What is a DDoS Attack?
October 09, 2025
Cybersecurity might as well have its own language. There are so many acronyms, terms, sayings that cybersecurity professionals and threat actors both use that unless you are deeply knowledgeable, have experience in the security field or have a keen interest, one may not know. Understanding what these acronyms and terms mean is the first step to developing a thorough understanding of cybersecurity and in turn better protecting yourself, clients, and employees.
In this blog series, we aim to explain and simplify some of the most commonly used terms. Previously, we have covered bullet proof hosting, CVEs, APIs, brute force attacks, zero-day exploits, doxing, data harvesting, IoCs, and credential stuffing. In this edition, we dive into DDoS attacks.
DDoS Attacks 101
DDoS is an acronym for Distributed Denial of Service Attack – a malicious attack on a network that is executed by flooding a server with useless network traffic, which exploits the limits of TCP/IP protocols and renders the network inaccessible. This excessive traffic prevents legitimate users from accessing the service, effectively causing a “denial of service.”
The frequency of DDoS attacks are constantly on the rise. Some reports estimate that there were approximately 2,200 DDoS attacks every hour in the first three quarters of 2024 – a staggering 49% QoQ increase in DDoS attacks and a 55% increase YoY. The United States ingested more than 40% of DDoS attacks, followed by Germany, then Brazil, Singapore, Russia, South Korea, Hong Kong, United Kingdom, Netherlands, and Japan.
While the average length of a DDoS attack is under 10 minutes, the financial damage that it can cause to the attacked can be very damaging – the average cost per minute of downtime is $22,000. On the flip side, attackers can rent tools online to launch an attack for as little as $5 an hour.
How Does a DDoS Attack Work?
A DDoS attack leverages a large network of botnets. Botnet can be defined as an army of compromised computers or internet of things (IoT) devices that collectively utilized for a malicious purpose. This flood of traffic leaves the device unable to be used by legitimate users. Motivations for committing a DDoS attack range:
- Extortion: Attackers demand a ransom from the target to stop the attack.
- Hacktivism: Attackers use hacking techniques to achieve a political or social agenda, such as protesting against organizations, governments, or ideologies they disagree with, raising awareness on a political agenda, or exposing corruption.
- Business Competition: A business might launch an attack on a competitor to disrupt their services and gain a competitive edge.
- Cyber Warfare: Nation-states damage another nation’s digital infrastructure, information systems, or critical services for military or political objectives.
- Distraction: A DDoS attack can be a smokescreen to distract security teams while attackers conduct a more sophisticated breach, such as stealing data.
DDoS Attacks in the Wild
Esports and Gaming
Esports platforms, streamers, and tournaments have become prime targets for cyberattacks. The reasons are simple: high visibility, massive online audiences, and often, poorly secured infrastructure.
A report from Control Risks explains that “the sheer popularity of esports, combined with lax security protocols in some areas, makes them an ideal target for DDoS attacks, credential theft, and extortion.” In fact, the report states that over 37% of all DDoS attacks are directed at online gaming and esports platforms. This makes gaming and gambling the industry most targeted by DDoS attacks.
These aren’t hypothetical threats. In recent years, major tournaments have been halted mid-stream due to attacks, players have been forced offline during crucial matches, and attackers have used ransomware to hold tournament servers hostage.
UK Councils
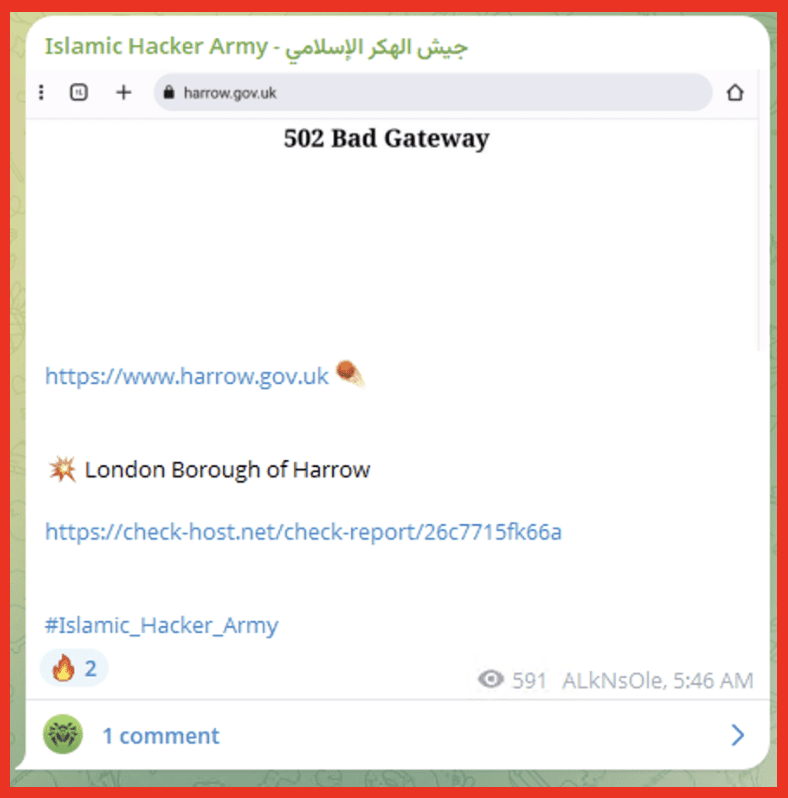
One group of organizations which has been increasingly targeted by ransomware groups and other threat actors is UK councils which are the local level of government in the UK. Recently hacktivist groups which are associated with countries involved in conflict such as Russia, Ukraine, Palestine, Iran and Israel have been known to conduct DDoS attacks targeting council websites. The image to the left shows proof of DDOS against London Borough of Harrow from Palestinian affiliated hacktivist group which caused temporary website outages and service disruptions across multiple local councils including Blackburn with Darwen, Exeter, and Arun District Council. These attacks were politically motivated in response to the UK’s support for Ukraine and carried out by hacktivist group NoName057(16).
