Dark Web Groups Turn Their Attention to Israel and Hamas
October 10, 2023
Disclaimer: DarkOwl is not affiliated with any of the groups mentioned in this article and do not support the actions of cybercriminals regardless of their motivations. This information is provided for informational purposes only and has not been independently verified.
Other Resources Since the Publication of This Blog:
- Hamas Affiliated Channels Quiet Preceding Invasion?
- Monitoring the War in the Middle East
- 23andMe Suffers Data Breach
- Hacktivist Groups Use Defacements in the Israel Hamas Conflict
- Iran’s Role in the New Middle East Conflict
- 2 Month Review of Cyber Activities in the Israel Hamas Conflict
- Israel and Hamas Conflict: A 6 Month Review
Introduction
The world was shocked by the invasion of Hamas insurgents into Israel along multiple entry points from the Gaza Strip on October 7, 2023. This has led to a huge number of posts, images and videos being shared of the incursion and atrocities on social media but also on the dark web and dark web adjacent sites.
DarkOwl analysts are closely monitoring this situation and have identified a wealth of information being shared, some of it legitimate and some likely to be disinformation. We will be authoring a series of blogs showing our initial findings as well as providing new information as it is uncovered.
Here we provide information relating to known cyber groups active on Telegram and how they have reacted to the invasion.
Which Side to Pick?
As events unfolded over the weekend, chatter on several Telegram channels monitored by DarkOwl turned towards Israel and Hamas and the events unfolding in the Middle East. A number of these groups have been heavily involved in the Russian Ukraine Conflict supporting one side or the other and posting leaked information, DDOS attacks and defacement among other things.
Some groups quickly pledged their support for one side or the other. Killnet posted their intention to target the Israeli government, posting in both Russian and Hebrew, stating this was due to Israel’s support for Ukraine. An affiliate of theirs Anonymous Sudan quickly followed suit.
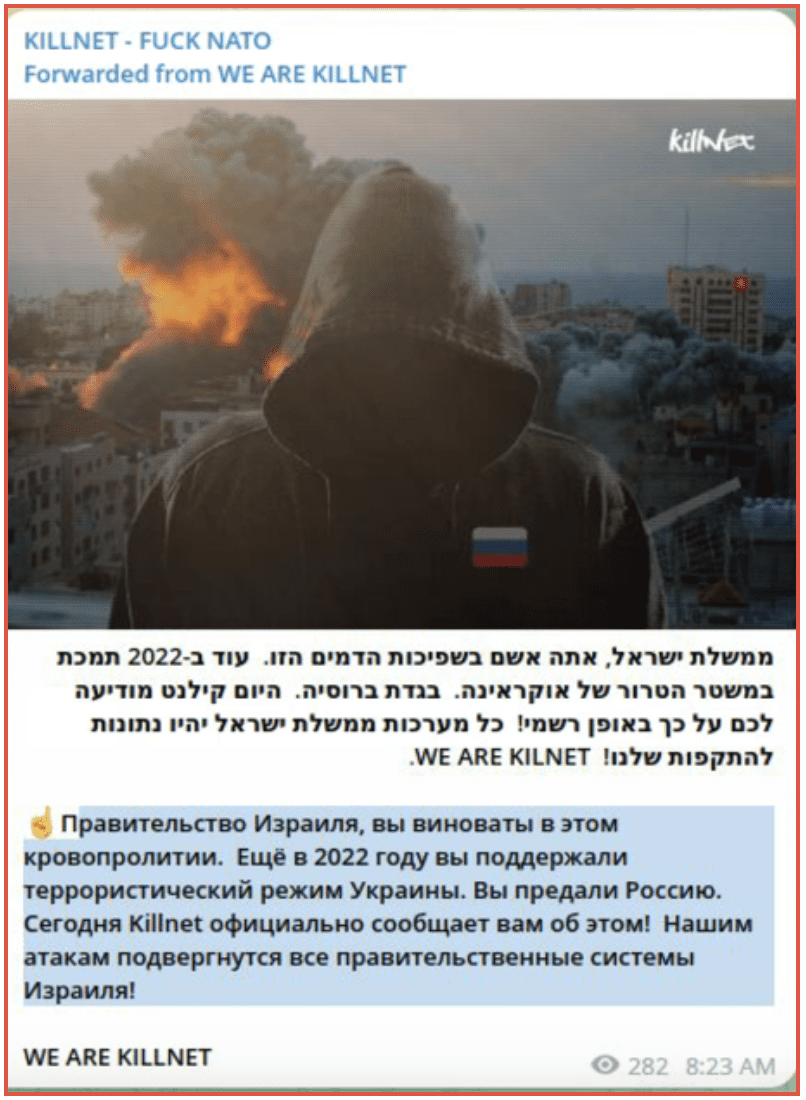
Figure 1: Killnet Telegram channel

Figure 2: Anonymous Sudan Telegram channel
The Five families, including SiegedSec and GhostSec posted on October 7 confirming their support for Palestine/Hamas. These groups have been very active on behalf of Russia in the Ukraine Russian conflict.
