Cyber Insurance and the Darknet: Part II
August 24, 2022
Earlier this summer we researched the cyber insurance industry and the darknet and reviewed basic policies, first- and third-party coverage and looked at a sample of the type of data insurers might want to monitor the darknet for. We discovered there is an increasingly complex interrelationship between data from the darknet and the organizations involved in issuing cyber liability insurance policies and managing claims.
Cyber Insurance is not a Substitute for Cyber Defense
Surprisingly, we also discovered that most cybersecurity liability insurance policies exclude incidents caused by human error or negligence and events easily preventable by a stable and secure IT defense posture – proving that security professionals cannot become lackadaisical about their security posture simply because they have procured a comprehensive cyber insurance policy.
Organizations should not be fooled into thinking that cyber insurance is a substitute for robust cybersecurity defense and response.
Some popular exclusions of cyber liability insurance include:
- Lack of security processes (or poorly developed): Having detailed security policies and a comprehensive incident response plan is necessary for insurance underwriting;
- Prior breaches: Data leaks or incidents that occurred before the organization purchased their policy;
- Lost mobile IT devices: Most cyber liability insurance policies do not cover lost or stolen personal mobile devices, for example, company CEO leaves mobile phone on an airplane or in an Uber;
- Human error: Any cyberattack triggered by basic human error of an organization’s employee;
- Insider attacks: The loss or theft of data due to an ‘insider attack’ –an employee initiating the cyberattack from within the organization or using their authorized organizational access to launch the attack;
- Pre-existing vulnerabilities: Like a pre-existing medical condition, if there are documented evidence of previously determined network vulnerabilities and the company fails to remediate, then the resulting cybersecurity incident is not covered;
- IT infrastructure security improvements: Any costs related to improving the security of information technology systems, e.g. hardening applications and networks;
- Criminal litigation: Claims brought as result of grand-jury proceeding or criminal investigation or action;
- Acts of War: Traditional insurance policies do not typically cover property damaged during war-time, often referred to as the ‘hostile act exclusion.’ The same is true for nation-state sponsored cyberattacks against businesses.
Given we are in a time of the first ever global cyberwar as the result of Russia’s invasion of Ukraine and CISA has advised an increased security posture for all critical industry sectors, CISOs and security professionals should never speculate on their coverage and review their cyber insurance policies carefully.
Cyber insurance policies should augment organizational security processes, not replace them. Insurance carriers must carefully analyze all potential policy holders’ security posture and insist on robust security position prior to issuing the policy. Cyber insurance underwriters should carefully consider the security posture of policy applications through thorough pre-policy questionnaires and employee interviews, evidence of robust and regular employee security training, domain network scanning, darknet monitoring and exposure analysis.
Evidence of a policy holder’s prior breaches, organization credential exposures, and and the risk of insider attacks can be evaluated using a robust darknet database, like DarkOwl Vision.
Insider Risk Increasing & Not Covered by Cyber Liability Insurance Policies
DarkOwl has observed numerous darknet threat actors actively recruiting disgruntled employees a.ka. ‘insiders’ to help carry out their attacks and shorten the attack timeline; notably in the ransomware/extortion-as-a-service model of the criminal underground. Banking and financial fraud specialists have advertised they were seeking banking insiders and cyber criminals have offered $500 – $1,000 USD to AT&T and other mobile carrier providers who can assist with sim-swapping. Some recruitment offer payment on swap or a percentage commission on the value of the fraud conducted.
On Telegram, LAPSUS$ openly recruited insiders to help with their attacks calling for employees at telecommunications, software and gaming corporations, call centers, and web/server hosting organizations. They specifically asked for the employees to have remote access via VPN, Citrix or anydesk applications.
