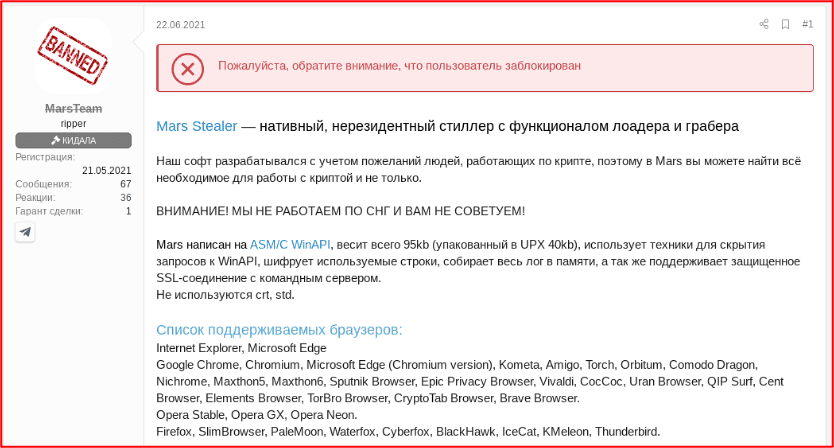
Gaming, Streaming, and the Darknet
July 08, 2022
Two years after the COVID-19 pandemic forced the world into their homes for quarantine, video gaming and streaming subscription service use is at an all-time high. There are over 134 million registered monthly active users (MAUs) on the popular video gaming distribution platform, Steam; an estimated 62 million connect daily to the service. 85% of US households have at least one video streaming service and on average households subscribe to at least 4 different services. In early 2022, Netflix reported over 221.6 million global MAUs of their services. (Source)

Given the widespread use of such services across all ages, demographics, and regional and cultural backgrounds, topics related to video gaming and streaming are frequently discussed in conversations in the criminal digital underground. The video gaming industry and the darknet community also have similarities in their core user base. Many gaming enthusiasts are intelligent, young, technically savvy, thrive in online communities and navigate the controversial and psychological games of the darknet with ease.
In celebration of National Video Game Day – July 8th – our analysts decided to take a closer look at the intersections between gaming, streaming and the darknet to uncover how interrelated the online communities are.
Accounts For Sale
Video gaming and streaming accounts are regularly offered for sale on the darknet. Accounts and accessories for popular video games such as PlayerUnknown’s BattleGrounds (PUBG), Dota 2, League of Legends (LoL), and Counter Strike (CS): Global Offensive are amongst those that regularly traded.
Game accounts are offered as “premium” with bonus account perks like player outfits, custom “skins,” and additional “uc” or “unknown cash” which can be used as virtual currency on the game platform for purchasing weapons and player skills.
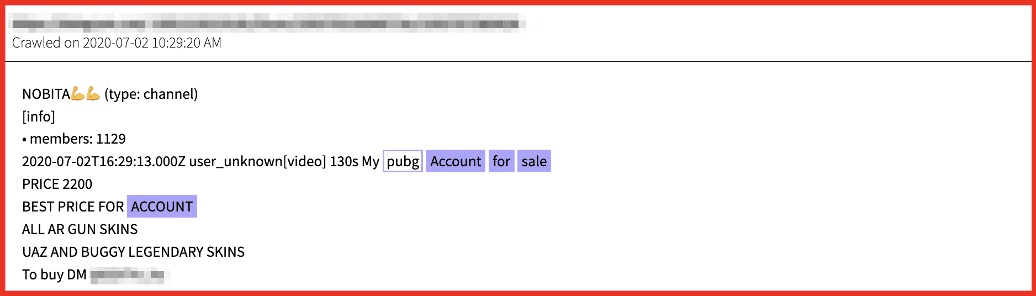
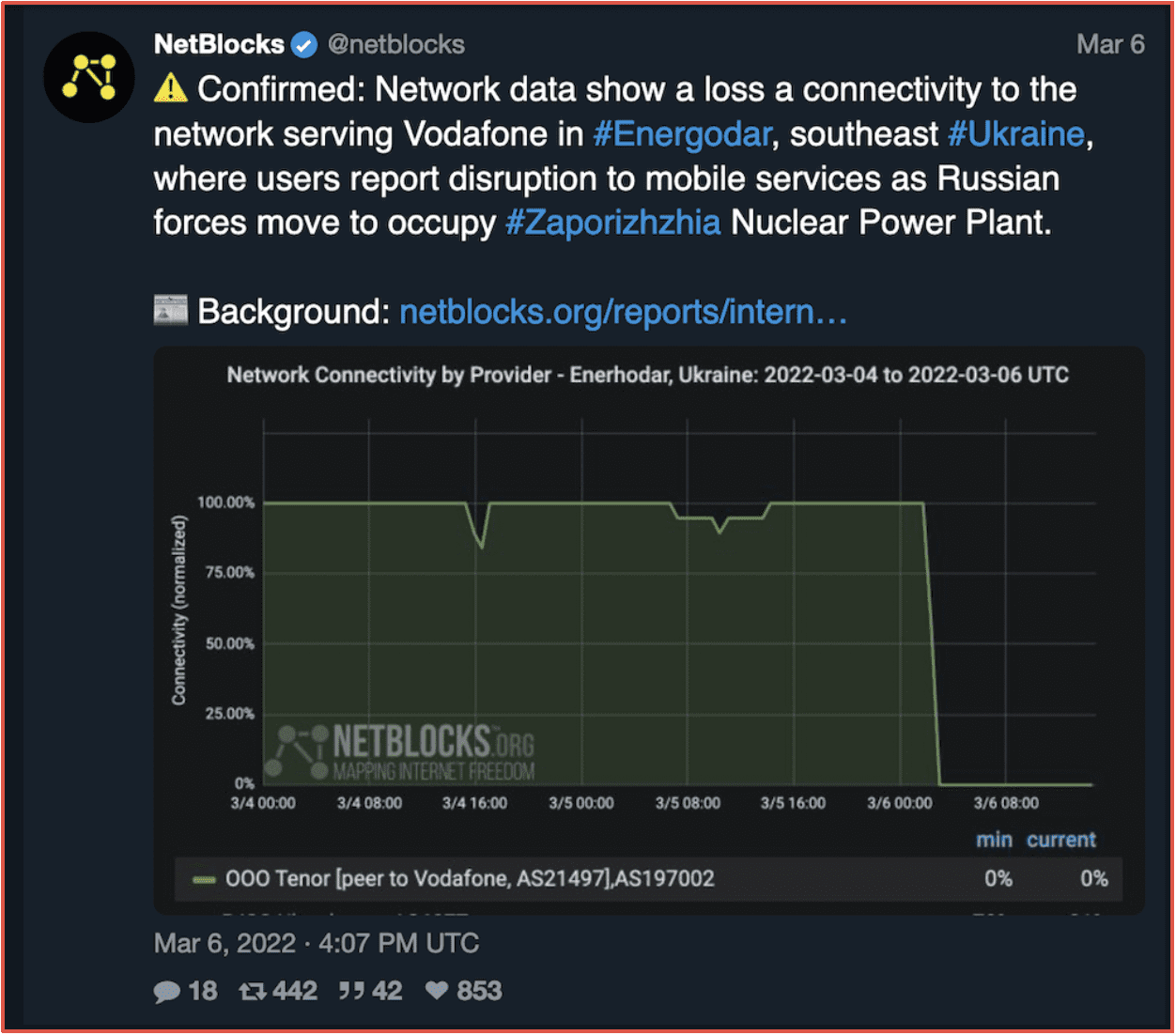
Figure 1: Source DarkOwl Vision
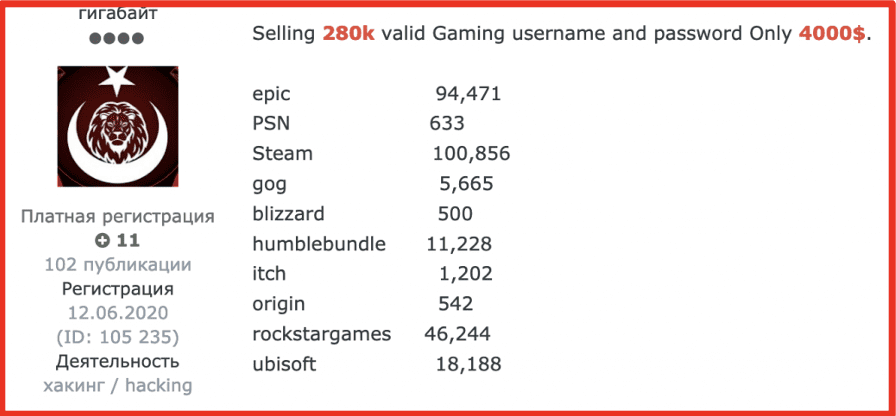
Figure 2: Offer for over 280,000 Video Game Accounts for Sale
Some video gaming accounts include “leveled up” advanced player status that includes more skills or badges, years of experiences, with extensive in-game credibility that is more valuable than a standard account on the game.