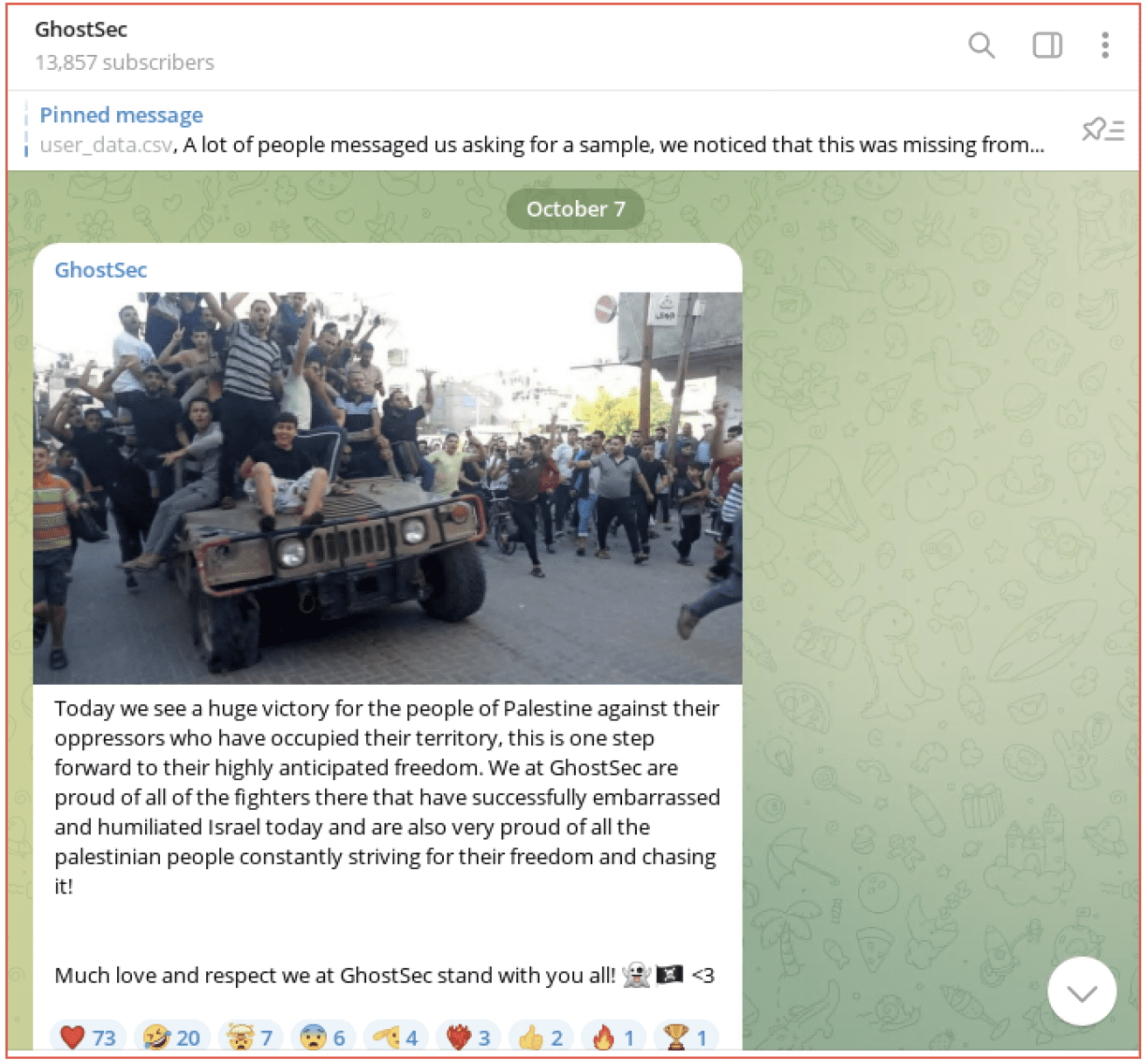
Figure 3: GhostSec Telegram channel
A hacktivist group known as Cyb3r Drag0nz who has targeted several groups and organizations from many countries posted a poll to their public channel asking them which country they should support. They quickly began activity in support of Palestine.