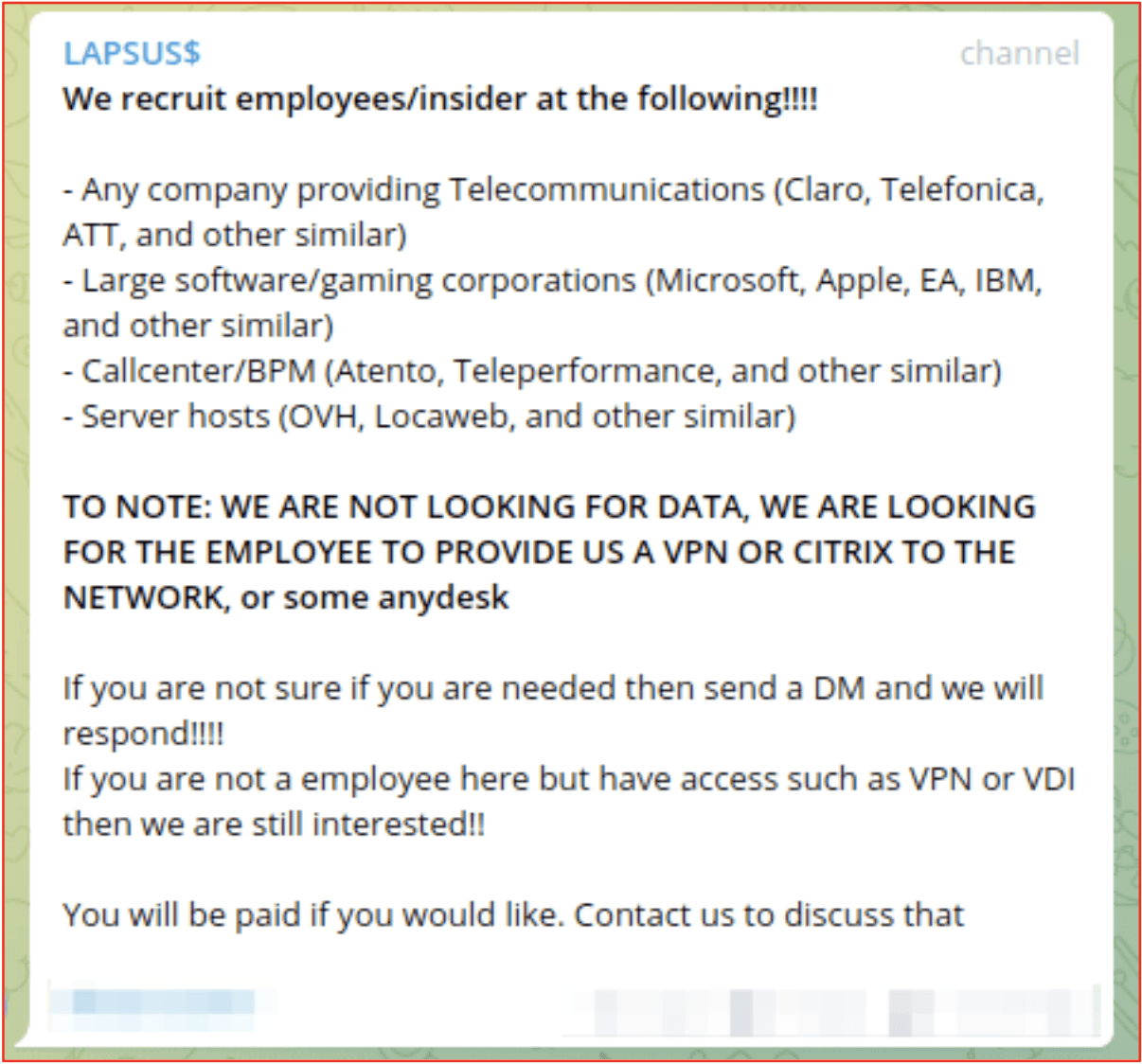
Figure 1: LAPSUS$ Criminal Gang’s Recruitment of Insiders to provide VPN or Citrix Network Access
Government, healthcare, and Insurance carriers are also targeted for insider recruitment in a recent deep web post captured by DarkOwl (below).
