Ransomware RoundUp: 2022
March 30, 2023
Ransomware groups continued to be a major threat over the past year, causing significant financial and reputational damage to their victims. Their evolving tactics and strategies make it increasingly difficult for organizations to defend against their attacks. However, with increased awareness and investment in cybersecurity, governments and businesses can work together to protect themselves from this growing threat.
Despite the number of reported ransomware complaints decreasing in 2022, the victim payouts have increased. The IC3 estimates that from 800,944 complaints the potential loss is around $10.2 billion. Ransomware continues to run rampant with around 33% of organizations globally being a victim of ransomware, indicating that the groups are becoming more confident and targeted.
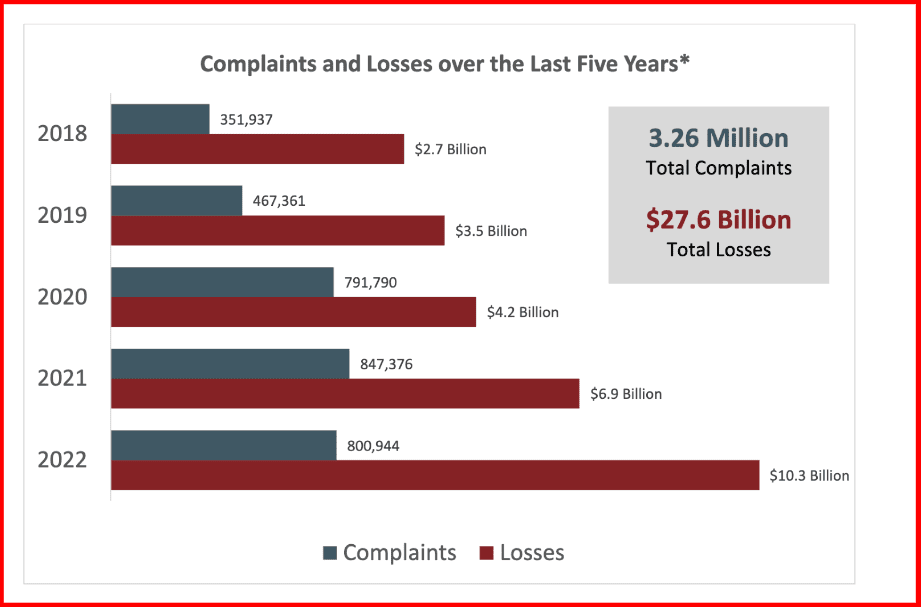
Figure 1: Source: 2022 IC3 Report
The overall increase in victim payouts could be partly due to the ways ransomware gangs have changed their operations. In 2022, ransomware groups deployed more backdoors – which allow for remote access. They also began to favor extortion, typically through ransomware or business email compromise. Europe saw 44% of these extortion cases.
According to IBM’s X-Force Threat Intelligence Index, the manufacturing industry was the most extorted in 2022. The FBI’s IC3 (Internet Crime Complaint Center) received the most ransomware attack complaints from Health Care and the Public Health sector; a trend DarkOwl has seen reflected in the victims of the groups detailed below.
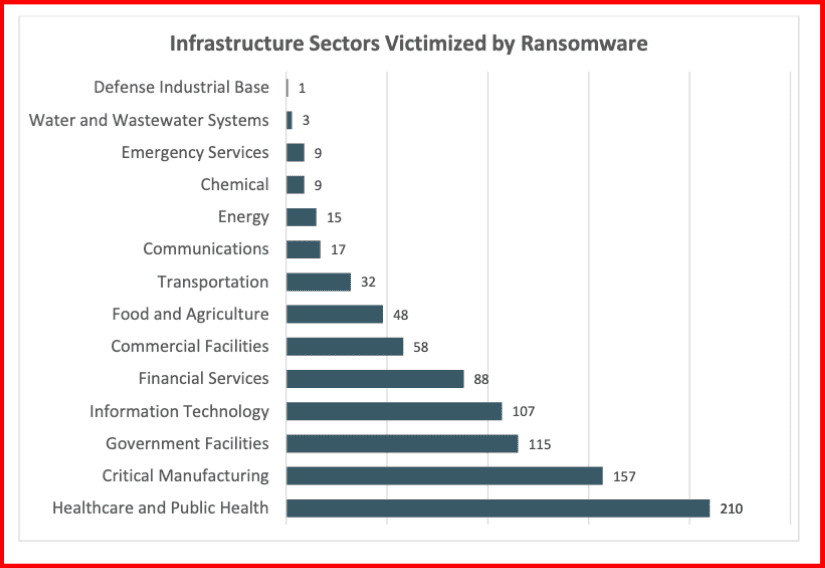
Figure 2: Source: 2022 IC3 Report
In this roundup, DarkOwl analysts take a look at the some of the largest ransomware and ransomware-as-a-service (RaaS) gang activity from 2022, and introduce several new and emerging groups that DarkOwl has observed actively operating on the darknet today.