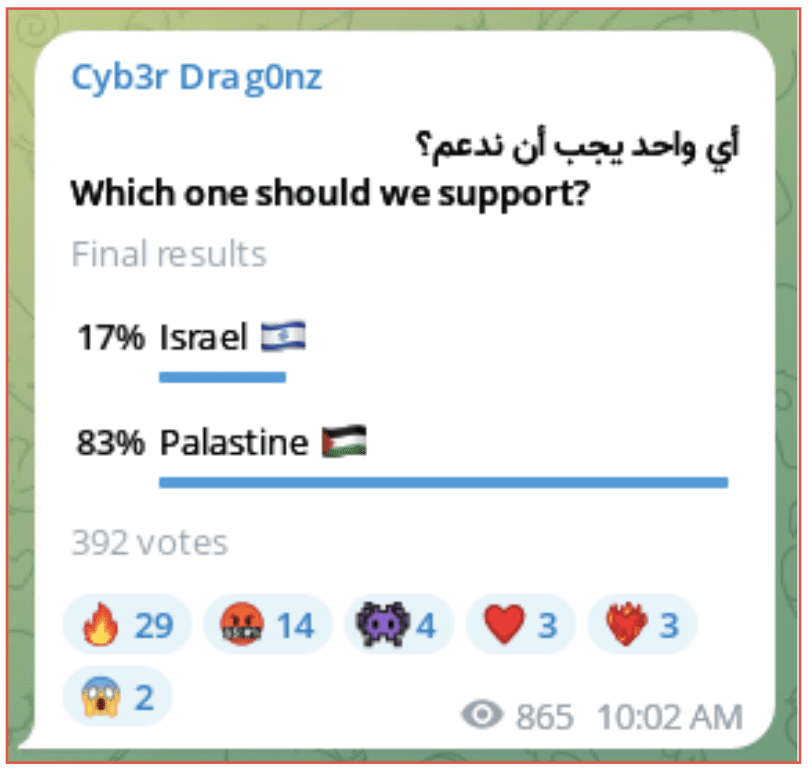
Figure 4: Cyb3r Drag0nz Telegram channel
A ransomware group known as RansomVC, was reported to be buying access to any countries affiliated with Gaza, including Iran and Palestine. Although no other information was provided it is likely this means the group is planning to attack organizations within these countries.
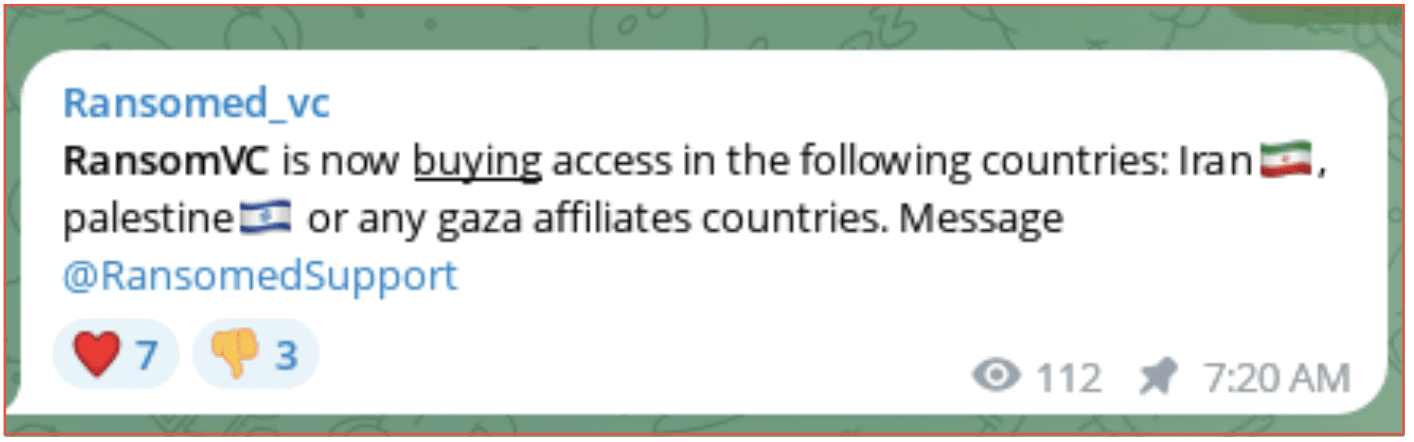
Figure 5: RansomedVC Telegram channel
The threat group ThreatSec stated it didn’t like Israel but that they also don’t like war, so they plan to attack the Gaza region as that is where many of the Hamas fighters are located. They later had to clarify this statement saying they are neither on the side of Israel or Palestine and they want to stay neutral. So, they will target both countries.
The group Garuna Ops made a number of posts in support of Israel and stated as well as attacking Palestine they would attack any other countries that supported them.
This is just a small number of the groups identified which were previously active in the Russia Ukraine conflict. It is worth noting there are a number of other groups on both sides which have been supportive of Hamas or Israel for some time. We will provide more information on them in subsequent blogs.
The Cyber War Begins?
Hacktivist groups have been quick to launch attacks on both sides of the war, the type of activity conducted has varied depending on the group and presumably what skills they possess. DarkOwl has not verified the reported attacks were successful.
Some channels as well as providing details of the attacks they have conducted or information they have obtained have also shared graphic images and videos of the conflict as well as support for their chosen side and justification for their beliefs. Here we only focus on the attacks they claim to have conducted.
DDOS Attacks
Two separate groups claimed to have taken down the Red Alert System. This is the system used by Israel to alert its citizens of the threat of a rocket attack. The system has an app which is installed by the user. Anonymous Sudan first made the claim on October 6, providing a screenshot which showed a loading image on the app and a screenshot saying there had been no alerts in the past day. However, the screenshots do not provide a date or time.