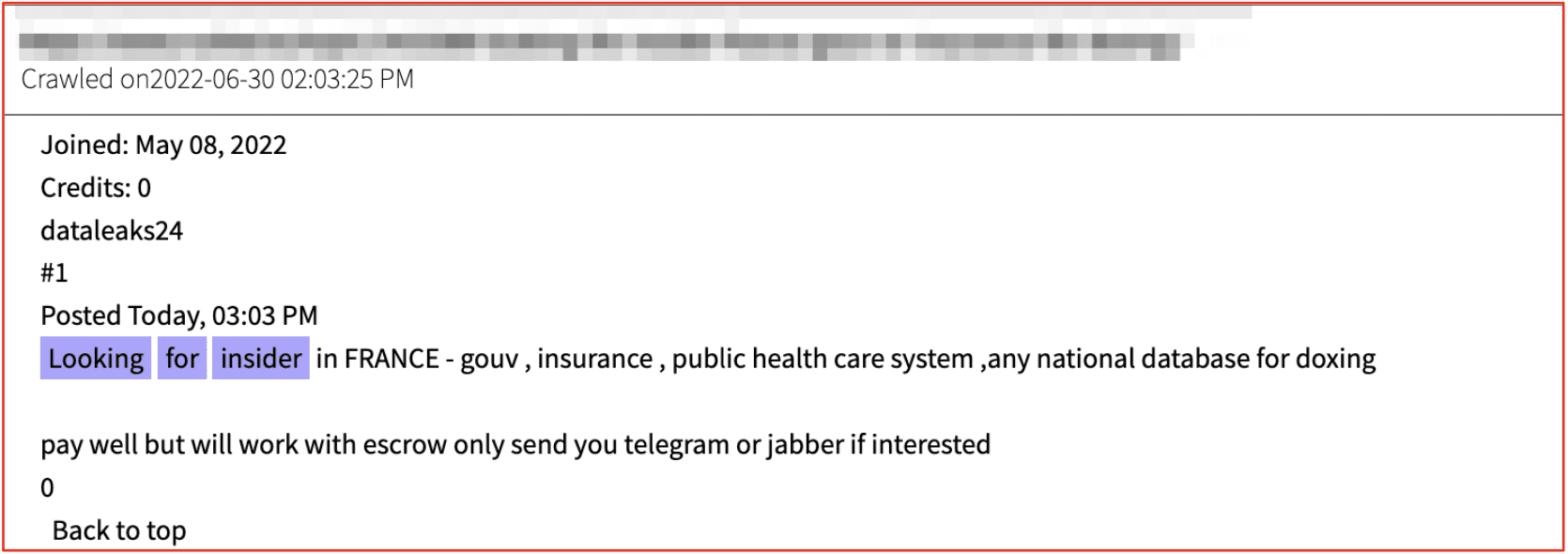
Figure 2: Source DarkOwl Vision
In early July, in an unusual insider-threat example, a HackerOne employee exploited their internal access to bug reports to duplicate the reports and gain financial payment for the bug bounty program. In this scenario, the fraudulent payments could not be recovered by their cyber liability insurance, unless specifically stated in their policy.
Prior Breaches & Organizational Exposures
In addition to monitoring for mentions of organizational credential data, like email addresses, hashed and cleartext passwords, and authentication data like session tokens and API keys, DarkOwl Vision can also provide indication of prior breaches and leaked data.
Cyber criminals regularly offer to sell or share organizational information they obtained on the darknet. Such data could indicate a potential prior breach occurred at the organization. In August 2020, a post on Telegram indicated a cybercriminal had obtained significant confidential data from the Intel Corporation. The leak allegedly included over 20GB of documents and product roadmaps for multiple technology programs in Intel for only $ 200 USD.
