Threat Intelligence RoundUp: April
May 01, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Malicious PowerShell script pushing malware looks AI-written – Bleeping Computer

A March 2024 email campaign targeting German organizations was possibly authored by initial access broker TA547 AKA Scully Spider. The script loads the Rhadamanthys infostealer, which can steal cookies, browser and clipboard information, and more system metadata. As the security community studied the malicious code that is used in the script, they noted a hashtag used in coding comments, along with very verbose comments, indicating that AI or a non-human entity possibly authored the code. Read article.
2. U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks – The Hacker News
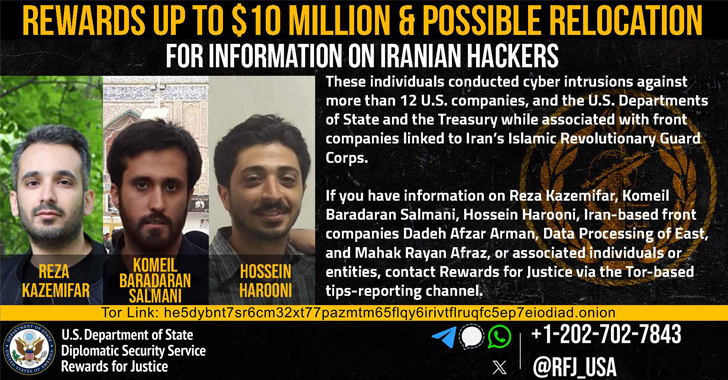
The US Treasury sanctioned several Iranian individuals and front companies who have been targeting the US on behalf of the Iranian Government. Their operations used spear phishing and social engineering to target US military veterans, US defense contractors, and other US government entities. Full article here.
3. UnitedHealth confirms it paid ransomware gang to stop data leak – Bleeping Computer
United Health publicly admitted that they paid BlackCat/AlphV ransomware actors in February 2024 to prevent the sale of private healthcare data to criminal actors. Payment activity was confirmed by the public transaction on the blockchain as a Bitcoin payment to the wallet used by BlackCat ransomware gang was visible. Read article.
4. Indian Government Rescues 250 Citizens Forced into Cybercrime in Cambodia – The Hacker News

India’s government issued a public statement and update about the rescue of 250 Indian nationals who went to Cambodia under the pretense of employment but were then forced to participate in cybercrime. In what some dubbed “cyber slavery”, organized crime groups are luring people to Cambodia and other countries with false employment opportunities, and then forcing them to create thousands of social media accounts to use for various purposes, such as gambling, crypto fraud, romance schemes, and more. If the trapped individuals didn’t meet their quota of accounts created, the cybercrime groups denied them food and sleep. Other hotspots observed for this kind of activity include Myanmar, Thailand, and the Philippines. Read more.
5. DPRK hacking groups breach South Korean defense contractors – Bleeping Computer

Targeting technological information, North Korean hacking groups including Lazarus and Kimsuky used extant vulnerabilities to plant malware that sent data back to their cloud servers and was used by the North Korean government. One group accessed the account of an employee who worked with defense subcontractors, while another took advantage of an email server vulnerability. Read more.
6. US Health Dept warns hospitals of hackers targeting IT help desks – Bleeping Computer
The US Department of Health and Human Services issued a public warning this week, concerning social engineering techniques used by threat actors to go after IT desks of the health sector. In these operations, threat actors will call health organizations using a local number of the area they are targeting. They’ll provide details of the organization which are stolen, providing actual corporate ID and/or social security numbers procured in malicious cyber operations. By providing this real information to the IT department, they appear legitimate and then the helpdesk enrolls the threat actor device into corporate multi-factor authentication, allowing deep access to corporate information. Malicious actors then change ACH information regarding payments gain access to corporate email accounts and continue social engineering. Read more.
7. Russia charges suspects behind theft of 160,000 credit cards – Bleeping Computer

Six Russian individuals were recently charged by the Russian Prosecutor General’s Office. The men were charged with skimming 160,000 carss — using malware to steal credit card and other payment details – throughout the past seven years. The group didn’t use the stolen cards instead selling them on various dark web platforms for profit. Article here.
8. Cybercriminals Targeting Latin America with Sophisticated Phishing Scheme – The Hacker News
ZIP files are currently being used to deliver malicious files which appear as an invoice, targeting Spanish-speakers in LATAM. The files redirect the user to another domain, newly set up by the malicious actors. This redirection activates a script that then takes metadata from systems and checks for anti-virus software, collecting system information to use and further malicious operations. Read article here.
9. Scammers offer cash to phone carrier staff to swap SIM cards – SC Media
Cyber actors are cold-contacting employees of various US cell phone companies and offering them cash in exchange for their participation in SIM swapping operations. In SIM swapping incidents, actors fool a wireless carrier, such as Verizon or T-Mobile (who were both targeted in this latest campaign) into rerouting services to a device controlled by the criminals themselves. Once the “swap” is completed, the victims lose access to most personal accounts and personal data attached to the cell phone account is also stolen and used in other malicious operations. Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















