Threat Intelligence RoundUp: March
April 01, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. LockBit ransomware re-emerges after law enforcement takedown – The Hacker News
Proving resilient, LockBit ransomware came back into operation using new infrastructure just days after a global law enforcement operation took them offline. The actors debuted a new onion address and already had 12 new victims in their post-takedown operations. Additionally, the actors themselves authored a long note explaining what happened from their perspective. Read full article.
2. ALPHV/BlackCat ransomware group exit scams – The Hacker News

One of the most active ransomware groups of the past few years, ALPHV/BlackCat, shut down their onion site after their latest big victim, UnitedHealth’s Change Healthcare unit, purportedly paid their $22 million ransom. Actors believed to be a part of the gang engaged in conversation on Russian forum RAMP. Read article.
3. US government agencies are impersonated in business email compromise attacks – SC Media
US government agencies have been impersonated in business email compromise (BEC) attacks. The Department of Transportation, Department of Agriculture, and the Small Business Administration have all faced QR codes circulating in PDF documents. The QR codes send victims to phishing sites mimicking portals for the aforementioned agencies. All PDF’s had the same metadata, which indicated creation in Nigeria. Article here.
4. Iranian actors observed targeting aerospace and aviation industries in the Middle East – The Hacker News
Malicious Iranian cyber activity was observed targeting various industries using cloud infrastructure for their command and control (C2) along with social engineering tactics to deliver two backdoors named Minibike and Minibus. Targeting these industries allows for strategic information to be procured and sent back to the Iranian government. Article here.
5. Darknet marketplace Nemesis Market seized by German police – Bleeping Computer

German authorities, using intelligence from Lithuanian and American agencies and partners, captured infrastructure in both Germany and Lithuania, resulting in the take down of popular dark web Nemesis Market. Authorities seized $100,000 in cash as well as digital infrastructure that supported the illicit goods market. No information was provided regarding the status of the platform’s operators being arrested or contacted as of the time of this writing; DarkOwl will continue to monitor for updates. Read article.
6. Cybercrime gangs join forces to launch double extortion ransomware attacks – The Hacker News
GhostSec and Stormous ransomware groups have combined their operations to conduct ransomware attacks against technology, education, government, and many more verticals. Both groups are part of “The Five Families.” In August of 2023, cybercrime conglomerate SiegedSec announced the formation of “The Five Families” to attempt to offer structure to the digital criminal underground on August 28. They named ThreatSec, GhostSec, Stormous, Blackforums, and themselves as the five participants. Read full article.
7. China’s “Earth Krahang” infiltrates organizations throughout 45 countries – Bleeping Computer
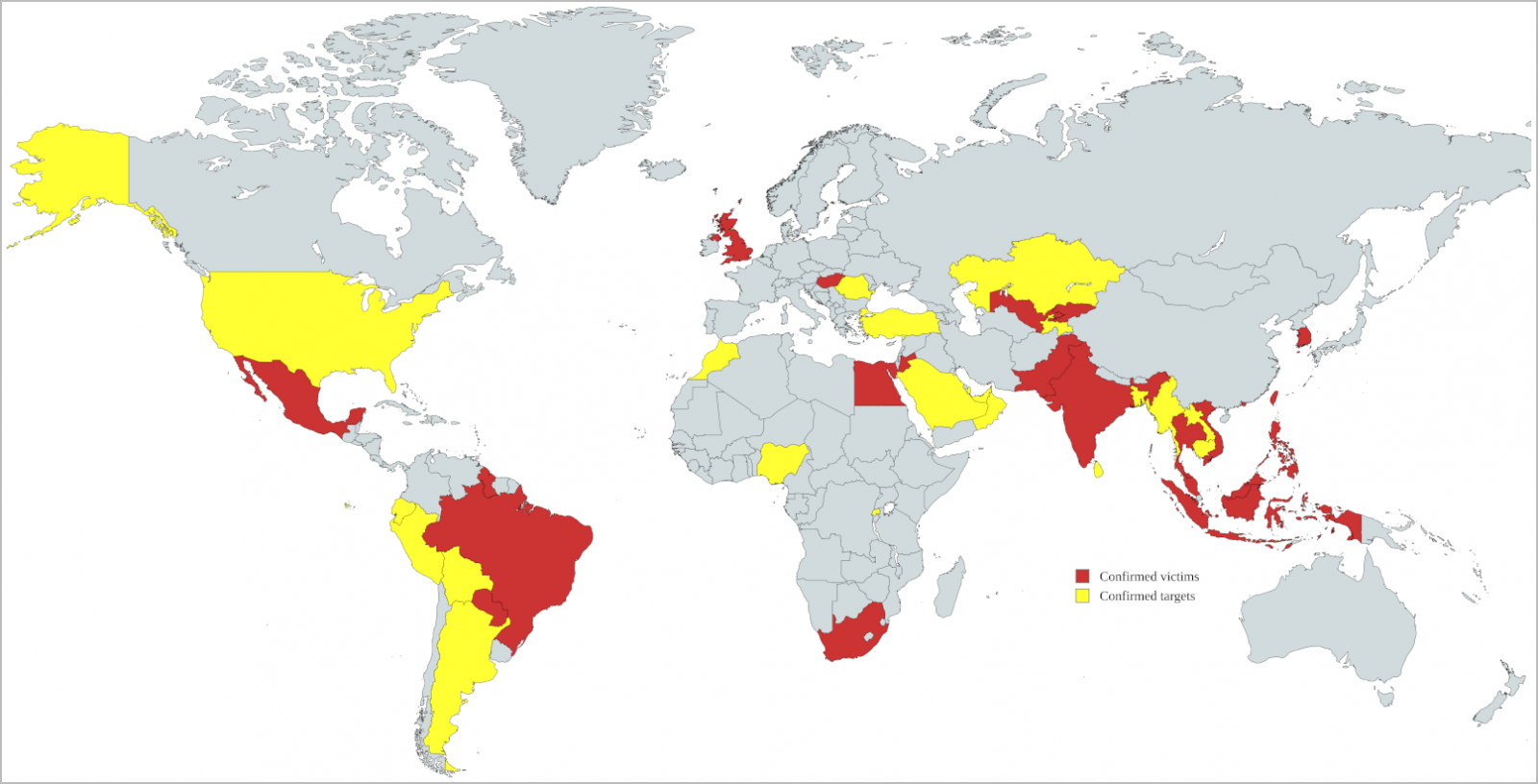
Government organizations worldwide were the target of a two-year, Chinese state-sponsored campaign. Spear-phishing is employed to deploy backdoors while exposed internet-facing servers are also attacked, leading to a multi-pronged attack. The group uses open-sourced tools to build VPN servers and then brute-forces email accounts to procure passwords, focusing on compromised Outlook accounts. Article here.
8. Microsoft source code accessed by Russian actors Cozy Bear – CyberScoop
As of January 2024, Russian state-sponsored actors Cozy Bear (who are believed to be part of Russia’s SVR intelligence branch) accessed Microsoft source code and company systems. The actors were able to read the emails of senior Microsoft executives. While the exact nature of this infiltration is still under investigation, Microsoft offered that they do not believe customer-facing systems were accessed/impacted. Read full article here.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