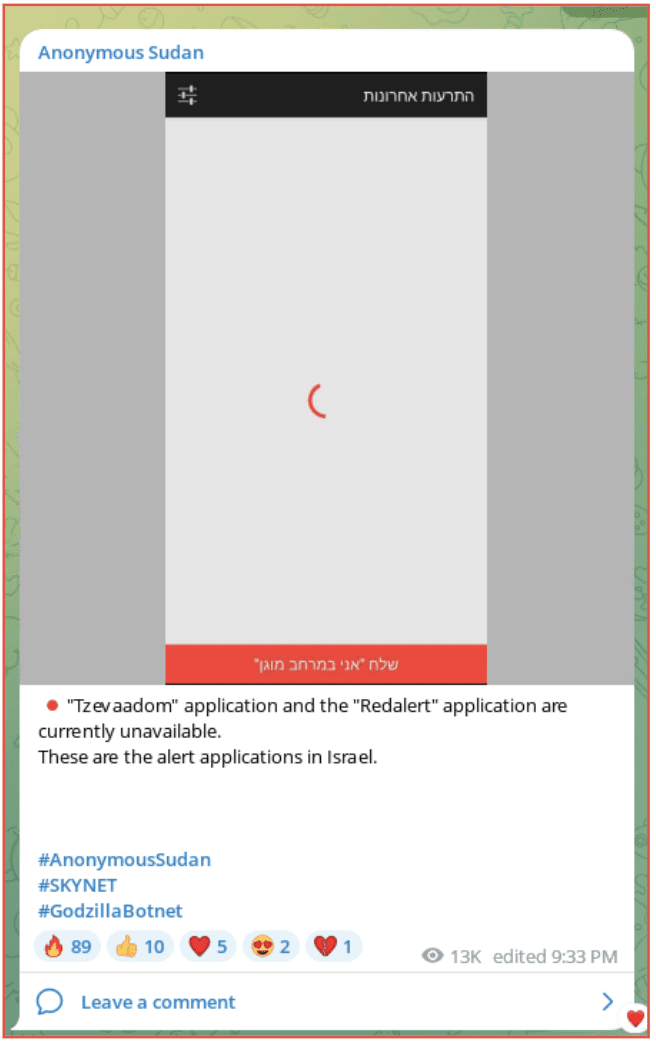
Figure 6: Anonymous Sudan Telegram Channel
GhostAnon was the second group to claim it had taken down the app and it was affecting different areas. Again, they did not provide any concrete evidence this was in fact the case.
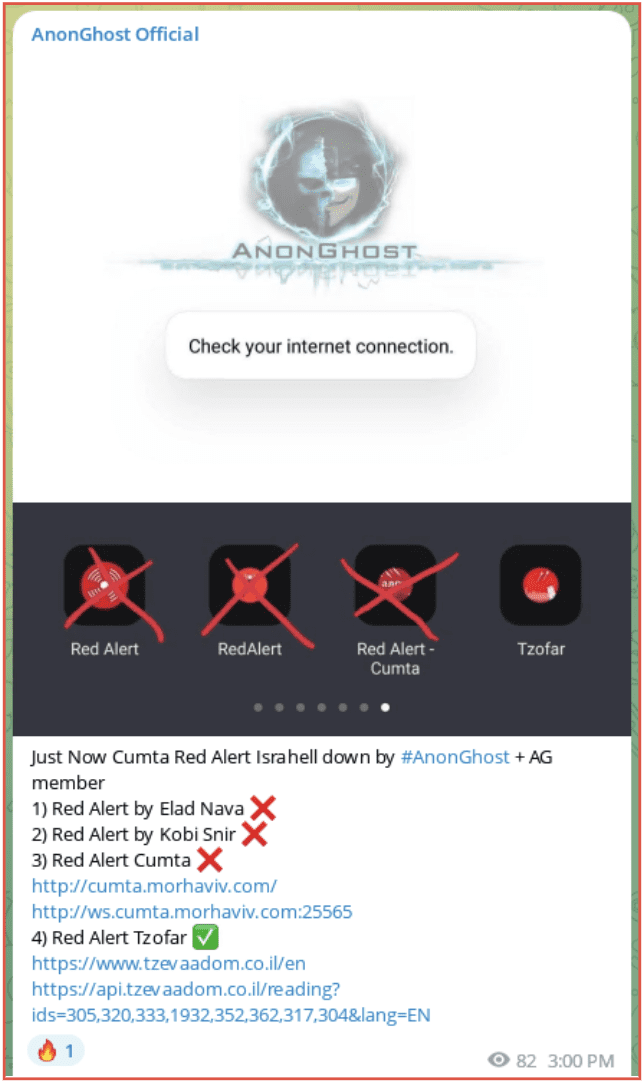
Figure 7: AnonGhost Official Telegram channel
The manager of the Red Alert app refuted the claims the app was down. This is possibly corroborated by a further threat group posting images of the Red Alert Map showing where Hamas rockets were striking Israel, although the timing of the screenshot is unknown.
Anonymous Sudan also claimed to have successfully DDOS The Jerusalem Post, the website of a newspaper based in Israel. The company did post on X (formally Twitter) that they were suffering from a major cyber-attack and the site continues be down several hours later.
