Darknet Data Use Cases: Commercial
December 8, 2022
In our previous blog on dark net use cases, we focused on intelligence agencies, law enforcement, and government and how darknet data plays a critical role in their investigations and reporting. In this blog, DarkOwl analysts outline the top commercial darknet use cases and detail real-world applicative use cases and examples of DarkOwl’s software-as-a-service (SaaS) darknet data platform and help identify and describe how key data sources in the criminal underground can be leveraged to facilitate analysis and reporting required across commercial entities’ security departments.
Event & Executive (VIP) Protection
Key corporate executives, CXOs, Board Members, and essential technical staff are at elevate risk of targeting for social engineering and phishing attacks from threat actors. Some high-profile executives, political and government employees require increased physical protection as threats of direct violence against them appear in darknet sources and social media.
Data from the darknet can serve as predictive telemetry of potential threats against corporate and government leadership. DarkOwl has observed threat actors leaking detailed personal profiles, termed “doxxes”, of individuals in the darknet. Social anarchist groups also utilize the darknet for coordinating attacks against key facilities and events that are contrary to their beliefs.
A dox (also doxx) is a detailed public record of someone’s identity. To ‘dox’ someone is to publish private information about that person – as a form of public shame and generated to enact revenge on the company or person for some perceived wrongdoing. The dox presents a significant security threat to the company and the individual, with detailed information such as their mobile phone numbers, residential address, social media accounts, bank accounts, and familial associations publicized and subsequently targeted for phishing, fraud, and even kidnapping for murder or extortion.
The personal information of executives and VIPs are often shared on darknet websites which specialize in the distribution of doxxes. While many of the executive dox shared on the darknet observed by DarkOwl include familiar celebrity VIPs like Mark Zuckerberg or Jack Dorsey, other lesser known executives are also exposed as a result of some grievance experienced by the psychologically delicate cybercriminal.
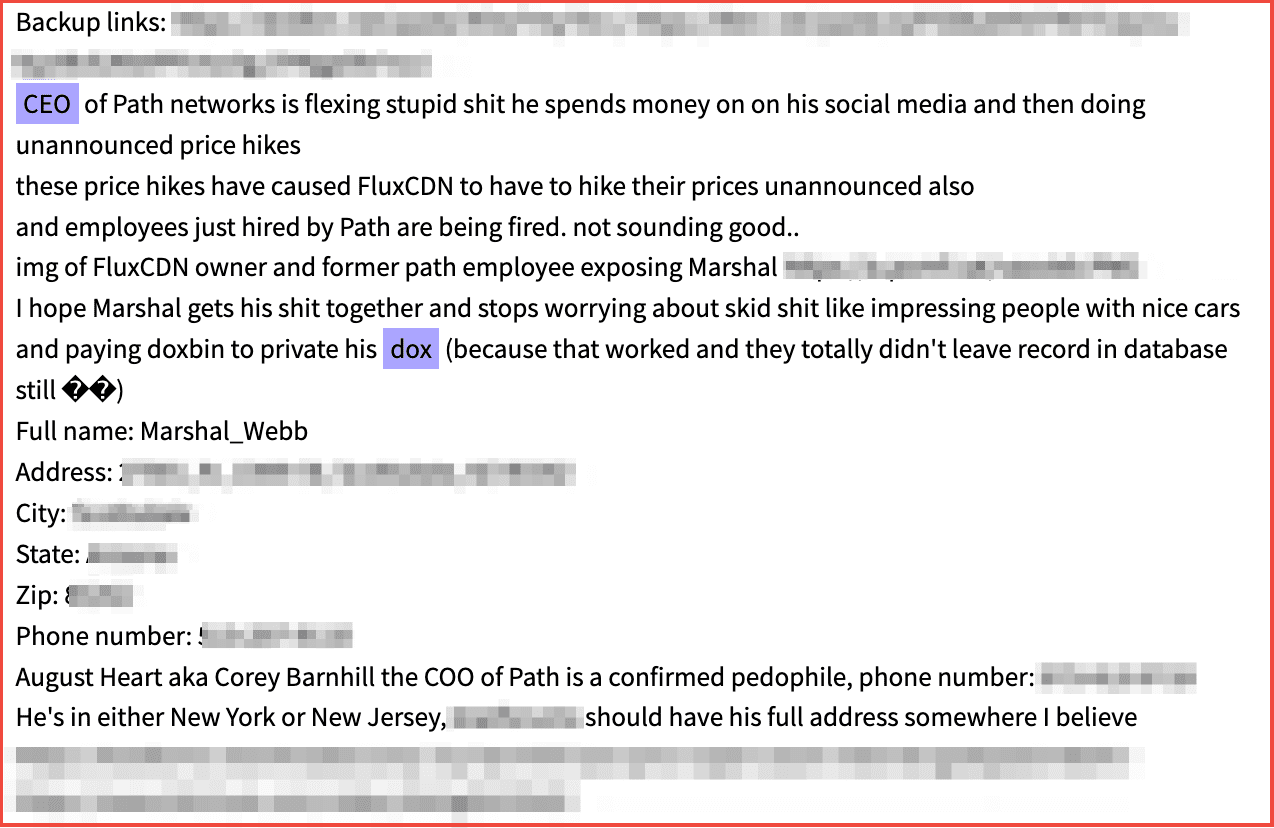
Figure 1: Source DarkOwl Vision
In another example, earlier this year while Roe vs Wade was in the process of being overturned by the US Supreme Court, cyber criminals leaked detailed information from the justices to the deep web. In 2021, anti-democratic party hacktivists similarly leaked personal details of key cabinet members and staff from President Biden’s Administration and suggested their homes and families be targeted for extreme fraud and murder.
