Super Bowl Security and the Darknet
February 08, 2023

Events that bring masses of people together are inherently attractive to cyber threat actors. For one, the physical gathering of such a large crowd of people offers the opportunity for close-proximity hacking. However, the cyber threats surrounding large-scale events like this are much more complex. Well before fans, performers, media teams and vendors arrive at the stadium that Sunday, there will have been numerous betting transactions made, sponsorship payments delivered, and accounts for fantasy apps created. All of these digital touch points offer threat actors with the opportunity for exploitation and theft.
In taking a closer look at what the cyber threat landscape looks like around Super Bowl LVII, our analysts turned to the darknet and found examples of key game-day vendors with darknet exposure. This includes exposed credentials, chatter around malware that can allow hackers access to key vendor technologies, such as ticket payment systems.
The Super Bowl as a Target for Hackers
Cyber incidents impacting large scale events such as the Super Bowl have ranged from “hacktivists” making political statements to DDoS attacks that have taken down entire stadium, as witnessed in the 2018 Winter Olympics
While an attack on that catastrophic level has not been successfully carried out during the Super Bowl to-date, experts agree that it remains a highly attractive target for hackers. Further supporting this notion is a recent example from the 2019 Super Bowl, when – just before the big game – cyber crime group OurMine took over teams’ Twitter accounts, as well as the official account of the National Football League. Per reporting, 15 teams had their Twitter or Instagram accounts compromised, as well as accounts for ESPN and the UFC.
Darknet Risks to the Super Bowl: Key Vendors Pose Supply Chain Risk
This following findings from our analysts present these examples using screenshots from the darknet (and dark web adjacent sources such as Telegram), as well as from DarkOwl Vision, our darknet threat intelligence tool.
Gambling & Online Sports Betting Apps
This year, gambling and sports betting apps are a highly attractive target for hackers for a number of reasons. After legislation legalized sport betting around the nation, these types of apps are now available and being used by a vastly higher degree of population than in previous years.
These types of services are also typically connected to a payment system, allowing users to make bets and access their transaction with minimal effort. From a threat actor perspective, that makes digital sports gambling apps one of the most likely targets for phishing campaigns and potential account takeover.
DraftKings
Below is an example of a threat actor selling stealer logs for DraftKings on the darknet site Russian Market. These logs include stolen browser session cookies, which are used to crack accounts and bypass multi-factor authentication for logins. In this case, the vendor is offering “premium” stealer logs for just $10 US dollars.
Stealer logs are typically harvested by threat actors using a form of malware known categorized as “info stealers,” such as Raccoon and Redline.
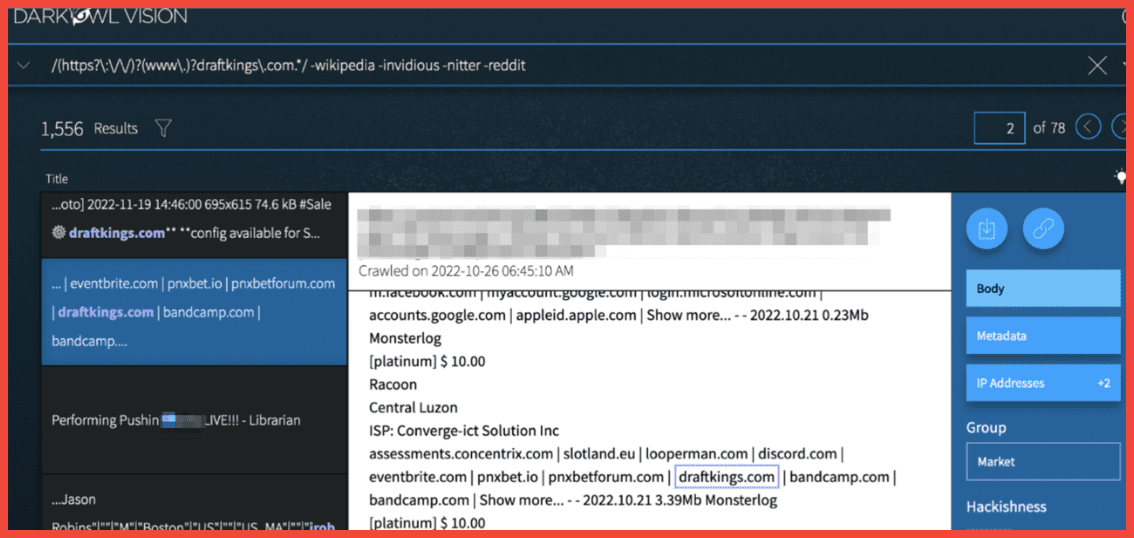
Figure 1: DraftKing Stealer Logs for sale on a darknet marketplace, Screenshot: DarkOwl Vision, Original Source: Tor, Russian Market
Hackers also gain access to existing DraftKing accounts using more traditional methods like credential stuffing and exchanging combolists to exploit exposed account login information.