Review of Active Ransomware Groups in 2022
LockBit
LockBit has been one of the most active ransomware groups this year, claiming to have targeted 436 organizations in just the later half of 2022. The group released LockBit 3.0 with new capabilities making it harder to identify in June 2022 and notably started their own bug bounty program. After a LockBit attack on SickKids hospital, LockBit blamed one of their affiliates, released a decryption key for free, and apologized saying the attack went against their policy.
Black Basta
A newcomer that rose to prominence in April 2022 with their attack on the American Dental Association is Black Basta. This group also has possible ties to other ransomware gangs such as Conti, REvil, and Carabank (Fin7). They specialize in double extortion and have been seen outsourcing tools with the use of initial access brokers, Qakbot, and Cobalt strike.
Black Pasta has been observed using the darknet to request login credentials for initial access. Their malware and victim selection suggests they are sophisticated Ransomware actors.
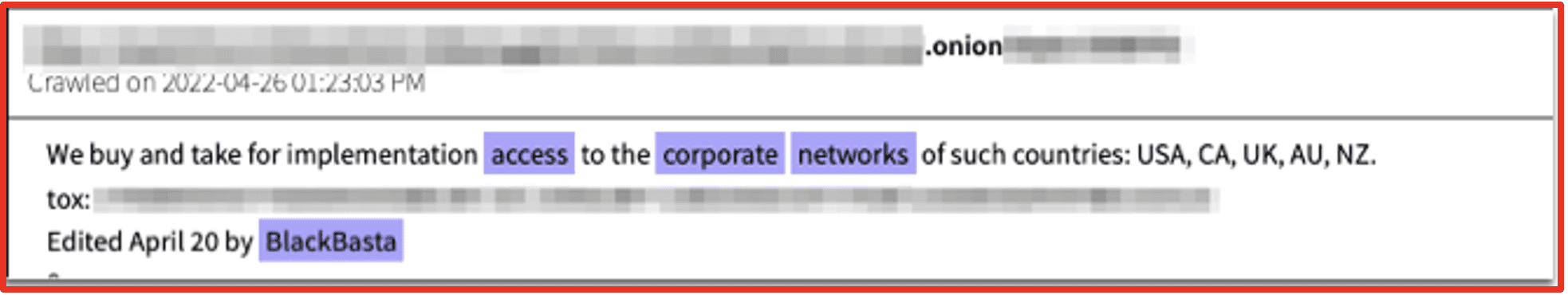
Figure 3: User Black Basta posts in a Darknet forum for corporate access; Source: DarkOwl Vision
Hive
Hive ransomware was first observed in June 2021 and uses an affiliate RaaS model. Unlike some other groups who claim a moral code, Hive has repeatedly targeted healthcare organizations and threatened to leak patient information. As of March 2022, 125 healthcare organizations had been targeted by Hive.
Hive’s original ransomware was written in GoLang – but, in 2022, they switched to Rust. The switch improved their method of encryption, among other advantages.
In January 2023, the Hive operation appeared to have been shut down with a seizure banner appearing on their site detailing a multi-country law enforcement operation. Law enforcement had access to Hive’s computer networks ahead of the takedown and were able to help those who would have been victims.