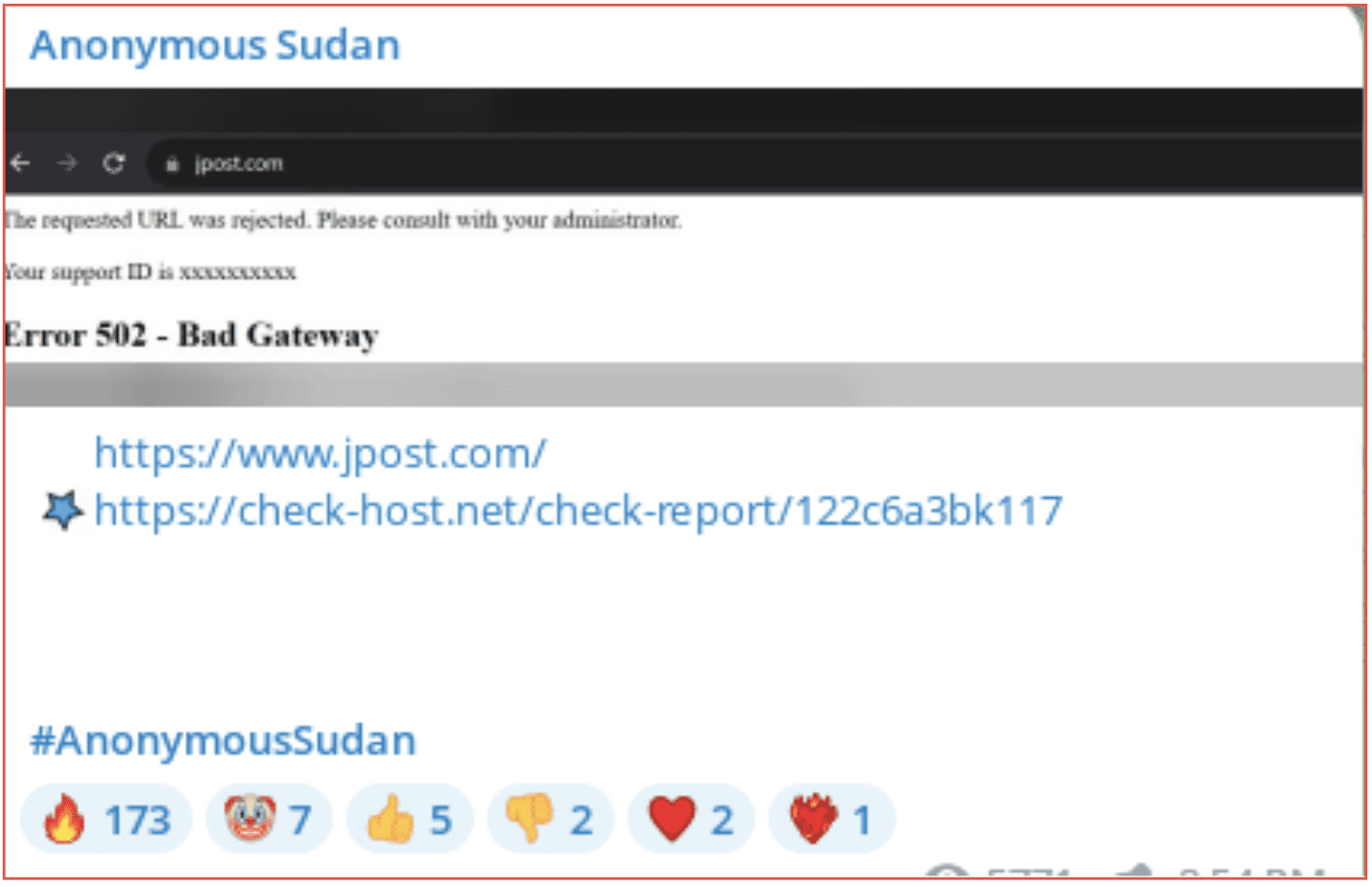
Figure 8: Anonymous Sudan Telegram channel
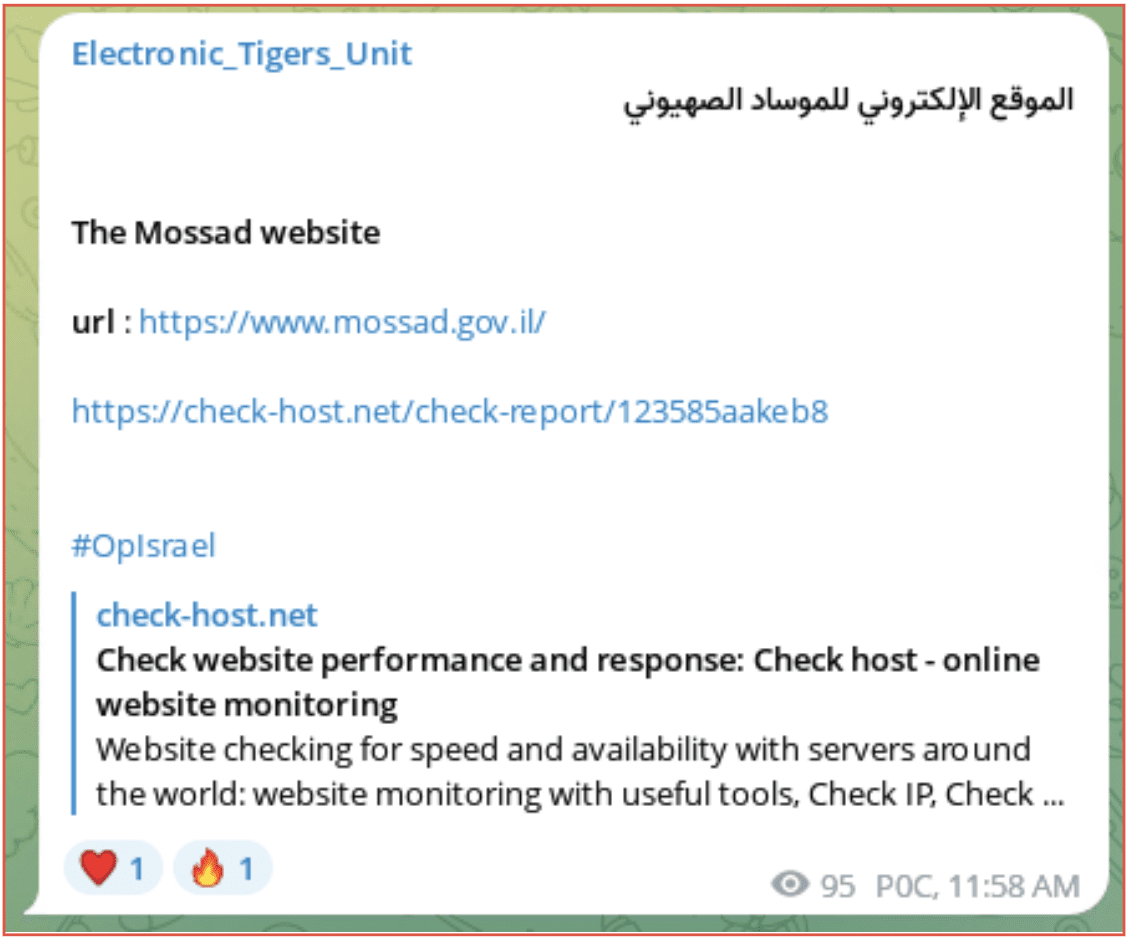
The Electronic_Tigers_Unit claimed they had successfully attacked the Mossad open website via a DDOS attack. Although this is the open site and therefore unlikely to hold any sensitive information its likely aim was to cause distraction to the Israeli Intelligence services.
Defacements
A cyber hacktivist group knows as Cyb3r Drag0nz posted a series of images claiming it had defaced several Israeli websites. The image featured a Palestinian flag as well as the aliases of the individuals involved and their associated Telegram channel.

Figure 9: Cyb3r Drag0nz Telegram account
The companies that were targeted by this group ranged in industry and no reasoning was provided other than they have a .il domain. Defacements have long been used by less sophisticated users or those that want recognition for the activities they are causing. This is a known tactic of Iranian cyber actors.