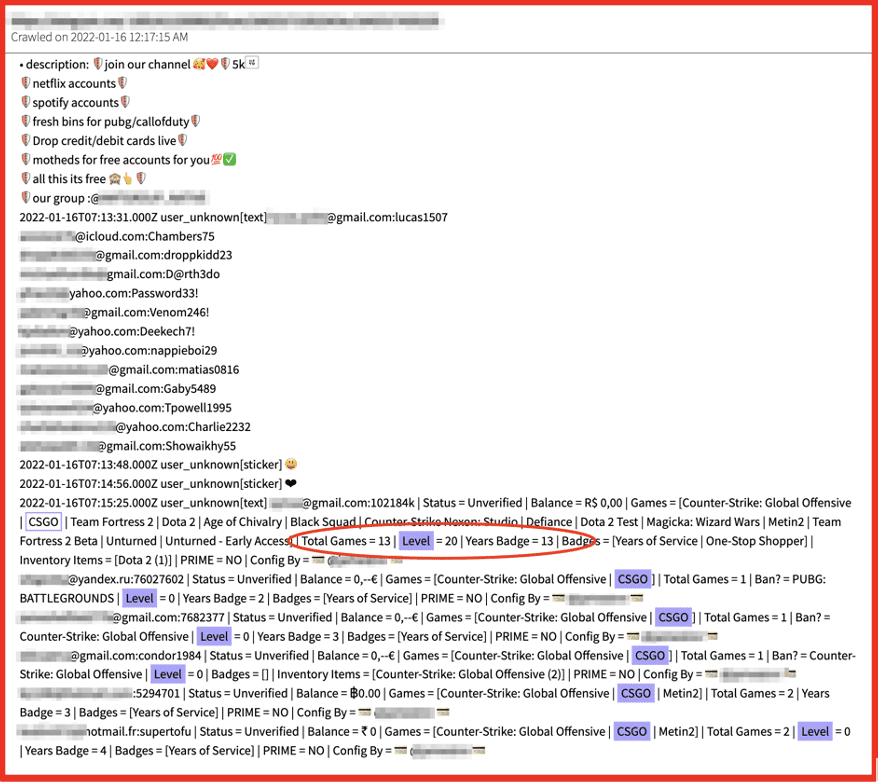
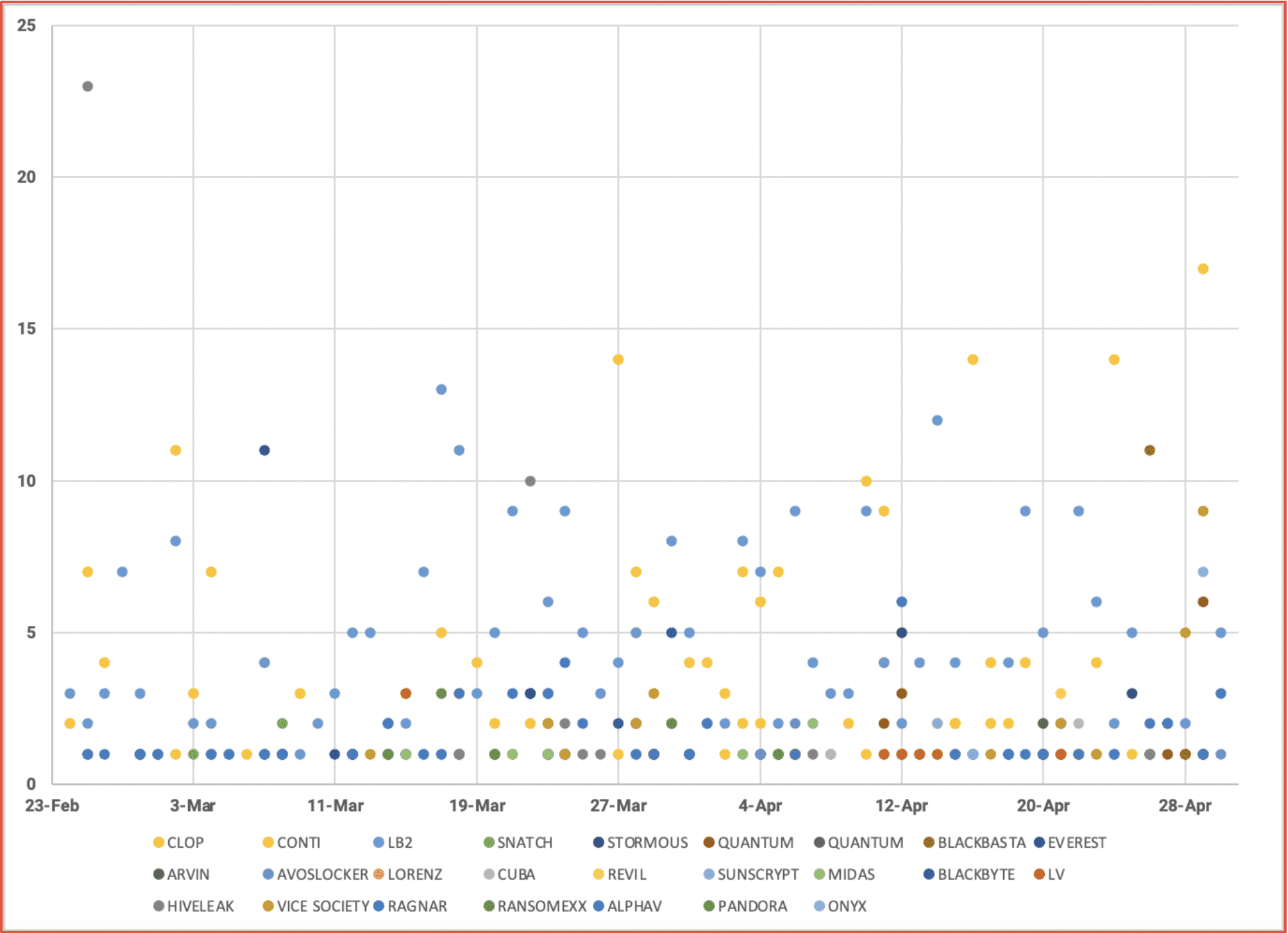
Figure 3: Source DarkOwl Vision
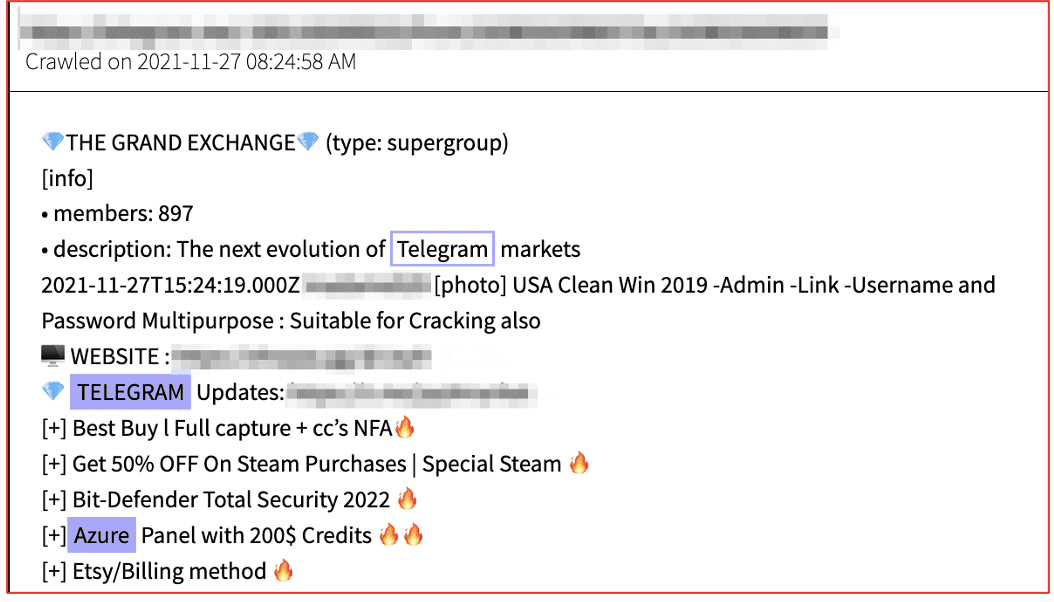
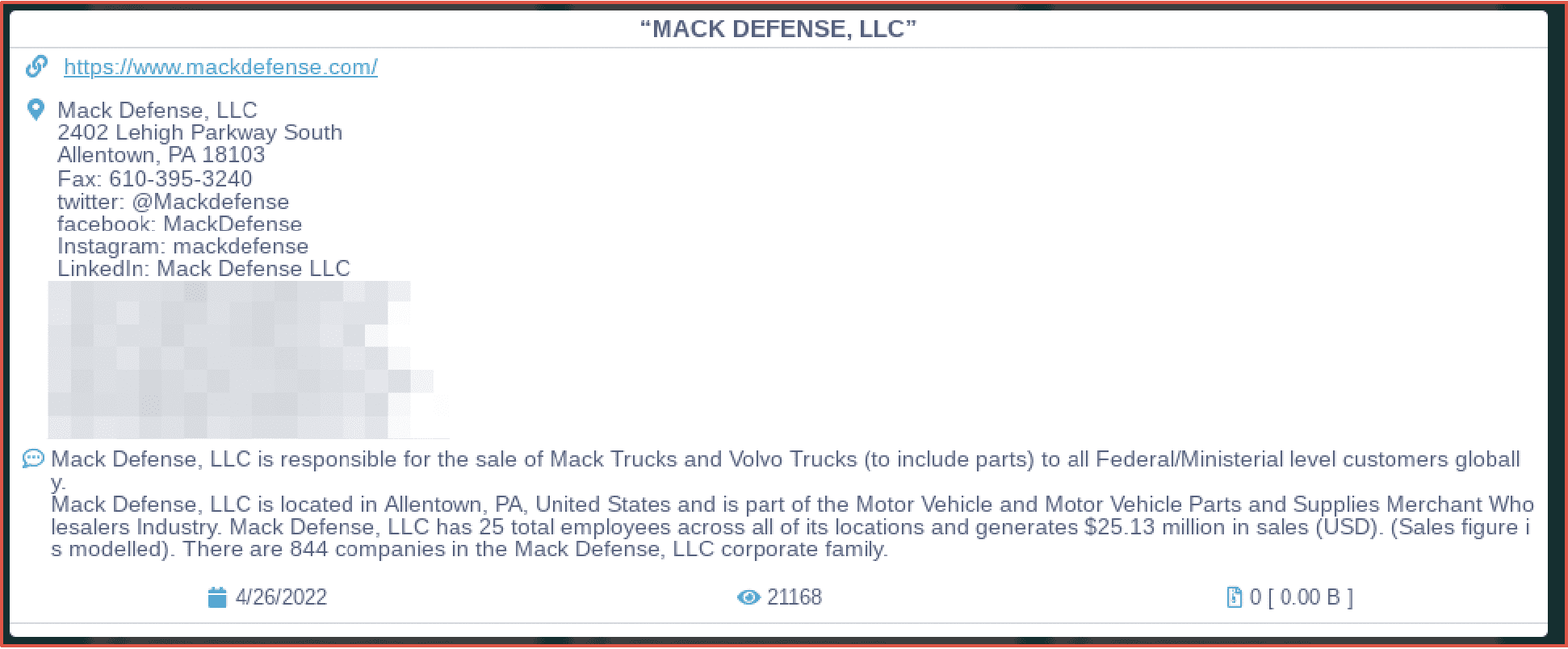
DarkOwl has also observed accounts for all of the mainstream video streaming services, such as, Hulu, Amazon, Disney+, Netflix, HBO Max. Some of these accounts are offered for free on Telegram channels, as proof of the legitimacy of accounts available for sale. We’ve also observed accounts for streaming services offered for sale on Telegram for $40 USD, with indications that the original account holder was completely unaware that their account had been sold and used by someone from the darknet.
