Threat Intelligence RoundUp: March
April 01, 2025
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. This Data Could Destroy The FBI—Russian Crime Gang Warns Kash Patel – Forbes
In a February 25 post on their dark web leak site, the Russian ransomware gang LockBit claimed to have stolen data from the Federal Bureau of Investigation (FBI). The post directly addresses new FBI Director Kash Patel and claims that the ransomware gang has “an archive of classified information” that would “negatively affect the reputation of the FBI [and] destroy it as a structure.” The message prompts FBI Director Patel to contact LockBit personally in order to gain access to the password-protected file included in the post. Read full article.
2. Police arrests 300 suspects linked to African cybercrime rings – Bleeping Computer

In a March 24 press release, INTERPOL announced the arrest of 306 suspects and the seizure of 1,842 devices as part of the INTERPOL-led operation “Red Card,” which aims to “disrupt and dismantle cross-border criminal networks.” The arrests were carried out in Benin, Côte d’Ivoire, Nigeria, Rwanda, South Africa, Togo, and Zambia. Operation Red Card, which took place between November 2024 and February 2025, specifically targeted “mobile banking, investment, and messaging app scams,” which involved more than 5,000 victims. Article here.
3. X hit by ‘massive cyberattack’ amid Dark Storm’s DDoS claims – Bleeping Computer

On March 10, X (formerly known as Twitter) suffered multiple worldwide outages. The hacktivist group Dark Storm has claimed responsibility for the distributed denial-of-service (DDoS) attacks which caused the outages. Specifically, the group made posts on their Telegram channel the same day the attacks took place and shared screenshots from check-host.net as proof of the attack. Tens of thousands of users were impacted by the outages. Read more here.
4. Ukrainian military targeted in new Signal spear-phishing attacks
– Bleeping Computer

In a March 18 bulletin, Ukraine’s Computer Emergency Response Team (CERT-UA) warned of numerous cases of targeted cyberattacks against employees within Ukraine’s defense industry and members of the Armed Forces of Ukraine (AFU). According to the report, in March 2025 threat actors were observed using compromised Signal accounts to distribute malware. The phishing messages contained a PDF and an executable file classified as the DarkTortilla cryptor, “which, when launched, decrypts and executes the remote access trojan Dark Crystal RAT (DCRAT). Read here.
5. Police arrests suspects tied to AI-generated CSAM distribution ring – Bleeping Computer
In a February 28 press release, Europol announced the arrest of 25 suspects who were part of a criminal group “engaged in the distribution of images of minors fully generated by artificial intelligence.” The global operation—dubbed “Operation Cumberland”—was led by Danish law enforcement and involved authorities from 19 countries. In addition to the 25 arrested suspects, the operation also identified 273 suspects, conducted 33 house searches, and seized 173 electronic devices. Learn more.
6. Cyberattack takes down Ukrainian state railway’s online services – Bleeping Computer
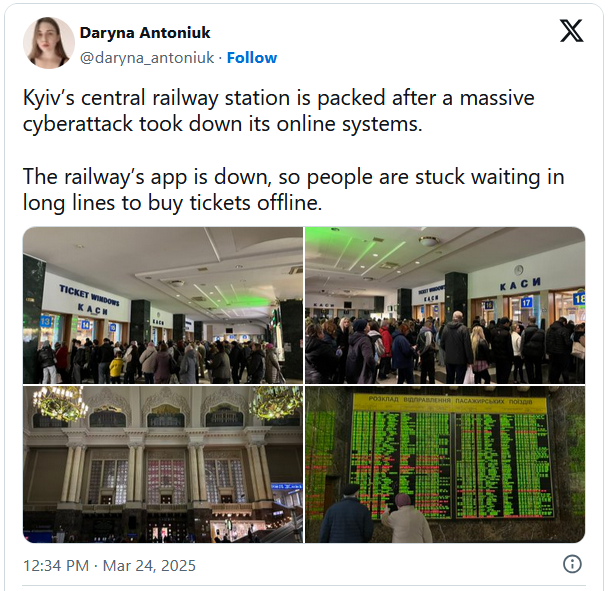
On Sunday, March 23, Ukraine’s national railway operator Ukrzaliznytsia was targeted in a “systematic, complex, and multi-level” cyber-attack. The attack disrupted the company’s online services, preventing users from purchasing tickets. Railway operations themselves were not impacted by the intrusion, however the hit to online systems resulted in long waiting times, delays, and overcrowding. Read full article.
7. Vo1d Botnet’s Peak Surpasses 1.59M Infected Android TVs, Spanning 226 Countries – The Hacker News
According to researchers at Xlab, nearly 1.6 million Android TV devices have been infected with a new and improved variant of the Vo1d malware botnet. 226 countries have been targeted in the campaign, with Brazil, South Africa, and Indonesia accounting for the largest number of infections (24.97%, 13.6%, and 10.54% respectively). Xlab has been tracking the campaign since November, 2024, and has reported that the botnet peaked on January 14, 2025. The new variant currently encompasses 800,000 daily active IP addresses. Read full article.
8. BADBOX 2.0 Botnet Infects 1 Million Android Devices for Ad Fraud and Proxy Abuse – The Hacker News

Over 1 million devices have been impacted in a fraud operation dubbed “BADBOX 2.0,” an expansion of the previous BADBOX operation discovered in 2023. As noted in the Satori Threat Intelligence report, “BADBOX 2.0 is the largest botnet of infected connected TV (CTV) devices ever uncovered.” Satori researchers assess that it is likely that the same threat actors are behind both operations. Four different threat actor groups have been identified: SalesTracker Group, MoYu Group, Lemon Group, and LongTV. Learn more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















