Q4 2023: Product Updates and Highlights
January 16, 2024
Read on for highlights from DarkOwl’s Product Team for Q4, including new exciting product features.
Actor Explore Launched
The team released a major new Explore section in our Vision UI focusing on threat actors, providing invaluable insights into cyber threat actors. This feature is designed to empower security professionals, researchers, and organizations with analyst curated information about threat actors. Our analyst team selected 298 actors in these categories:
- State-sponsored
- Cybercrime groups
- Ransomware
- Access brokers
- Exploit brokers or exploit buyers
- Critical infrastructure attackers
- Bulletproof hosting providers
Each actor dossier includes descriptors, contact, and cryptocurrency. The Darknet Fingerprint page includes darknet operations (Telegram Channels or Websites Administered), associated data leaks within the DarkOwl Vision dataset, as well as Forums and Marketplaces on which the actor has been observed. Additional tabs include lists of known Tools and CVEs used as well. Within the Actor Explore section, you can see a Target Map of countries, Links to Research actor aliases and attributes in the DarkOwl Vision dataset, and can compare across different actor groups to see collisions.
This wealth of data enables users to gain a profound understanding of the threat actors, their tactics, and the potential risks they pose. Actor Explore will be regularly updated with new information and actors, prioritizing client needs, ensuring that users have access to the latest intelligence to bolster their cybersecurity efforts and research.
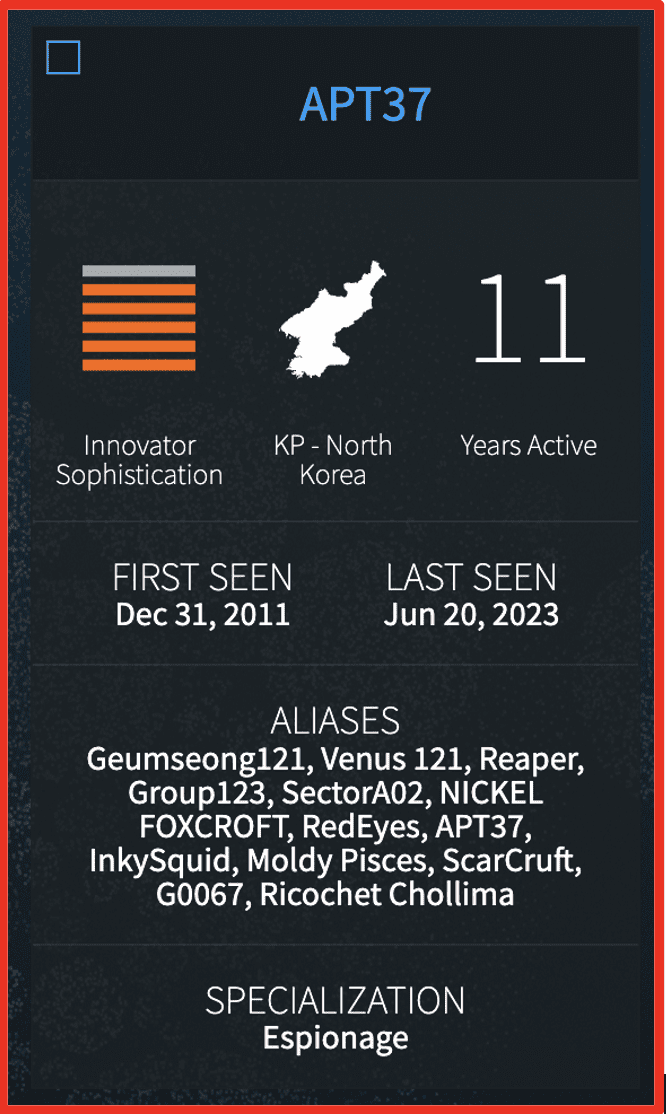
Figure 1: DarkOwl Actor Explore result for APT37
Leak Context Additions
The team has significantly increased the information in Leak Context this quarter, after the initial release in September. All of this content is available in both the UI and Leak Context API.
- We’ve added a Search for Filetree button in the UI that lets you pivot to open a new tab & see the list of all files within the leak.
- We’ve added more than 7 content fields relating to the Original Post location, the Attack Type of the leak, and the Size of the leak.

Leaks of Interest Collected
23andMe
Four datasets relating to 23andMe emerged on a deep web hacking forum as well as Telegram in early October. On October 6, 23andMe confirmed that it was investigating a cyberattack that resulted in unauthorized individuals gaining access to certain customer accounts. The company said it believed that the hackers were able to access certain accounts through a credential stuffing attack, where users had recycled login credentials. Our analyst team wrote a blog covering this leak here.

INDIA – ICMR Leaks Aadhar and Passports 200K Sample
According to the post by RavishKumarOfficial on BreachForums, this is a 200K sample from the 815 million Aadhaar and passport data leak previously posted for sale by pwn0001. The data leak is purported to be a COVID testing data breach. Data exposed includes full names, phone numbers, passport numbers, Aadhaar numbers (Government of India’s 12 digit individual identification number), age, gender, and physical addresses.
Johnny Logs 11DEC23
A batch of infostealer logs were posted to the Johnny Logs Telegram channel on December 12, 2023. Data exposed includes log data from a reported 3,000 log files and varies based on data that was exfiltrated from each machine.
Vision UI & API Updates
We launched our UI Assistant to announce new features and content, including a weekly What’s Leaking update.
For Email Domains, you are now able to generate an Email Domain Report PDF, a PDF version of the information displayed on the screen.
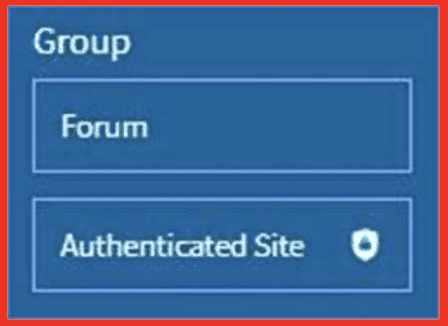
The Authenticated Site label now appears on search results, allowing user to easily tell which search results are from these sites
Search Block translations: We added new search block keywords in Arabic, French, Russian, and Spanish, and updated the design of this page to feature our growing translation options.
Search Result Pivoting: Within search results with extracted chat users or extracted emails, cards, cryptocurrency, or IP addresses, you can select research actions under the corresponding View Switch to help you to navigate to additional results with the Research or Entity Explore sections:
- Username Research (Chat Users): Identify the darknet footprint associated to a username or user ID of interest, that can lead to alternate usernames and conversations in our chat application data.
- Entity Explore Results: See aggregate data on Email Addresses, Credit Cards, Cryptocurrency or IP Addresses, with the ability to filter and batch export relevant results.
Curious how these features can make your job easier? Get in touch!
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