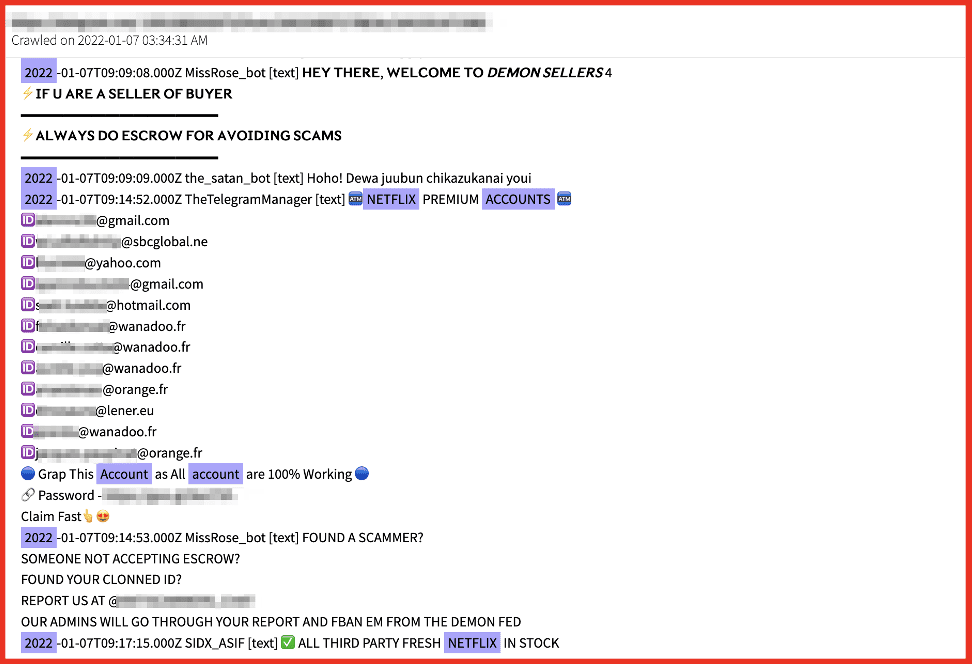
Figure 4: Source DarkOwl Vision
Cracked Accounts, Cracking Tutorials & Hacks
Some of the accounts being offered or sold are simply accounts that have been curated by darknet users, which are often described as their “own personal account.” Others are created in masse by “cracking” users’ accounts at scale, i.e. stealing and reselling account credentials. Most cracked accounts are obtained by account brokers, who compile leaked credentials from compromised commercial services and perform credential stuffing, or utilize nefarious brute-force password cracking utilities like John the Ripper.
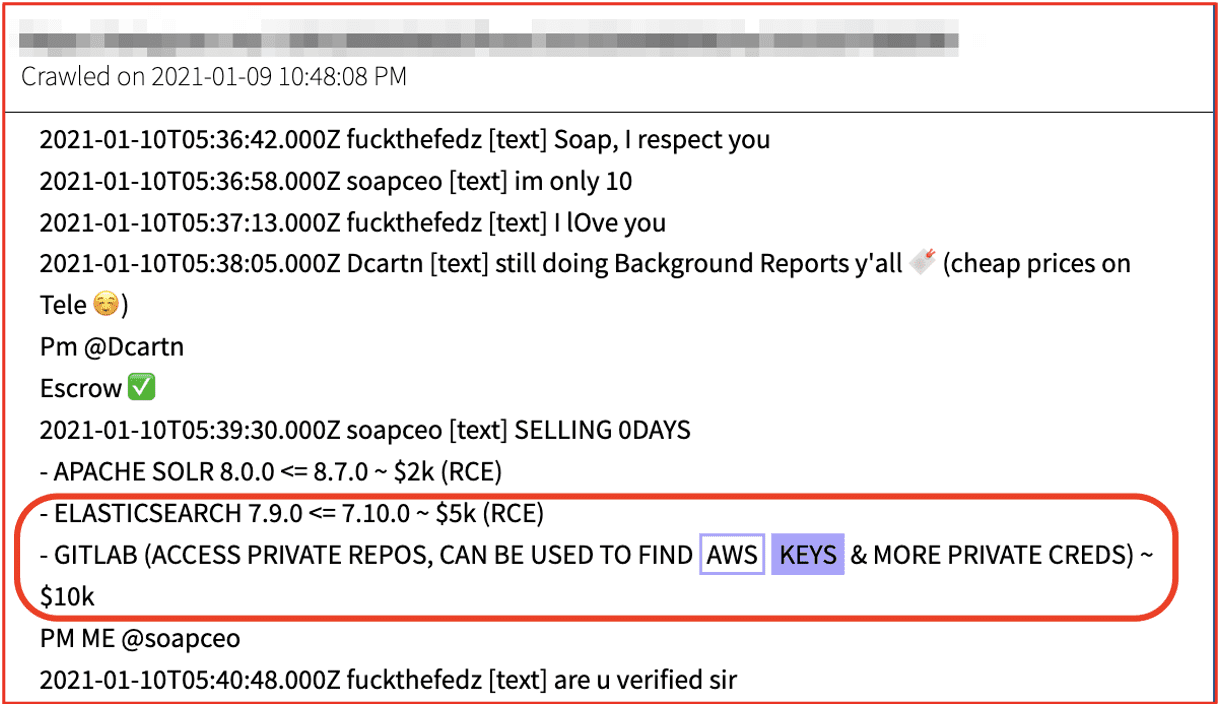
One such utility for offer on the darknet states that using their tool, users can create 10 private Counter Strike game accounts per hour. (Source: DarkOwl Vision)
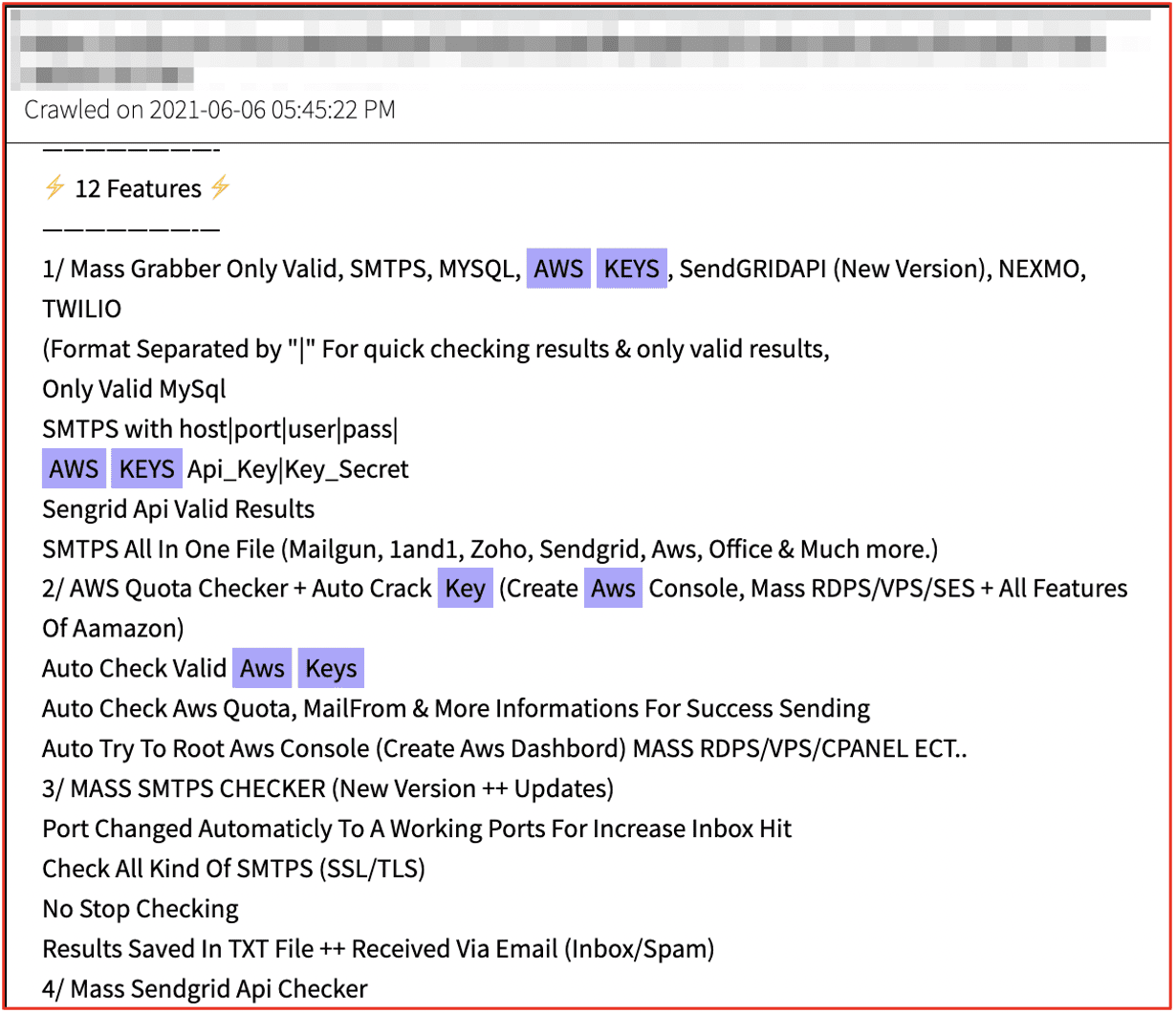
We’ve seen similar offers for automatic account generator sold in conjunction with “Cracking Tool Packs” which includes crackers, stealers, email validators, and checkers for generating and validating accounts.