In the screenshot below, a user on Telegram lists DraftKings as one of the services they have cracked (likely stolen) credential logins for.
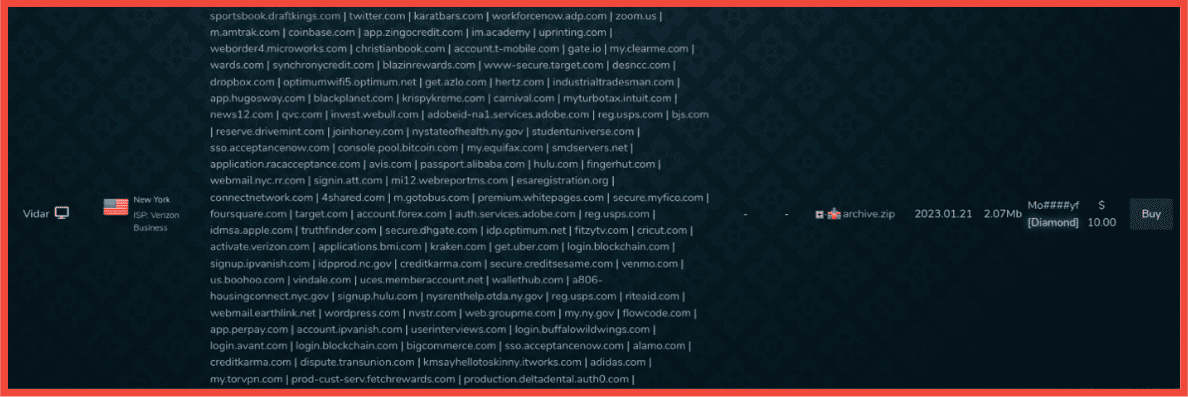
Figure 2: DraftKings accounts among the many listed under compromised credential combolists, Screenshot & Original Source: Telegram
Other listings for stolen DraftKing accounts on Telegram are more explicit, with some offering accounts that come with pre-existing balances, as well as methods to bypass multi-factor authentication.
As demosntrated in the screenshots below from Radiant’s Market, the listing for “DraftKing + bal (New method instant cash)” accounts appears alongside similar listings for other services popular with NFL fans, including Fanduel and Superdraft.
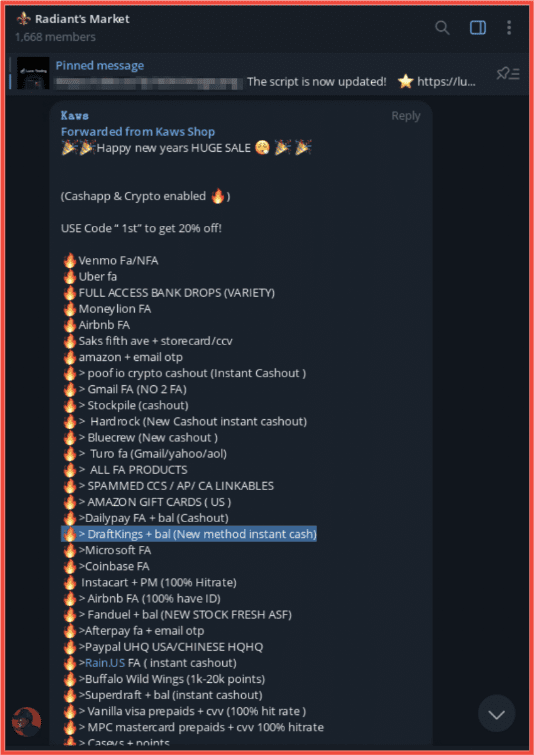
Figure 3: Listing on Telegram for compromised accounts including popular NFL affiliated vendors, Screenshot & Original Source: Telegram, Raidiant Market
BetMGM
The below screenshot from DarkOwl Vision shows multiple listings for BetMGM accounts (in the preview window on the left), as well as a noteworthy result from the darknet carding forum, WWH Club. The post is from a russian-speaking threat actor looking to buy “betmgm.com and fanduel accounts”.
