Threat Intelligence RoundUp: February
March 01, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys Released – The Hacker News

LockBit ransomware was taken offline by a global law enforcement operation as of February 20, 2024. The National Crime Agency of the UK led the operation, obtaining LockBit’s source code, arresting two members of the ransomware gang, and freezing 200 cryptocurrency accounts related to LockBit operations. Read full article.
2. FBI seizes Warzone RAT infrastructure, arrests malware vendor – Bleeping Computer

The FBI have seized four domains connected to the Warzone RAT, a commodity malware which offered a number of features including UAC bypass, hidden remote desktop, cookie and password stealing, keylogging, webcam recording and remote shell among others. They also arrested, in conjunction with Malta Police, an individual they said was behind the RAT as well as an individual based in Nigeria.
The individual based in Malta was also reported to have sold the Pegasus RAT for the Skynet corporation. Read article.
3. Bumblebee Malware Buzzes Back on the Scene After 4-Month Hiatus – Dark Reading
Bumblebee is a malware loader which is believed to have been developed by Conti and Trickbot groups. Recent reporting indicates that is has been used to target thousands of organizations in the US in phishing campaigns. According to security researchers the malware is commonly distributed in phishing campaigns to drop additional payloads for initial network access and to conduct ransomware attacks. The use of the malware has not yet been attributed to a specific group. Article here.
4. Russian Hackers Target Ukraine with Disinformation and Credential-Harvesting Attacks – The Hacker News
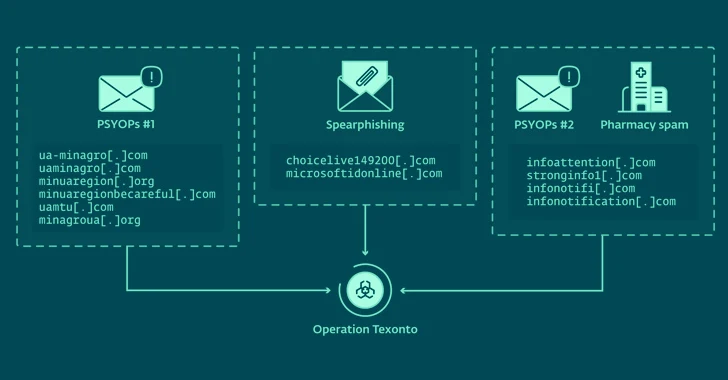
Two years after the Russian invasion of Ukraine, cyber activity remains a crucial part of Russian warfare. While no specific Russian actor has been identified, the latest operation, occurring between November and December 2023, involved spear-phishing emails sent to harvest Microsoft login credentials. Content included in the campaign now includes PDF attachments related to food and supply shortages, heating issues, and other war/conflict disinformation. Article here.
5. Chinese Hackers Exploited FortiGate Flaw to Breach Dutch Military Network – The Hacker News

Continuing their world-wide efforts to infiltrate government, military, and key sources of intel, China exploited an extant Fortinet vulnerability (CVE-2022-42475) to deploy a backdoor named COATHANGER and gain access to a network used by the Dutch military. This is the first time the Dutch have publicly attributed a cyber incident to Chinese actors. Read article.
6. ‘ResumeLooters’ Attackers Steal Millions of Career Records – Dark Reading
Using legitimate, open-source pen-testing tools combined with XSS and SQL injection techniques, a threat actor group stole millions of email addresses, phone numbers, and other pieces of personal data and put them up for sale throughout several Chinese-speaking Telegram channels. The specifically targeted sector was retail, along with multiple general employment websites. Read full article.
7. Johnson Controls says ransomware attack cost $27 million, data stolen – Bleeping Computer
Industrial control systems and security equipment giant Johnson Controls was the victim of a ransomware attack with a detrimental cost of $27 million dollars. The offices located throughout Asia were the entry point for the malicious actors, who then spread through their entire corporate network; this event did negatively impact customer facing systems, in addition to the loss of 27 TB of corporate information. Article here.
8. New Report Reveals North Korean Hackers Targeting Defense Firms Worldwide – The Hacker News
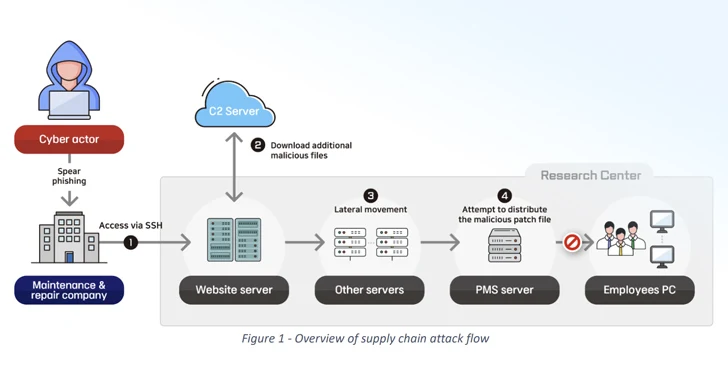
North Korean actors are conducting a cyber espionage campaign gaining access to defense technologies. Actors create fake profiles on LinkedIn and build trust with contacts, and then offer possible job opportunities and exercises which are documents containing malware. Additionally, supply chain attacks play a large part in these operations as well, with North Korean actors deploying remote control malware. Read full article here.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