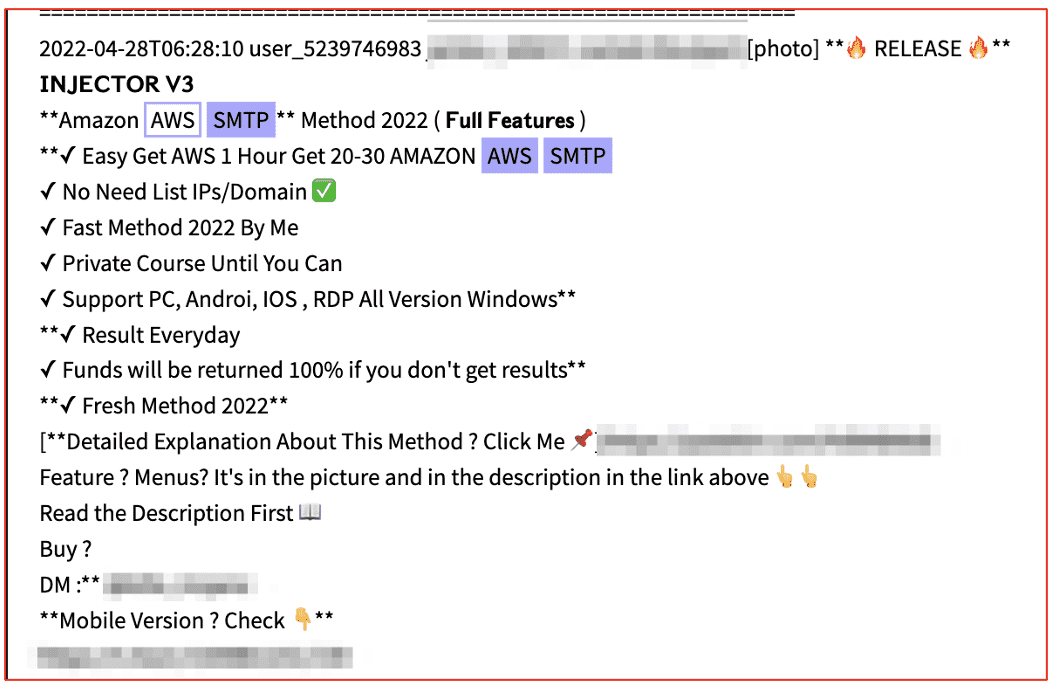
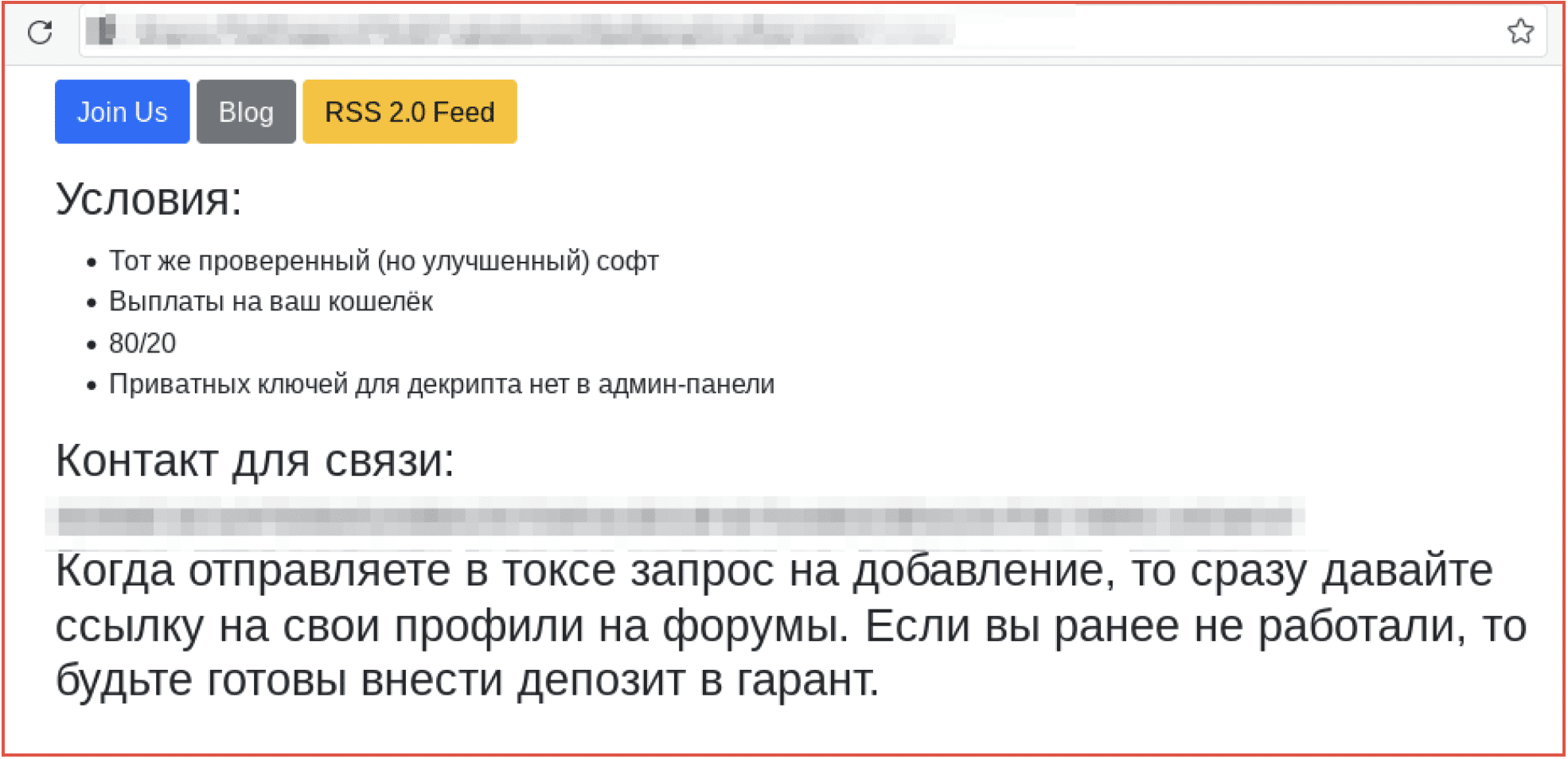
Many gamers of the darknet offer game hacks for increasing skills or a player’s credibility without the time in service in the game. For example, one document in Vision details the Fifa 2022 Coin Generator to acquire unlimited free FIFA 22 coins and points for one’s “Ultimate Team” and according to the offer, secure players like Gullit, Ronaldo, and Maradona on one’s team. The hack uses a series of network proxies to avoid the account getting banned or suspended.
