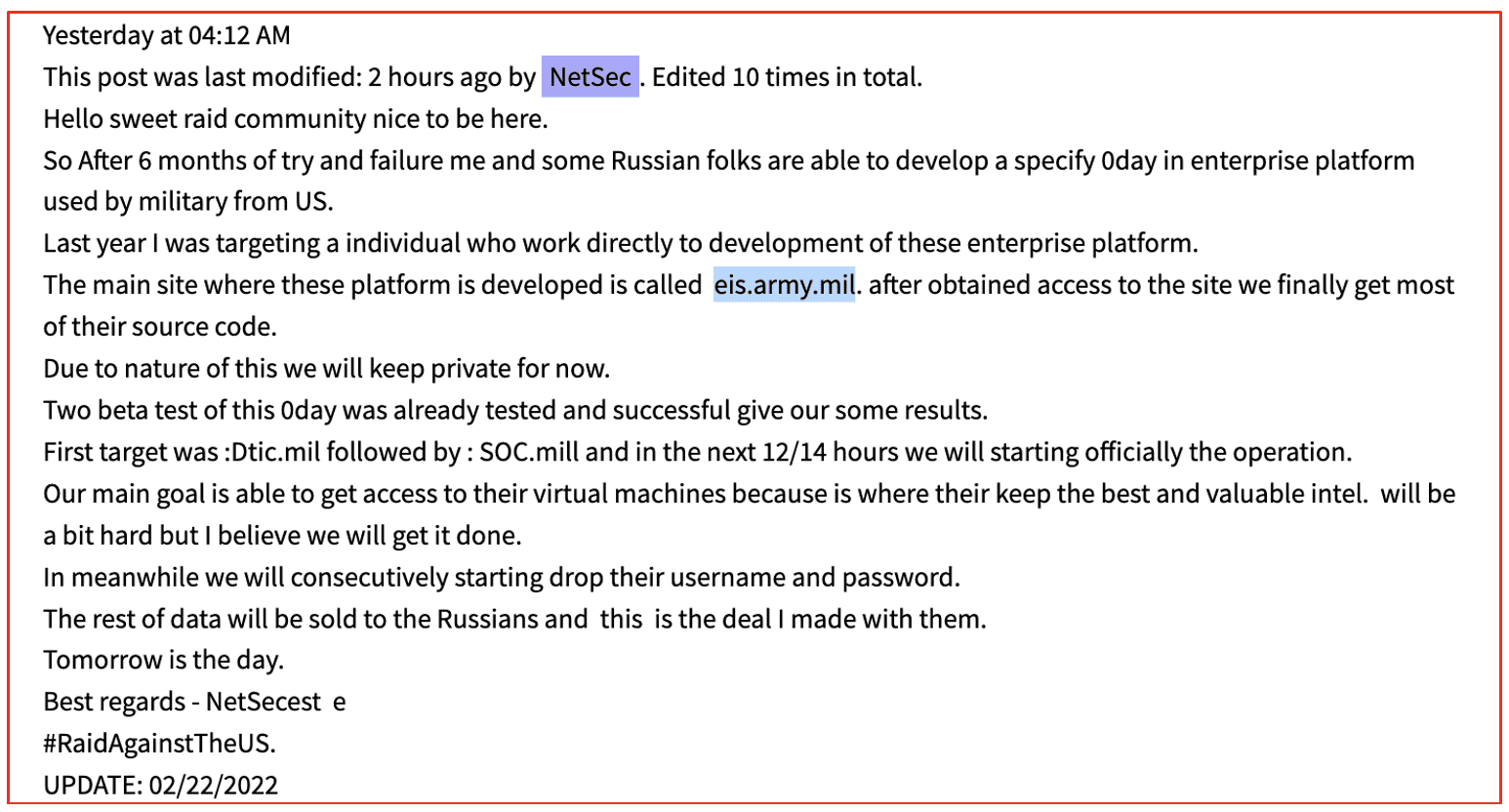
Some threat actors, like the alias NetSec, claimed to be targeting the US government and military networks using Anonymous-style hashes such as #RaidAgainstTheUS. In the days leading up to the invasion of Ukraine, NetSec shared email addresses and hashed passwords for the U.S. Strategic Command (stratcom[.]mil), U.S. Special Operations Command (soc[.]mil), the Defense Technical Information Center for the US Government (dtic[.]mil) and Lockheed Martin defense contractor employees.