The fact that this solicitation was posted on a carding forum indicates that this actor is actively targeting sell BetMGM – even linking their Telegram handle for potential sellers. This, combined with the numerous listings for already-cracked BetMGM accounts, demonstrate that they are a desirable target for hackers.
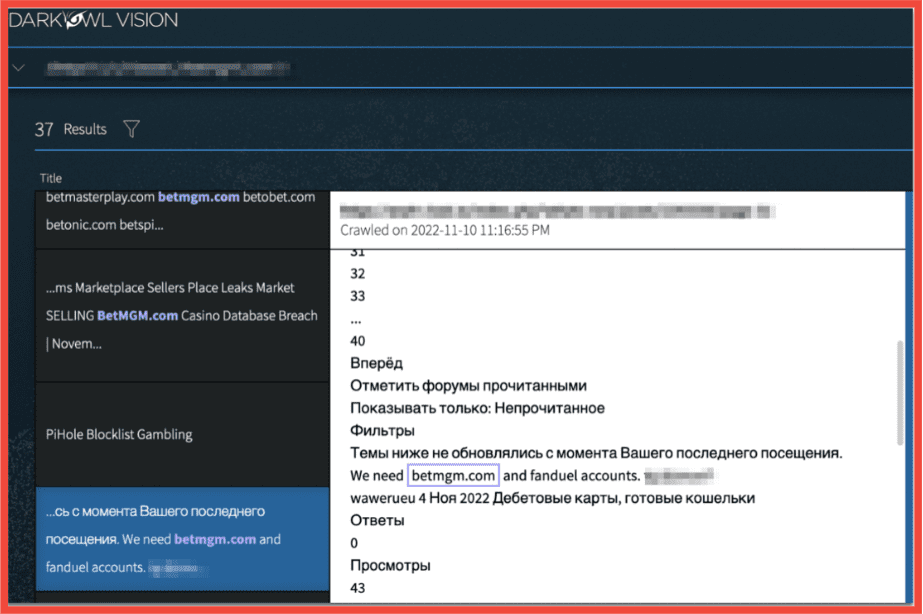
Figure 4: Post on a darknet marketplace soliciting for BetMgM (and Fanduel) accounts, Screenshot: DarkOwl Vision, Original Source: Tor, WWH Club
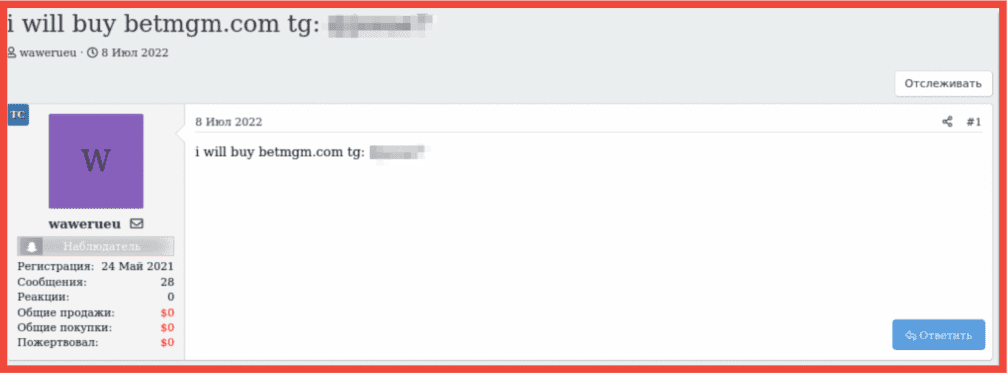
Figure 5: Post on a darknet marketplace soliciting for BetMgM (and Fanduel) accounts, Screenshot: & Original Source: Tor, WWH Club
Banking Systems
Truist
In January 2021, the bank Truist signed a multi-year deal to be the official retail bank of the NFL. As a result of this agreement, Truist is now the exclusive financial service provider for all facets and personnel within the NFL, including player contracts. Per their website, the services Truist offers include:
- Banking products and services, including loans and deposit accounts
- Investment management services
- Securities, brokerage accounts and /or insurance (including annuities)
- Investment advisory services
- Life insurance products
The partnership between the NFL and Truist also contains a heavy branding component, with the Tuist logo now featured on all official NFL materials and marketing campaigns. The combination of Truist’s role in the NFLs financial security, in tandem with their brand’s newly formed partnership tying them together so closely, make Truist a critical asset for the football league – and an attractive target to threat actors.