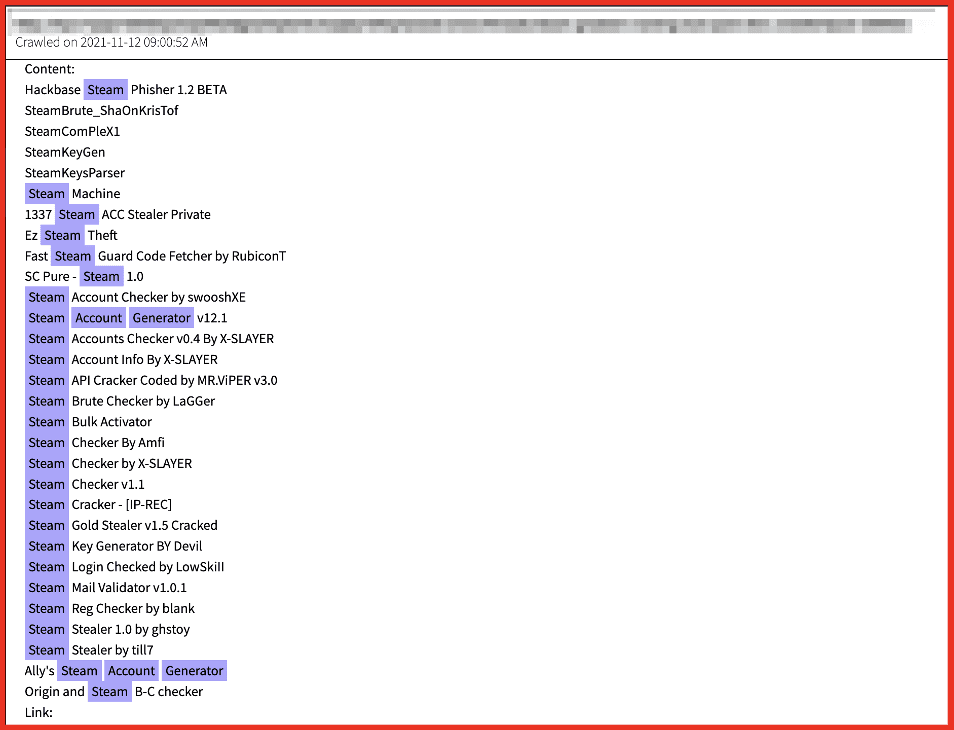
Figure 5: Source DarkOwl Vision
Cracked Games
Many deep web forums offer “cracked” games or pirated game software that can be played without any licensing or payment. Recently users on Breached Forums shared several Surface Web sites where games are available without purchase. (Source: DarkOwl Vision)
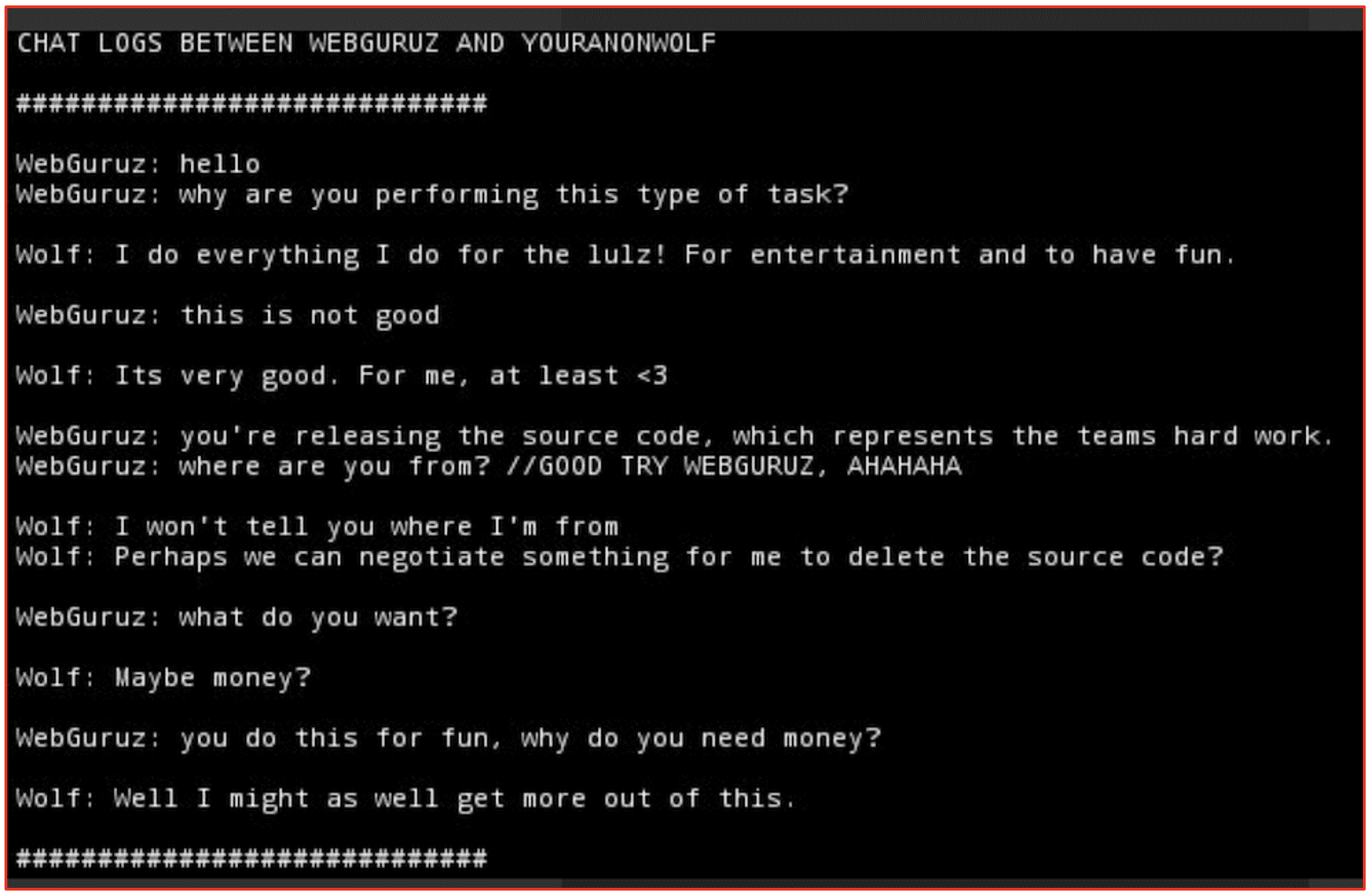
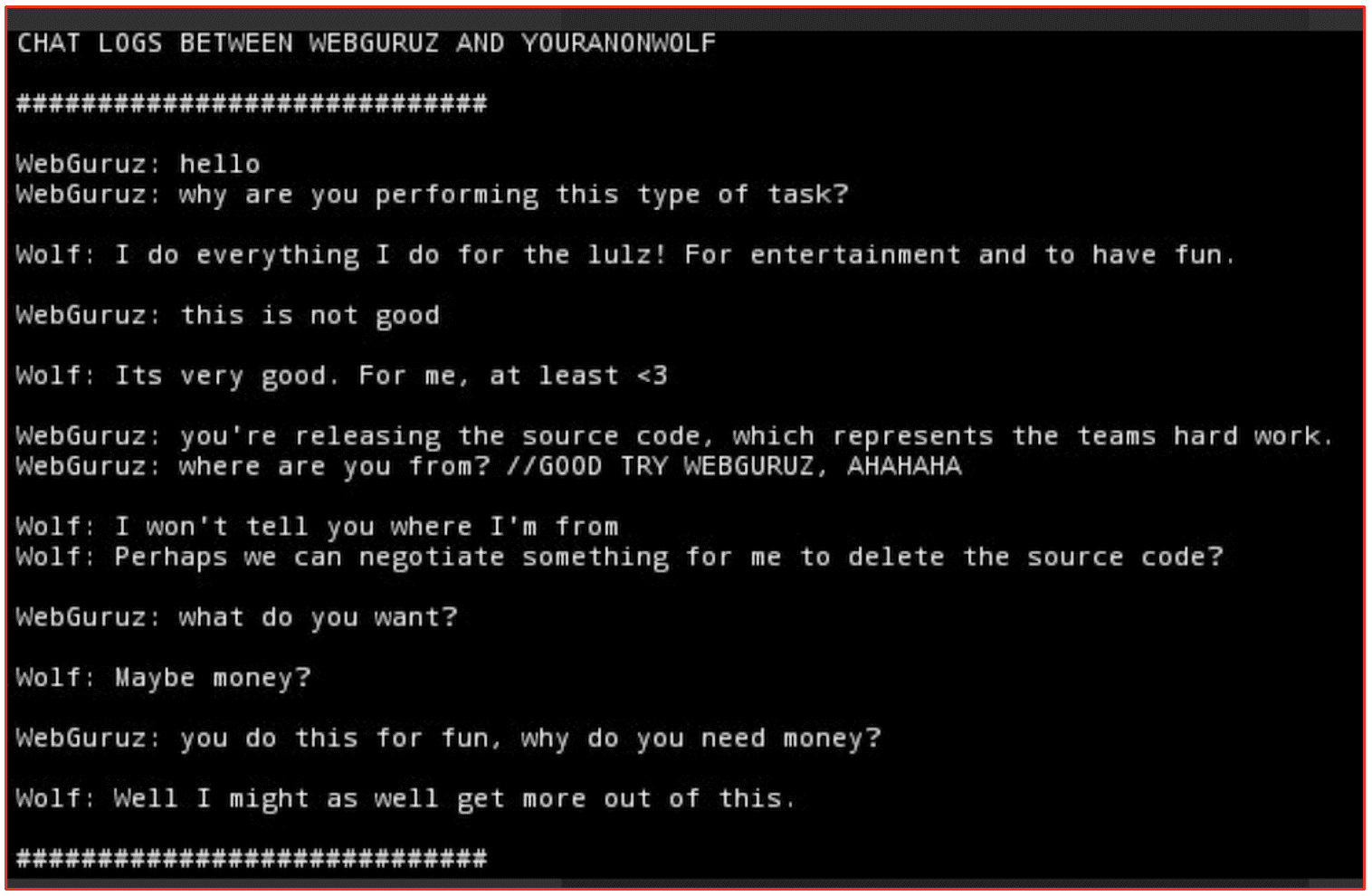
Video games are cracked by reverse engineering the programmed copyright protection features and bypassing codes in the software that validates the games as authentic. The darknet is replete with users who abhor the idea of intellectual property and celebrate software piracy; afterall, the darknet is home to The Pirate Bay (TPB). Cracking tutorials in the darknet cover all matters of illegal “cracking” including passwords, wi-fi routers, commercial accounts, and software.