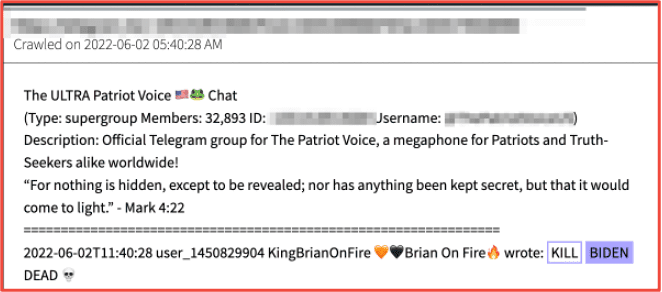
Figure 2: Source DarkOwl Vision
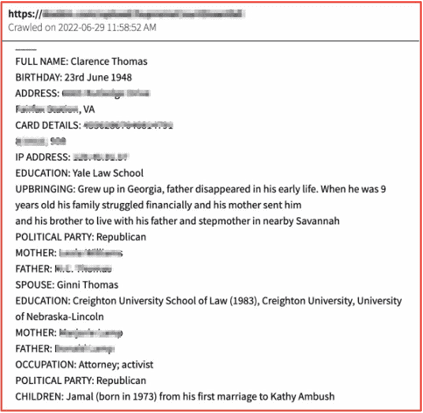
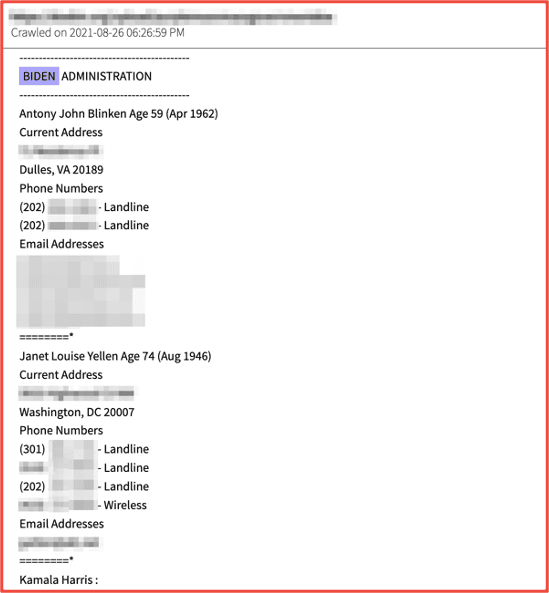
Figures 3 and 4: Source DarkOwl Vision
Cyber Investigations
DarkOwl’s darknet data can significantly augment cyber-criminal investigations by providing key additive informational components – often in conjunction with other open sources like social media activity – to create a more comprehensive picture of the case itself, the criminal’s behavior, and psychological intentions, or simply fill in critical intelligence gaps and solidify evidence such that indictments and subsequent legal action may be executed.
Using DarkOwl in conjunction with other open sources and utilities, an investigator can easily identify and a track threat actor’s digital fingerprints and subsequent virtual breadcrumbs, such as social media accounts, usernames, aliases, avatars, email addresses, PGP keys, and cryptocurrency wallet identifiers.
The snapshot example below details how DarkOwl identified and tracked a Portuguese-speaking threat actor involved in mobile device malware development. The lower third of the graphic, consisting of evidence collected from the darknet and DarkOwl Vision – confirmed the suspect’s activities across various underground communities in the darknet and a leaked IP address provided a potential physical location of João Pessoa, Brazil.
