Threat Intelligence RoundUp: November
December 01, 2023
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Iranian Cyber Espionage Group Targets Financial and Government Sectors in Middle East – The Hacker News

Iranian cyber actors have run a campaign for the past year targeting various entities in the already conflict-laden Middle East. Victims include Jordan, Kuwait, Oman, Iraq, Israel, and Saudi Arabia. Tools used in the 8-month long campaign include custom web shells and backdoors, indicating an elevated level of sophistication. Read full article.
2. Boeing Breached by Ransomware, LockBit Gang Claims – Dark Reading
Threat group LockBit claimed to have infiltrated Boeing’s systems using a zero-day. Boeing appeared on the LockBit leak site at the end of October 2023, but they offered no proof of data or material belonging to Boeing. Article here.
3. General Electric, DARPA Hack Claims Raise National Security Concerns – Dark Reading
Notorious actor “IntelBroker” published their purported access into General Electric (GE) and the Defense Advanced Research Projects Agency (DARPA), claiming credentials, military and other sensitive data was for sale. GE confirmed an incident occurred, but didn’t provide additional details. IntelBroker claims to have access to GE’s development environment. Read more.
4. Researchers Expose Prolific Puma’s Underground Link Shortening Service – The Hacker News

Prolific Puma is distributing phishing services, malware, and other scams via link shortening services. They have registered tens of thousands of unique domain names since the spring of 2022 and are consistently abusing DNS infrastructure in their efforts. They have not been observed advertising these services on underground markets as of yet. There is also no indication as to where Prolific Puma operates from or what language they speak. Read here.
5. Ardent Health Hospitals Disrupted After Ransomware Attack – Dark Reading
30 hospitals in the Ardent Health Services system have been hit by a ransomware attack, resulting in all emergency services being redirected. While Ardent is headquartered in Tennessee, the impact has been felt throughout six states. Learn more.
6. Cybercriminals Using Telekopye Telegram Bot to Craft Phishing Scams on a Grand Scale – The Hacker News
A new bot, Telekopye, has emerged on Telegram. Actors are using it in seller, buyer, and refund scams. The criminal group known as the “Neanderthals” has pioneered the use, tricking innocent users to enter payment details to buy goods and/or services via emails or SMS that do not exist. The groups ensure use of VPN, proxy, and TOR technologies to remain anonymous. Read full article.
7. Meet the Unique New “Hacking” Group: AlphaLock – Bleeping Computer
Russian cyber group AlphaLock debuted on Telegram this week, advertising various services such as “training pentesters.” This is often code for ransomware operations, with Russian groups using this language as they don’t want to be seen as malcious ransomware actors. The group also offers customized online courses, directed to be used for training the future, and then using said newly trained actors to establish a marketplace on DDW forum XSS where they sell the pentesting services. Read full article.
8. Russian-speaking threat actor “farnetwork” linked to 5 ransomware gangs – Bleeping Computer
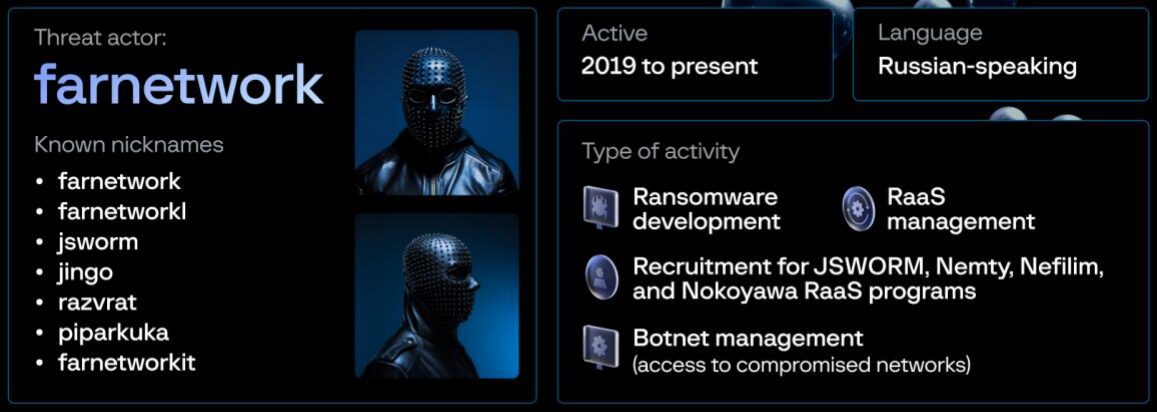
Russian-speaking actor “farnetwork” contributed to the Nokoyawa RaaS operation as a project leader and recruiter, and contributed to the development of JSWORM, Nefilim, Karma, and Nemty ransomware variants. The actor recruited for the various gangs, and actively speaks to analysts from various intelligence firms to promote their work. Their online aliases include: farnetworkl, jsworm, jingo, razvrat, piparkuka, farnetworkit. Learn more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















