Threat Intelligence RoundUp: May
June 01, 2023
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Hackers swap stealth for realistic checkout forms to steal credit cards – BleepingComputer
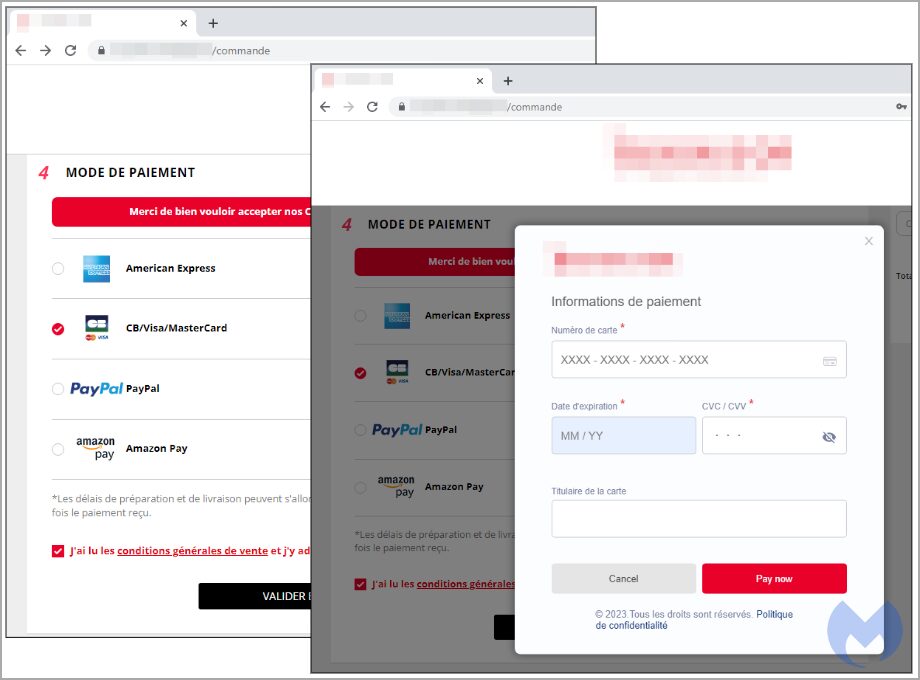
A report by Malwarebytes highlights how MageCart skimmers are using real online stores checkout pages and hijacking them with their own fraudulent but realistic-looking forms to steal credit card information. They are displayed as modal HTML pages that are convincingly superimposed onto the original page. At checkout the malware-laden checkout page is sophisticated, sometimes appeared more legitimate than the real one. Read full article.
2. ViperSoftX info-stealing malware now targets password managers – BleepingComputer
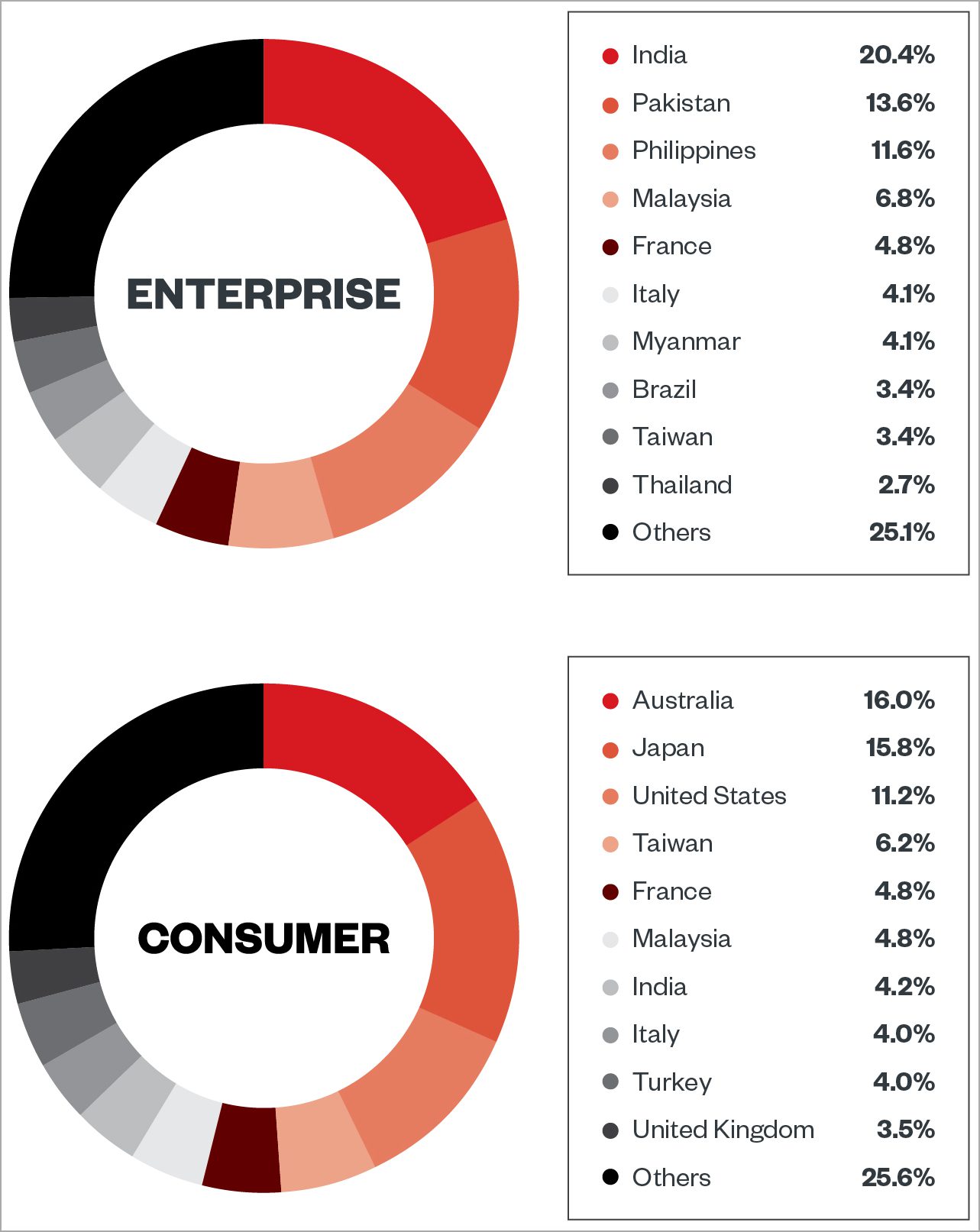
The most recent version of the ViperSoftX infostealer has been observed targeting password managers including KneePass and 1Password. Updated and more robust detection-evasion methods are also part of the new stealer. The malware installs targets Chrome, Brave, Edge, and Opera browsers with a malicious extension called VenomSoftX. According to Trend Micro, the malware has targeted the consumer and enterprise sectors in the U.S., Italy, Brazil, India, Australia, Japan, Taiwan, Malaysia, France, and Italy. According to analysts the malware can be distributed as software cracks, activators, and key generators and hides inside the not dangerous-looking software. The new version has additional features for detection-evasion techniques. A standout feature of the malware is its byte mapping used for code encryption which remaps and changes the order of shellcode bytes. Read more.
3. Stealthy MerDoor malware uncovered after five years of attacks – BleepingComputer
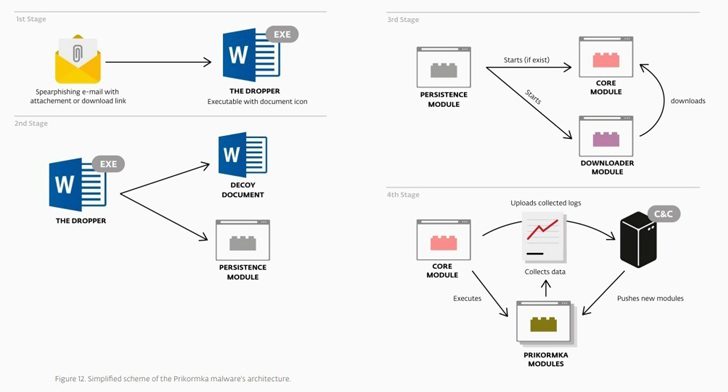