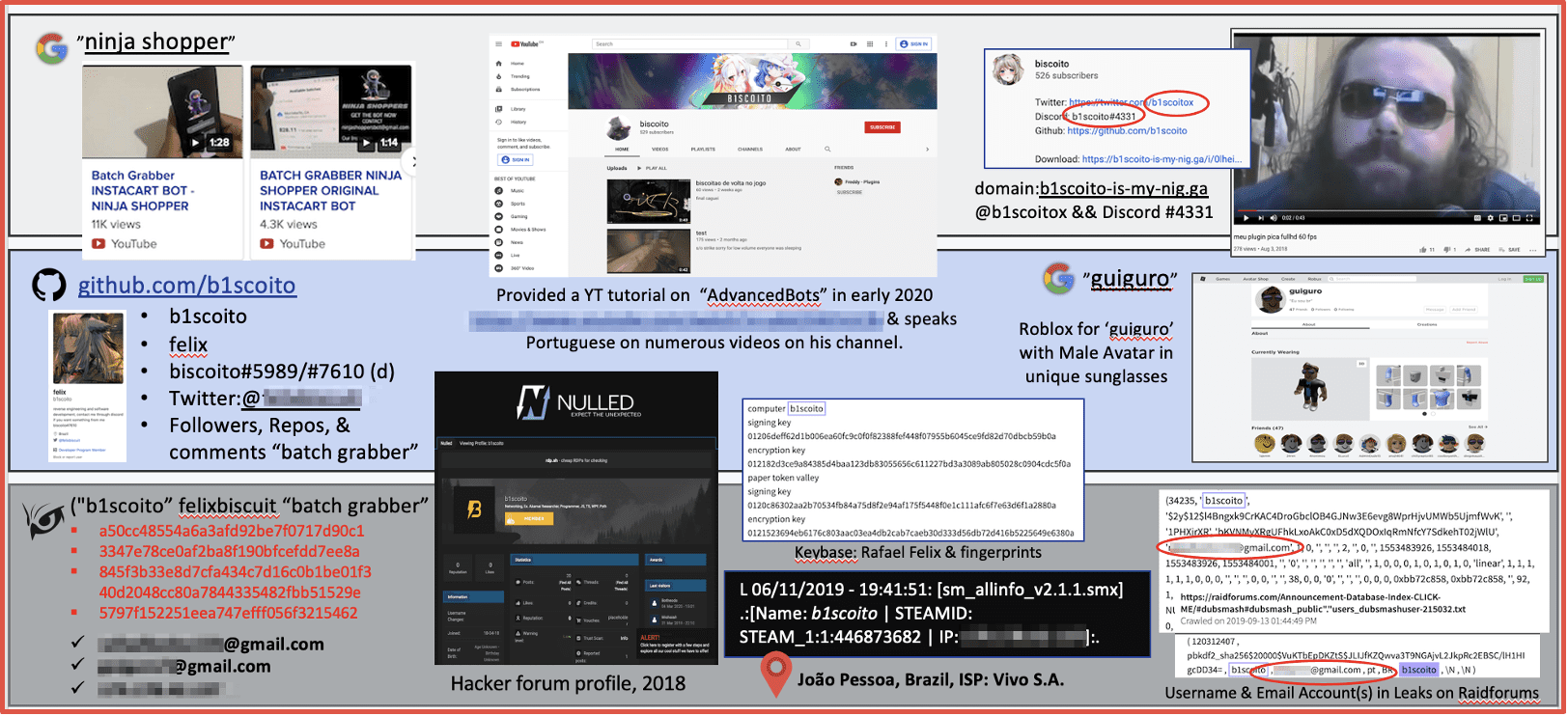
Figure 5: Source DarkOwl Analyst, July 2020
Situational Awareness: Ransomware
Russia’s late February military invasion of Ukraine and on-going offensive operation was preceded by numerous opportunities for geopolitical situational awareness prior to the invasion, and subsequent monitoring of the conditions is available with a surge of new Telegram channels documenting live events ‘on-the-ground’ and conversations between users that have unique perspectives of the conflict.
Commercial organizations, including retail outlets, are targeted daily by dozens of active ransomware-as-a-service (RaaS) gangs that operate exclusively on the darknet. A ransomware incident against a commercial organization can cause serious loss of revenue and interrupt operations for weeks while incident response and remediation is carried out. Shoprite, in South Africa, experienced a ransomware attack from Ransom House group who subsequently leaked the usernames, IDs, and personal information of its consumers when the company failed to pay the extortion.

Figure 6: Source DarkOwl Vision
Insider Threat Risk
Many employees who are unhappy with their employers – including both corporate or government civilians – often rant in darknet chat rooms and forums, under the cloak of anonymity, about their working conditions, abusive bosses, or annoying coworkers. Sometimes the posts include calls for ‘darknet hackers’ to revenge them and attack the organization’s networks so they don’t have to work.
DarkOwl users can monitor the darknet for malicious mentions of their organizations that include information that is limited to employees and staff with authenticated or limited access to information, e.g. the ‘insider threat.’
DarkOwl uncovered a post on a darknet forum where a corporate employee detailed organizational issues with members of a specific team at the company and called out the management team leaking their names and their emails accordingly. With this information, the company can launch an internal investigation to identify the employee and mitigate the risk to the organization, through supervisor and HR intervention and/or termination.