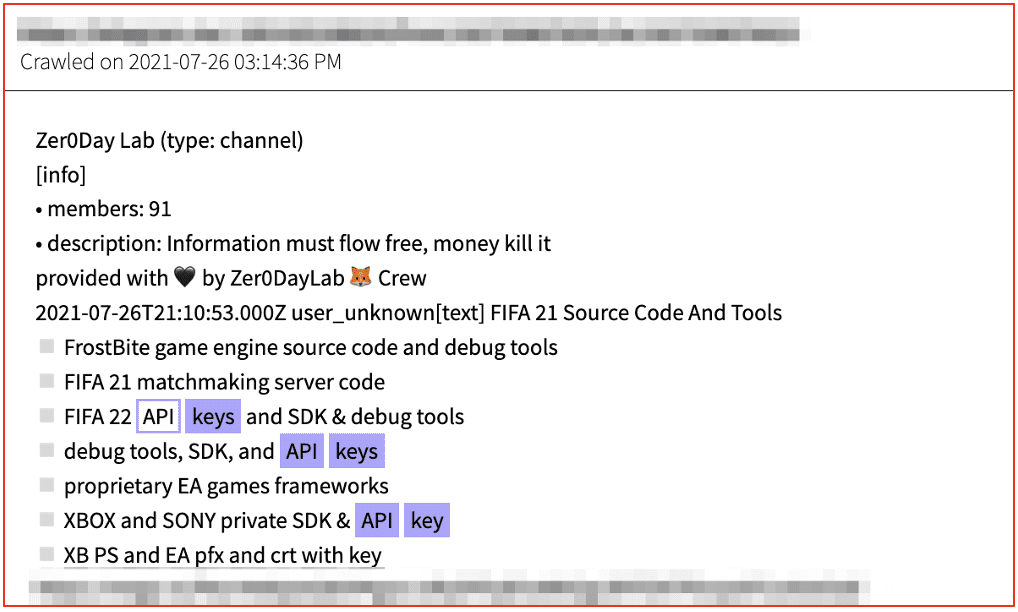
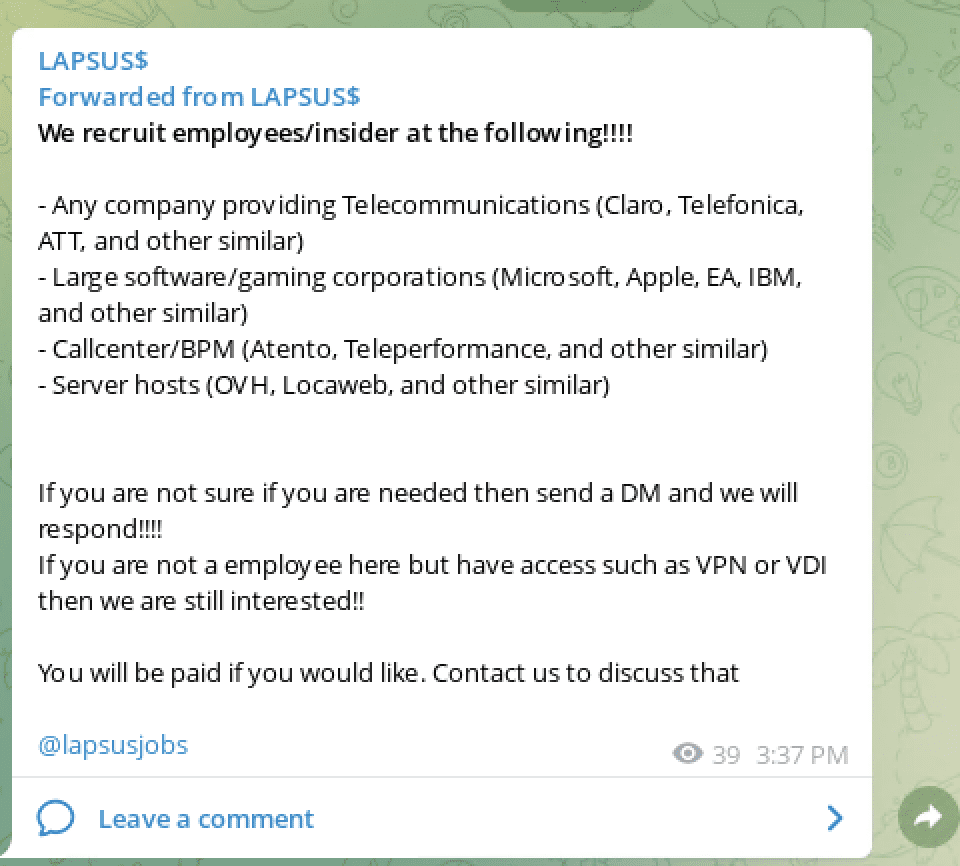
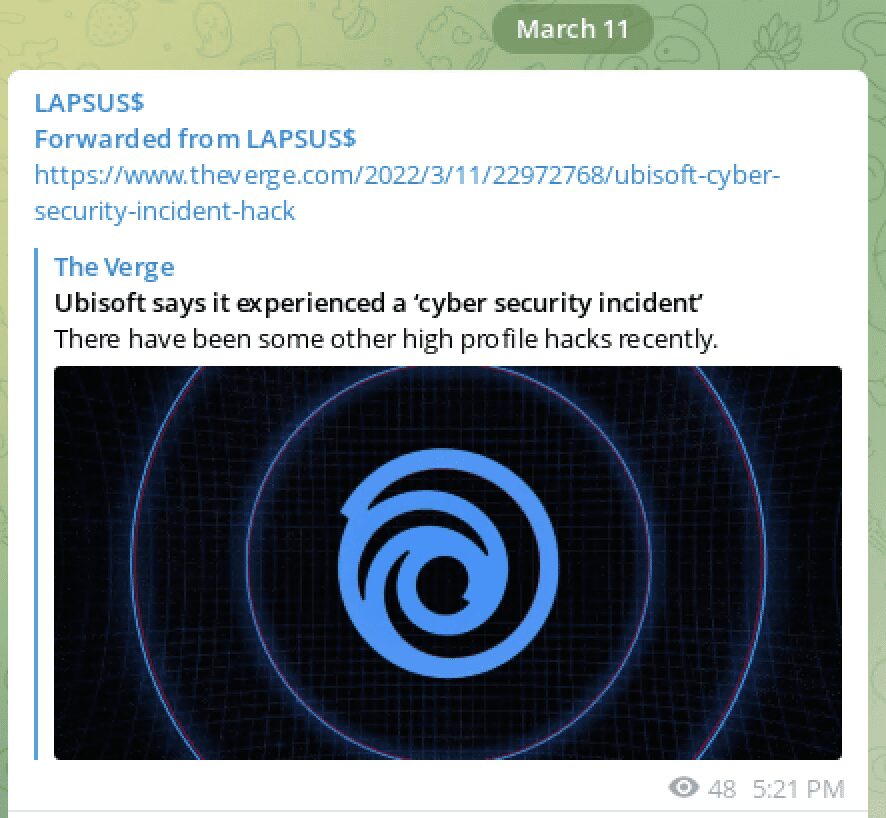
For obvious reasons, we’ll not detail any of the cracking tutorial methods that we’ve spotted across popular hacking forums and Telegram channels. In 2021, multiple video game developers were attacked by cyber criminals and source code for their projects stolen and resold on the darknet. In February 2021, cyber criminals gained access to the CD Projekt and exfiltrated the source code for Cyberpunk 2077, The Witcher 3, and Gwent. In July, the LAPSUS$ criminal group successfully exfiltrated the source code from Electronic Arts Fifa 2021 soccer game and the proprietary FrostBite game engine, which was the foundation for other popular games by the video game publisher.
The availability of such source code compilations facilitates the successful cracking of video game software applications in the future by cyber criminals profiting off selling pirated games.
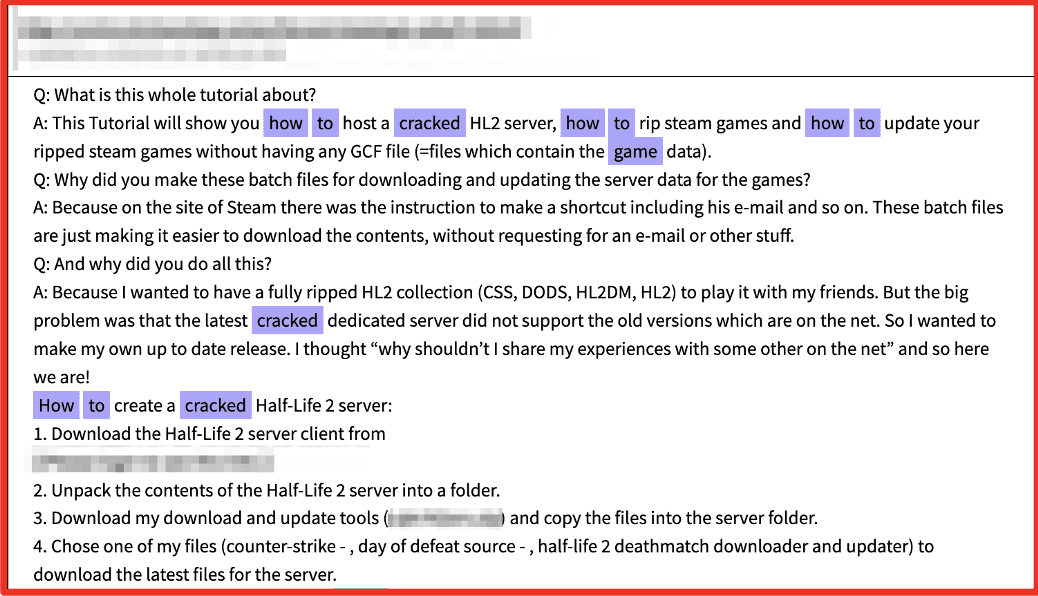
Figure 6: Source DarkOwl Vision DocID: 03ed2be2b016739aeeb6993d55655cd0d4791eef
Combolists
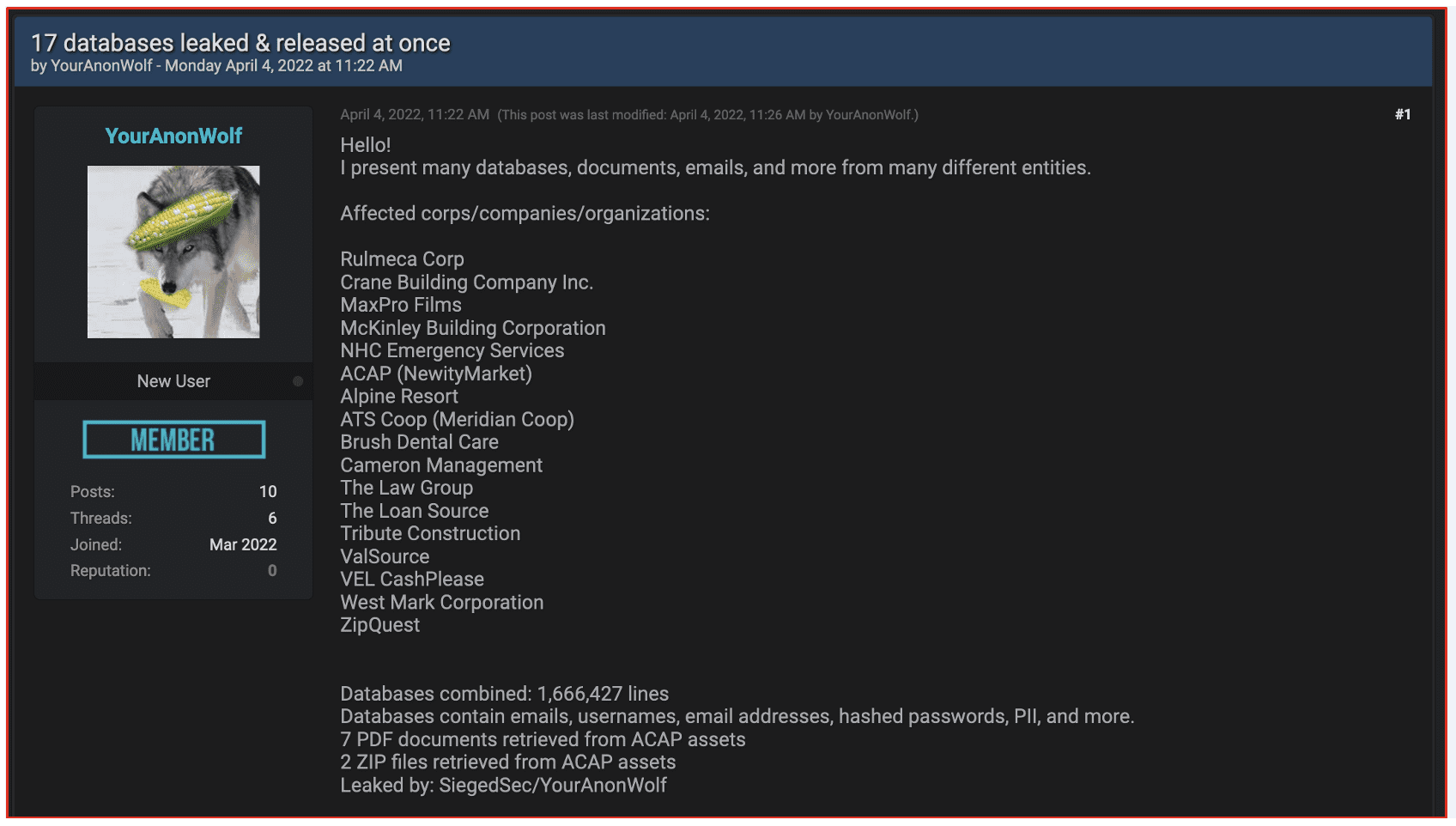
One of the fundamental tools an elite video gaming and streaming service account ‘cracker’ requires is a combolist. A combolist consists of a list of leaked usernames and passwords or email addresses and passwords combinations that can be used for cracking.