Leaked Information
Another group Cyber Av3ngers, which is supportive of Iran, activities preceded the invasion and began on October 6 when they targeted Noga Company, an electricity company claiming they were causing power outages “due to the actions of your [Israel] government.”
They have also targeted Dorad Power station both in a DDOS attack and a claim they have obtained sensitive information, this included images of the facility which they shared on their telegram channel, it is likely this was done to assist with an attack on the facility.
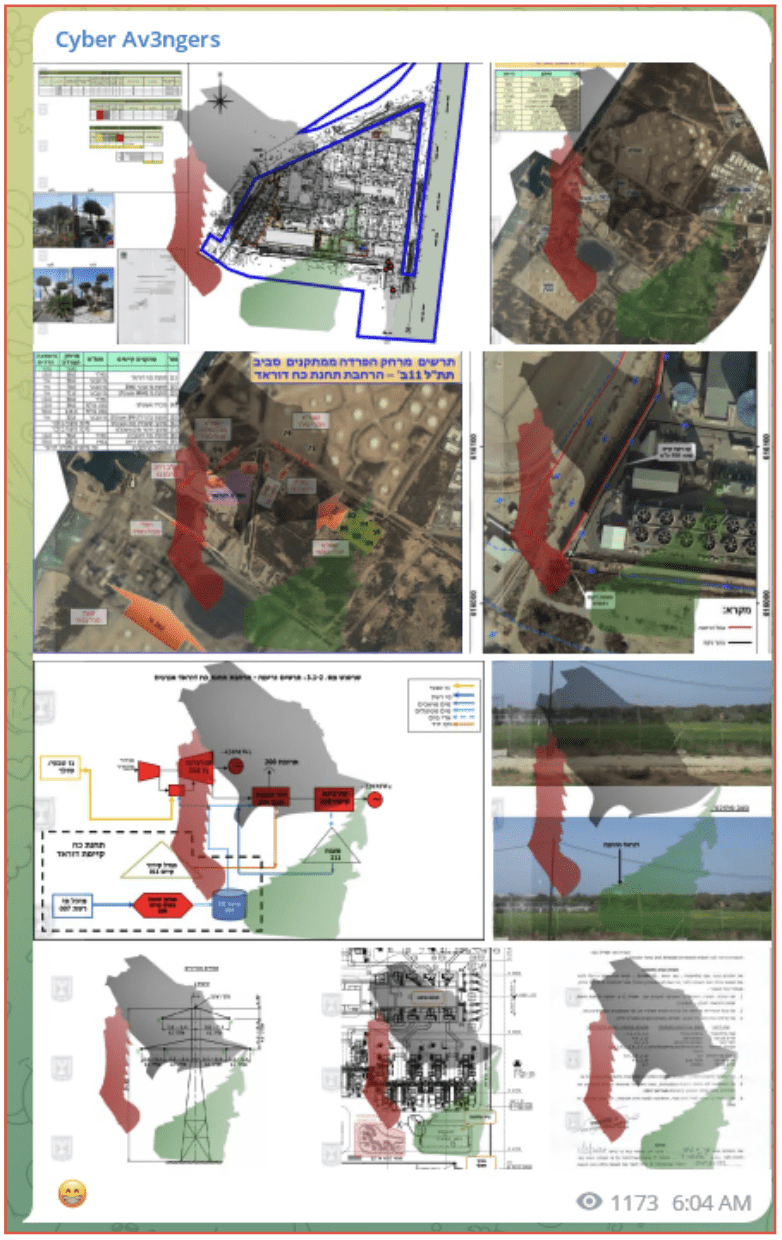
It is worth noting this group had previously claimed responsibility for attacking an Israeli public railroad in mid-September. Although this incident was denied by Israel.