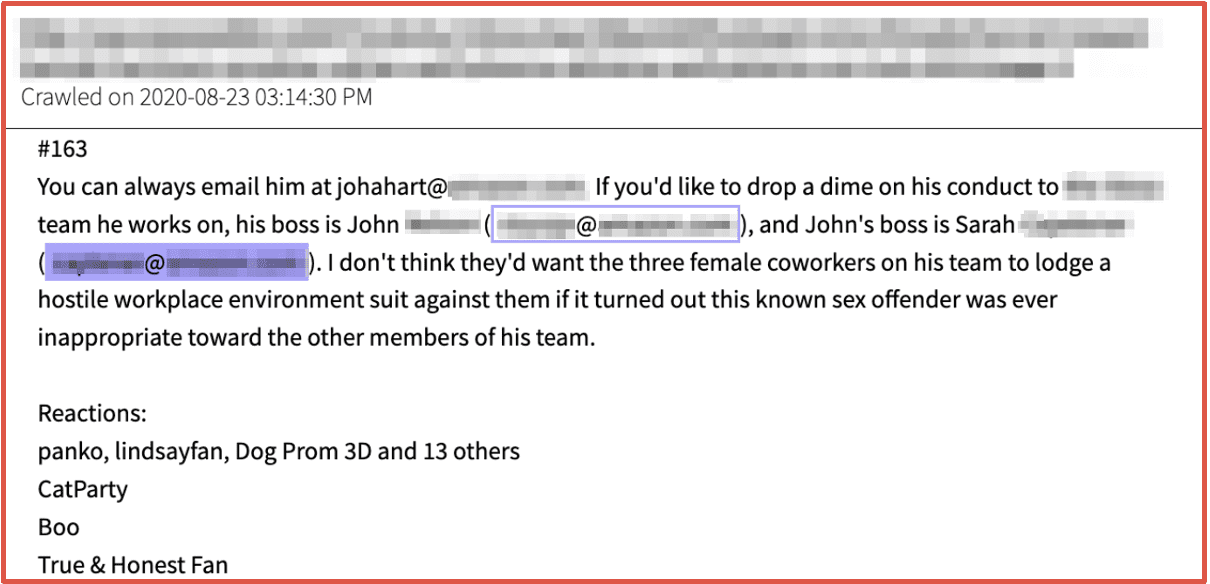
Figure 7: Source DarkOwl Vision
International ransomware threat actors also regularly solicit for insider threats to shorten the cyber-attack lifecycle by using employees with direct access to company IT resources instead of brute forcing network credentials or exploiting vulnerable network devices. Often instead of the network appliance mentioned the specific company name is included in the solicitation.
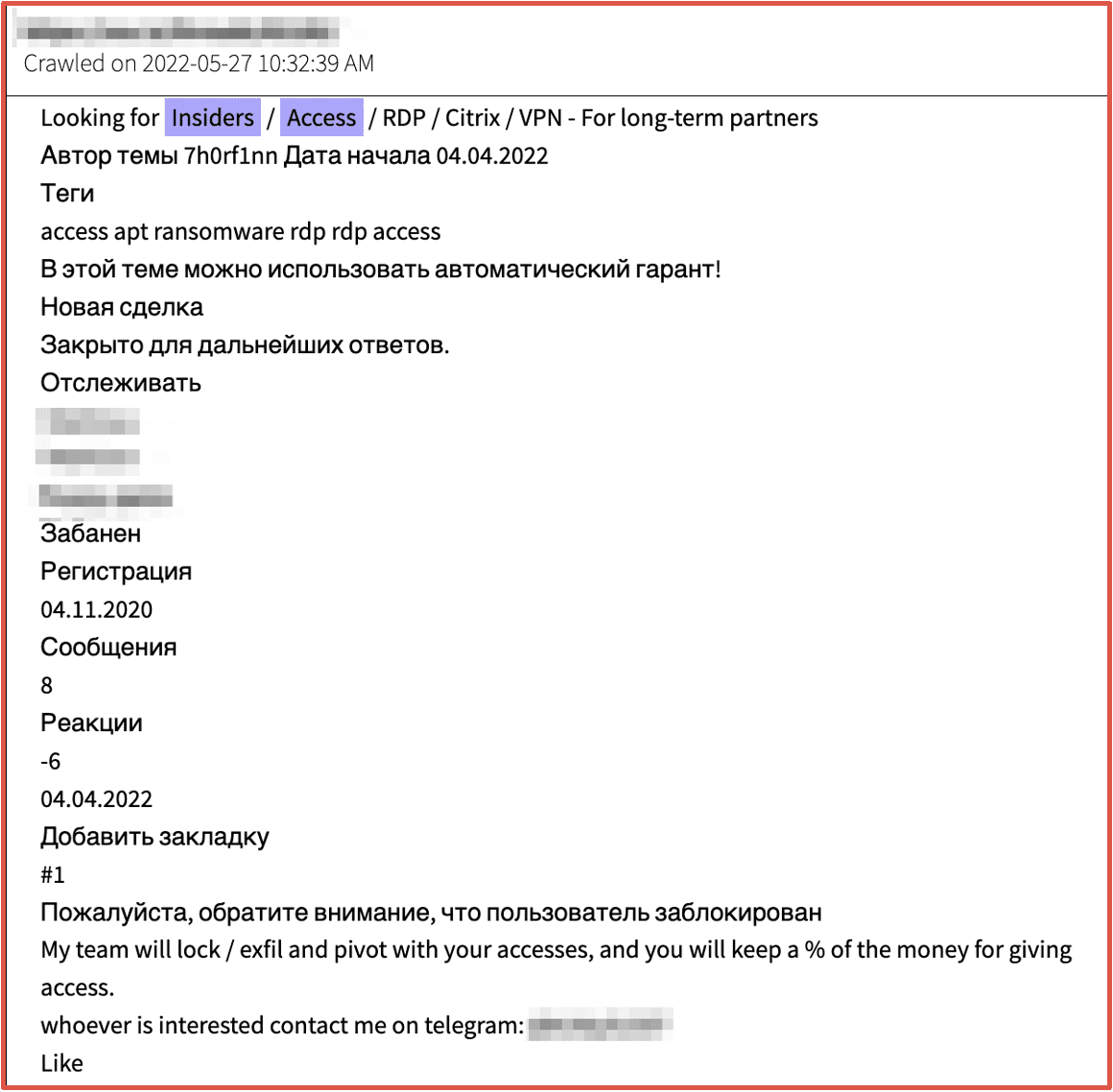
Figure 8: Source DarkOwl Vision
Brand and Reputation Risk
Corporate brand recognition, reputation, public perceptions are paramount in establish market share and sustaining fiscal certainty in uncertain economic conditions. Darknet data can be utilized to uncover derogatory mentions of a company or corporate identity that can help mitigate risks to the organization’s long-term success.