Figure 4: Hive Ransomware seizure banner; Source: Malwarebytes
Conti
The Conti Ransomware group going into 2022 was one of the most active and prolific RaaS groups. At the outset of the Russian invasion of Ukraine, Conti was one of the first to announce its support for the Russian government after which their ransomware source code and other sensitive data including PII and private communications between actors was leaked. In late May 2022 Conti shut down their official Tor website, Conti News, and the service site for their negotiations went offline. However, reporting indicates that the group has dispersed and not disappeared with some members joining other ransomware groups such as BlackBasta, BlackByte, and Karakurt. However, it is possible that Conti may reappear under a different name in the future.
BlackCat
The BlackCat Ransomware group (AlphaV) who first appeared in later 2021, is thought to have infected more than 60 victims in its first 6 months of operation. The groups are reported to be connected to BlackMatter/DarkSide, with the FBI reporting that many of the developers and money launderers in the group originated from Darkside. BlackCat were the first group to use Rust in their attacks before it was adopted by Hive. BlackCat were one of the first groups to create a public data leaks site and in 2022 they created a search feature for their indexed stolen data to put more pressure on organizations to pay their ransom. LockBit later followed suite. They continue to be active in 2023.
New or Emerging Ransomware Groups
DarkOwl has identified several emerging ransomware groups that are presently active on the dark web. Each of the new ransomware gangs below rose to prominence in 2022 and continue to be active into 2023.
0mega
The 0mega Ransomware group was first identified in May 2022, targeting organizations worldwide with double-extortion techniques. At the time of writing no sample has been identified and analyzed for the 0mega ransomware variant. The ransomware demands are customized to the victim, and victims are required to upload the demand to access the TOR payment negotiation site. The 0mega leak site on TOR currently has 3 victim companies listed with links to download the data. The site was last updated 2023/02/11.
0mega’s operation appears to be organized and is a group to look out for this year.
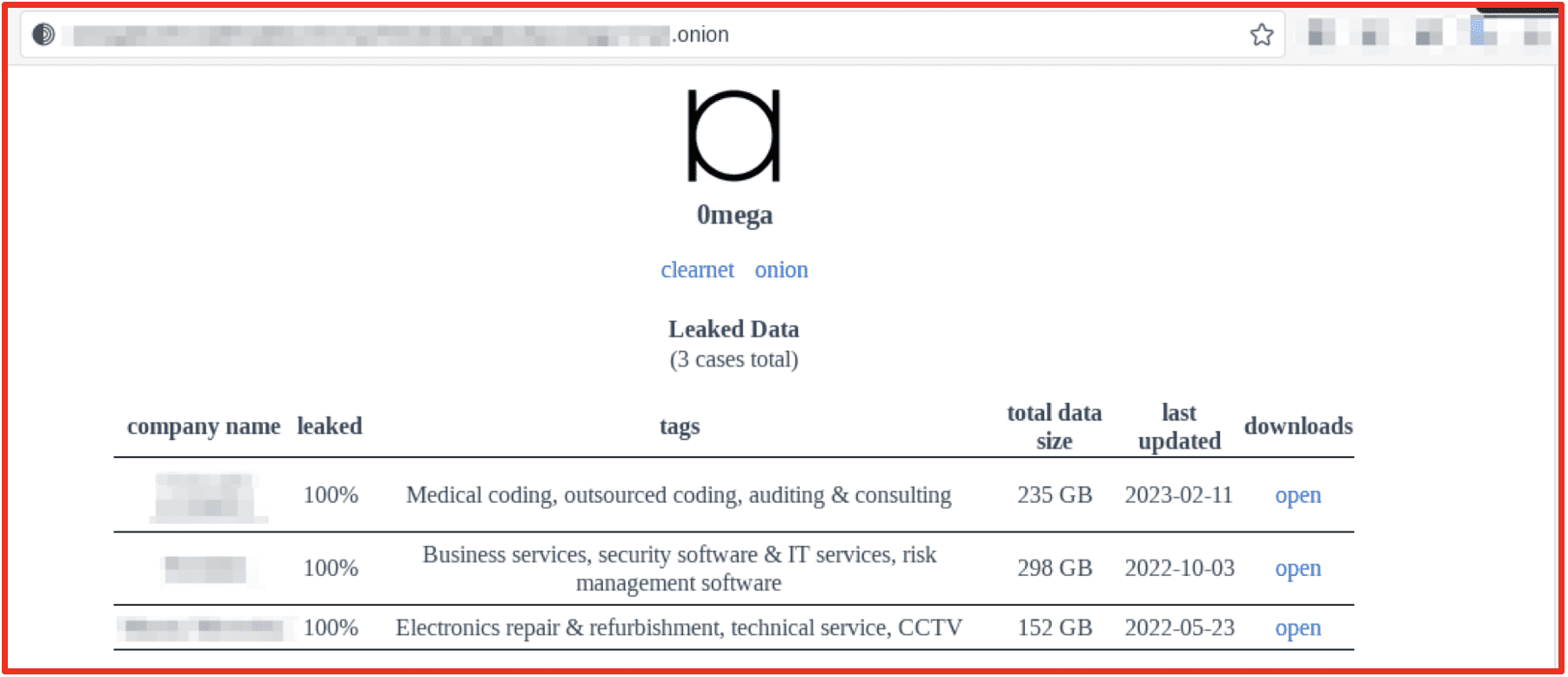
Figure 5: 0mega Data Leak Site; Source: Tor Anonymous Browser
BianLian
BianLian has had infrastructure since December of 2021 and tripled their infrastructure in August of 2022. Their victims include health services, information technology services, education, and construction companies. They have created their own toolkit with their ransomware written in Go, and have been seen using living off the land techniques and can establish a backdoor for persistence. BianLian currently offers an I2P mirror complete with instructions for how to install.
