Ontic Partners with DarkOwl, Adding Significant Index of Deep and Dark Web Data to Unified Protective Intelligence Software Offering
Immediate access to the world’s largest dark web dataset, as well as critical open source and public data seamlessly surfaces pre-incident physical threat indicators to help mitigate potential harm to Fortune 500 executives, employees, customers and assets
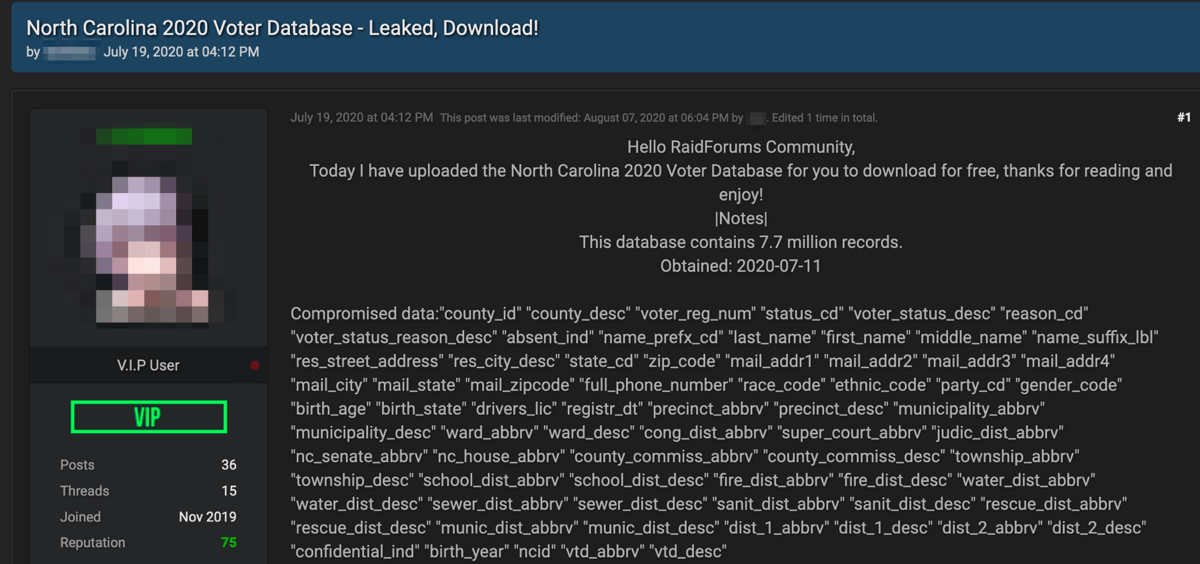
Ontic, the protective intelligence software innovator digitally transforming how companies actively identify, investigate, assess, watch and manage physical security threats, today announced a partnership with DarkOwl LLC, the leading provider of darknet, deep web, and high-risk surface net data. The partnership provides Ontic Fortune 500 clients with the ability to surface actionable insights from dark net data through the Ontic software platform for a more comprehensive view of potential physical threats to their business.
“In today’s world bad actors are posting less threatening information on publicly available websites and more nefarious and alarming information on the dark and deep web,” says Ontic CEO Lukas Quanstrom. “Through our partnership with DarkOwl, Ontic becomes the only protective intelligence platform to unite the largest dataset of dark web data that exists today with that from social media, news sites, public and criminal records, and company-proprietary records. This gives physical security professionals at corporations a proactive and more holistic way to address physical security threats.”
