Cybercriminal Arrests: 2022 Lookback
April 20, 2023
Cybercriminals who see the most return on their cybercrime-related activities can also suffer the greatest consequences at the hands of law enforcement. Despite the anonymous nature of the darknet, law enforcement has developed sophisticated tools and procedures to take down the most notorious criminals who operate on the darkest corners of the internet.
Major cybercrime arrests of 2022 show insights into the operations and true identities of several noted cybercriminals. This includes individuals involved in sophisticated illicit cyber activity from as young as age 15, business entrepreneurs who were virtually unknown in the darknet community, and whom no one suspected, to those who committed the crime a decade ago. DarkOwl analysts round up some of the most notorious arrests of 2022.
Diogo Santos Coelho (aka “Omnipotent”, aka “downloading”, aka “shiza”, aka “Kevin Maradona”)
The case of Diogo Santos Coelho, aka omnipotent, highlights the importance of OPSEC (operational security) and illustrates that many notorious cybercriminals, or hackers can be very young. On Tuesday April 12, 2022, the United States Department of Justice announced the seizure of RaidForums and unsealed criminal charges against Diogo Santos Coelho, RaidForum’s alleged administrator. He was arrested on January 31 in the United Kingdom. The six-count indictment against Coelho charged him with conspiracy, access device fraud, and aggravated identity theft. The FBI allege that he was the administrator to RaidForums from around January 2015 to January 2022.
RaidForums was a popular online marketplace known for providing leaks and breaches for sale or sometimes for download, either via credits accrued on the site or for free. These leaks could include powerful personal identifiable (PII) and financial information, ranging from social security numbers to credit cards, and would be used by criminals to commit fraud as well as accessing company networks. RaidForums was taken down in Operation TOURNIQUET, which was a joint operation with Europol, the United States, the United Kingdom, Sweden, Portugal, and Romania. Similar key cyber operations and law enforcement agencies involved in darknet takedowns can be found in DarkOwl’s interactive timeline.
Court documents show that Coelho used the names OMNIPOTENT, DOWNLOADING, SHIZA, and Kevin MARADONA. OMNIPOTENT and DOWNLOADING were used on the RaidForums site. In addition to being an administrator, the indictment shows he also provided a middleman service for buyers and sellers on the site. Searching in DarkOwl Vision, it appears that there is no honor among fellow thieves on the darknet, as Coelho was then subsequently doxxed.
According to DarkOwl’s darknet glossary, a dox is to publicly name or publish private information (PII) about an unwitting target. Doxxing can be used as a form of aggression between conflicting groups, such as when 22 members from Trickbot were doxxed as part of the Russia-Ukraine cyberwar by a pro-Ukrainian affiliate. Other times it is to express political opinions.
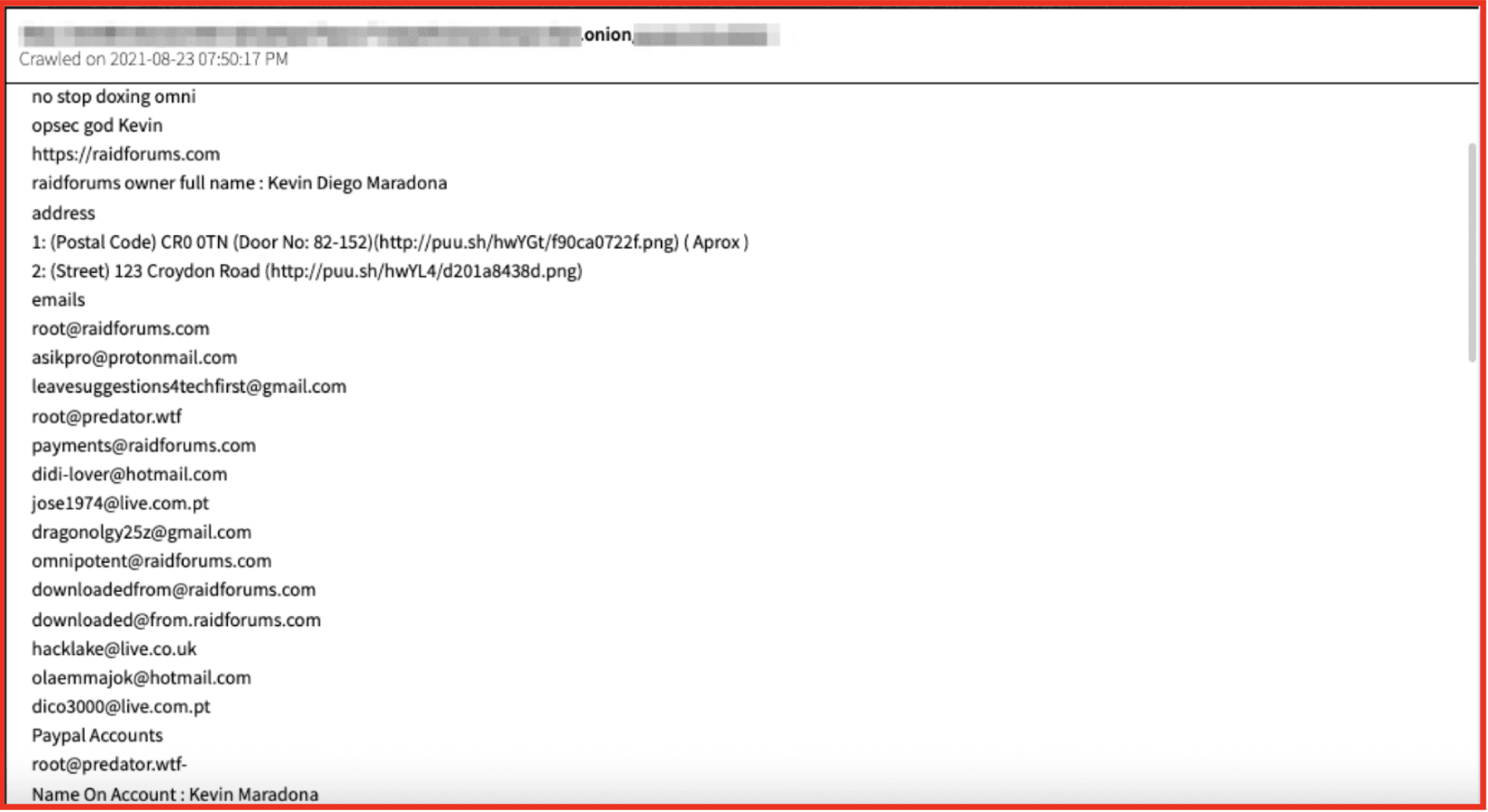
Figure 1: Screenshot of Omnipotent Doxx; Source: DarkOwl Vision