Avast recently released a free decryptor for the currently known BianLian ransomware strain. This could explain why recently BianLian has not been encrypting victim’s data, instead focusing on extortion. The group will need to stay ahead of researchers’ decryptors this year to continue targeting victims successfully.
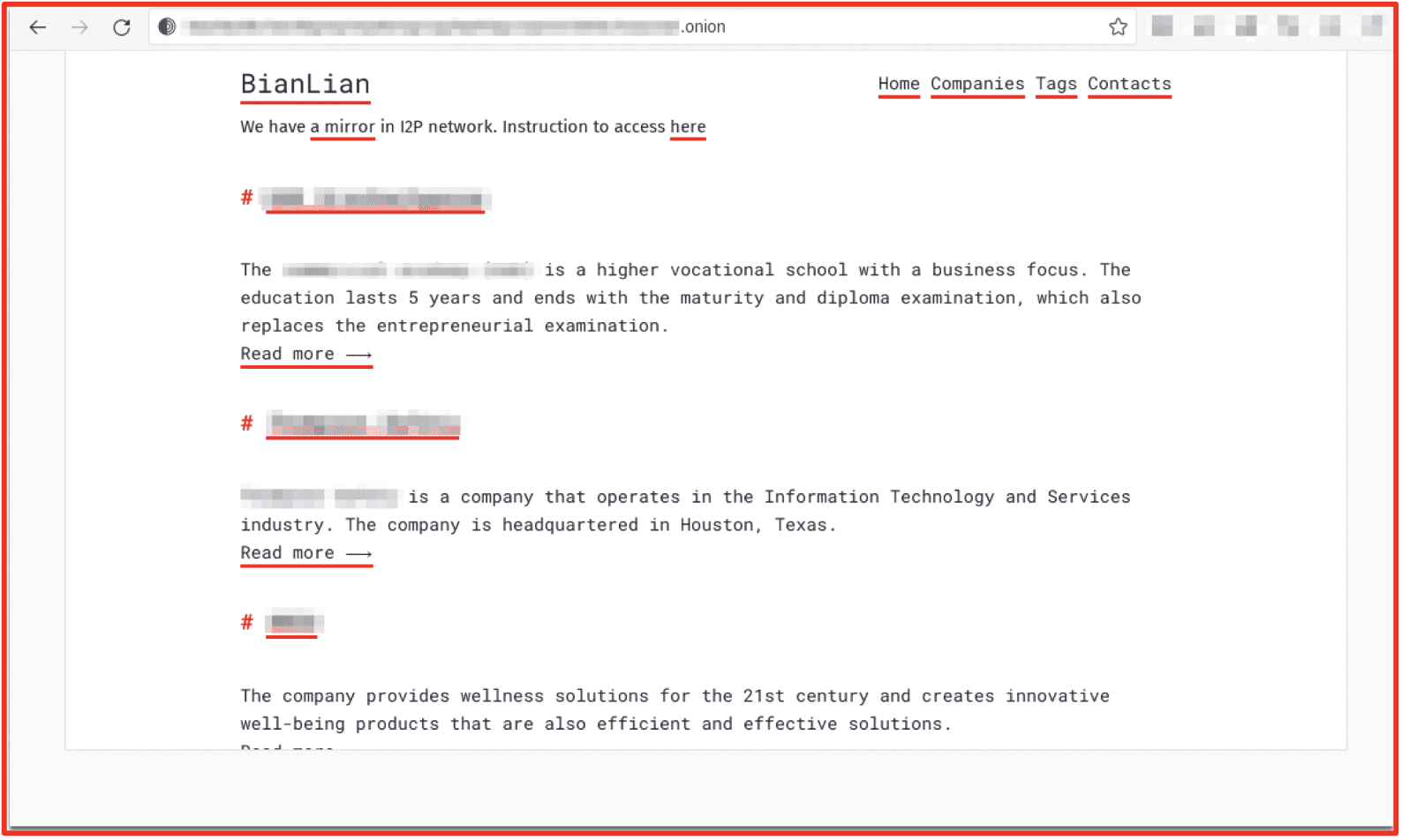
Figure 6: BianLian Data Leak Site; Source: Tor Anonymous Browser
Daixin
The Daixin ransomware group is known for targeting the health sector, leading CISA to issue a cybersecurity advisory to this sector in October 2022. The group have been active since June 2022 and built their ransomware from leaked source code attributed to Babuk Locker. In early 2023, their Tor leak site had 8 victims listed with details of what documents have been obtained by the group.
The Daixin Team encrypt the servers relied on by healthcare organization, which means they can halt key services increasing the likelihood of a payout and can also exfiltrate PII, creating a further revenue stream as this data achieves higher prices on dark web marketplaces. However, consistently attacking healthcare organizations has drawn the attention of law enforcement which could mean they are on the verge of disruption. Nevertheless, due to its profitability, the Daixin team will likely continue targeting this sector. The health sector should be wary of Daixin.
