The Importance of Tracking and Monitoring Cyber Threat Actors
Introducing DarkOwl’s new addition to our Vision UI platform, Actor Explore
November 08, 2023
Introduction
In today’s digitally driven world, the landscape of cyber threats is ever-evolving and increasingly sophisticated. As businesses and individuals become more dependent on technology, the need to protect sensitive data and critical infrastructure from cyber attacks has never been more critical.
One effective approach to enhancing cybersecurity is to track and monitor cyber threat actors. The actors that are responsible for conducting attacks; individuals or groups with malicious intent, often targeting organizations, governments, or individuals. Understanding why they are operating, what they hope to achieve and what methodologies they are using can assist analysts in protecting infrastructure and predicting future activities.
Why Are Threat Actors Important
Motivations for conducting these attacks can vary greatly from financially motivated to espionage threats to geo-political events, just to name a few. It is important to understand the motivation of threat actors as this can help identify what they are trying to achieve and what threats they might pose to certain organizations, industries or even countries.
Identifying and monitoring the tactics, techniques, and procedures (TTPs) of cyber threat actors, is also an important step to gain insights into actor’s strategies. This information can be invaluable in understanding how attacks are executed and identifying potential vulnerabilities in an organization’s defense.
Attribution is the process of determining who is the real individuals behind an attack. Knowing who is responsible for an attack not only helps with law enforcement efforts but also serves as a deterrent. When malicious actors know that they can be identified and held accountable for their actions, they may think twice before engaging in criminal activities. However true attribution is not always needed, knowing what activities a group are conducting and who their victims are can help us to understand what will happen next and learn for future attacks.
Actor Explore
Today, DarkOwl has launched Actor Explore, which will allow users to review analyst curated insights into active threat actor groups on the darknet and wider. We explore the motivations behind the groups, the tools they have used and searchable attributes to pivot on within DarkOwl Vision. Here we explore three of these groups available in Actor Explore and the motivations, methodologies and TTPs that the groups use.

Anonymous Sudan
Anonymous Sudan are a hacktivist group who are very active on Telegram, running their own channel which regularly publishes details of the attacks that they are undertaking and re-posting information from affiliated groups such as Killnet.
They appear to be politically and religiously motivated, targeting countries or organizations they perceive to be anti-Muslim or pro-western. However, security researchers have hypothesized that they group is backed by Russia given their links to pro-Russian groups their way of operating and the financial backing they appear to have.
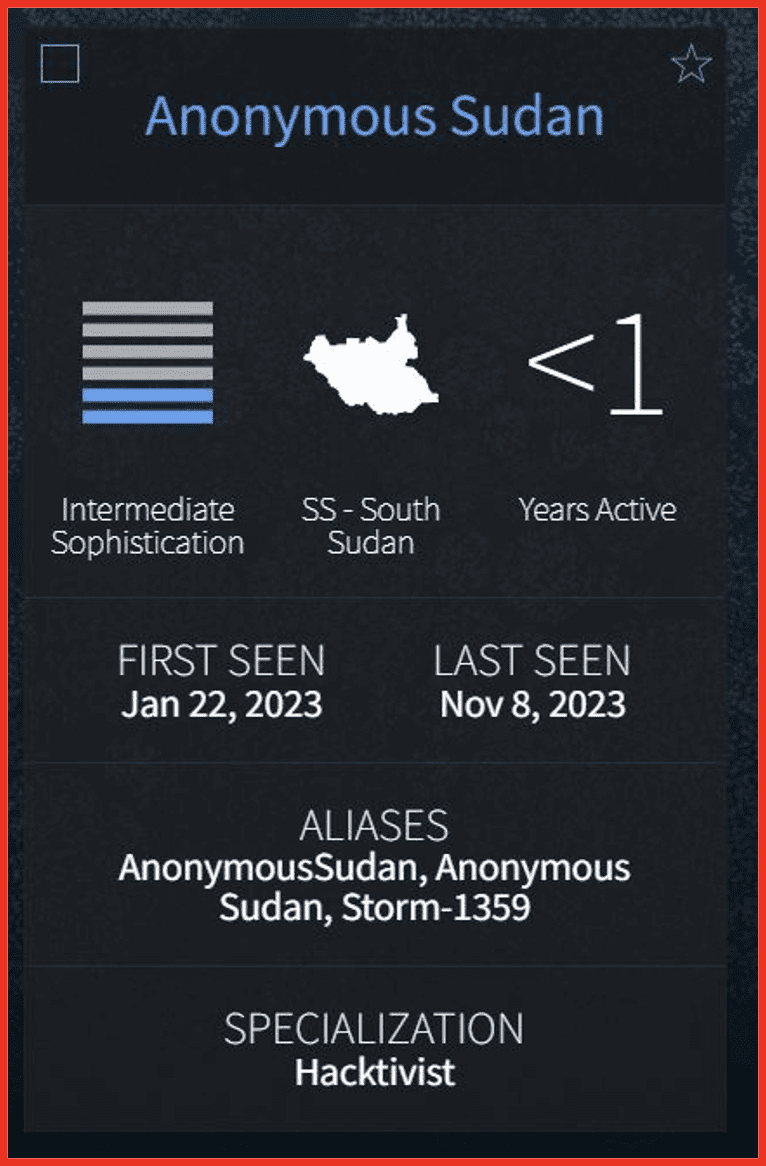
Figure 1: DarkOwl Actor Explore result for Anonymous Sudan
The group emerged in early 2023, when they began to conduct Denial of Service (DDOS) attacks against organizations in Sweden and Denmark. DDOS appears to be the main method of attack that they have adopted, often evidencing their success by posting images of the downtime of their victims’ websites.
