Threat Intelligence RoundUp: July
August 01, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. AT&T Confirms Data Breach Affecting Nearly All Wireless Customers – The Hacker News

On July 12th, AT&T confirmed that it had suffered a data breach affecting “nearly all” of its wireless customers between April 14th and April 25th, 2024. The leaked files contain records of customers’ calls and texts which occurred on January 2nd, 2023, and between approximately May 1st and October 31st of 2022. The leak also included customers of mobile virtual network operators (MVNOs). The data was stolen from the company’s workspace and on a cloud platform. This data does not appear to have been made publicly available at this time. Full article here.
2. GuardZoo Malware Targets Over 450 Middle Eastern Military Personnel – The Hacker News
Military personnel in the Middle East have been targeted by GuardZoo malware, an Android data-gathering tool. Over 450 victims across Egypt, Oman, Qatar, Saudi Arabia, Turkey, the U.A.E., and Yemen have been impacted by the surveillanceware operation, with the majority of victims located in Yemen. GuardZoo is a modification of Dendroid RAT malware which targets Android OS and was first discovered in 2014. Read more.
3. 4 FIN9-linked Vietnamese Hackers Indicted in $71M U.S. Cybercrime Spree – The Hacker News
Four Vietnamese Fin9 actors were indicted for cybercrime activity between May 2018 and October 2021. They conducted phishing campaigns, social engineering and supply chain attacks that resulted in data theft. In some instances, FIN9 used personally identifiable information (PII) to create fake accounts “tied” to victims from the first stage of their operations, conducting cybercrime from assumed identities.. Article here.
4. US disrupts AI-powered bot farm pushing Russian propaganda on X – BleepingComputer

On July 9th, the U.S. Department of Justice announced the disruption of a Russian, AI-powered information operation devised to spread Russian propaganda in the United States and abroad. The DOJ operation involved the seizure of two domains used to issue emails for the bot accounts, as well as the search of nearly 1,000 social media bot accounts which were subsequently suspended on X (formerly Twitter). According to the DOJ press release, the bot farm was developed by the deputy editor-in-chief of RT (formerly Russia Today), the state-controlled news organization. Court documents also reveal the use of artificial intelligence to enhance the Russian bot farm, reflecting the increasingly normalized use of AI in disinformation operations. Read article.
5. Fake CrowdStrike fixes target companies with malware, data wipers – BleepingComputer
On July 19, the cybersecurity company CrowdStrike distributed a faulty software update to its customers; the update affected devices running Windows, and an estimated 8.5 million computers worldwide were disabled. The incident—which grounded thousands of flights and affected a variety of industries, including the healthcare sector—is believed to be one of the worst cyber incidents of all time. Threat actors quickly took advantage of the worldwide disruptions by impersonating CrowdStrike in phishing emails to distribute malware. Full article here.
6. LockBit lied: Stolen data is from a bank, not US Federal Reserve – BleepingComputer
At the end of June 2024, LockBit ransomware group claimed they hacked the US Federal Reserve. However, further analysis of the data, which LockBit published on their website, proved that in reality, LockBit hacked Evolve Bank and Trust, an entity not at all tied to the US Federal Reserve. When approached, Evolve Bank and Trust admitted they were investigating a cybersecurity incident, but provided no additional details or confirmation. Full article.
7. Ukrainian Institutions Targeted Using HATVIBE and CHERRYSPY Malware – The Hacker News
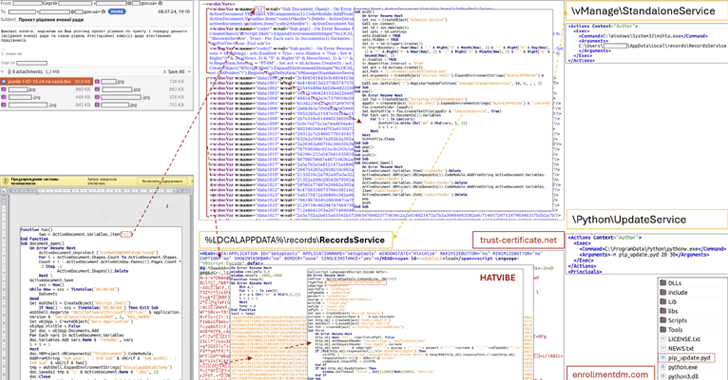
Ukraine’s Computer Emergency Response Team (CERT-UA) revealed that a Ukrainian research institution has been targeted by HATVIBE and CHERRYSPY malware distributed in a spear-phishing campaign. CERT-UA has attributed the attack to UAC-0063, which it previously identified as targeting state bodies in Ukraine. CERT-UA shared that it is aware of multiple cases of HATVIBE infections. According to previous research, the threat actor UAC-0063 has been linked with moderate confidence to APT28, the Russian GRU-backed threat actor. Read more.
8. U.S. indicts Russian GRU hacker, offers $10 million reward – BleepingComputer
The U.S. indicted 22-year-old Russian national Amin Timovich Stigal for allegedly assisting Russia’s military intelligence service’s “WhisperGate” cyberattack by distributing malware to Ukrainian government computer networks a month prior to the invasion of Ukraine. Stigal targeted non-military systems and attempted to sow doubt in the Ukrainian government by publishing citizen data. According to the federal indictment, Stigal also targeted countries that supported Ukraine, including the United States. The U.S. Department of State’s Rewards for Justice program is offering $10 million to locate the GRU hacker, who remains at large. Read here.
9. Microsoft links Scattered Spider hackers to Qilin ransomware attacks – BleepingComputer

According to Microsoft, the cybercrime group Scattered Spider has added RansomHub and Qilin ransomware to its arsenal and has begun utilizing them in its attacks. Scattered Spider was identified in early 2022 and is also known as Octo Tempest, UNC3944, and 0ktapus. RansomHub ransomware was first observed in February of 2024 and is believed to be a rebrand of the ransomware strain “Knight.” Qilin ransomware, meanwhile, first emerged in August of 2022 and was initially referred to as “Agenda.” Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