On February 22nd, 2022, NetSec claimed to be working with “some Russian folks” to develop a zero-day for enterprise platforms used by the US Government by targeting an individual who worked directly for the enterprise platform. The threat actor refers to eis.army.mil – which resolves to the Program Executive Office (PEO) Enterprise Information Systems (EIS) for the Army.
NetSec is a self-proclaimed cybersecurity hacktivist reportedly in Switzerland with possible US citizenship, but not directly working with a government or for a company. They refer to being the “devil in the red hat” and feature women in their avatars in social media and forums, often in swimming suits or a big red hat.
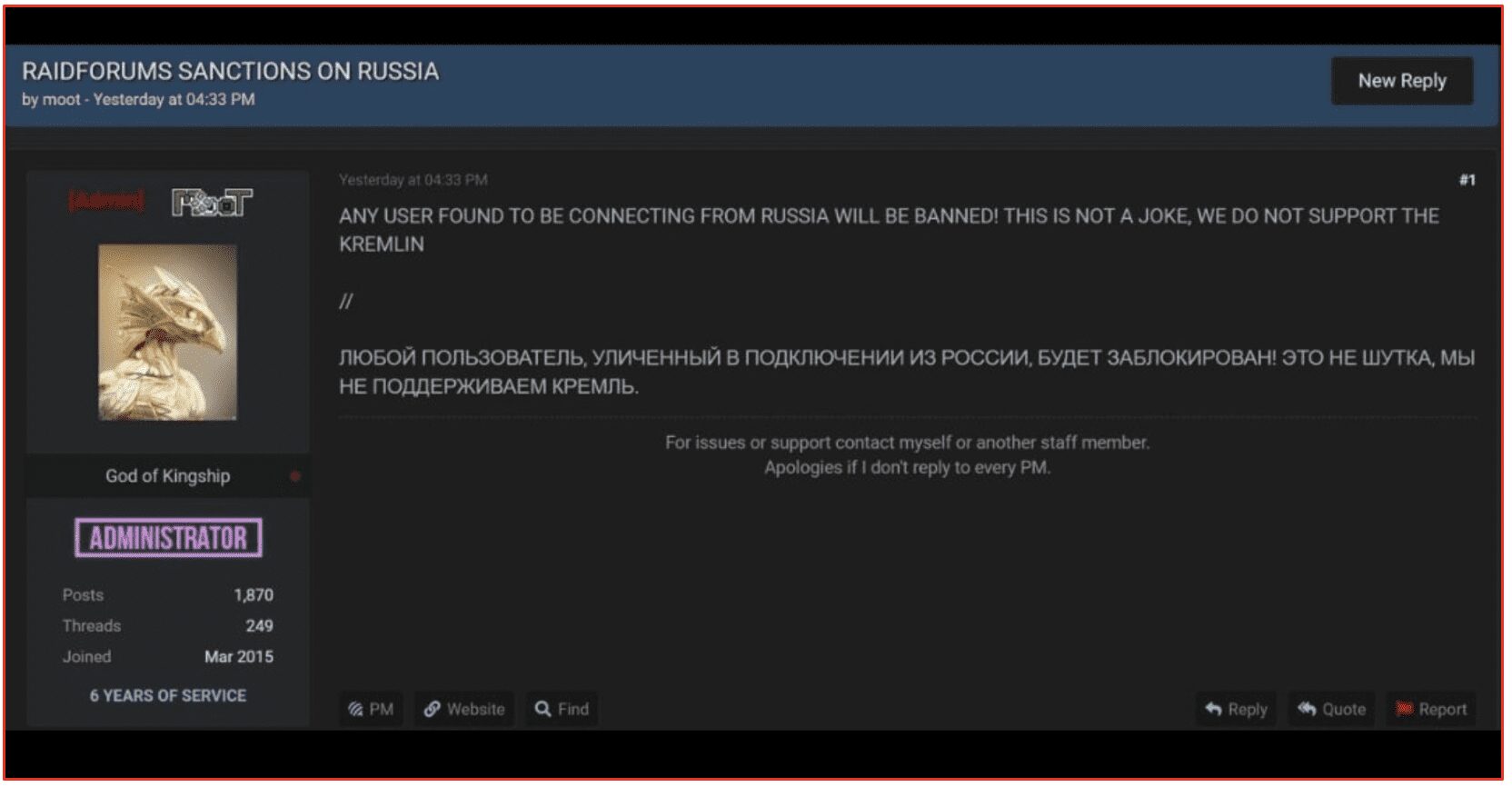
On the evening of the invasion, RaidForums leadership projected a zero-tolerance approach to Russian actors on the forum. Moot, another staff administrator of RaidForums posted in a thread titled, “RAIDFORUMS SANCTIONS ON RUSSIA,” stating that anyone connecting to the forum from a Russian IP address would be banned.
Seizure Unofficially Announced