As seen in Figure 1, the name on the account is “Kevin Maradona.” Using DarkOwl Vision email lexicon, the email didi-lover[@]hotmail.com is in a document linked to omnipotent[@]raidforums.com, Kevin Mardona, and his address. It is not known exactly the techniques that law enforcement used to identify Diogo Coelho, however, personal information such as emails, aliases, and addresses all help investigations. Law enforcement were able to seize three domains which hosted the RaidForums site, leading to further investigations.
Not only did Diogo Santos Coelho establish arguably the most popular online marketplace to illegally buy, sell, and trade highly sensitive information from around the world, but he started this site when he was only 15 years old.
Ilya “Dutch” Lichtenstein and Heather Morgan (aka “razzlekhan”)
The indictments against Ilya Lichtenstein and Heather Morgan of New York were ones that no one, except perhaps the IRS, saw coming. Both were known in the business world and involved as entrepreneurs in startups. Morgan even had an online rapper persona, Razzlekhan. The couple was arrested in New York and charged with Money Laundering Conspiracy and Conspiracy to defraud the United States. The indictments stem from their alleged attempts to launder $3.6 billion in stolen bitcoin from the Bitfinex exchange hack.
It is alleged that Lichtenstein and Morgan moved the funds through multiple transactions to different accounts across separate platforms to try and hide the paper trail. U.S. law enforcement successfully traced the stolen bitcoin via the blockchain to several accounts owned by Lichtenstein and Morgan. Lichtenstein kept the addresses and keys in cloud-storage which law enforcement was able to decrypt and discovered a file with 2,000 cryptocurrency addresses and the private keys to each. A federal magistrate judge in New York ruled that Morgan and Lichtenstein be released on bond for $3 million and $5 million respectively. However, the Chief U.S. District Judge ruled that Morgan may return home to New York “under strict conditions” but that Lichtenstein must remain in prison in the District.

Figure 2: Picture of Heather Morgan who called herself a cold-email expert; Source: Forbes.com
Sebastien Vachon-Desjardins
NetWalker Ransomware group primarily targeted healthcare and education institutions as well as other sectors such as law enforcement, companies, and emergency services. Most well-known for taking advantage of the global COVID-19 pandemic to leverage targeted attacks against their victims, NetWalker distributed pandemic-related phishing emails to target healthcare institutions already pushed to their max by the global health crisis.
In January of 2021, the Department of Justice announced the successful disruption of NetWalker ransomware group as the result of an international law enforcement operation. Law Enforcement were able to seize almost $500,000 and Canadian national Sebastien Vachon-Desjardins was charged with wire and computer fraud, “intentional damage to a protected computer, and transmitting a demand in relation to damaging a protected computer arising from his alleged participation in a sophisticated form of ransomware known as NetWalker.” In March of 2022, the Department of Justice announced Sebastien Vachon-Desjardins’ extradition and the seizure of $28,151,582 of cryptocurrency after executing a search warrant.