A new Advanced Persistent Threat (APT) group named LanceFly is utilizing a custom, stealthy backdoor called “Merdoor” to target organizations in South and Southeast Asia since 2018. Methods for initial access are unclear, but Symantec has observed the group using methods such as phishing emails, SSH credential brute forcing, and others. Merdoor is put into “’perfhost.exe’ or ‘svchost.exe” which are both real Windows processes through DLL side-loading. The stealthy backdoor is persistent and can remain on devices between reboots. The backdoor establishes connection with a C2 server, from which it can be given instructions. Read full article.
4. BouldSpy Android Spyware: Iranian Government’s Alleged Tool for Spying on Minority Groups – The Hacker News
With a moderate confidence level, Lookout has attributed a malware called BouldSpy (names DAAM by Cyble) to the Law Enforcement Command of the Islamic Republic of Iran. Victims of the malware’s use include minority groups such as “Kurds, Baluchis, Azeris, and Armenian Christian groups.” It is an Android-based malware family, and the intrusion vector appears to be via physical access to devices. It has a C2 panel to influence victim’s devices and creates other malicious applications masqueraded as harmless apps like a currency converter. Among other impressive features it is able to disable battery features so that the victim device will never remove the malware. It utilizes an element from the open source CryDroid, which could indicate the malware is still being developed or being used as a false flag. Read more.
5. Bad Magic’s Extended Reign in Cyber Espionage Goes Back Over a Decade – The Hacker News
Threat actor, Bad Magic (aka Red Stinger), has been linked to a new cyberattacks targeting companies in the Russo-Ukrainian area, but also to multiple activities back in May of 2016 – meaning that this threat actor has been around for longer than originally thought. Read here.
6. Malicious Windows kernel drivers used in BlackCat ransomware attacks – BleepingComputer
According to Trend Micro, the ALPHV ransomware group (aka BlackCat) has been observed employing improved signed malicious Windows kernel drivers, known as “POORTRY,” in order to not be detected while conducting cyberattacks by security software. Read more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