On the 25th of February, users were no longer able to successfully log into the RaidForums domain. On the same day, a prominent moderator from the forum, Jaw posted to the forum’s Telegram that the raidforums.com domain had been seized and the current website domain was run by law enforcement as a honeypot and phishing operation.
Another RaidForums moderator, moot, locked the chat and Jaw suggested rf[.]to would be the new domain for future RaidForums operations. It’s unclear how Jaw confirmed the seizure of the RaidForums domain. Some speculate Omnipotent was allowed to call from inside police custody and notified Jaw directly. The rf[.]to domain is unresolvable and according to WHOIS records was setup around the same time as rfmirror[.]com.
![Chat where RaidForums moderator, moot, locked the chat and Jaw suggested rf[.]to would be the new domain for future RaidForums operations.](https://www.darkowl.com/wp-content/uploads/2022/04/Screen-Shot-2022-04-04-at-4.41.02-PM.jpg)
Databreaches.net was unable to get confirmation from British or US law enforcement whether the RaidForums domain was seized. The FBI’s outright, “decline to comment” indirectly confirmed the community’s suspicions.
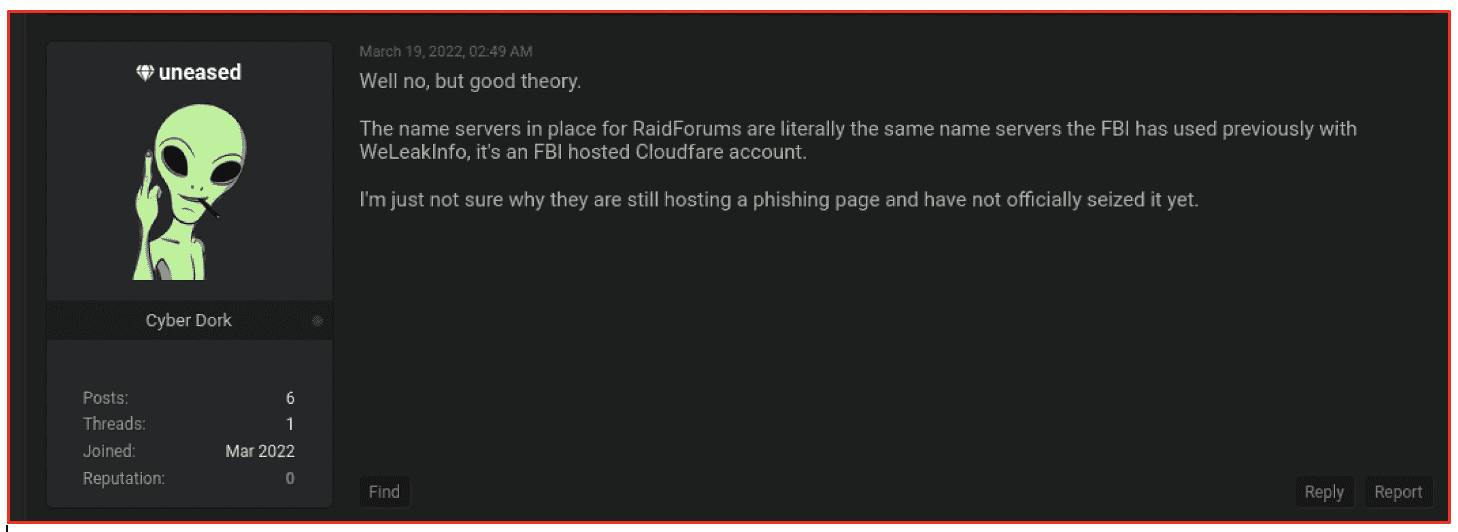