The image below includes an announcement on Telegram by pro-Ukrainian hackers calling for the boycott of purchasing Nestle products due to their continued operation in Russia and subsequent economic support for the Putin-backed Kremlin.
In the days following the post on Telegram, prominent darknet threat actor group, KelvinSec compromised Nestle’s company network and leaked sensitive databases containing their customers, transaction, and shipping data.
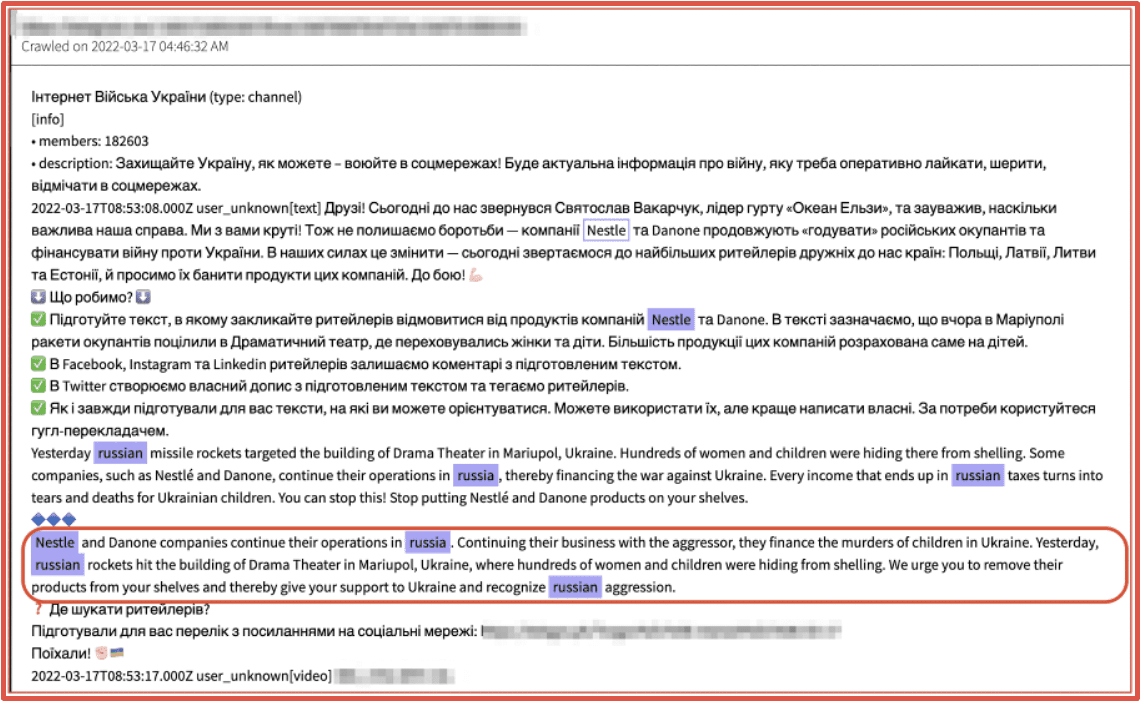