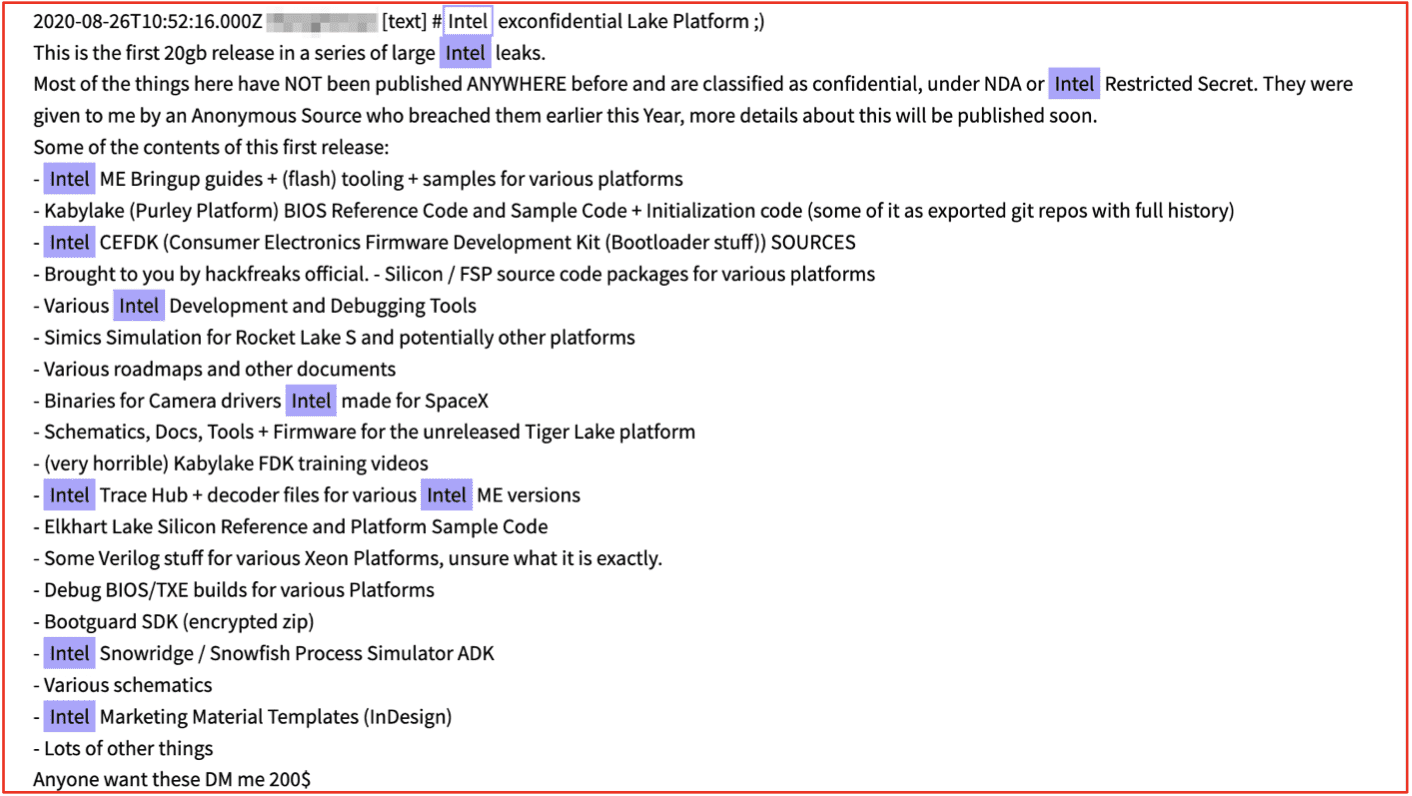
Figure 3: Source DarkOwl Vision
In the middle of an attack or immediately thereafter, threat actors often openly shame the victim and their associated IT security departments for haphazard network security, ‘poor digital hygiene,’ and private information protection. We recently captured a threat actor sharing proofs of exfiltrated victim data – in an apparent ransomware attack – and simultaneously stated this was not the first time they had been targeted and the personal data of clients compromised.
The threat actor even alleged they had tried to reach out to the company and provide recommendations on how to secure their corporate network.
“No matter if this is a medicine company, even they do not respect professional ethics and doesn’t care about private information regarding clients, employees, medicine tests, hospital cards, drug tests and researches and any other sensitive Data. They have a lot of vulnerabilities and absolutely careless IT service. We are trying to reach them to help resolve issue and provide a recommendations about how to fix such a bugs in the corporate network. Moreover it’s not the first time they have an issue with IT security and get a breach in their network, so it’s obviously that XXX is not able to protect own Data and personal Data of clients, so everyone can be convinced soon when we will provide the access to the files from one of their servers – XXX from central office with about 5,7TB of Data (and this is just a minor part of what we were able to download). We never tell lies when we saying that we have something, unlike XXX security team, which are telling in the internal or public reports that nothing is compromised and all is in safe. As a final try we are publishing here just a little piece of proof just in the hope that someone from CEO will notice and take under control this issues.” – Source, DarkOwl Vision
Attacks Against Insurance Industry Persist
Ransomware gangs show no slowdown in targeting the insurance industry with several new attacks independent agents and family-owned insurance-affiliated businesses around the world in recent weeks. REvil’s stated intention to gain additional information about insurance policyholders for the sake of exploiting that information for future gain in negotiations and targeting is apparent. We continue to witness proofs and announcements of attacks against independent agents and family-owned insurance-affiliated businesses around the world regularly posted by some of the most active and successful ransomware gangs in operation.
