Threat Intelligence RoundUp: June
July 03, 2023
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Car pentesting growing in importance as autos become more connected – IT Brew
The world is becoming more and more tech-centric, and that includes the automotive industry. This shift in car technology demands that cars become more secure, in the tech and cyber sense. This article highlights the importance of penetration testing (pentesting) for electronic control units (ECUs) to secure them against hackers. Read full article.
2. Swiss government warns of ongoing DDoS attacks, data leak – BleepingComputer
On June 12, the Swiss government announced that one of their IT suppliers had been a victim of a ransomware attack and that their data may have been impacted. They then warned that they are not a target in DDoS attacks. These attacks highlight the complex third-party environments almost all organizations and government entities face. Read more.
3. EncroChat takedown led to 6,500 arrests and $979 million seized – BleepingComputer

Last week, Europol announced that they had arrested over 6,600 people and seized $979 million in illicit funds. This came after that the takedown of the EncroChat encrypted mobile communications platform. Learn more.
4. APT37 hackers deploy new FadeStealer eavesdropping malware – BleepingComputer
APT37, also known as StarCruft, Reaper, or RedEyes, is a state-sponsored North Korean hacking group who has a history of cyber espionage attacking North Korean defectors, educational institutions and EU-based organized that do not align with the North Korean government interests. They are believed to be using a new “FadeStealer” information-stealing malware which has a “wiretapping” feature. This feature allows them to listen and record from their victim’s microphones. Read full article.
5. New ‘PowerDrop’ PowerShell malware targets U.S. aerospace industry – BleepingComputer
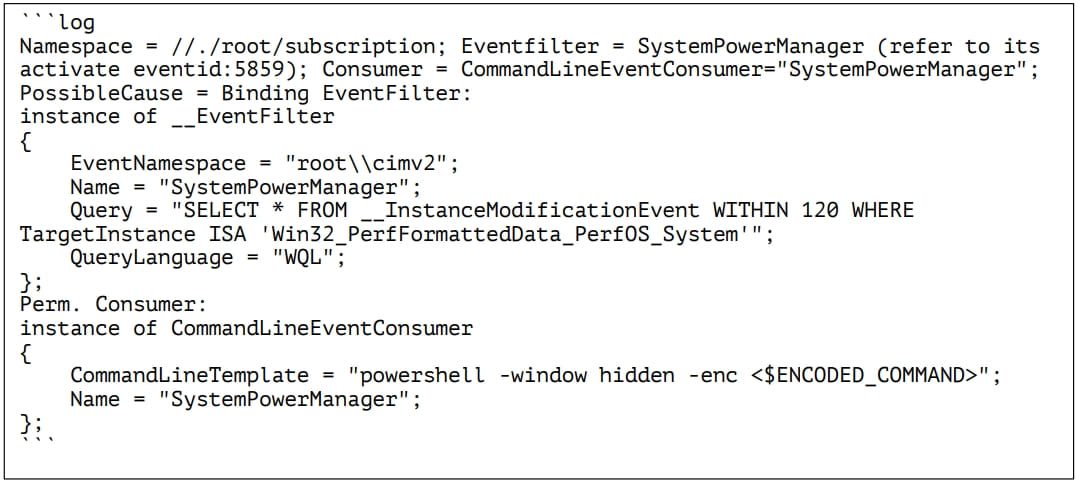
Adlumin discovered a new PowerShell malware script named “PowerDrop.” It was discovered being used in attacks against the U.S. aerospace defense industry, when a sample of the malware was found in a U.S. defense contractor’s network. Read more.
6. Chinese Hacker Group ‘Flea’ Targets American Ministries with Graphican Backdoor – The Hacker News
A Chinese state-sponsored actor, Flea, (also known as APT15, BackdoorDiplomacy, ke3chang, Nylon Typhoon (formerly Nickel), Playful Taurus, Royal APT, and Vixen Panda) has been targeting foreign affair ministries in the Americas from late 2022 into early 2023. The group is linked to cyberattacks targeting governments, diplomatic missions and embassies since at least 2004. Read full article.
7. SmokeLoader Malware Adopts New Tactics, Raises Serious Security Concerns – The Cyber Express
At the beginning of June, the Computer Emergency Response Team of Ukraine (CERT-UA) uncovered a new cyberattack campaign named UAC-0006 that involved distributing SmokeLoader malware, using compromised email accounts and using multiple delivery methods. This attack is a sign of TTP changes and expansion Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