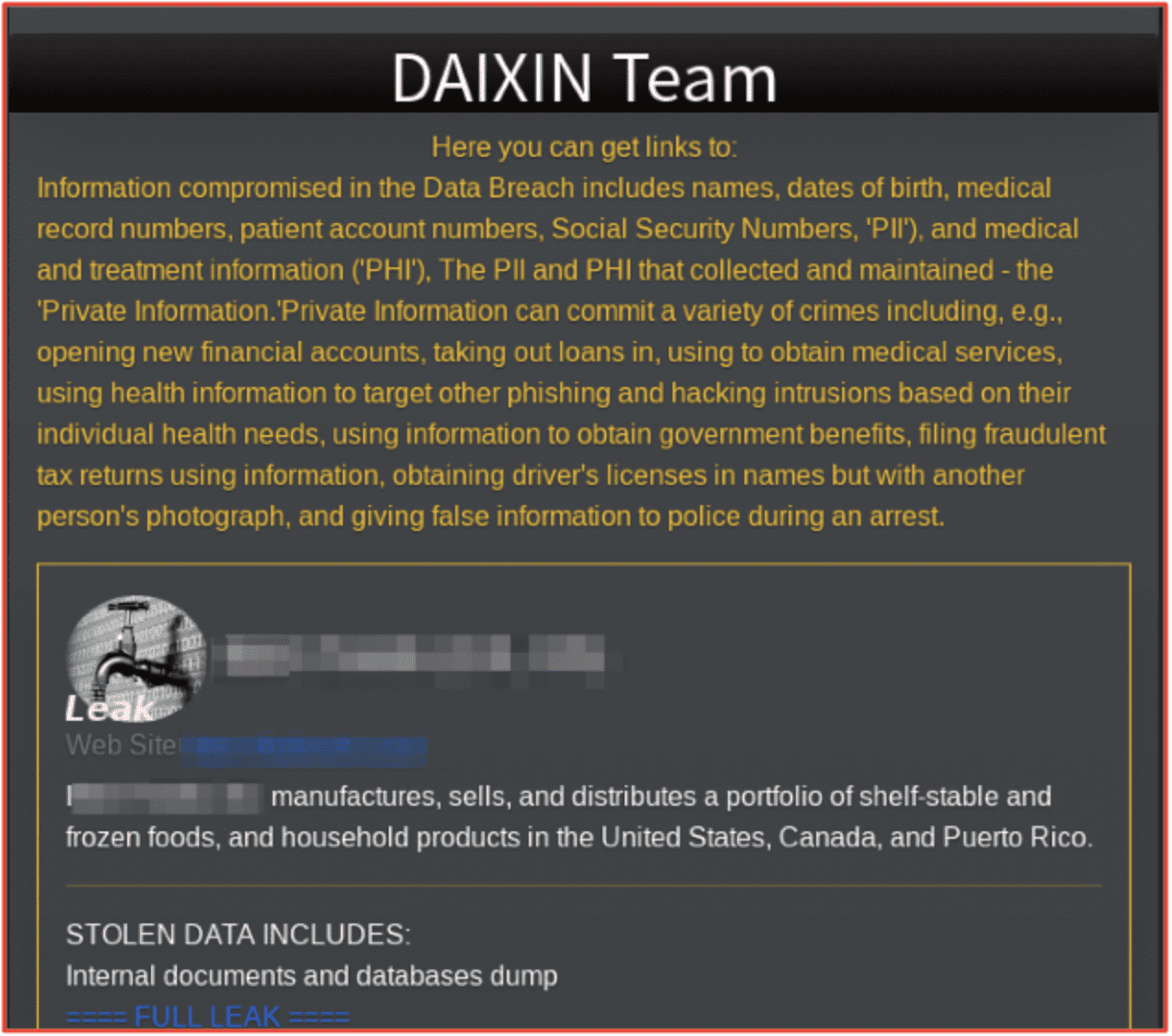
Figure 7: Daixin Team Tor Site; Source: Tor Anonymous Browser
Royal
Royal first materialized in January of 2022 and is believed to be made up of actors previously associated with Conti, TrickBot, and Roy/Zeon malware (the group was originally named Zeon). Unlike some other groups, Royal does not provide its ransomware as a service and they do not make their code available to affiliate actors. Recently they have released a malware variant which preys on Linux systems. The group is known for using call-back phishing tactics impersonating food delivery or software providers.
Royal’s Tor page begins with a contact form, requiring the user to submit an email address. It also has search bar functionality to identify victims. Royal currently has around 58 victims for 2023 listed on their site, the highest of any group reviewed in this article. Royal will upload samples of data to this site to prove their legitimacy to their victims. If the victim refuses payment, 100% of the stolen data will then be uploaded to the site. Some ransomware gangs will remove victims’ information from their site if they pay the ransom. Therefore, the number of victims shown does not always reflect the true number of victims targeted.