Below are several examples of actors on the darknet and deep web actively targeting Truist Bank.
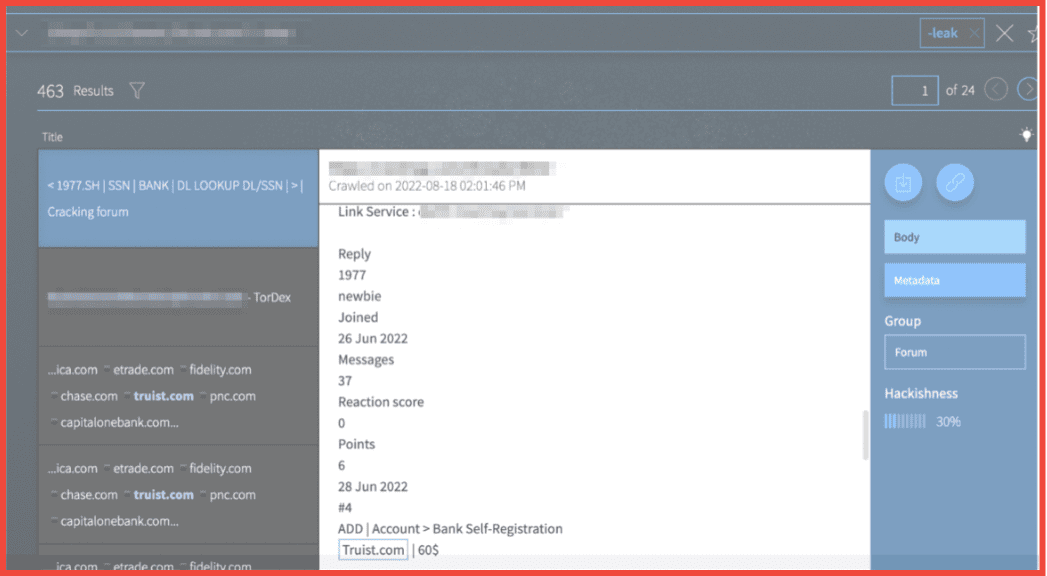
Figure 6: Post on the forum Cracking X offering a Truist bank account for sale, Screenshot: DarkOwl Vision, Original Source: Telegram, Cracking X
In the screencapture from DarkOwl Vision above, a user on the site Cracking X offers access to cracked Truist bank accounts for as little as $60 US dollars.
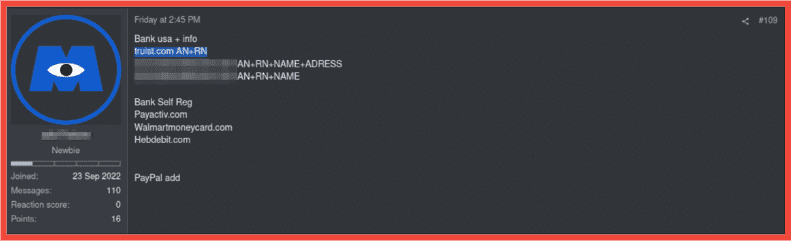
Figure 7: Another offer for Truist.com accounts on the Cracking X channel, Screenshot & Original Source: Telegram, Cracking X
Below, two different vendors offer Truist bank accounts with Debit Logs. Both listings advertise that they come with associated Personally Identifiable Information including login credentials, SSN, Date of Birth, and Email Access for bypassing multi-factor authentication.
The first example pictured contains several listings for stolen or fraudulent Truist bank accounts. One of these advertised listings allegedly contains a balance of $122,000 and is listed for only $1,200 US dollars.
