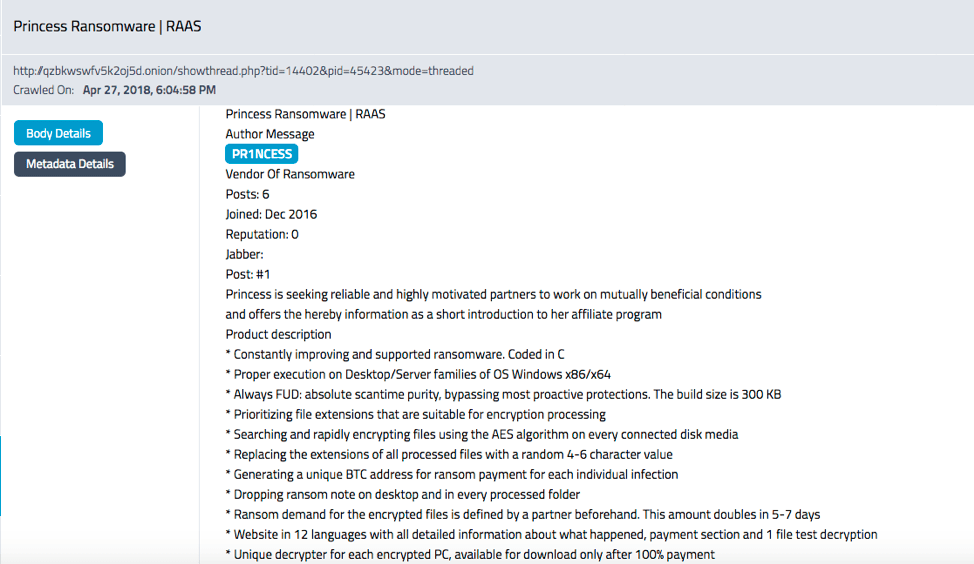
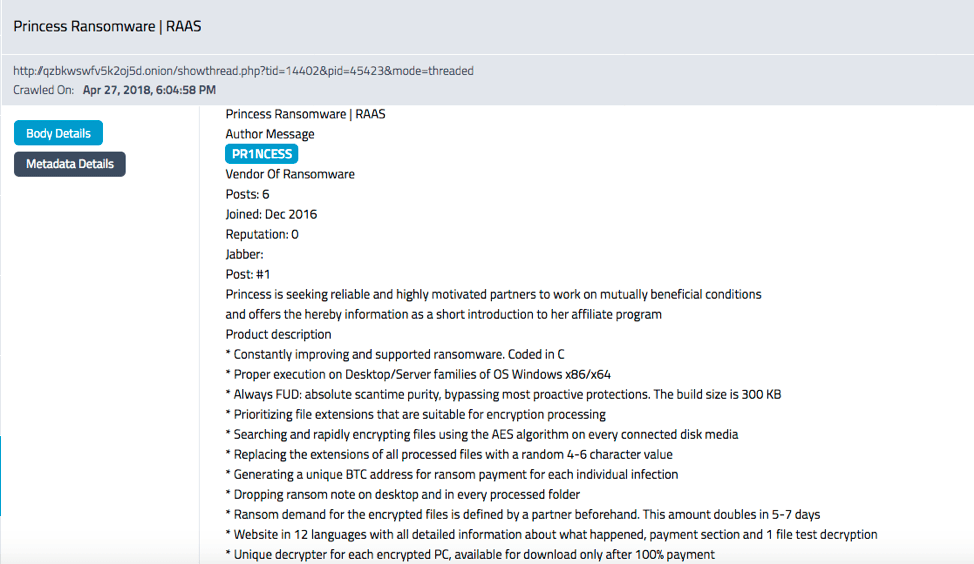
DarkOwl LLC and Cowbell Cyber Announce Strategic Partnership to Bring Darknet to Cyber Insurance Market
The new partnership between DarkOwl and Cowbell Cyber will add darknet insights into cyber insurance underwriting
Denver, CO – WEBWIRE – Thursday, October 17, 2019 “The darknet is the primary destination for the exchange of hacked data. By partnering with DarkOwl, we will be able to include darknet intelligence in real-time when assessing an organization’s overall risk profile” – Jack Kudale, Cowbell CEODarkOwl LLC, a Denver-based cybersecurity company specializing in darknet data, is proud to announce a new innovative partnership with Cowbell Cyber.