The group’s current Telegram channel was created in September 2023, when they claimed that their original channel had been banned by Telegram. In response to this they attacked the Telegram website and caused issues and downtime for Telegram users. The attacks appeared to continue throughout the month.
Later that month the group targeted a number of US companies, including Netflix and Hulu which it stated was a response to US interference in Sudanese internal affairs.
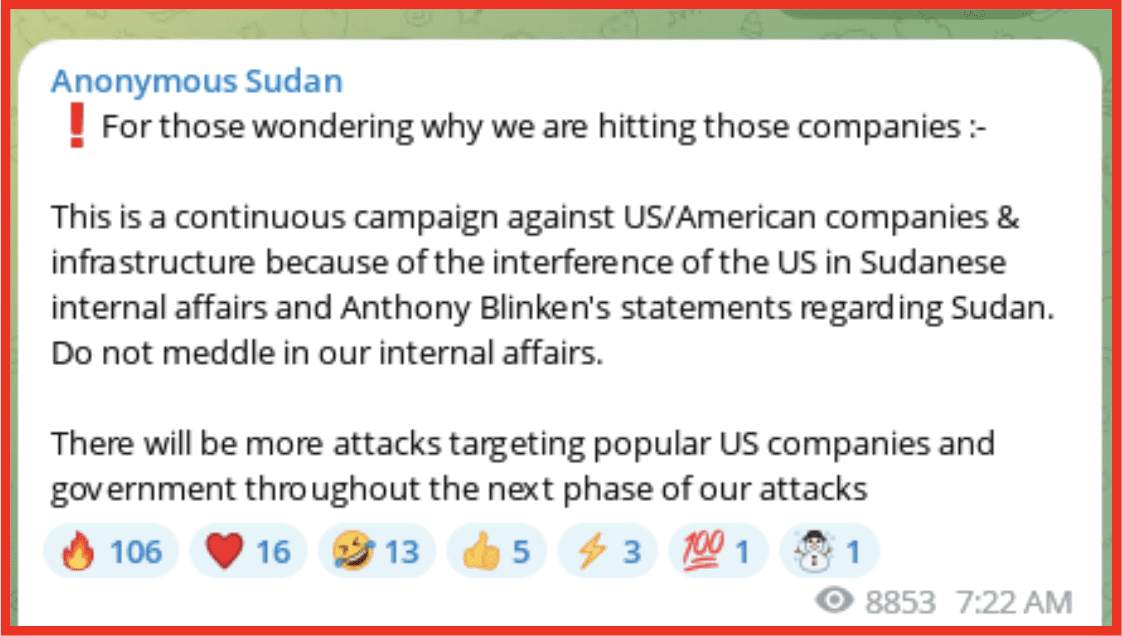
Figure 2: Anonymous Sudan Telegram channel
In response to the Hamas incursion into Israel, Anonymous Sudan pledged their support to Palestine and announced that they were attacking “some critical endpoints in the alert systems of Israel, which may affect the Iron Dome.” The post was made in English and Arabic, previously several posts have been in English and Russian. The group went on to target the Jerusalem Post, as well as “western” news outlets who it claimed were sharing fake news such as the New York Post, the Washington Post, and the Daily Mail. At the time of writing the attacks have predominantly been aimed at US corporations.

Figure 3: Anonymous Sudan Telegram channel
This group has shown capabilities that allow them to take high profile websites offline for varying periods of time. While they appear to be politically motivated and claim to be from Sudan, researchers have cast doubt on this highlighting why it is important to understand the motivations of a group, what activities they are conducting and how they are operating and who with. DarkOwl continues to track the activities of this group.