In the second screenshot, taken directly from Telegram, a more modest listing offers a Truist account with an alleged $14,000 balance for $250 US dollars.
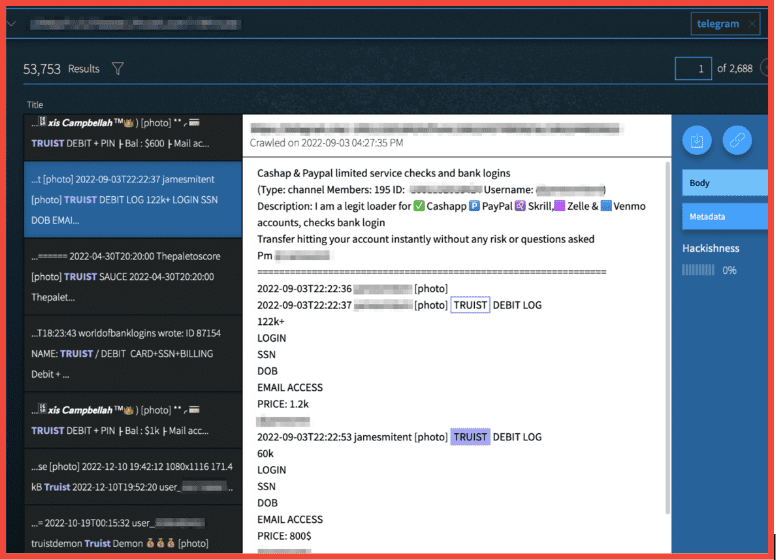
Figure 8: Hacked Truist Accounts with Debit Logs and PII on offer for sale, Screenshot: DarkOwl Vision, Original Source: Telegram
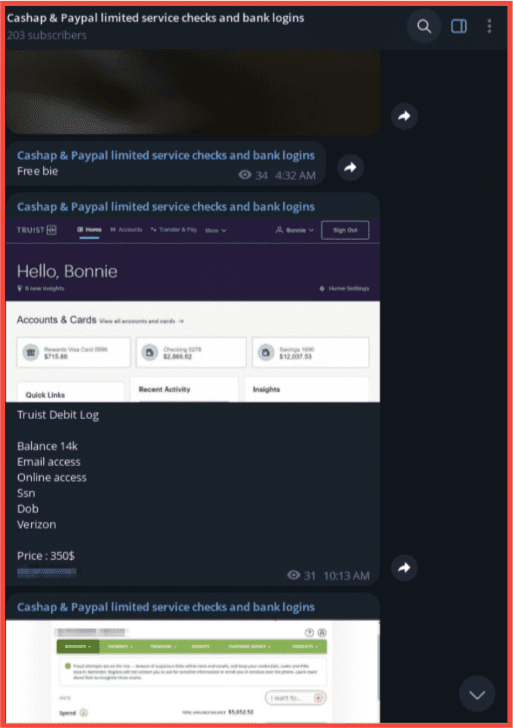
Figure 9: Hacked Truist Accounts with Debit Logs and PII on offer for sale, Screenshot & Original Source: Telegram
Ticket Payment Systems
StubHub
As the official ticket payment system of the Super Bowl, DarkOwl analysts found numerous instances of official Super Bowl ticket vendor StubHub data on the darknet.
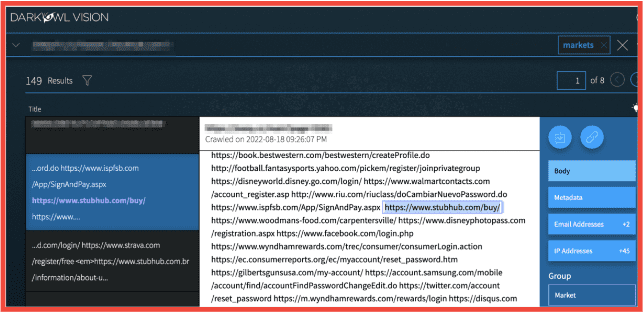
Figure 10: Source DarkOwl Vision
Above is a listing to a stealer log marketplace called 2easy Shop that has a large Russian language userbase. In this instance, a threat actor is selling access to stealer logs for someone’s accounts to StubHub and all the other domains mentioned. Price for bulk purchase of these logs typically sell for around $10-$20 US dollars.
