Threat Intelligence RoundUp: March
April 03, 2023
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. New MacStealer macOS malware steals passwords from iCloud Keychain – Bleeping Computer
A new information stealer named MacStealer targets Mac users specifically. The stealer can take credentials that have been stored in the iCloud Keychain, web browsers, crypto wallets, and other sensitive files. It is being sold for $100 as malware-as-a-service and was first spotted by Uptycs analysts on a darknet forum. It works on macOS Catalina up to Ventura. MacStealer is distributed as an unsigned DMG file with the goal of tricking the user into executing it on their machine. Then the malware will gather passwords, put them in a ZIP file, and send them to a C2 controlled by the actor who will notify them by Telegram channel. Read full article.
2. FTC says online counseling service BetterHelp pushed people into handing over health information – and broke its privacy promises – The Federal Trade Commission
BetterHelp offers online counseling services. Health information, especially mental health information, is of utmost importance to keep confidential. According to the Federal Trade Commission (FTC), BetterHelp pushed people to take an Intake Questionnaire which prompted them with questions about sensitive health information of which they could not move in the questionnaire until those questions were answered. Read more.
3. Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency – The Hacker News
An old security flaw in Progress Telerik was used by multiple threat groups to break into “federal civilian executive branch (FCEB) agency’s Microsoft Internet Information Services (IIS) web server.” The security flaw exploited used a .NET “deserialization vulnerability affecting Progress Telerik UI for ASP.NET AJAX.” CISA, the FBI, and MS-ISAC (Multi-State Information Sharing and Analysis Center) disclosed the information in a statement and the bad actors had access November 2022 to early January 2023. The CVE that was exploited, CVE-2019-18935, is commonly exploited by threat actors and has been used by the group Praying Mantis. Read more.
4. BidenCash market leaks over 2 million stolen credit cards for free – Bleeping Computer
A darknet marketplace, BidenCash, known for its carding data has released a free database of 2,165,700 debit and credit cards to celebrate its 1 year anniversary. According to researchers from Cyble, 2,141,564 are unique and the other thousands are duplicates. The data released contains information that make up fullz – which are typically financial information that is leaked with subsequent personal information (PII) such as address, email, etc. and can be leveraged by cyber criminals for sophisticated social engineering, phishing, or other attacks. Free credit cards leaks for promotions for users is a marketing technique that has been used by BidenCash before. Read full article.
5. Silicon Valley Bank collapse poses challenge for cybersecurity defenders, firms – The Washington Post

The collapse of Silicon Valley in mid March quickly became a new playground for cyber criminals and cyber attacks, as we have seen time and time again that hackers and cyber criminals often wait for tragedy to hit before striking. This the perfect scenario for a financially motivated threat actor. This article outlines those that should be concerned and the scams to be watching out for. Read here.
6. Cybercriminals Targeting Law Firms with GootLoader and FakeUpdates Malware – The Hacker News
GootLoader and FakeUpdates (SocGholish) are two malwares that have been used in separate threat campaigns to target 6 law firms this January and February. GootLoader has been around since 2020 and can deliver Cobal Strike and ransomware. Threat actors compromised WordPress sites and added new posts which included “business agreements” that when downloaded gave GoodLoader. SocGholish uses sites commonly used by law firms to carry out watering hole attacks. This malware strain does not deliver ransomware. Both attacks show the trend of browser-based attacks growing in popularity as an infection vector and starting to compete with the traditional method of infection via email. Read more.
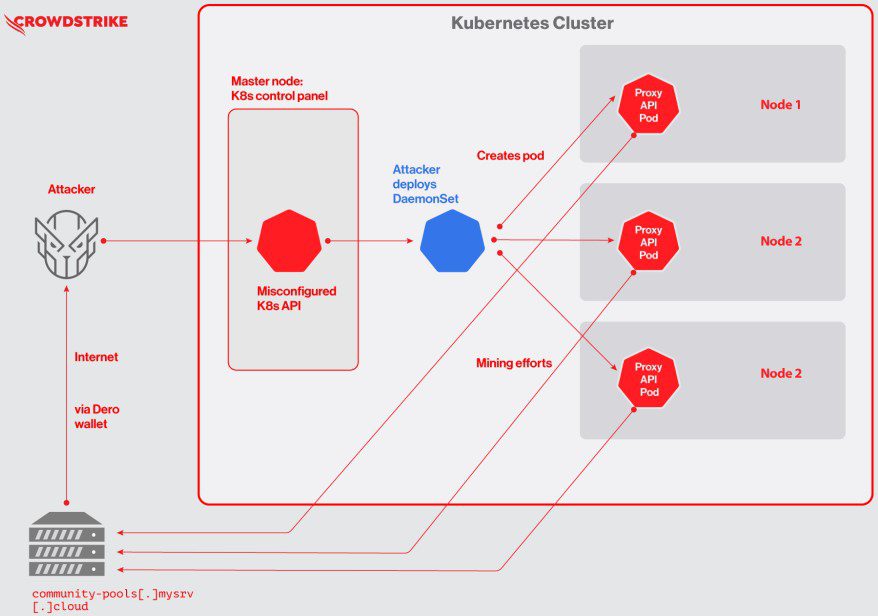
7. First-known Dero cryptojacking operation seen targeting Kubernetes – Bleeping Computer
Dero is a cryptocurrency advertised as a more secure currency than Monero. However, it has recently been the target of a cryptojacking operation. In this attack threat actors target vulnerable Kubernetes container orchestrator infrastructure that have exposed APIs. Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