0XCee

Figure 4: Telegram ID for 0xCee
0XCee is an Initial access broker (IAB) who is active on Telegram. They use a bot on the Telegram channel in order to verify a user who wishes to join their channel is not a bot. This is a level of sophistication that most Telegram channel administrators do not exhibit.
The user is active on several telegram channels where they have participated in chats and shared information. DarkOwl analysts have been able to identify the user profile for the individual as well as their private channel used for selling access, building identifying information allows analysts to monitor the activity of threat actors.
Some of these channels have been used to advertise the access that the actors have, they provide specifics about the pricing as well as details of how many times they are willing to sell the access.
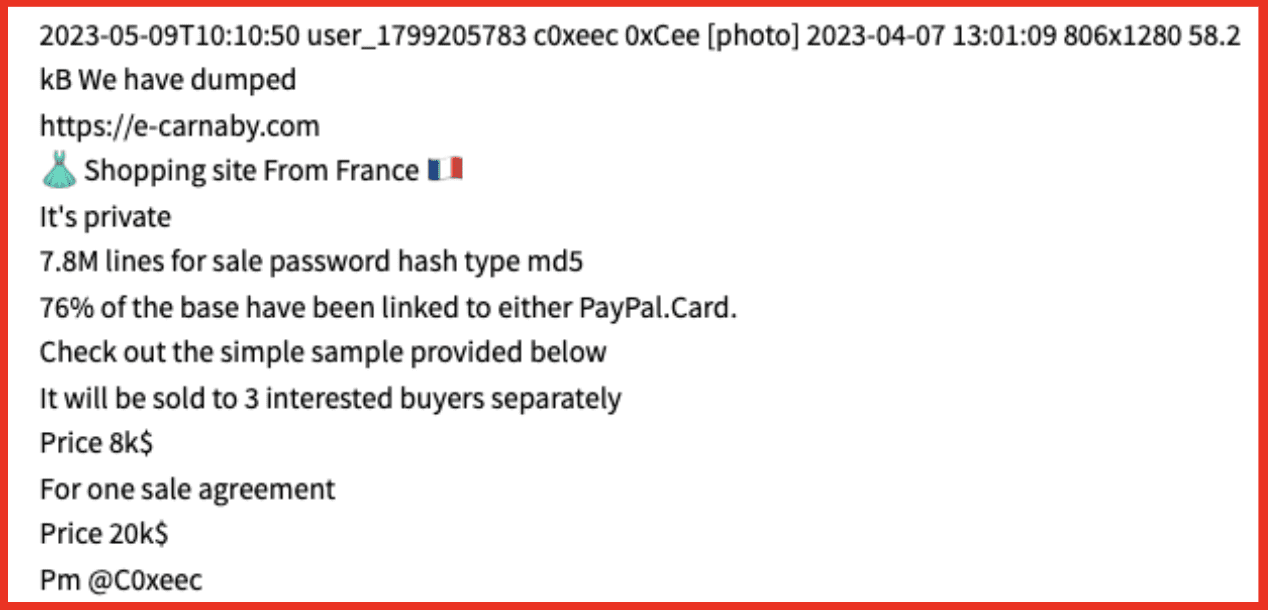
DarkOwl analysts have seen other Telegram users claim that some of the data that was purchased was old data and that they were not happy that they did not have the access that was advertised. 0xCee refused to provide any refunds on the data and insisted that it was used incorrectly. Reputation is very important in darknet markets, as most purchases are made on faith. Therefore, understanding these interactions can help analysts to make an assessment about the risk posed when an IAB advertises access to an organization.
APT Groups
Advances persistent threats (APT) are considered to be highly sophisticated threat actors, who usually operate over a prolonged period of time. The motivations of an APT can often dictate how they operate, with those committed to espionage trying to hide their activities, while those that are seeking to obtain intellectual property may be less concerned and those which are financially motived may publicize their activities through ransomware attacks such as the Lazarus group which was widely reported to be responsible for the WannaCry ransomware attacks in 2017.
While APT groups are difficult to track, generally identified via the TTPs they use rather than communications on darknet forums or platforms such as Telegram, it is possible to identify common signatures that they adopt which can assist with attribution. Identifying commonalities among victims can also assist analysts in identifying the origin of an APT as well as what their possible motivations are, this can also be assessed by reviewing what information has been accessed or exfiltrated.
DarkOwl analysts track the tools utilized by APT groups as well as details of victims and CVE’s and the dark web footprint of actors. Using open-source intelligence as well as our darknet collections details relating to these groups are tracked to assist analysts with their attribution efforts.