Figure 9: Source DarkOwl Vision
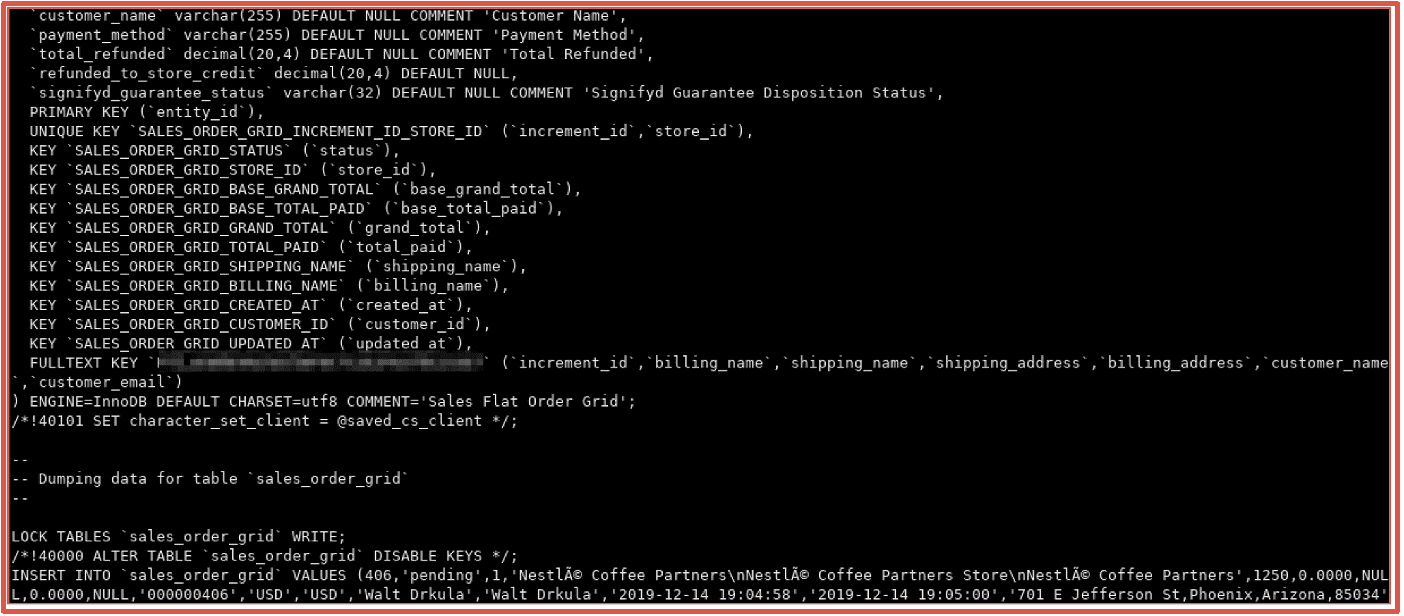
Figure 10: Source DarkOwl Analyst
Counterfeiting and Identity Theft
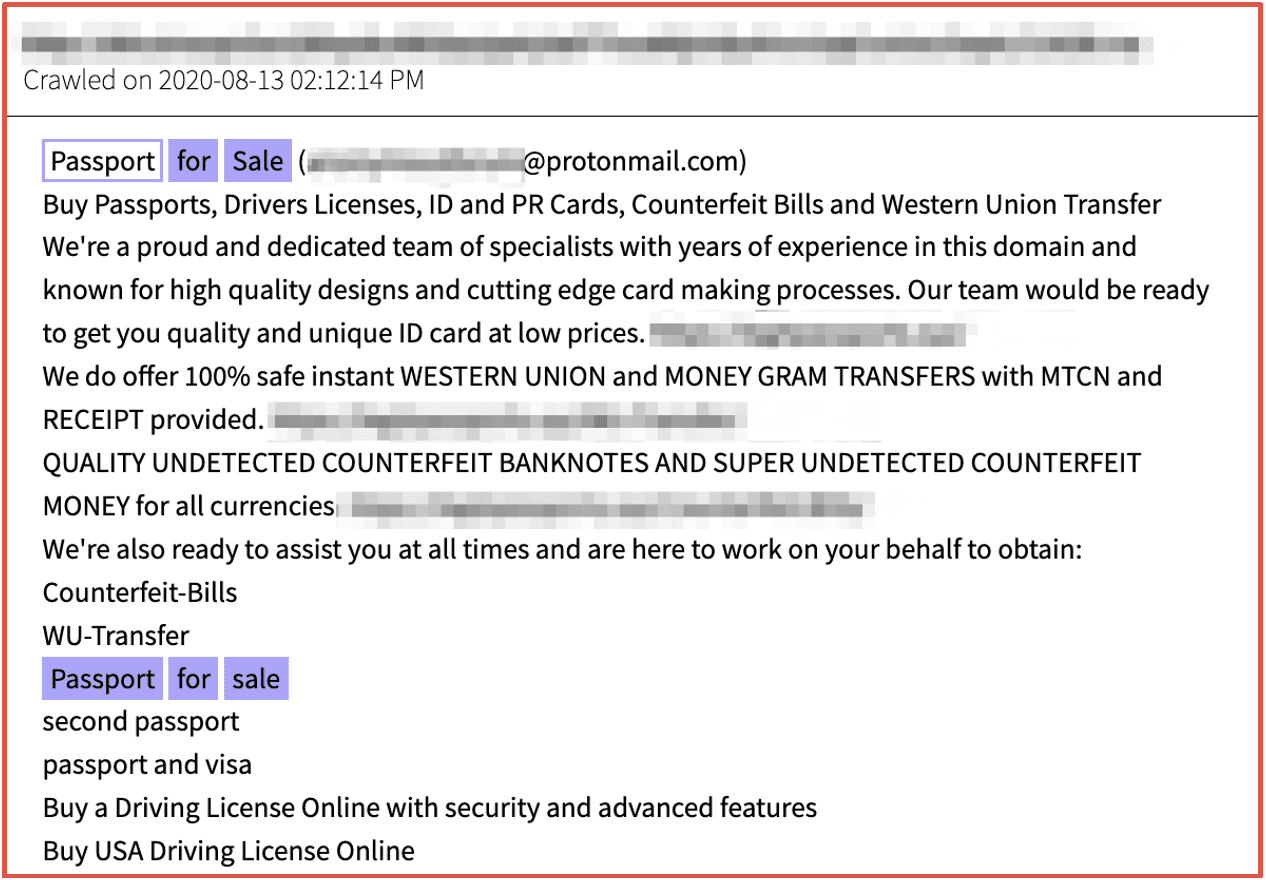
DarkOwl’s darknet data can provide indication of concerted efforts to sell or circulate counterfeit goods and identifications, in addition to monitor for potential identity theft. Passports, driver’s licenses, and military identity cards are regularly offered for sale on darknet marketplaces.
