Threat Intelligence RoundUp: May
June 03, 2024
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. LockBit ransomware admin identified, sanctioned in US, UK, Australia – Bleeping Computer

Dmitry Yuryevich Khoroshev, a Russian citizen, was revealed as the admin and developer of LockBit ransomware. Earning approximately $100 million dollars through the ransomware gang activity, Khoroshev is now subject to travel bans and his assets are frozen. His enjoyment of speaking and granting interviews to media outlets and his high level of activity posting on Russian dark web forums also contribute to the totality of the picture of LockBit’s ransomware activity. Five other members of the gang were arrested and are pending trial. Full article here.
2. FBI warns of fake verification schemes targeting dating app users – Bleeping Computer

Malicious actors are using malicious links to lure dating app users to a (fake) website that proves they are not sex offenders. On this fake website, the user enters their email, phone, and other pieces of personal information to verify they are not a sex offender and prove this to the audience on the dating site. However, after this information is entered, the person is subject to a monthly fee that is charged on their credit card, and their other PII is sold in criminal operations on dark web markets, as well as in certain cases, on Telegram. Read more.
3. Ascension redirects ambulances after suspected ransomware attack – Bleeping Computer
In another example of the digital realm having a physical impact, US-based Ascension healthcare had to change the destination hospital for several ambulances when a ransomware attack impacted their systems. The incident also caused clinical treatment disruption, such as delaying medical test and medication orders, as well as system outages. No group has publicly claimed this incident as of the time of this writing. Article here.
4. US Post Office phishing sites get as much traffic as the real one – Bleeping Computer
Continuing to emphasize the usefulness and success of typo- and combo-squatting, researchers observed that websites impersonating the US Postal Service official website get as much web traffic as the actual website, and during holiday times, the fake websites receive more web traffic than the official website. Combined with SMS messages that send “package unable to be delivered” themed messages and often provide a link to a malicious website, the fraud targeting the USPS is sophisticated, and expected to continue to remain elevated. Read article.
5. Chinese hackers hide on military and govt networks for 6 years – Bleeping Computer

A new threat actor attributed to China, “Unfading Sea Haze,” has been hiding on military and government networks in the South China Sea for the past six years. Their primary goals are both espionage and intel collection, and their tools appear to overlap with APT41. The group uses spear-phishing to begin their attacks, and sends documents laced with LNK files that will execute a PowerShell script under the right circumstances. They also use a custom keylogger named “xkeylog” as well as some GhostRAT malware variants. Full article here.
6. A Russian Influence Campaign Is Exploiting College Campus Protests – Wired
In what has become a normal operation for Russian intel operatives, the Kremlin is using Telegram, bot farms, and other social media platforms such as X (formerly Twitter) to increase division in US society. Doppelganger, a well-known, Kremlin-aligned group of actors, uses its vast botnet network to pass links that contain fake news about real world events to global publications, including Le Monde and other European new networks, as well as news outlets in the United States. Full article.
7. Owner of Incognito dark web drugs market arrested in New York – Bleeping Computer
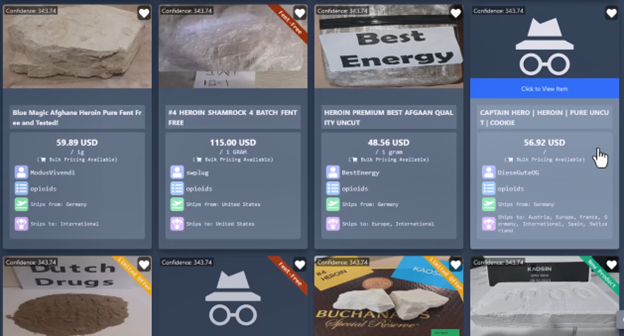
Continuing the trend of actor arrests and online market/malicious operation takedowns, this week witnessed the arrest of Incognito Market operator Rui-Siang Lin. Lin was arrested in New York City for his oversight and operations of the popular drug market, which had over ~200,000 customers that purchased all types of narcotics. Read more.
8. US charges two brothers with novel $25 million cryptocurrency heist – Reuters

Two MIT students who are also brothers stole $25 million dollars in Ethereum in 12 seconds in an attack that questions the very integrity of blockchain technology. The actors gained access to pending transactions by fraudulent means and altered the movements of Ethereum cryptocurrency. The brothers experimented with manipulating protocols in the months leading up to the theft, using a software vulnerability. Read here.
9. Over 50,000 Tinyproxy servers vulnerable to critical RCE flaw – Bleeping Computer
Small businesses and home internet users often use open-source HTTP and HTTPS proxy servers in their internet access. Cisco warned of a new flaw covered under CVE-2023-49606, which detailed a remote code execution issue that impacts incorrectly managed HTTP headers. This leads to actors possibly being able to access freed memory. Censys also confirmed approximately 90,000 internet exposed Tinyproxy services, over half of which were subjectable to the aforementioned CVE. Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