Below, users on Telegram offer access to cracked Stubhub accounts, including some that have access to order history and payment methods.
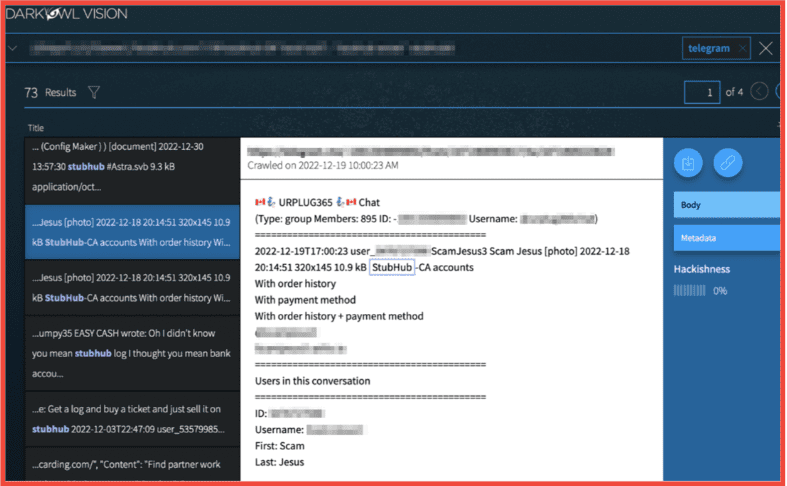
Figure 11: Users on Telegram sell stolen StubHub accounts, Screenshot: DarkOwl Vision, Original Source: Telegram
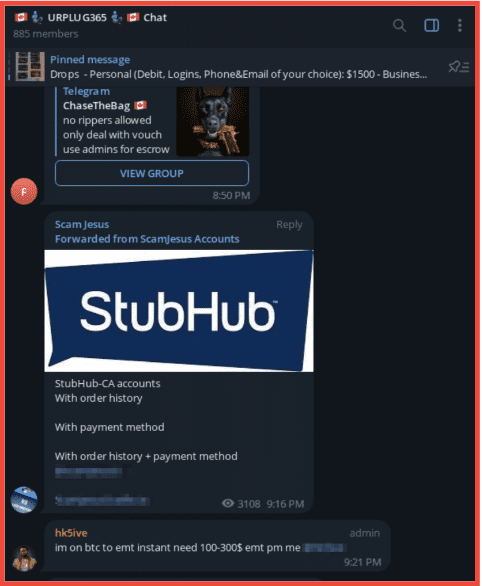
Figure 12: Users on Telegram sell stolen StubHub accounts, Screenshot & Original Source: Telegram
Streaming Services
Sunday Ticket
NFL Sunday Ticket is a streaming package provided by exclusively by DirectTV. While unlikely to pose a direct threat to the NFL directly, hackers defraud the streaming service frequently by cracking, selling, and trading stolen accounts.
YouTube TV
While not officially associated with the NFL yet, in 2024, YouTube is slated to pay around $2 billion dollars a year for the rights to the “Sunday Ticket” package, taking it over from DirectTV. While the deal presently does not include commercial rights or give YouTube TV stake in NFL Media, negotiations are ongoing and that is expected to change. So, while YouTube and its parent company Google are presently a low-risk asset for this year’s Super Bowl – that is something to keep an eye on for next year’s season.
Cyber Risks to the Super Bowl: The Bigger Picture
While the dispersed and perhaps seemingly small-scale nature of these vendors’ darknet footprints may make them seem inconsequential, it is important to consider the bigger picture. There is a good likelihood that threat actors will continue to ramp up attacks surrounding this event in tandem, which beyond the financial consequences can have a significant effect on corporate brand reputation.
With threat attack vectors becoming ever more sophisticated, large events like the Super Bowl –which bring together humans and technology at such a high magnitude during such a concentrated period of time – offer a unique opportunity to threat actors. By maintaining visibility into threat actor activity on the darknet, NFL fans, vendors, and corporate decision makers can position themselves in the best way possible to be ahead of and respond to cyber incidents.
Interested in learning how darknet data applies to your use case? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















