What are IoCs?
July 24, 2025
Cybersecurity might as well have its own language. There are so many acronyms, terms, sayings that cybersecurity professionals and threat actors both use that unless you are deeply knowledgeable, have experience in the security field or have a keen interest, one may not know. Understanding what these acronyms and terms mean is the first step to developing a thorough understanding of cybersecurity and in turn better protecting yourself, clients, and employees.
In this blog series, we aim to explain and simplify some of the most commonly used terms. Previously, we have covered bullet proof hosting, CVEs, APIs, brute force attacks, zero-day exploits, doxing, and data harvesting. In this edition, we dive into indicators of compromise.
Indicators of Compromise (IoC) 101
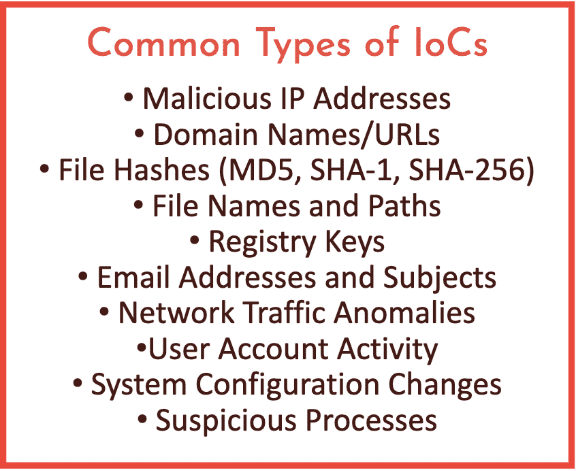
Indicators of Compromise (IoCs) are pieces of forensic data or artifacts found on a network or operating system that, with high confidence, indicate a potential intrusion, breach, or malicious activity has already occurred. Think of them as the “digital fingerprints” or “clues” left behind by an attacker and help security be able to determine if an attack has taken place.
Indicators of compromise help security professionals in several ways. They are essential for detecting both ongoing and past cyberattacks, even if the initial breach went unnoticed. Once an IoC is identified, it serves as a guide for incident response teams, helping them understand the full scope, nature, and methods of the attack. This understanding allows them to effectively contain the threat, eradicate the malicious presence, and recover compromised systems. Furthermore, by analyzing IoCs from previous incidents, organizations can proactively strengthen their defenses, updating security tools such as firewalls, intrusion detection systems, and antivirus software to prevent similar attacks in the future. Finally, sharing IoCs within the cybersecurity community is important to help other organizations defend against the same evolving threats, fostering a stronger collective defense across the digital landscape and keep up to date with the latest TTPs (tactics, techniques and procedures) of threat actors.
It’s important to distinguish IoCs from Indicators of Attack (IoAs). While IoCs tell you that a compromise has already happened, IoAs focus on the behaviors and tactics that suggest an attack is currently in progress or about to occur. Both are crucial for a comprehensive cybersecurity strategy. We will dive into IoAs in an upcoming blog.
IoCs in the Wild
Crowdstrike IoC list
Data purported to be from CrowdStrike was posted on BreachForum, a hacking forum, on July 28, 2024. According to the post, UsDoD claims to have the entire IoC (Indicator of Compromise) list from Crowdstrike but only released the first 100,000 records. Data exposed includes indicators, types of malware, actors, reports, kill chains, published dates, latest updates, and labels. Read more.
CISA and FBI: Ghost ransomware breached orgs in 70 countries
On February 19 this year, the Cybersecurity & Infrastructure Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint advisory detailing indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with Ghost (Cring) Ransomware. Since 2021, threat actors utilizing Ghost ransomware have targeted organizations in more than 70 countries. Victims have included organizations in a variety of sectors, including critical infrastructure, education, and healthcare.
SolarWinds
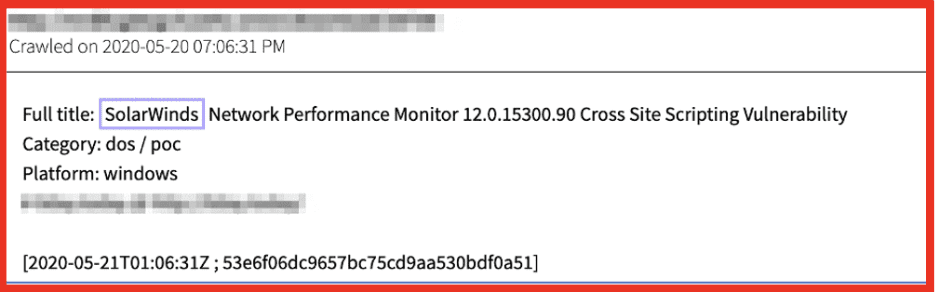
As was seen during the SolarWinds hack, monitoring the darknet for malicious discussions enables organizations to understand when and if they’re a target, and prepare accordingly. In the case of SolarWinds, we have evidence that they have been a target by hackers for a number of years. A few searches in DarkOwl Vision’s database of darknet content reveal glaring potential indicators of compromise that, when taken seriously, could have been leveraged by their customers as a cue to safeguard themselves against what ultimately resulted in the devastating hack that transpired this year.
DarkOwl Vision has collected 98 documents from a single popular zero-day marketplace with mentions of SolarWinds-specific vulnerabilities since February 2020 (shown below).
Tracking and Sharing IoCs
As shared above, sharing IoCs within the cybersecurity community is vital to developing collective defenses and sharing best practices. By keeping to date with IoCs in the wild, organizations can expand their understanding of current attack vectors, speed up their own incident response, avoid analyzing threats that have already been analyzed, and improve their overall security posture.
One way for tracking and sharing IoCs is through TIPs (Threat Intelligence Platforms). These specialized platforms are designed to collect, process, and disseminate crucial threat intelligence, including IoCs, to the wider community. To ensure efficient and interoperable sharing, IoCs are often exchanged using standardized formats and protocols. For instance, STIX (Structured Threat Information eXchange) provides a common language for representing and sharing cyber threat intelligence, encompassing not only IoCs but also threat actors and their tactics. The TAXII (Trusted Automated eXchange of Intelligence Information) protocol then facilitates the secure transmission of this STIX-formatted data between different organizations or security platforms.
Beyond specialized platforms, many cybersecurity vendors, research organizations, and government agencies provide Threat Intelligence Feeds. These feeds deliver real-time or near real-time updates of IoCs directly to an organization’s security tools. Information Sharing and Analysis Centers (ISACs) and Information Sharing and Analysis Organizations (ISAOs) play a critical role as well. These sector-specific or cross-sector organizations create trusted environments for their members to share sensitive threat information, including IoCs, and collaborate on defense strategies. For example, there are dedicated ISACs for sectors like finance, energy, and healthcare. Governments also contribute significantly; many have Government Initiatives to facilitate threat intelligence sharing, such as CISA’s Automated Indicator Sharing (AIS) in the United States, which provides federal agencies and partners with machine-readable cyber threat indicators.
Finally, the broader Security Research and Open-Source Communities are invaluable contributors. Independent security researchers, ethical hackers, and open-source projects frequently discover and publish IoCs through various channels like blogs, online forums, GitHub repositories, and specialized websites.
Product Highlight: Entity API
Entity API enables the identification and contextualization of specific entities—such as email addresses, IP addresses, and domains—within DarkOwl’s darknet data. This tool is invaluable for incident responders and threat hunters seeking to correlate Indicators of Compromise (IOCs) and assess potential threats.
Investigators can gather IOCs from dark web sources and link them to threat actors or campaigns. This helps in profiling the activities, tactics, and techniques of adversaries, enabling proactive threat hunting and vulnerability assessments.