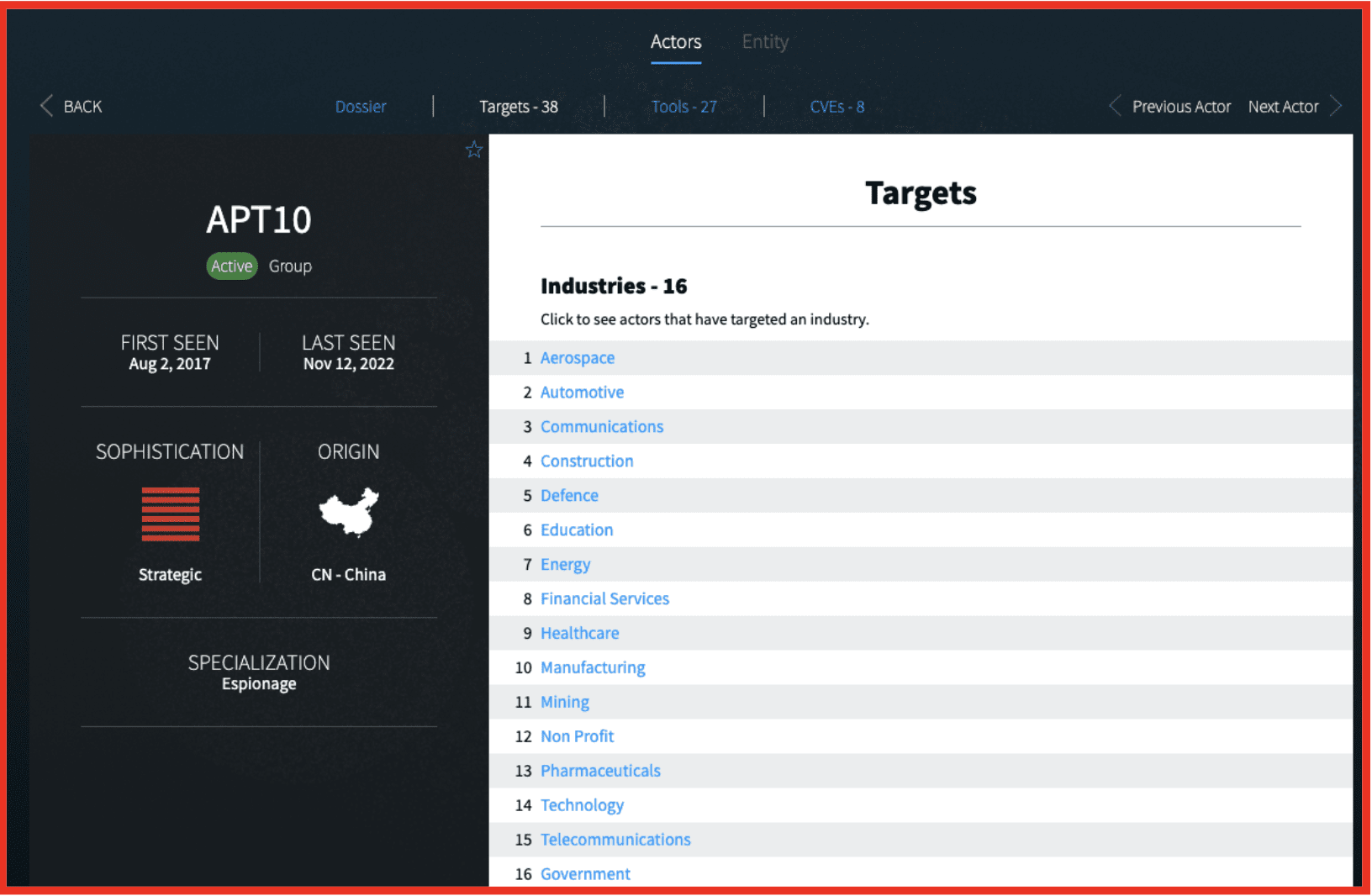
Figure 5: Screenshot of APT10 Threat Actor Group Profile in Actor Explore
Conclusion
True attribution is very difficult to achieve, and some Cyber Threat Intelligence Analysts would argue that it is not important. However, tracking available information about threat actors such as their motivations, TTPs, victims and activities can provide valuable intelligence which allows analysts to predict behavior and take proactive steps to protect their organizations.
DarkOwl sees the benefit of this information and have therefore created Actor Explore to provide our users with intelligence relating to threat actors active on the darknet, and the wider threat actor community. This latest feature is designed to empower security professionals, researchers, and organizations with analyst curated information about threat actors, enhancing their ability to understand and combat cybersecurity threats effectively.
To learn more about Actor Explore, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