Figure 4: Source DarkOwl Vision
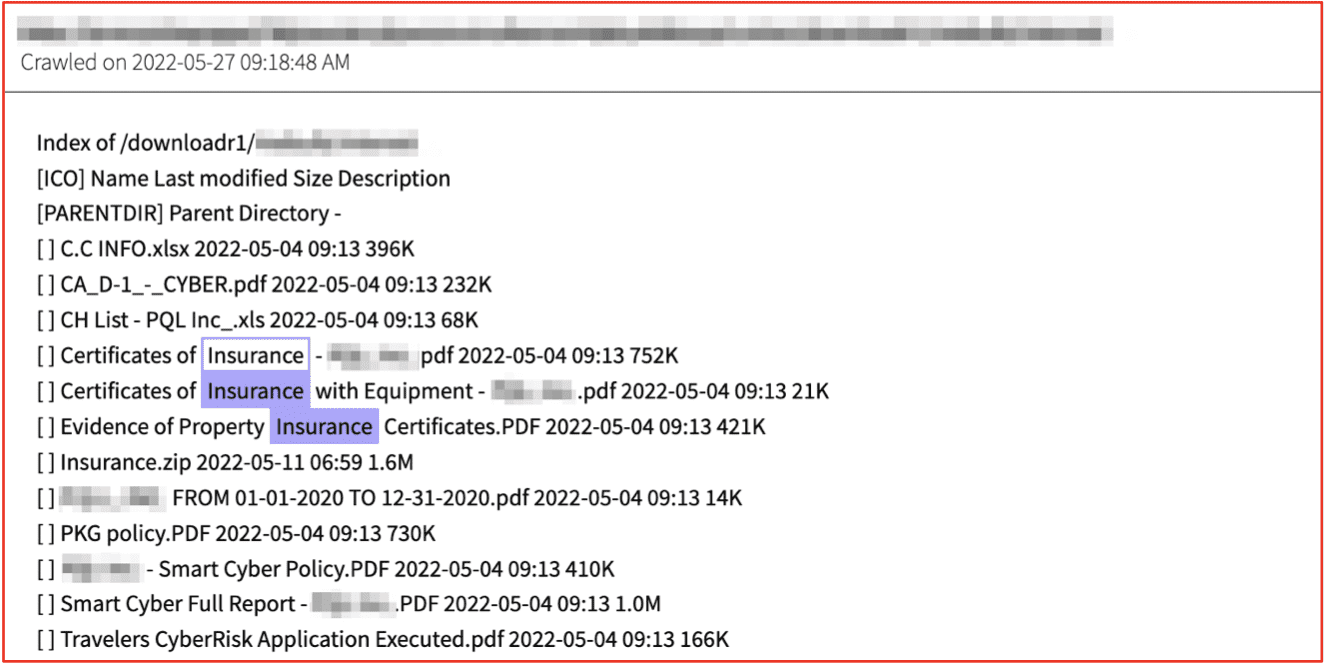
Figure 5: Insurance Policies, Cyber Risk Assessments, and Certificates of Insurance Shared From Victim Network – Source DarkOwl Vision
Any entity that interacts with insurance companies are also at risk of cybersecurity incident or ransomware attack. We have seen ransomware gangs target business processing companies, insurance brokerage network and underwriting service providers, as well as legal firms that support the insurance industry.