Cowbell Cyber, focused on Artificial Intelligence (AI)-powered cyber insurance for small to mid-sized enterprises, is a disruptor in the cyber insurance industry and is changing the way that policies are underwritten.Cowbell will utilize DarkOwl’s platform of searchable darknet data and DARKINT™ Scores, both important data sets to incorporate when assessing the overall cyber risk footprint of any organization.
Mark Turnage, CEO of DarkOwl says: “We are delighted to be working with Cowbell Cyber, a pioneering firm addressing an important gap in the cyber insurance market. Their approach will improve the insurance industry, and our Scores product will allow Cowbell to quickly measure darknet exposure and its associated risk for organizations seeking cyber insurance.”
Cowbell and DarkOwl agree that as cyber attacks escalate, more commercial insurance carriers are tasked with understanding fundamental cyber risk and underwriting insurance policies to address that risk. Our partnership is aimed at building industry-wide best practices that will improve the quality of cyber insurance underwriting.
“The darknet is the primary destination for the exchange of hacked data. By partnering with DarkOwl, we will be able to include darknet intelligence in real-time when assessing an organization’s overall risk profile,” stated Cowbell Founder and CEO, Jack Kudale. “DarkOwl’s data brings a critical piece of the puzzle in closing insurability gaps and offering cyber coverage that truly matches businesses’ needs.”
About Cowbell Cyber