Darknet fraudsters intent on financial fraud of individuals are sophisticated enough to bypass identification verification utilities, such as ID.me. Users on Telegram offered a compromised ID.me with driver’s license and social security number for $20K USD earlier this year. Others offer “ID.me bypass” methods for sale on fraud forums and public chats.
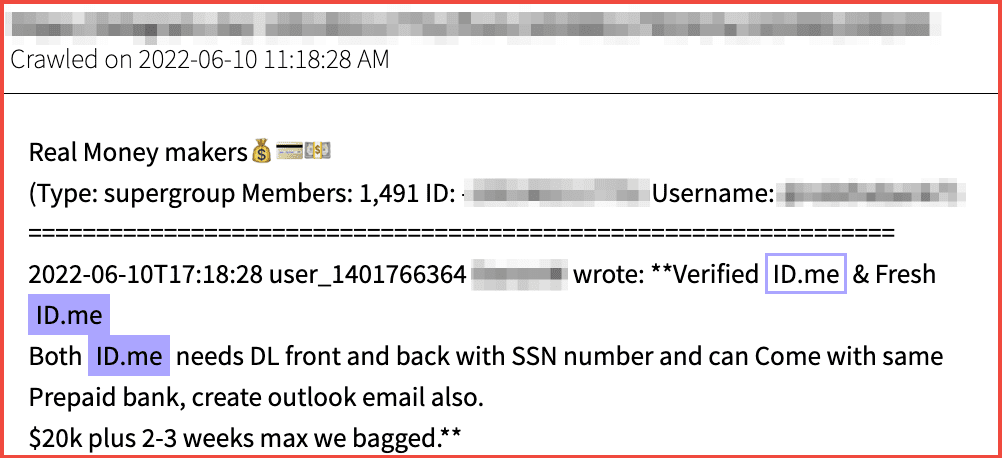
Figure 11: Source DarkOwl Vision
Driver’s licenses are available for sale across many darknet marketplaces and Telegram groups. A vendor on Nemesis decentralized darknet market offered USA driver’s license templates to create fake identification cards for as little as $5.00 USD with guaranteed refund if the template was unsuccessful. Canadian templates are more expensive at 300 CAD for a template of only the province of Quebec.
Figure 12: Source DarkOwl Analyst
Large data leaks, like GiveSendGo shared on DDoSecrets, includes photographs and scans of US and Canadian military identification cards that could be leveraged by threat actors for identity fraud and/or unauthorized access to military installations.
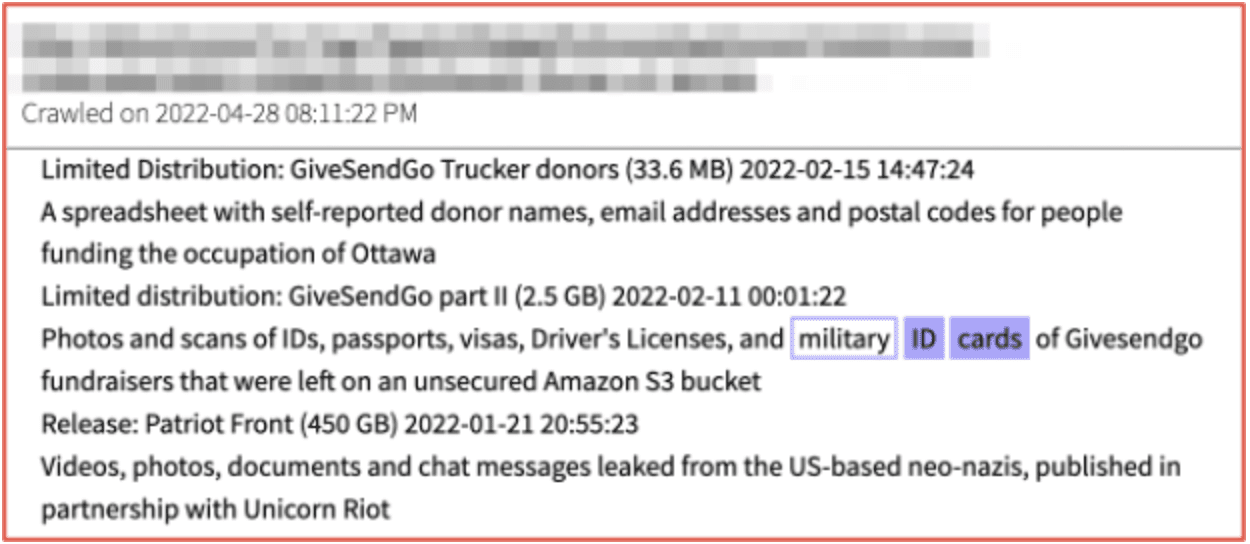
Figures 13 and 14: Source DarkOwl Vision
Supply Chain Risk Mitigation
Supply chain attacks are industry-agnostic cybersecurity attack methods that cause damage and destruction to an organization via compromising less secure elements in the organization’s supply chain. This has been observed across many ransomware groups – who operate within the darknet and target suppliers and vendors of major victims and utilize the organizational data, exfiltrated from the compromised network to carry out additional attacks on the same organization and vendors and suppliers connected to the victim.