DarkOwl recently observed a legal firm that focuses on representing insurance carriers in disagreements with their policy holders shamed on the LockBit ransomware blog. Earlier the same group shamed the insurance company Risk Strategies – calling their web domain out on another victim’s announcement for not paying a more significant amount for their attack against the policyholder, another legal services company.
Do not use the insurance company risk-strategies.com it will not help you in case of hacker attack, XXX were insured for 1 million dollars, and the fucking faggot insurance agent was able to offer the maximum amount of 45 thousand dollars, this is fraud in the purest form. A full-service law firm delivering consistent, successful results for more than 100 years. Among the fastest growing law firms in the southeastern United States. Our services are customized because each client’s situation is unique. XXX attorneys focus on meeting your current needs, achieving the best possible results, in a cost-effective manner.
– Posted March 2022, Source LockBit Ransomware Blog on Tor
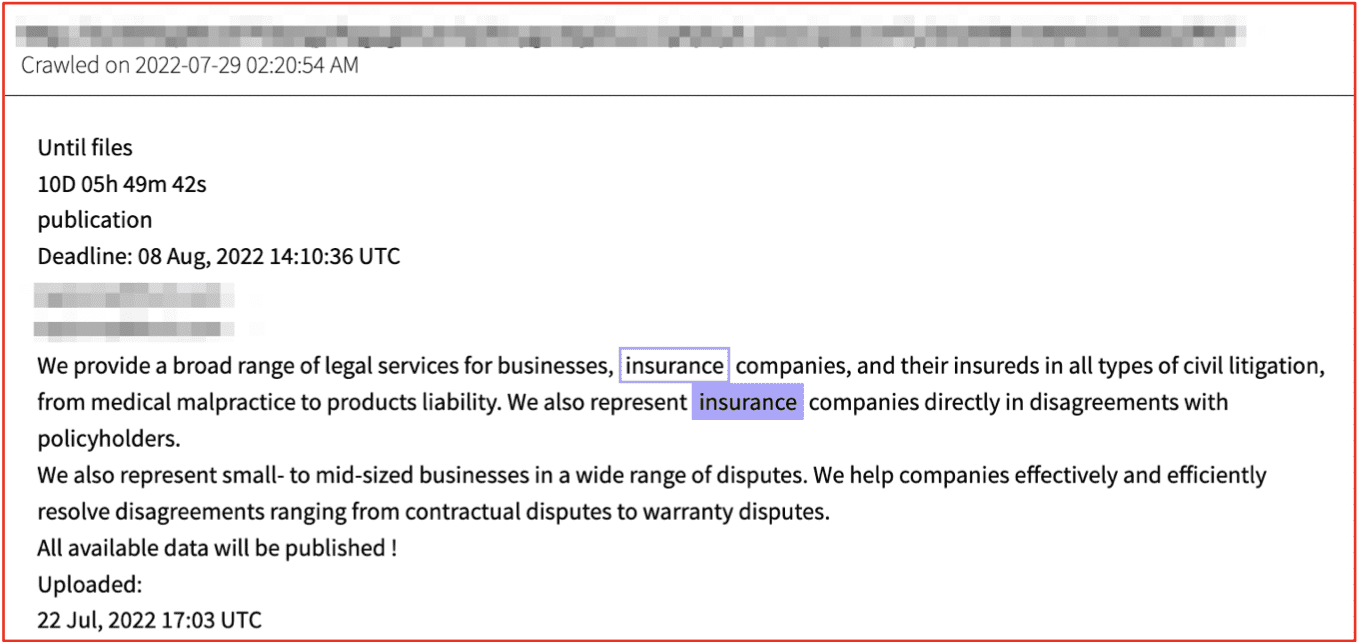
Figure 6: Source DarkOwl Vision
In this piece, we reviewed how cyber liability insurance is not a substitute for solid corporate network security protocols. We reviewed a number of cyber insurance policy exclusions such as war-time, insider threats, and prior breaches, and looked at some examples where the insurance industry itself continues to be targeted by darknet threat actors.
Learn how darknet data available in DarkOwl Vision can help drive better risk decisions in issuing policies and persistent monitoring for on-going security risks to insurance carriers, brokers, and their policy holders. Contact us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