In the last year alone, DarkOwl has scraped nearly 100,000 documents across the darknet and deep web for offers of “combolists” from across the US, Europe, and Latin America. Most of the combolists are advertised as “private combos”, with hundreds of thousands of credential combinations in each combolist, and available for purchase on darknet marketplaces like Nemesis for under $20 USD.
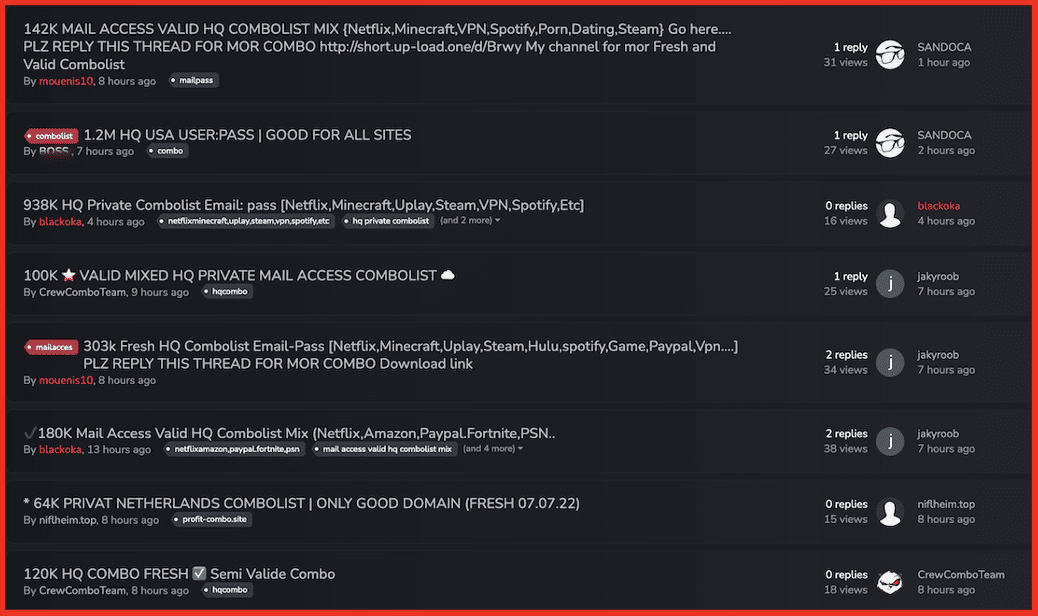
Figure 7: Marketplace Offering Combolists for Download and Purchase
The combolists are used in credential stuffing programs to validate the credential combinations work on the commercial gaming or streaming service authentication logins. With hundreds of thousands of combinations to work from, even a 1% success rate is a significant volume of accounts that a cracker could resell as a ‘cracked account’ for the platform.
Video Game Fraud, Pranks, & Scamming
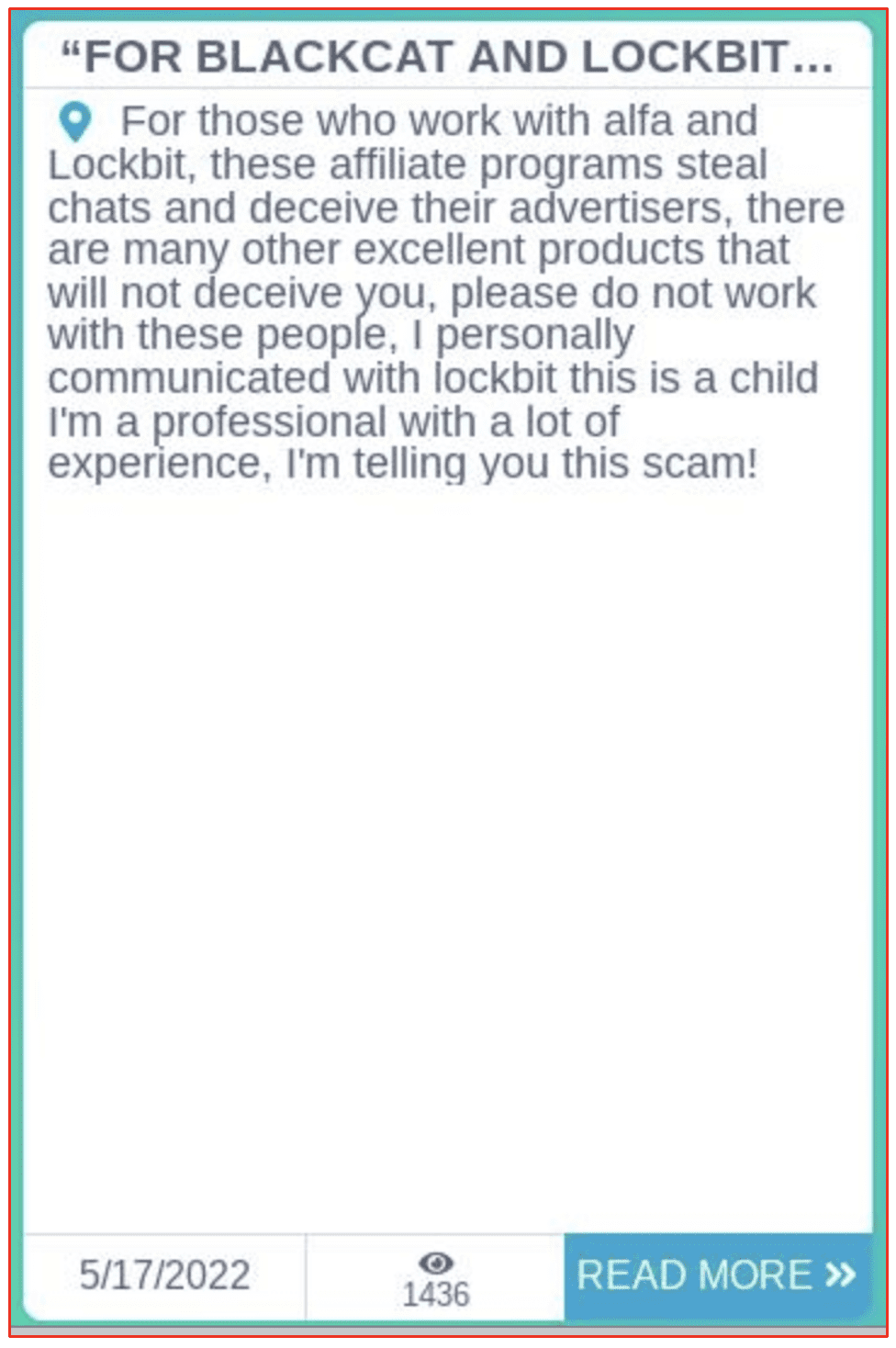
The darknet is known for widespread fraud and scamming and the video gaming community is perfect for exploiting its younger and often naïve users. With online gaming environments supporting multiplayer teams – that include a socialization and sense of community with group and private chats – gamers spend hours a week with their teammates creating very real sense of community and unfortunately, a false sense of trust and confidence in their online “friends.”