On October 9, AnonGhost-Info provided a list of IP addresses which it claimed formed part of the Israeli Iron Dome. This is the missile defense system which attempts to destroy any rockets entering Israeli airspace. Although these IP addresses have not been verified if legitimate these addresses could be used by a cyber actor to attack the Iron Dome. The IP addresses have been redacted for security purposes.

Pro-Palestinian groups have also been targeting Israeli citizens and sympathizers. Leaks of their alleged information have been revealed with users being encouraged to target their social media accounts to provide pro-Palestinian messages.
On October 9, Cyb3r Drag0nz also claimed to have hacked the Israeli Instagram and provided screenshots showing the information they had obtained which included images and usernames. They later released a download which they claimed included all the user data which contained more than 100,000 Israeli Instagram accounts. This information has not been verified.
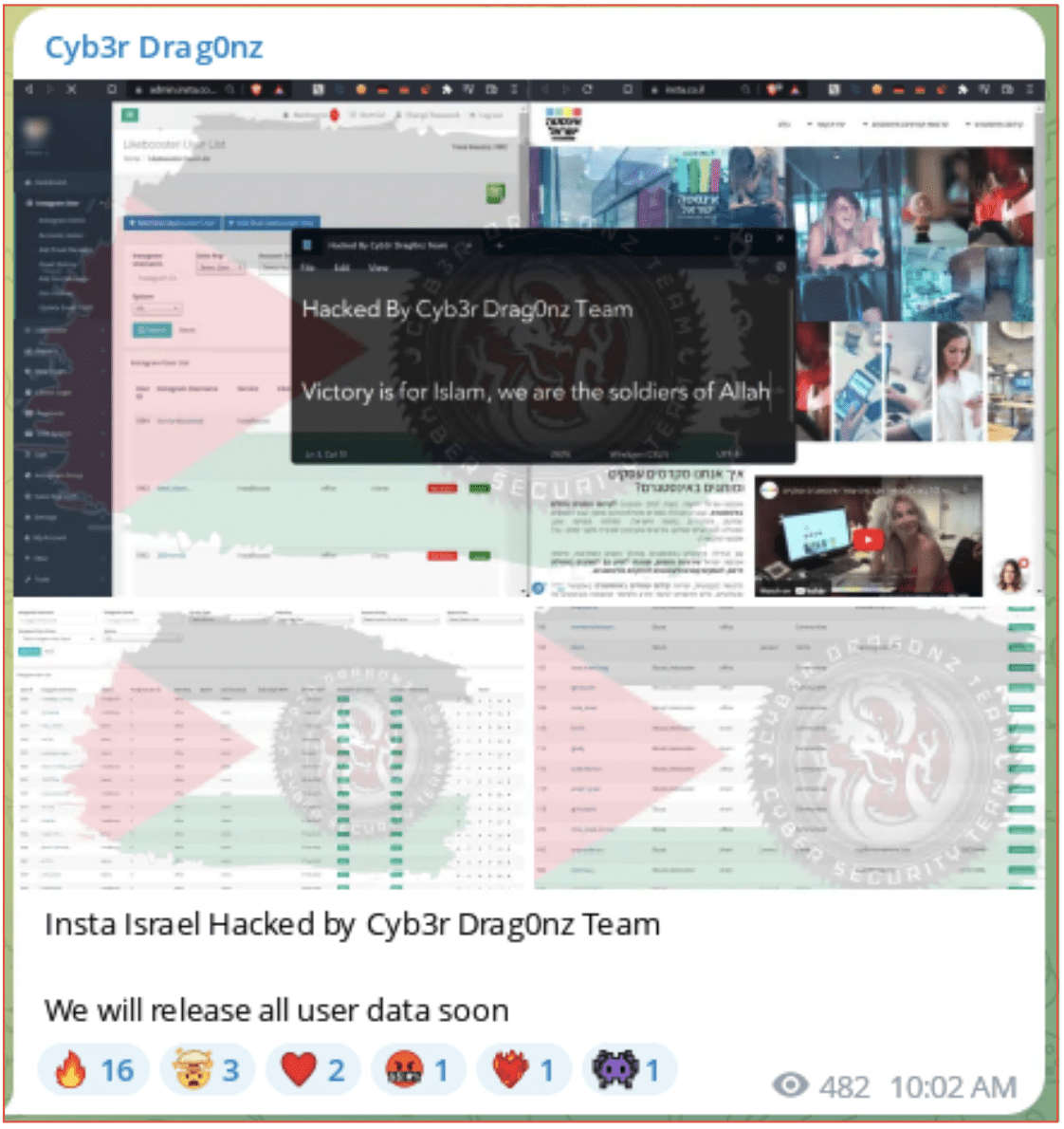
Figure 10: Cyb3r Drag0nz Telegram account
High ranking officials have been subject to DOX attacks with the purported name and phone number of the Director General of the Israel National Cyber Directorate being released and followers being encouraged to spam his phone.