Cowbell Cyber maps insurable threats and risk exposures using artificial intelligence to determine the probability of threats and impact on coverage types for the enterprise. In its unique approach to risk selection and pricing, Cowbell combines risk observability with cyber insurance using Cowbell risk-ratings factor to offer standalone, affirmative and individualized coverage. As a result, small to medium enterprises (SMEs) can obtain insurance via brokers using simplified binding and expedited underwriting process. Cowbell Insurance Agency is a fully owned subsidiary of Cowbell Cyber and currently licensed in six states. For more information, please visit https://cowbell.insure/.
About DarkOwl
DarkOwl was founded in 2016 with the mission of using machine learning to collect and index the broadest dataset of darknet content available in the cyber-defense industry, and making that data actionable by its clients. By empowering its customers to have continual eyes on the darknet, DarkOwl enables organizations to fully understand their security posture, detect potential breaches and other threats, and investigate even the furthest and most obscure reaches of the internet.



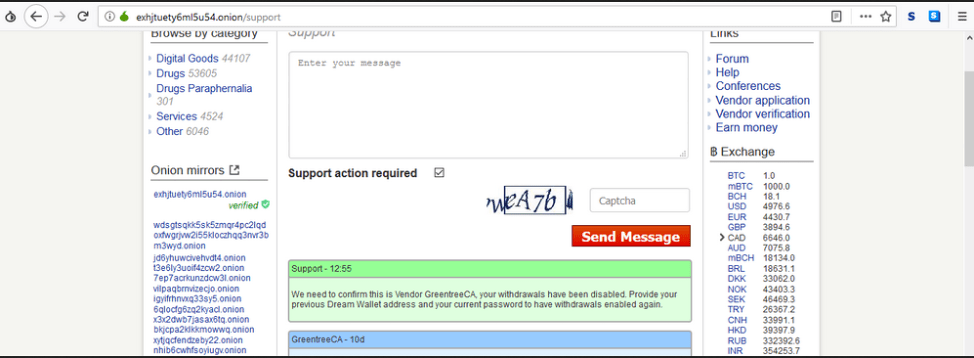
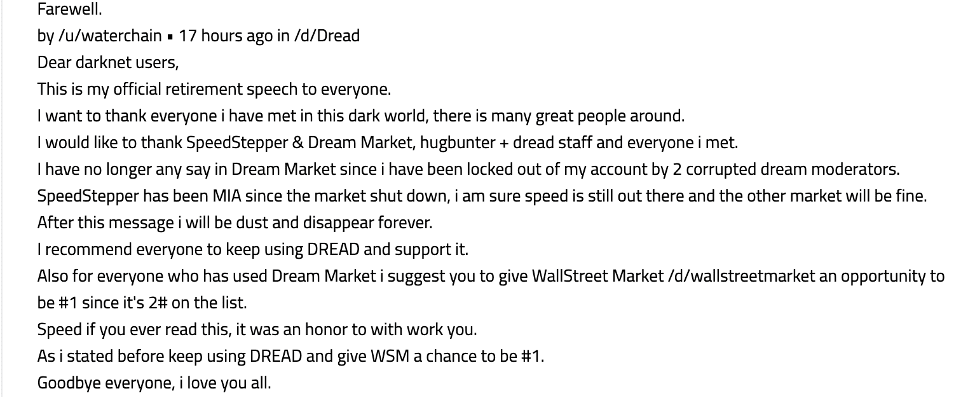
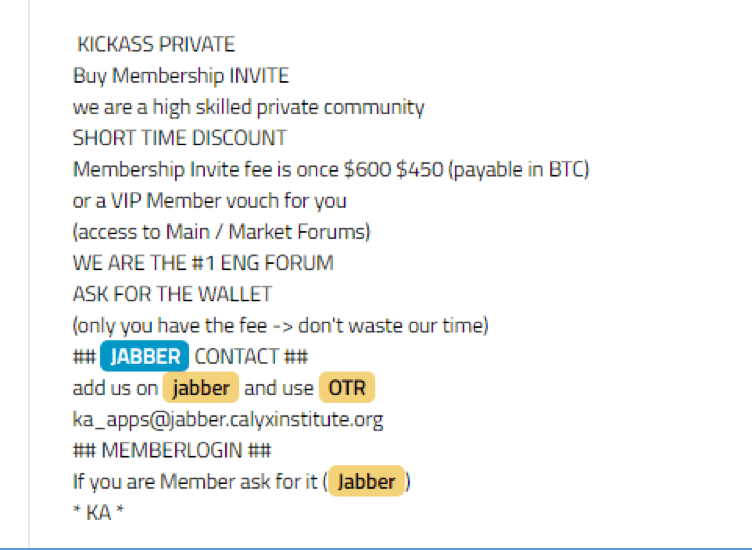
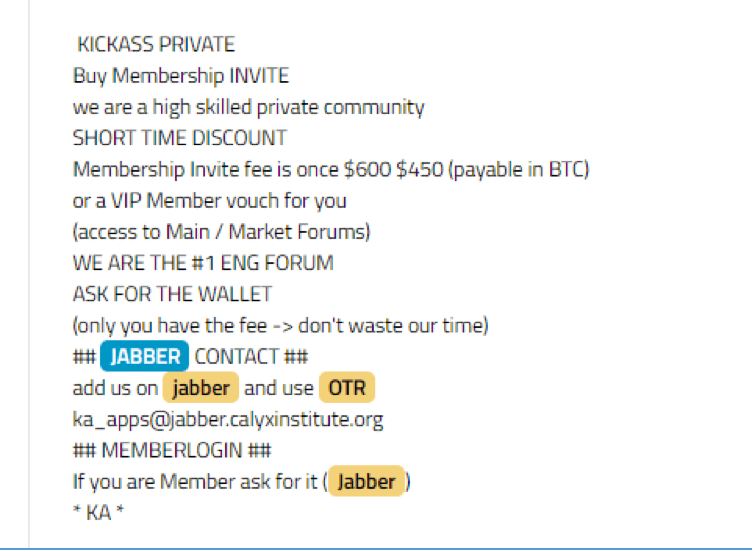
![Galaxy3 Post by user ChatTor (http://galaxy3m2mn5iqtn[.]onion)](https://www.darkowl.com/wp-content/uploads/2021/12/DanPicture4.png)
![Capture of Le-Chat conversation debating the validity of staff with Daniel's services (http://mat32scrdvrn5o4m.onion/neo/uploads/181119/MATRIX_115636_YsP_ChatTorConfession[.]png)](https://www.darkowl.com/wp-content/uploads/2021/12/DanPicture5.png)