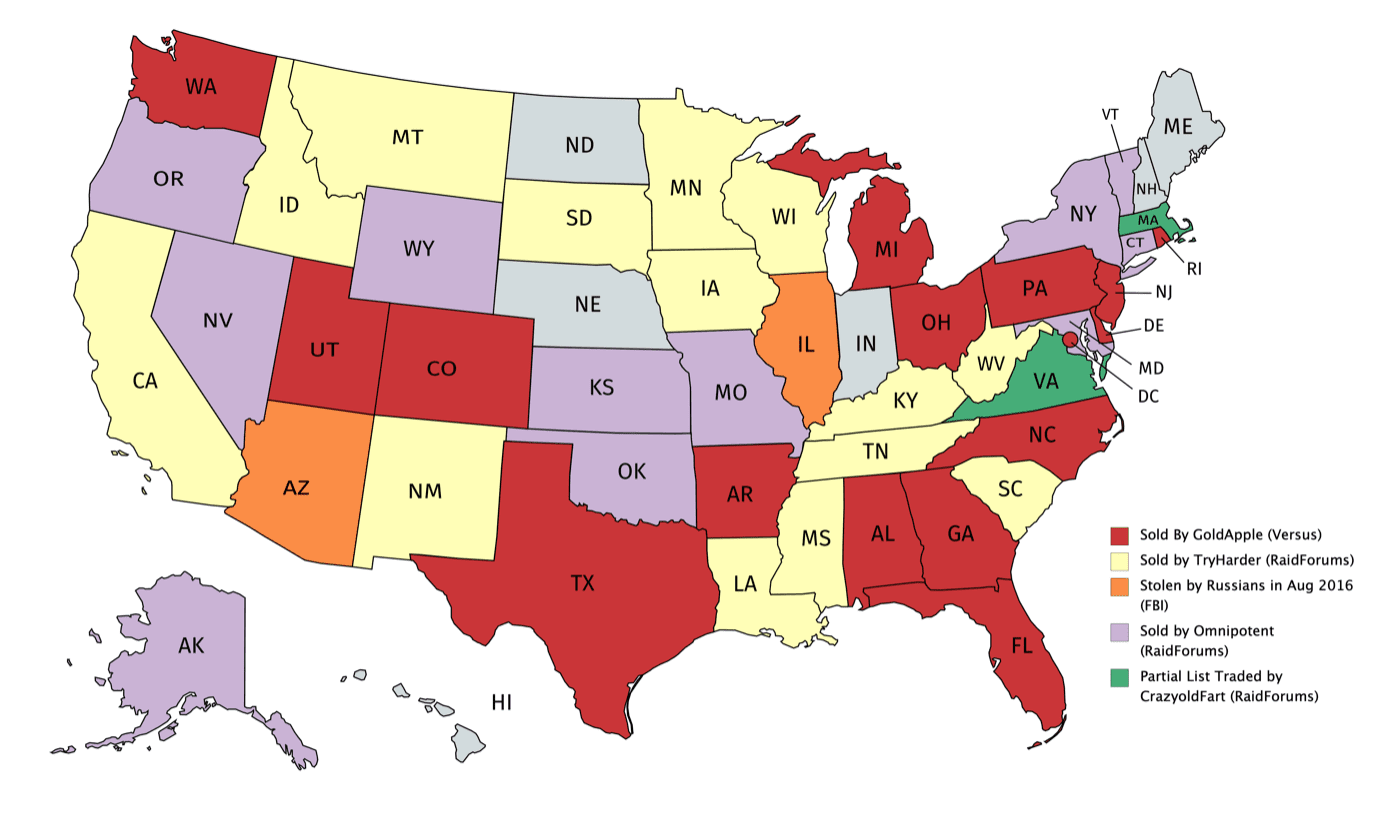
DarkOwl is the world’s leading provider of DARKINT™, darknet intelligence and the world’s largest commercially available database of darknet content. It automatically, continuously, and anonymously collects, indexes and ranks darknet, deep web, and high-risk surface net data. Because its platform collects and stores data in real-time, darknet sites that frequently change location and availability can be queried in a safe and secure manner without having to access the darknet itself.
“Darknet content is often overlooked as it relates to physical security threat management but is key to helping connect the dots on potential threats to businesses,” says Mark Turnage, chief executive officer, DarkOwl. “We’re proud to partner with Ontic and fuel the new technology-driven standard it has created for unifying critical threat data physical security teams need to identify, investigate, assess, watch and act on both known and unknown threats.”
DarkOwl darknet data is currently accessible to clients via Ontic’s platform, where end-users will benefit from support and guidance from the Ontic and DarkOwl teams to ensure successful use of the data.
About DarkOwl
We are darknet experts. DarkOwl was founded in 2016, we are the world’s leading provider of DARKINT ™, darknet intelligence and offer the world’s largest commercially available database of darknet content. DarkOwl enables cybersecurity organizations, law enforcement and government organizations to fully understand their security posture, detect potential breaches and violations of the law and mitigate them quickly. We offer a variety of options to access our data, please visit us at www.darkowl.com
About Ontic
Ontic is the first protective intelligence software company to digitally transform how Fortune 500 and emerging enterprises proactively address physical threat management to protect employees, customers and assets. Ontic’s SaaS-based platform collects and connects threat indicators to provide a comprehensive view of potential threats while surfacing critical knowledge so companies can assess and action more to maintain business continuity and reduce financial impact. ForFor more information please visit ontictechnologies.com
Press Contacts
For Ontic:
Zander Wharton
[email protected]
203-733-2815
For DarkOwl:
Kim Ketchel
Director of Marketing, DarkOwl