DarkOwl’s darknet data platform supports continuous monitoring for and quantifying supply chain and vendor risks. Many third, fourth, and even fifth party vendors do not always expeditiously inform their stakeholders of critical cyberattacks and the early mention of the supplier on a ransomware blog site hosted on the darknet can assist all organizations connected to the victim, regardless of role or capacity, establish a solid defense posture with increased security awareness and proactive protection. Simply monitoring for mentions of an organizational website domain over time can be an indicator of risk.
In the example graphic below, DarkOwl captured where various organizations connected to the Volvo car corporation were attacked by multiple ransomware groups over the course of a year. It is highly likely that the data exfiltrated from the attacks in 2021 was utilized in the subsequent attacks against Volvo’s subsidiaries and their suppliers.
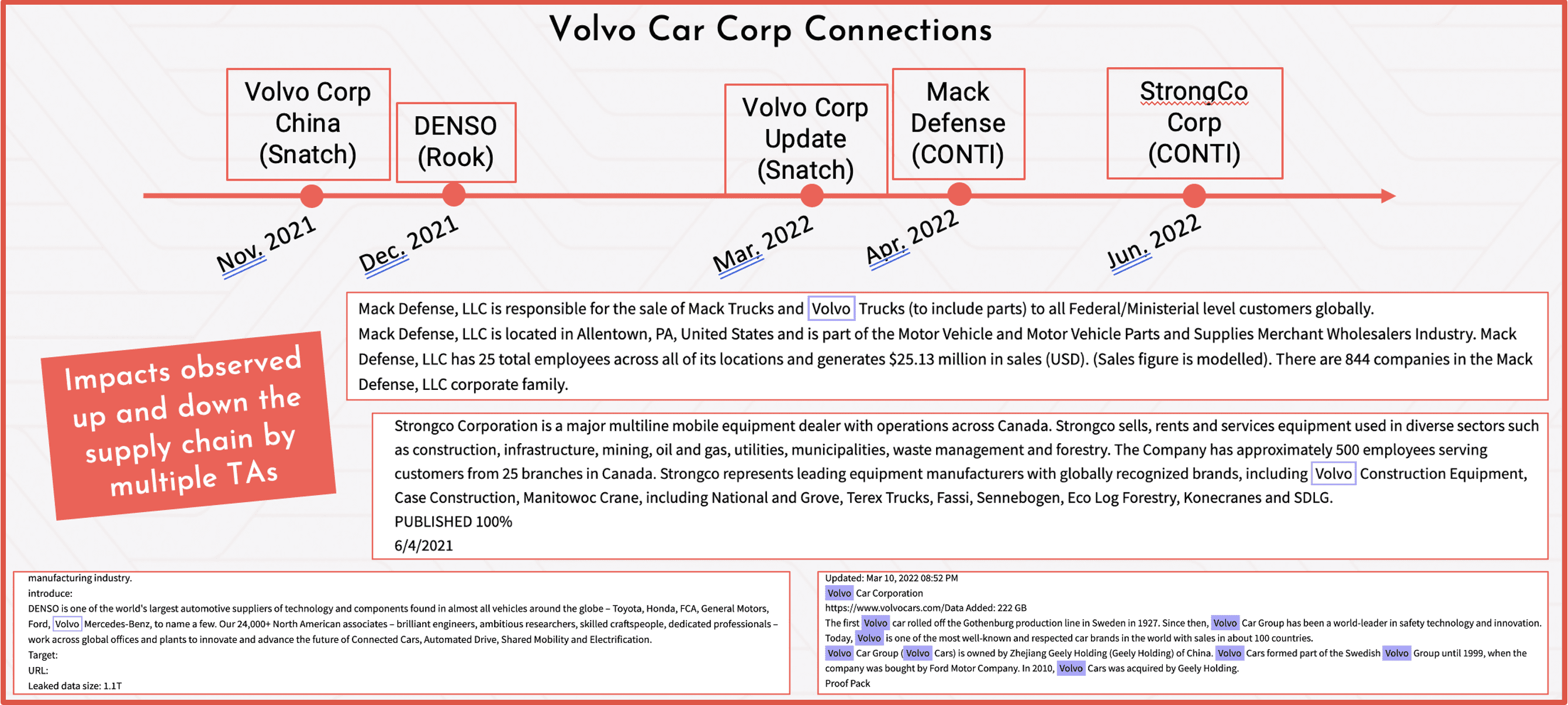
Figure 15 Source: DarkOwl Marketing, Presentation Recap Blog Here
DarkOwl uses machine learning to collect automatically, continuously, and anonymously, index and rank darknet, deep web, and high-risk surface net data that allows for simplicity in searching.
Our platform collects and stores data in near real-time, allowing darknet sites that frequently change location and availability, be queried in a safe and secure manner without having to access the darknet itself.
To learn more about darknet use cases and how to apply them to your business, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