Conspiracy to commit computer fraud and wire fraud, intentional damage to a protected computer, and transmitting a demand in relation to damaging a protected computer arising from his alleged participation in a sophisticated form of ransomware known as NetWalker.
On October 3rd, 2022 Sebastian Vachon-Desjardins was sentenced to 20 years in prison (following his extradition to the U.S.). He agreed to give up $21.5 million as part of a plea agreement. He is believed to have been a key active affiliate for the ransomware NetWalker group and is rumored to have close affinity with the hacking group REvil.
Information from the seizure of NetWalker’s backend servers in Bulgaria highlighted the true number of victims exploited by the group. The FBI reports that 115 victims filed a report, however, the true number of victims is likely between 400 to 1,500. In the words of U.S. Attorney Roger B. Handberg, “the defendant in this case used sophisticated technological means to exploit hundreds of victims in numerous countries at the height of an international health crisis.”
Figure 3: Screenshot from NetWalker’s darknet blog; Source: DarkOwl Vision
Mark Sokolovsky (aka “photix”, aka “raccoonstealer”, aka “black21jack77777″)
On October 25, 2022 a grand jury unsealed indictment charges against Ukrainian national Mark Sokolovsky due to his alleged role in Raccoon Infostealer as a core member. Raccoon stealer is a prolific infostealer which functions using a malware-as-a service model. Raccoon stealer is available for purchase for around $200. Customers (typically cybercriminals) receive access to a control panel with the most recent version of the malware, could work on infected systems in real time, and see the stolen data such as logins and credentials and interact with the ransomware.
Information stealers such as Raccoon are a type of infostealer malware, also known as a Trojan or a remote access tool (RAT), that is designed to steal sensitive information from victims’ computers or devices. Once infected, Raccoon typically operates in the background, while it systematically searches for and collects a wide range of data from the compromised system. This data can include login credentials, credit card numbers, social security numbers, banking information, and other types of personal and financial data. Raccoon may also capture screenshots, record keystrokes, and log other user activity to further gather information. This data is collected and leveraged for fraud and exploitation such as identity theft or the draining of bank accounts. At the time of the indictment, the FBI found over 50 million unique credentials and pieces of identification taken with the stealer’s help.
Sokolovsky is charged with one count of conspiracy to commit computer fraud and related activity in connection with computers; one count of conspiracy to commit wire fraud; one count of conspiracy to commit money laundering; and one count of aggravated identity theft.

Figure 4: Mark Sokolovsky leaving Ukraine and avoiding mandatory military service, taken at the Polish border; Source: KrebsOnSecurity.com
James Zhong
The Silk Road was notoriously one of the first well-known and most used darknet marketplaces created by Ross Ulbricht, a.k.a Dread Pirate Roberts. The marketplace was shut down by law enforcement in 2013. However, billions of dollars were unaccounted for despite the site’s seizure. In November of 2022, the Department of Justice announced they found $3.36 billion worth of Bitcoin that had been stolen from The Silk Road around 10 years before. It was hidden in a popcorn tin in a bathroom closet along with Casascius coins and bars of precious metals. $661,900 in cash was also seized.
The announcement from the Department of Justice read that in 2012 Zhong made 9 accounts on The Silk Road and triggered over 140 transactions “to trick Silk Road’s withdrawal-processing system into releasing approximately 50,000 Bitcoin from its Bitcoin-based payment system into Zhong’s accounts” which he then put through cryptomixers and moved to various accounts to cover his tracks. Zhong gave up 1,004.14621836 Bitcoin to the government. He pled guilty to one count of wire fraud.

Figure 5: The popcorn tin where the criminal proceeds of James Zhong was found; Source: Department of Justice

Figure 6: Some of the physical Bitcoins (Casascius coins) and other items seized by law enforcement; Source: Department of Justice
Paige Thompson (aka “erratic”)
The case of Paige Thompson highlighted the potential grey area between a white-hat hacker and a cybercriminal. The former Amazon employee was responsible for a major breach in 2019 when she downloaded and posted to the darknet the personal information of more than 100 million Capital One users. The data included 140,000 social security numbers and 80,000 bank account numbers.