Many scammers play the criminal long game, willingly infiltrate online teams and lure the game participants to share personal information such as their real name, location, age, etc that can be used for identity theft and financial fraud. Not all of this social engineering is used exclusively for fraud. Some aggressive players gain this information to formally dox the players and SWAT them for the sake of online bullying and harassment.
To SWAT someone involves calling 911 (or similar emergency services) and lying about someone committing a serious crime, e.g. hostage, kidnapping, etc, to urge dispatchers to send a team of police officers, ideally a SWAT team, to a victim’s location. This is often carried out in the middle of a game or Twitch stream where the audio and video of the SWAT team arriving can be witnessed by others. Gamers will also prank victims with large deliveries of food like pizza that requires payment upon receipt.

Figure 8: Source DarkOwl Vision
Scammers will send other players third-party links to “cheats” and “gifts” for the game that are malicious in nature and often covertly install malware on the player’s device. Some of the links are simply phishing links that trick the victim into entering personal information, or their login in attempt to hijack the player’s gaming account for “cracked account” resale.
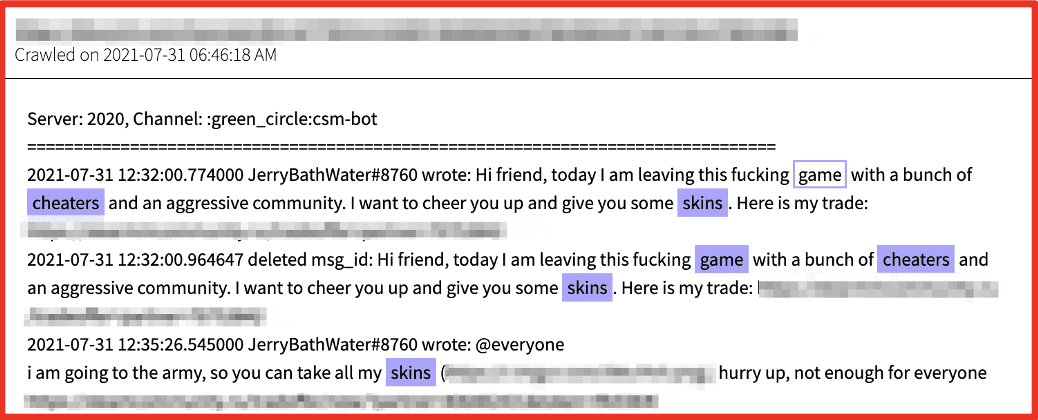
Figure 9: Source DarkOwl Vision
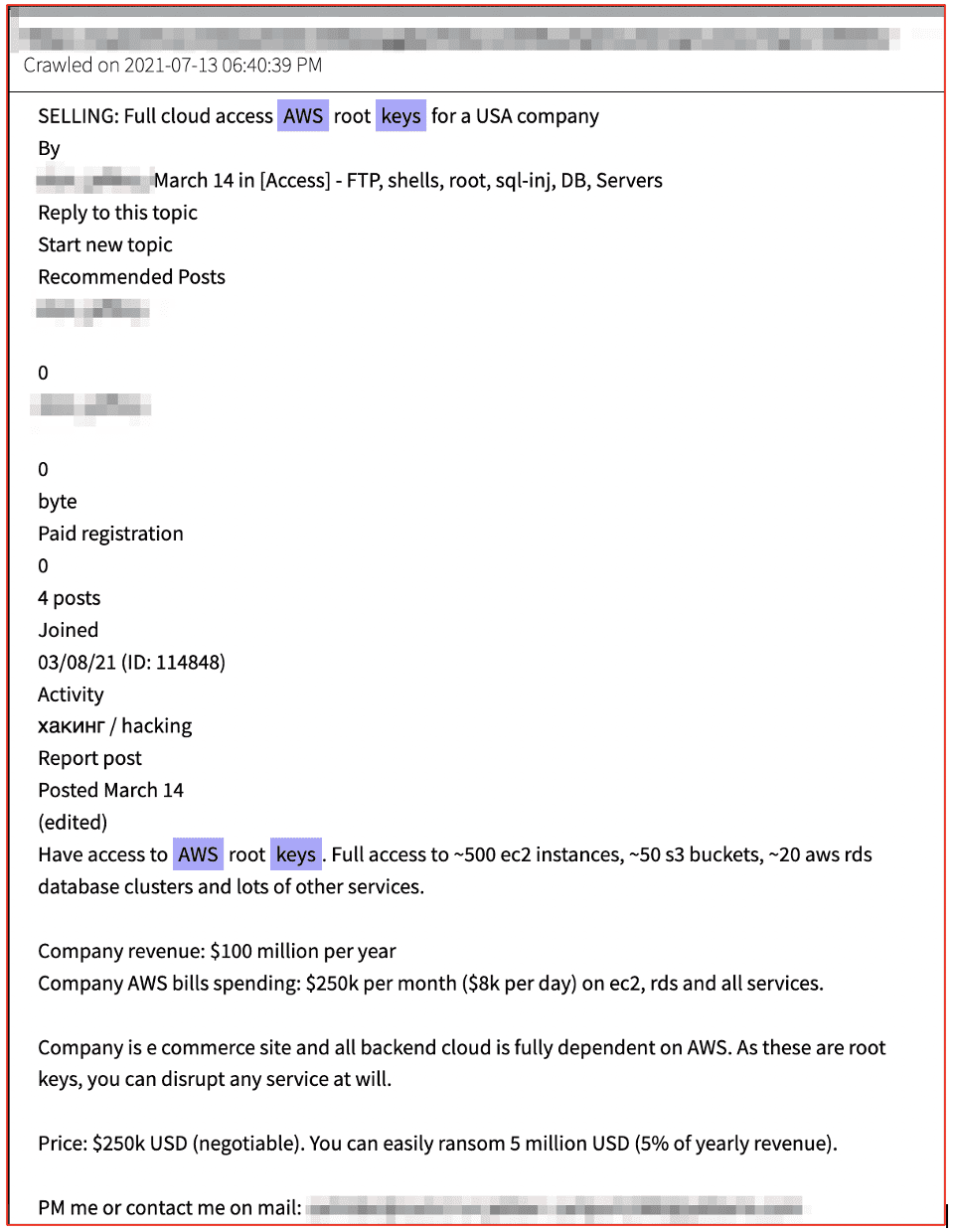
We have also captured offers for physical game consoles for sale on darknet marketplaces, which are often either stolen goods or buyers are scammed, cryptocurrency on the market loss as the electronics or console is never delivered.
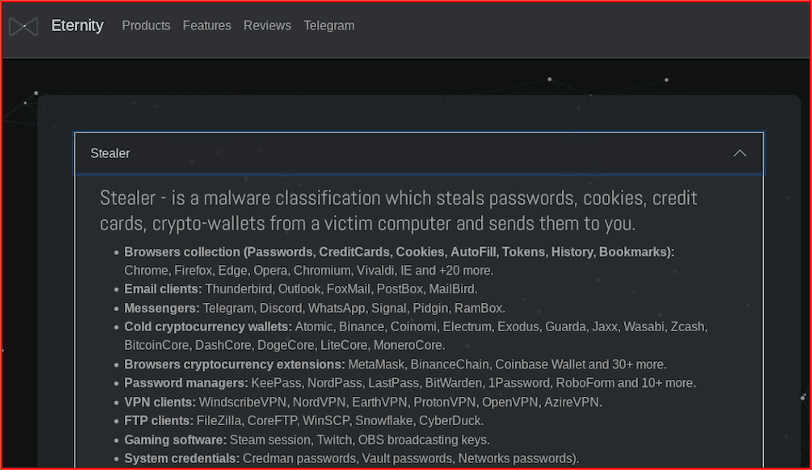
Some malware in circulation intentionally targets gamers for theft of personal information and fraud. According to open sources, there has been “cracking malware” like BloodyStealer, in circulation that behave like traditional information stealers, but target information specific to video game users like account logins and user tokens for Steam, Epic, VimeWorld, Discord, and EA.
Gamers Recruited for Criminal Activity and Information Operations
In recent years, chatter on darknet discussion forums and Telegram channels detail how political extremists have leveraged video gaming platforms and online communities for recruitment and socialization of political and societal ideologies. Gamers have stated both “fascists” and right-wing “Q” extremists have infiltrated popular video game group chats, spamming the chat with racial slurs and hateful rhetoric in attempt to trigger its players and evaluate how players react and respond.
Many users on the platform login to the game – not to play the game, as evidenced by their lack of skills and time actually playing – but to dialogue and post content to the game’s group and team chat for recruitment and information operations.
Open-source reporting by counter-terrorism specialists opines that some terrorist groups such as ISIS have utilized video game platforms and streaming communities like Twitch to spread their polarizing and violent political beliefs about controversial issues. The desensitization of first-person shooting games like Call of Duty and Grand Theft Auto (GTA) helps radicalization of individuals, especially teenagers between the ages of 11-17 years to carry out violent acts against marginalized groups in society.
Other young video gamers have been lured through video game communities to meet up with other users in-real-life (IRL) after establishing an online “friendship” through the game. Law enforcement have reported several of the young female gamers have ended up physically harmed, such as harvesting their organs, and even sold into sex-trafficking as a result of the in-person meet-ups.