To this day, the raidforums[.]com domain continues to load but the forum is inactive. The domain’s registration information changed on February 25th, 2022. Some threat actors state the new name services for RaidForums is the same servers the FBI has previously used with WeLeakInfo and is associated with an FBI hosted CloudFlare account.
RaidForums Replacements Quickly Emerge
Raid Forums 2
Right after the forum’s outage in early February, the deep web domain raidforums2[.]com was registered and protected by CloudFlare. RaidForums 2 (RF2) is reportedly administrated by the moniker, “burkeluke” and claims no association with the original RaidForums domain. The administrator stated RF2 would be focused on computer science with coding sections and workshops.
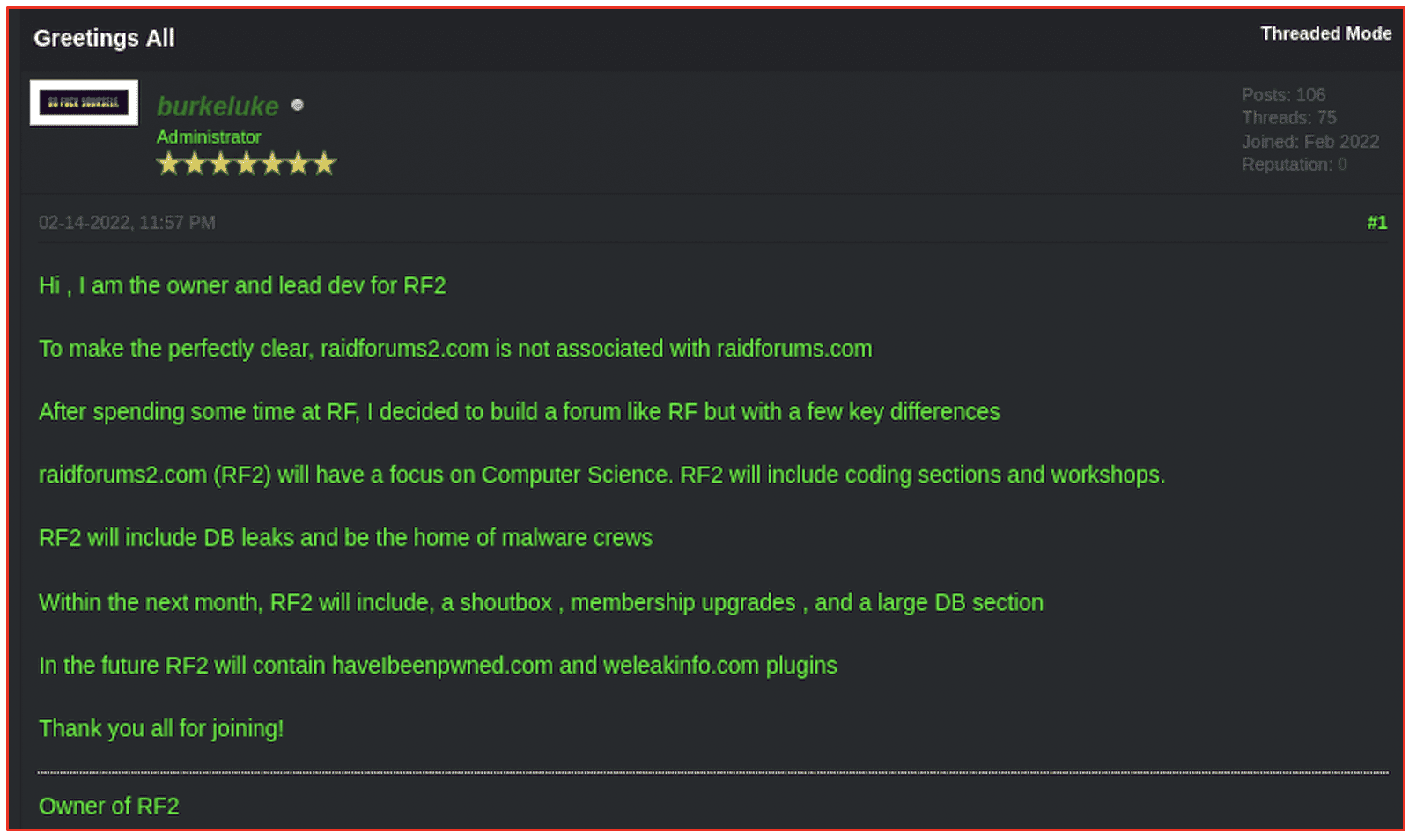
RF2 has been slow to adoption, but its members are well known including AgainstTheWest (a.k.a. Blue Hornet) who quickly used RF2 to share leaks it obtained through campaigns against critical Russian and Chinese targets in recent weeks. The forum also has a section dedicated to the SAMSUNG and Nvidia source code leaks released by LAPSUS$.
Raidforums’ staff aliases like Omnipotent and Jaw appeared, but their authenticity is in question. More than likely, these are classic cases of alias hijacking.
As of time of writing there are 1,025 registered members, 369 posts and 211 threads.
Breached Forums