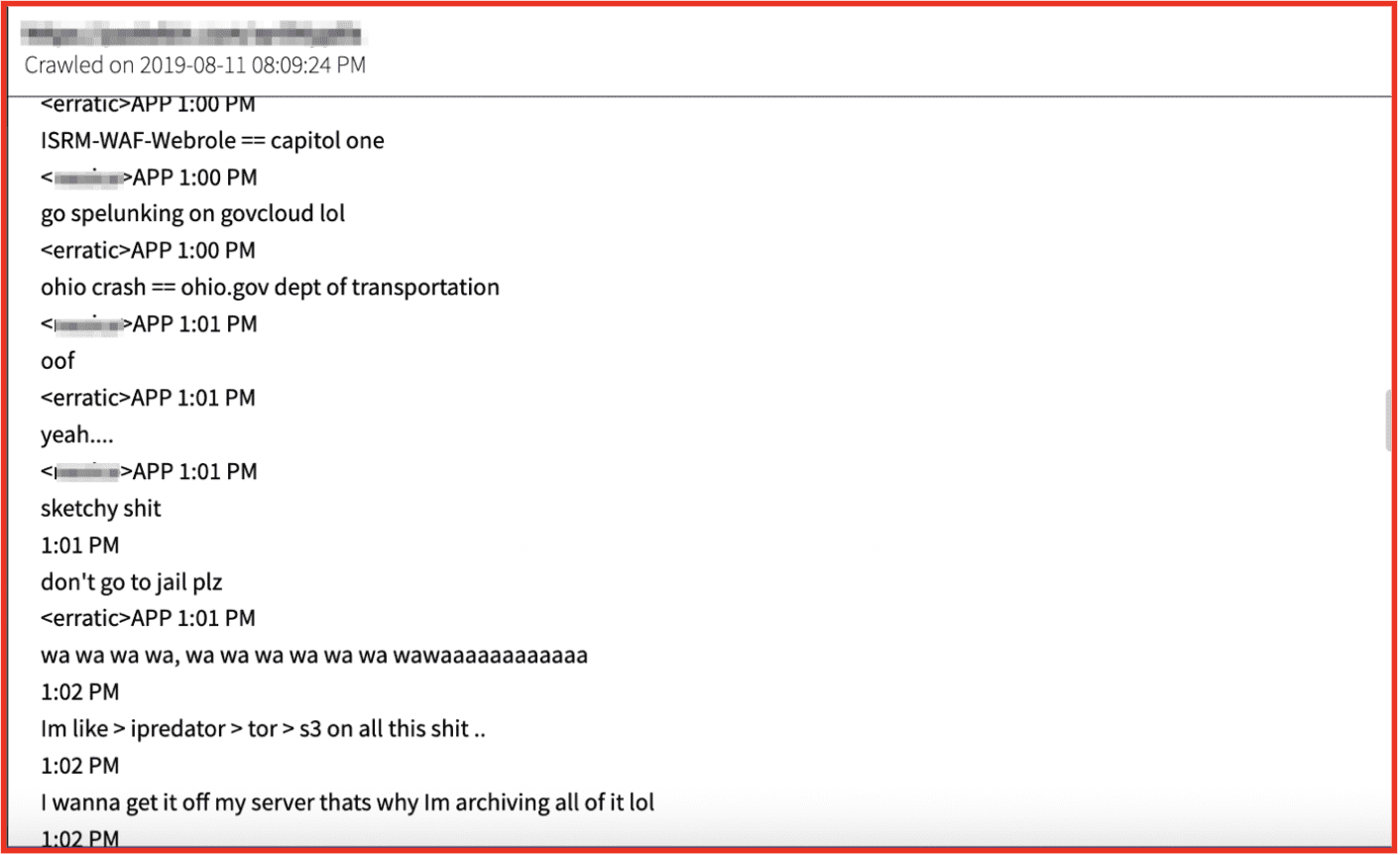
Figure 7: Paige Thompson, alias “erratic” posting on a forum the Capital One data; Source: DarkOwl Vision
Prosecutors said Paige Thompson exploited misconfigured web application firewalls to get credentials stored by customers with a Cloud Computing Company, access sensitive data and use the servers to mine cryptocurrency. Her lawyers argued that her actions fall under the category of a white-hat hacker, as she was scanning for online vulnerabilities and probing what they exposed. The Federal Government contends that she had no intention to disclose the vulnerabilities and wanted to use the stolen information for her own gain.
She pled not guilty for violating the Computer Fraud and Abuse act. She was found not guilty of identity theft and access device fraud but was found guilty of wire fraud, damaging a protected computer, and five counts of unauthorized access to a protected computer. Capital One paid $80 million to regulators and $190 million to the people whose sensitive information was exposed.
Conclusions: Law Enforcement is Never Far Behind
Cybercriminals who commit large crimes are likely to attract the attention of law enforcement. However, the illicit cybersphere is so decentralized that it would take many, many years for law enforcement to track down every cybercriminal.
To help facilitate these efforts, law enforcement agencies have developed sophisticated tactics to attribute online crimes to people even if they are working in an anonymous environment. Using darknet search and monitoring services such as DarkOwl is one such tactic favored by law enforcement as it allows investigators to gather evidence and follow leads over time in order to build a robust case.
To learn more how DarkOwl can aid in cybercriminal investigations, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