Emails and Domains
Email Address and Domain endpoints allow you to request all exposed information relating to a single email address or email domain. For example, you can request a list of all emails belonging to a particular domain, or see if a specific email address has been exposed with a hashed or plaintext password (if detected).

Credit Cards and BIN
Credit Card and Bank Identification Number (BIN) endpoints allow you to request to see information relating to a single credit card number or BIN. For example, end users can query all credit cards belonging to a specific BIN that have not expired or the URL source of the pages on which a specific credit card was posted.

Cryptocurrency Addresses
Cryptocurrency Address endpoints allow you to see if specific cryptocurrency addresses have been exposed. Sample response include: a contextual text fragment provided from the original source document.

IP Addresses
IP Address endpoints allow you to request to see information relating to a single IP address. For example, end-users can leverage search parameters to find: if a specific IP address has been posted on darknet forums.
One of the most prevalent use cases for insight into DarkOwl’s data is the recent persistent rise in cybercriminal activity as a whole, and specifically ransomware activity, which largely presents itself in the dark web. The global dark web intelligence market size is expected to raise at a CAGR rate of 22.3% by 2028, to the total of $1.3 billion.
Other recent reporting from Kaspersky maintains that the most common attack vector for all ransomware attacks continues to be via account takeover utilizing stolen or brute forced credentials. Entity API will empower threat intelligence teams with the tools to determine when such account information has been compromised, and take remediation steps accordingly.
Monitor Cryptocurrency Mentions Using Entity API
With Entity API, users have access highly-targeted, structured information from the largest commercially available collection of darknet and deep web sources. This includes Tor, I2P, Zeronet, Data Breaches, encrypted chats, IRC, and authenticated forums. Users can search for a crypto address that DarkOwl has captured from darknet sources including illegal marketplaces and vendor forums to detect wallets with problematic activity. Cryptocurrency address endpoints allow users to see if specific cryptocurrency addresses have been exposed.
Cryptocurrency types include:
- Bitcoin
- Ethereum
- Monero
- zCash
- Litecoin
- Dash
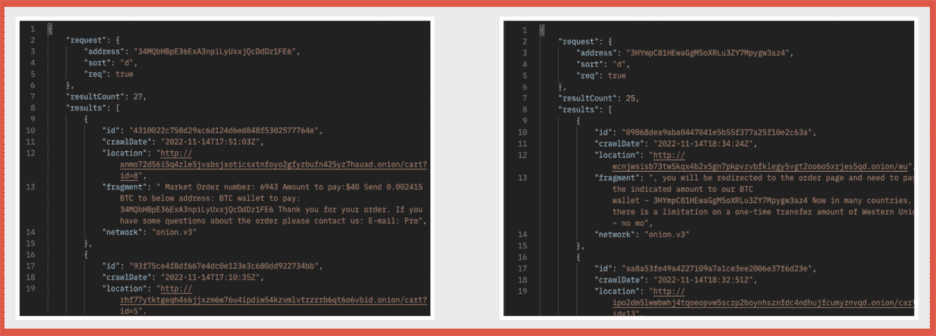
Figure 2: Request to see all instances of a specific cryptocurrency address appearing on the darknet (or other underground networks). Sample responses pictured above.
For those in charge of monitoring for critical information regarding their business or their customers, having access to DarkOwl’s darknet data means access to near real-time data from exclusive dark web sources including authenticated forums and emerging chat networks. Contact us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