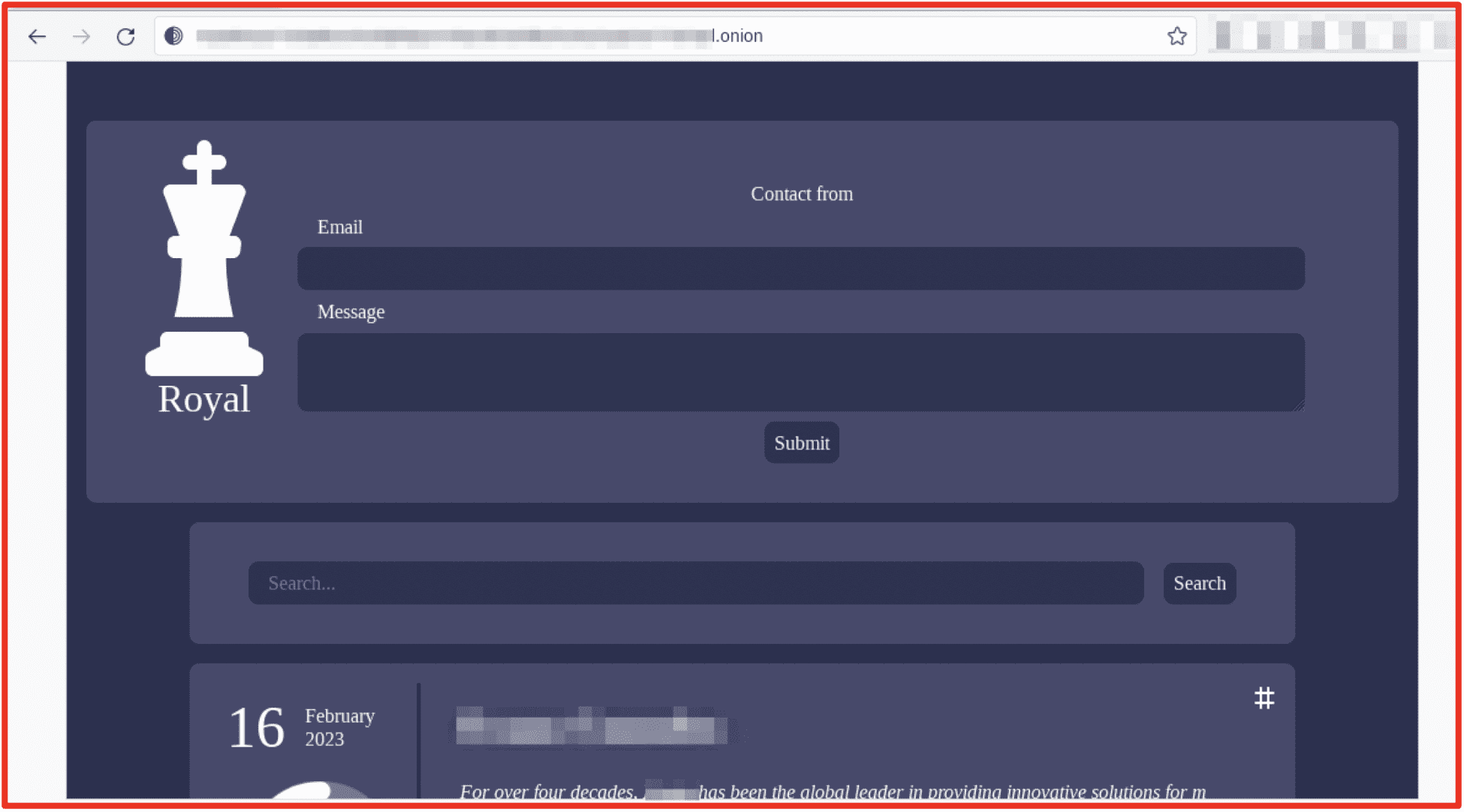
Figure 8: Royal Ransomware Tor Site; Source: Tor Anonymous Browser
Although Royal ransomware has emerged recently, researchers believe the actors running the group are sophisticated and experienced. DarkOwl analysts assess Royal will continue to grow into an even greater threat in 2023.
Final Thoughts
Ransomware is an ever-evolving threat ecosystem. Some groups are driven by political motivations, but most attacks are for financial gain. Ransomware groups use the darknet and darknet-adjacent sites to negotiate with victims, spread their personal brand, and develop or purchase new, sophisticated technology to thwart cyber defense teams. Advances in cyber defenses have prompted some groups to focus on data extortion, pressuring companies with the valuable private data they have stolen rather than encrypting networks.
Despite the successes of cyber defense teams in 2022, ransomware gangs will be keen to develop different tools and tactics to better evade security measures. Additionally, ransomware attacks are underreported – around 75% are never reported. Even when law enforcement successfully shuts down a ransomware operation, the group is likely to rebrand or the members will simply disband and work for other ransom groups. Given some entities are still willing to pay, ransomware will remain a threat because of potentially massive financial rewards.
DarkOwl Vision allows organizations to monitor these ransomware groups on the darknet, to identify more information about their tactics, techniques, and procedures and the sectors they are targeting. DarkOwl analysts continuously monitor the darknet to identify emerging new groups and who the most recent victims are to best track and predict potential attacks.
Interested in learning more? Contact us to learn about our Ransomware API.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















