Threat Intelligence RoundUp: December
January 06, 2026
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Bloody Wolf Threat Actor Expands Activity Across Central Asia – InfoSecurity Magazine
The threat actor group, Bloody Wolf, has been observed using remote-access software to infiltrate government targets throughout Central Asia. Cybersecurity researchers claim the group has shifted from traditional malware to “a streamlined Java-based delivery method”. Reports claim the group has been operating a sustained campaign in Kyrgyzstan since June 2025 and recently began targeting Uzbekistan. By using counterfeit PDF documents, spoofed web domains, and fraudulent emails to pose as the country’s Ministry of Justice, the group has manufactured an air of legitimacy that has facilitated their access. Once a victim opens the downloaded JAR file, the loader retrieves additional components and installs NetSupport RAT for remote control. Read full article.
2. Poland arrests Ukrainians utilizing ‘advanced’ hacking equipment – Bleeping Computer
Three Ukrainians, claiming to be IT specialists, were arrested by Polish police while traveling through Europe. During a routine traffic stop, officers conducted a search of the threat actor’s vehicle, discovering suspicious items that could be “used to interfere with the country’s strategic IT systems, breaking into IT and telecommunications networks”. The seized equipment included “spy device detector, advanced FLIPPER hacking equipment, antennas, laptops, a large number of SIM cards, routers, portable hard drives, and cameras.” The data seized was encrypted but according to officers from Poland’s Central Bureau for Combating Cybercrime (CBZC) claim to have been able to collect evidence. Article here.
3. Chinese Hackers Have Started Exploiting the Newly Disclosed React2Shell Vulnerability – The Hacker News

Hours after CVE-2025-55182 was made public, Amazon Web Services (AWS) observed two different Chinese hacking groups, Earth Lamia and Jackpot Panda, beginning to weaponize the vulnerability. CVE-2025-55182, aka React2Shell, allows unauthenticated remote code execution in React Server Components (RSC). Using automated scanning tools, these threat actors have been observed exploiting additional vulnerabilities including CVE-2025-1338. AWS identified Earth Lamia due to the use of previously used infrastructure the group had demonstrated earlier in the year. This situation highlights threat actors systematic approach in abusing vulnerabilities quickly and learning to scan for common vulnerabilities. Read more here.
4. FCC Warns of Hackers Hijacking Radio Equipment For False Alerts – InfoSecurity Magazine
On November 26, the Federal Communications Commission (FCC) announced threat actors had been hijacking US radio transmission equipment and broadcasting fake emergency tones and offensive material. Several stations in Texas and Virginia were targeted, resulting in broadcasts being disrupted by emergency signals, alert tones, and obscene language. The threat actors targeted Barix network audio devices and reconfigured them to capture attacker-controlled streams. The FCC reports that the incidents stemmed from unsecured equipment, noting that some stations did not discover the compromise until after the attacks and were seemingly unaware as they unfolded. Read here.
5. CISA warns of Chinese “BrickStorm” malware attacks on VMware servers – Bleeping Computer

U.S. Cybersecurity and Infrastructure Security Agency (CISA) warn of Chinese hackers backdooring VMware vSphere servers with BrickStorm. Malware samples analyzed by the National Security Agency (NSA) and Canada’s Cyber Security Centre were found on victim networks in which the attackers had specifically targeted VMware vSphere environments. One of the incidents showed the threat actors compromising a web server in an organization’s demilitarized zone (DMZ) in April 2024, then moved laterally to an internal VMware vCenter server and deployed malware. Learn more.
6. Glassworm malware returns in third wave of malicious VS Code packages – Bleeping Computer

First emerging in October, the Glassworm campaign, has released 24 new packages distributing malware to OpenVSX and Microsoft Visual Studio. According to Koi Security, Glassworm malwares uses “invisible Unicode characters to hit its code”. Following previous detection, Glassworm evolved technically, using Rust-based implants packaged inside extensions as well as invisible Unicode. Once the malware is installed it attempts to steal GitHub, npm, and OpenVSX accounts, as well as cryptocurrency wallet data from 49 extensions. Additionally, the malware deploys a SOCKS proxy to route malicious traffic and give operators stealthy remote access. Read full article.
7. React2Shell flaw exploited to breach 30 orgs, 77k IP addresses vulnerable – Bleeping Computer
On December 03, React disclosed the vulnerability, CVE-2025-55182 aka React2Shell, detailing “that unsafe deserialization of client-controlled data inside React Server Components enables attackers to trigger remote, unauthenticated execution of arbitrary commands.” React2Shell is a security flaw that allows attackers to run code on a server without logging in. It can be triggered with just one HTTP request and affects any framework that uses React Server Components, including Next.js. Over 77K internet exposed IP addresses are vulnerable to React2Shell and researchers believe 30 organizations are already compromised. Read full article.
8. RomCom Uses SocGholish Fake Update Attacks to Deliver Mythic Agent Malware – The Hacker News
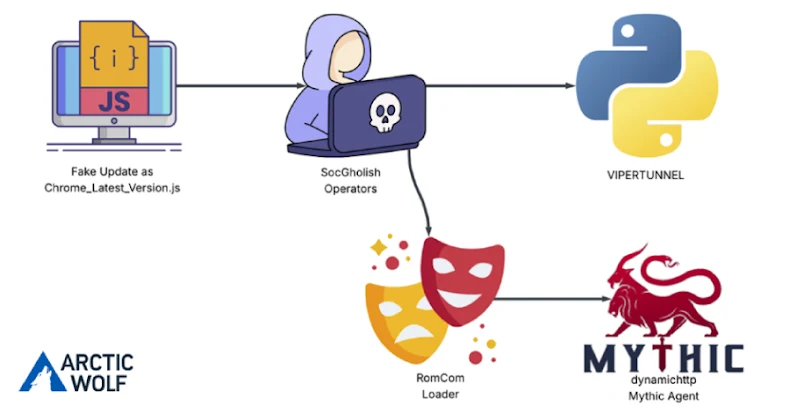
The malware group RomCom has been observed using the JavaScript loader, SocGholish, to target U.S. based civil engineering company. By targeting poorly secured websites, the group injects fake Google Chrome or Mozilla Firefox update alerts into otherwise legitimate but compromised pages. These alerts trick users into downloading malicious JavaScript that installs a loader, which then retrieves additional malware. According to Arctic Wolf researchers, this allowed the threat actors to execute commands on the compromised host through a reverse shell connected to the command-and-control (C2) server, enabling activities such as system reconnaissance and deployment of a custom Python backdoor known as VIPERTUNNEL. Learn more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