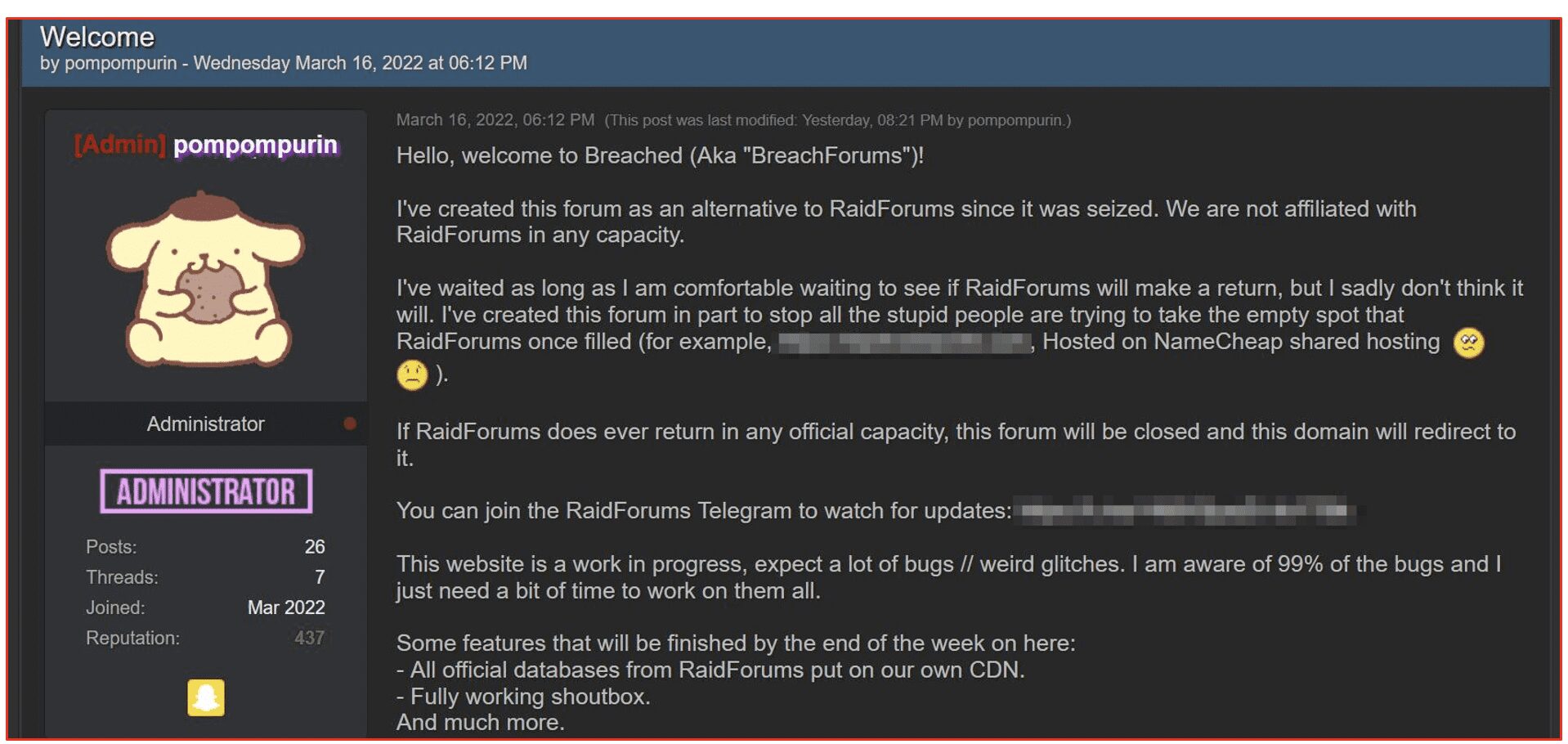
When Jaw announced the raidforums[.]com domain had been seized and was now a honeypot, a legacy user of the community, pompomurin, reportedly DDoS attacked the domain to prevent users from exposing themselves and limit the FBI’s success in obtaining the credentials they sought by keeping the domain alive. The RaidForum user pompompurin is known for prominent commercial data leaks such as CVS and Park Mobile and represented by an adorable avatar – the beret wearing golden retriever character from the Japanese Sanrio Hello Kitty franchise. According to their surface web blog, pompur[.]in, pompompurin, resides in Canada.
During the first week in March, pompomurin setup BreachedForums (BF) on the domain: breached[.]co and opened the site on March 16th for registration and forum discussion. The forum is setup identically to RaidForums complete with the same color scheme, shoutbox, and default avatars. pompompurin claimed no direct affiliation with RaidForums; yet stated that if RaidForums ever returned in an official capacity, then he would shut down BF and redirect the domain to the main RaidForums site.
The popularity and wide acceptance of BreachedForums is evident with the sheer volume of posts and memberships already active on the forum. In less than three weeks activity, the BF domain has registered 3,293 members, with 13,707 posts across 1,939 threads.
The Databases section of the forum includes over 80 unique ‘official’ datasets maintained by the forum’s staff with over 1 Billion records. DarkOwl estimates over 700 unofficial commercial and government data archives have been distributed by members in the leaks and databases sections of the forums.
Many of the posts are related to the conflict in Ukraine with shares of sensitive data exfiltrated in conjunction with Anonymous’s #opRussia cyber campaign.
The BF domain is already being targeted by malicious actors and/or law enforcement. Earlier this week, the forum was offline briefly after the domain was reported to its hosting provider for containing illicit content and CSAM. As a result, pompomurin setup a new onion service on Tor as well as five alternate mirrors in the deep web.
The breached[.]co domain was unreliable and timed out numerous times while writing this report.
Question about something you read or interested in learning more? Contact us to find out how darknet data applies to your use case.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















