Threat Intelligence RoundUp: January
February 01, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. China claims it cracked Apple’s AirDrop to find numbers, email addresses – BleepingComputer

China claims to have decrypted device logs for Airdrop, the apple tech that allows for proximity sharing of pictures, files, etc. China’s constant effort to control its population means they’ve blocked many popular messaging apps, as well as used their internet controls to block many popular websites within China. Many Chinese citizens moved to Airdrop as it doesn’t need cell service. This use included the 2019 protests where Chinese citizens used Airdrop to share protest information and anti-Chinese government material. The Chinese government claims they can see the phone numbers, emails, and other metadata from devices who partook in this activity. Read full article.
2. 29-Year-Old Ukrainian Cryptojacking Kingpin Arrested for Exploiting Cloud Services – The Hacker News
A 29-year-old male was arrested in Mykolaiv, Ukraine after making over two million dollars in profits running cryptojacking schemes. The arrest was the result of collaboration between Europol and a top cloud service provider. The attacker most likely used compromised credentials to install miners without the victim’s knowledge. Read article.
3. SMTP Smuggling: New Flaw Lets Attackers Bypass Security and Spoof Emails – The Hacker News
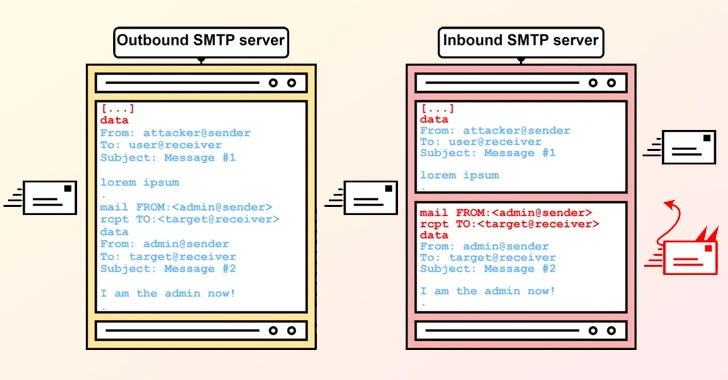
SMTP smuggling has emerged as a way to conduct targeted phishing operations. SMTP is a common protocol used to send email. A protocol is simply a system of rules and guidelines used to communicate data. For email, a connection is established between the sender and recipient, and this connection sends the email content using the established rules (the protocol). In this new smuggling process, actors are using inconsistencies between the sender and receiver, which allows for spoofing domains. An actor could send an illegitimate email with a malicious attachment, and it would go through due to some inconsistencies between sending and receiving servers processing methods. Read full article.
4. DDoS Attacks on the Environmental Services Industry Surge by 61,839% in 2023 – The Hacker News
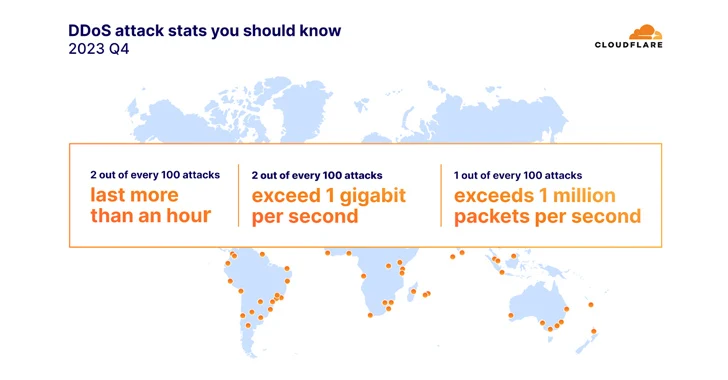
Distributed denial of services (DDoS) attacks had a record increase in 2023, targeting the environmental sector. This pattern solidifies the growing trend of cyber issues impacting real world, environmental matters and causing disturbances/interruptions in the sector which impact the day-to-day lives of average citizens. Several firms in the industry detailed how DDoS trends indicate more sophisticated attacks targeting multiple vectors, lasting longer, and focusing on multiple IP destinations in the same event. Article here.
5. Malware Using Google MultiLogin Exploit to Maintain Access Despite Password Reset – The Hacker News

A Google endpoint exploit is allowing for hijacked sessions and continuous access to Google services by extracting tokens and account IDs. Having this information then allows for the regeneration of Google authentication cookies, which enables threat actors to input them and remain in access to user accounts. Read article.
6. Ransomware victims targeted by fake hack-back offers – BleepingComputer
An actor claiming to be a security researcher has recently contacted several victims of ransomware gangs and offered revenge services against members of Royal and Akira ransomware. The individual offered victims the chance for them to delete the stolen data located on the servers of Akira and Royal for the cost of five Bitcoin. The handles used by the actor are “Ethical Side Group” and “xanonymoux”. Read full article here.
7. Majorca city Calvià extorted for $11M in ransomware attack – BleepingComputer

Majorca city announced it was hit by a ransomware attack that negatively impacted municipal services, suspending deadlines and other offerings for personnel until January 31, 2024. A task force of IT specialists is helping the city recover from the incident, with city officials reminding the population that phone and in-person services are all available and unaffected. Read article.
8. BreachForums Founder Sentenced to 20 Years of Supervised Release, No Jail Time – The Hacker News
Conor Brian Fitzpatrick, aka pompompurin, the founder of cybercrime hotspot BreachForums, was sentenced to supervised house release for his illicit online activities. 21-year-old Fitzpatrick also operated Leaks Market and sold data bases with social security numbers, passwords, and other PII to use in criminal operations. In addition to GPS monitored house arrest, he must register as a sex offender. The full dollar amount he will have to pay to the numerous victims is still being determined by courts of law. Article here.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