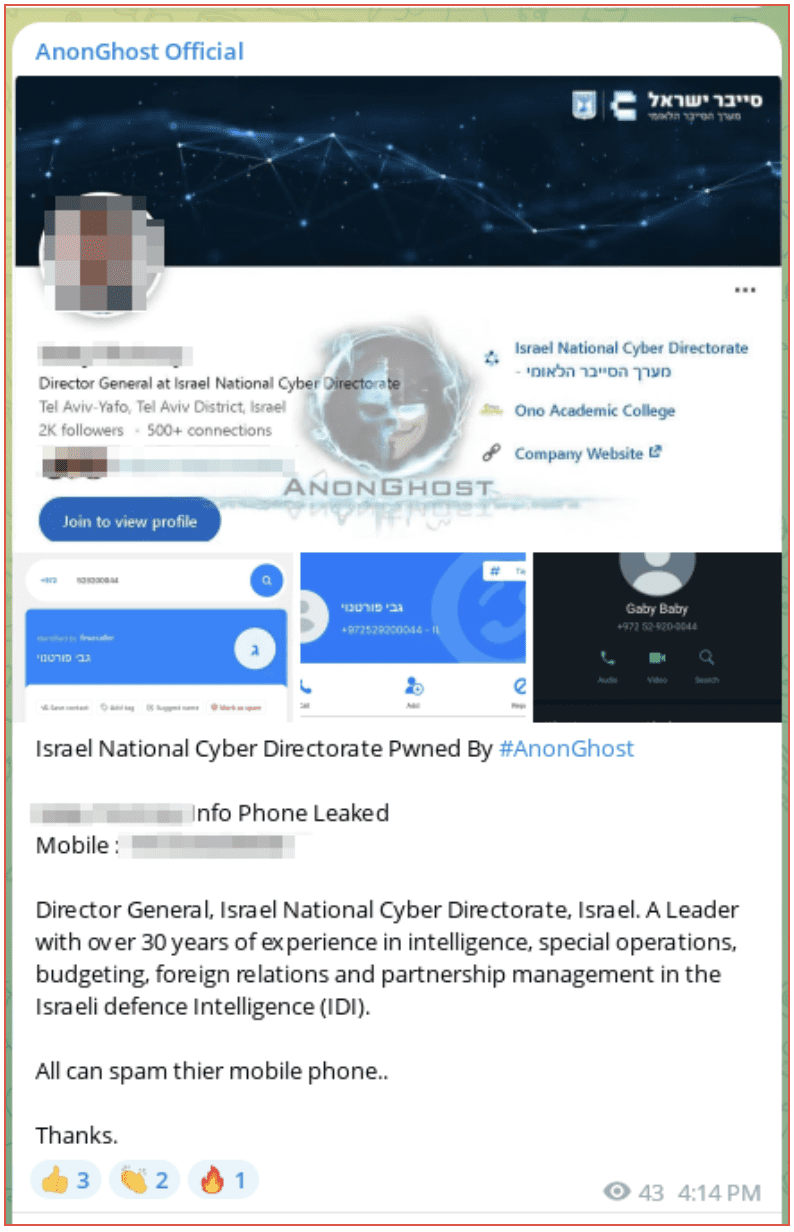
Figure 11: AnonGhost Official Telegram channel
Summary
Although Government sources have claimed they have not yet seen any evidence of cyber-attack, DarkOwl’s coverage of darkweb adjacent groups has shown they have been quick to involve themselves in the conflict. While the tactics which have been observed so far are not assessed to be highly sophisticated, they can be very disruptive, and it is likely more sensitive information is being shared in closed channels. It appears, just with Russia and Ukraine, cyber-attacks will be another front in this war both from hacktivist groups as well as nation states acting directly and via proxies.
DarkOwl coverage on this topic will continue.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