Hacktivist Group: Dark Storm
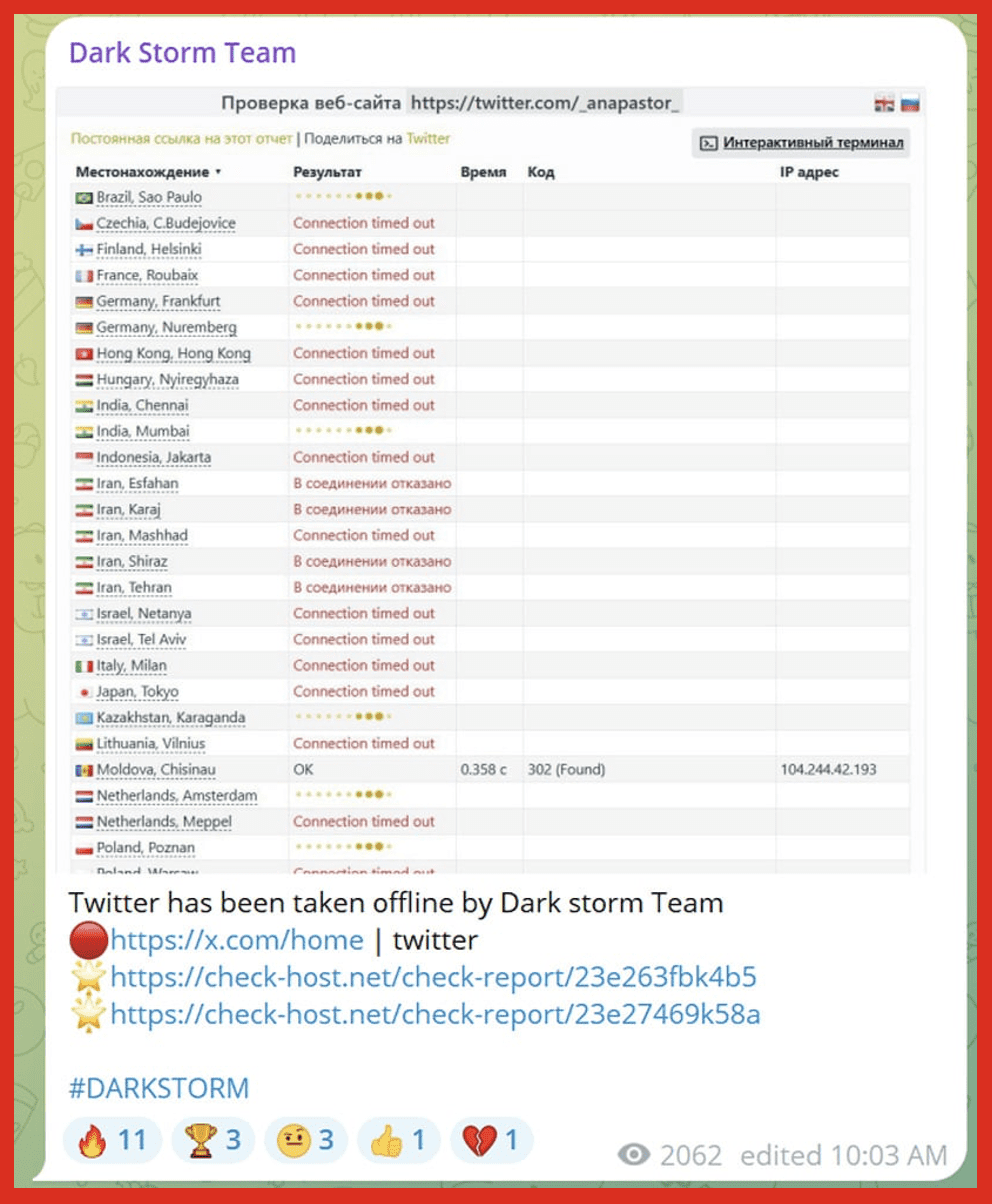
Earlier this year, X suffered multiple worldwide outages. The hacktivist group Dark Storm has claimed responsibility for the DDoS attacks which caused the outages. Specifically, the group made posts on their Telegram channel the same day the attacks took place and shared screenshots from check-host.net as proof of the attack. Tens of thousands of users were impacted by the outages.
A month after Dark Storm caused the outages of X, the notorious hacking forum BreachForums went offline, this time possibly as a result of a Distributed Denial-of-Service (DDoS) attack. Dark Storm, once again, claimed that it was behind a DDoS attack against BreachForums. The group shared a Check-Host.net link in its Telegram channel which showed that the hacking forum was down in over two dozen countries.

Protection and Mitigation
As always, DarkOwl recommends practicing good cyber hygiene in order to prevent an attack before it happens if at all possible. While attackers are constantly changing their TTPs (tactics, techniques, and procedures), there is no single foolproof way to prevent a DDoS attack, a multi-layered approach to protection is recommended. Every organization should have a DDoS Response Plan and keep it up to date (who to contact, what systems to check, etc), know the normalities of your network so you can know when patterns or activities look off, maintain good cyber hygiene by keeping all systems, software, and applications updated with the latest security patches, and increase your system bandwidth so if an attack does happen, you have more capacity to handle the flood of traffic and stay online.
Keep up with DarkOwl. Follow us on LinkedIn.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















