Data for Sale on Leak Sites
May 23, 2023
DarkOwl analysts have observed the emergence of leak sites that are dedicated to simply posting leaked data and are not affiliated with known ransomware groups. These leak sites are similar to other darknet marketplaces and forums, but they specialize in selling other people’s data and usually don’t sell other products like malware, drugs, or weapons. The leak sites described here should not be confused with the leak sites and victim blogs used by ransomware gangs.
Ransomware Services
Ransomware gangs use victim blogs or leak sites as part of what DarkOwl refers to as Ransomware Services: the services related to ransomware threat actors, where victims are announced and their data is leaked if they do not pay. Typically, a ransomware gang will publish the victim’s name, details, and part of the stolen data as proof of its legitimacy.
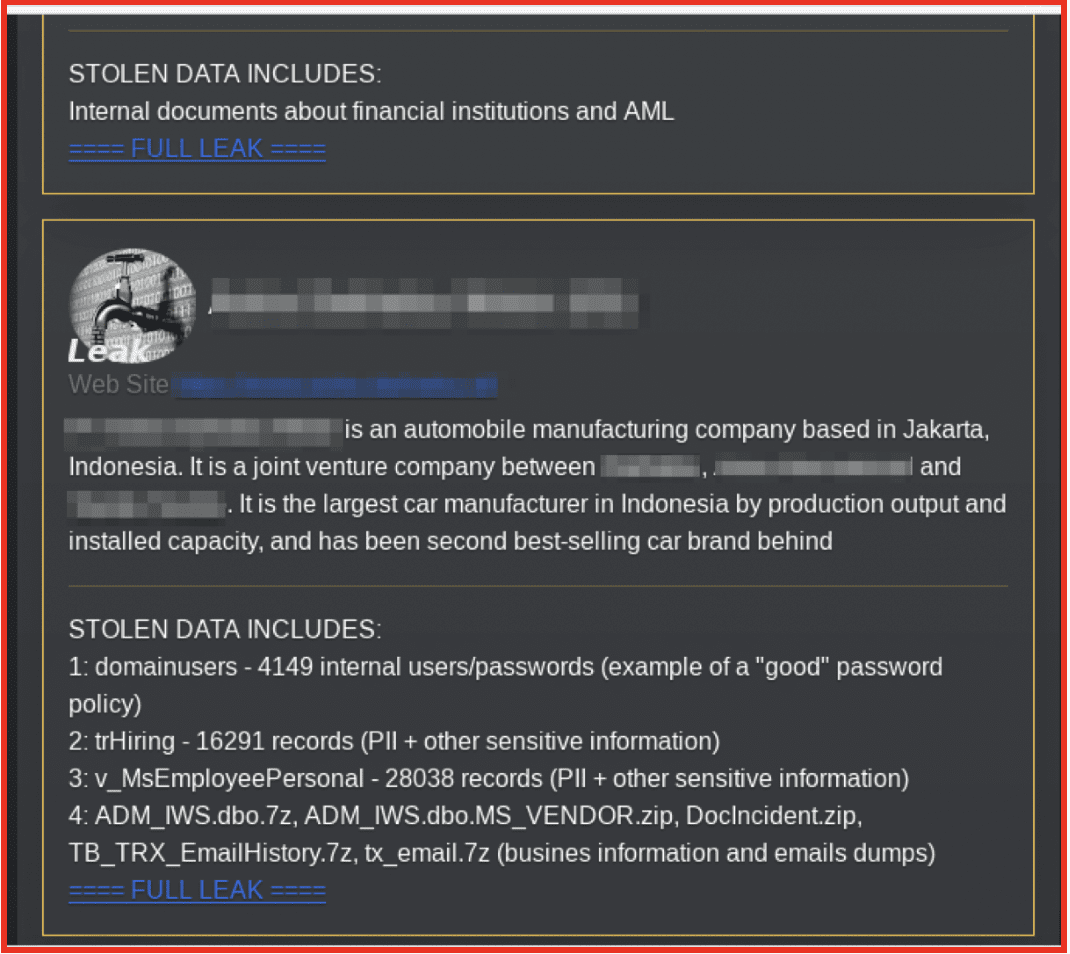
Figure 1: Post to Ransomware Gang Leak Site; Source: Daixin Team Tor Site Tor Anonymous Browser
Leak sites are also used as a means of communication between ransomware groups and their victims to conduct negotiations. In figure 2, Royal ransomware group’s leak page includes a contact form at the top with a list of victims below. That way a victim can check if the sample of data provided is legitimate, and then contact Royal.
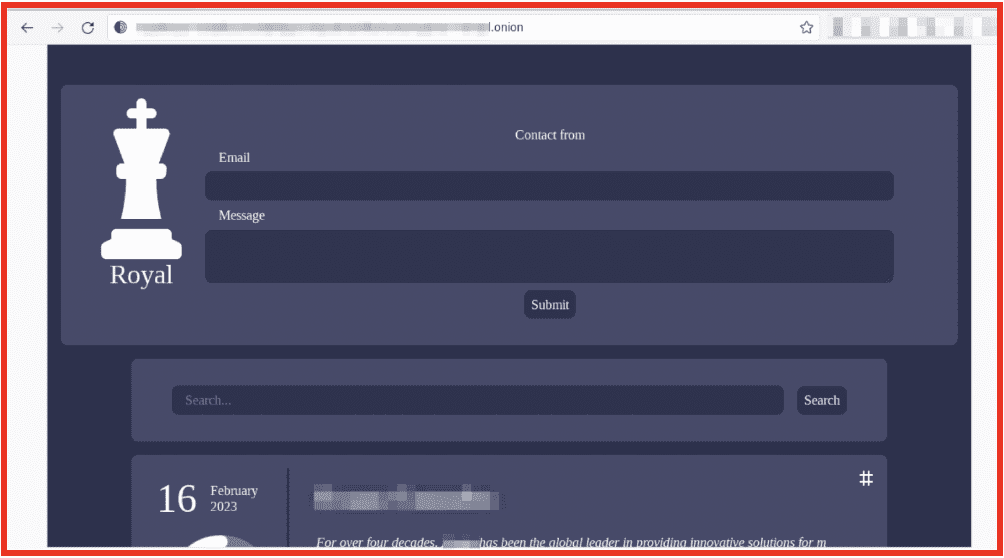
Figure 2: Contact Form on Royal Ransomware Leak Site; Source: Tor Anonymous Browser
Leak sites and victim blog sites are used by ransomware groups as part of their double-extortion techniques. In a double-extortion attack a ransomware gang will encrypt the victim’s files and demand a ransom payment for the decryption key, as well as exfiltrate the data to their own devices. The ransomware gang will then threaten to publish the sensitive data to the darknet or sell it to the highest bidder. Sensitive data published to the darknet or purchased by a darknet actor can expose the victim to future vulnerabilities, such as sophisticated social engineering and phishing attacks.
Leak sites are a type of darknet marketplace. However, leak sites only sell data. Darknet marketplaces that are not leak sites will sell a variety of other products such as malware, cracking tools, drugs, social engineering and phishing methods, job postings, website penetration testing, detective services, and occasionally weapons. Darknet marketplaces will also sell leaked data (CVVs, ID cards and passports, company data, personal data from apps, etc) along with their other merchandise. Large marketplaces have many vendors and there will usually be a forum section to the marketplace. The leak site DataCloud only has data uploaded by the admin instead of by multiple vendors. Leak sites can be more decentralized and potentially run by a fewer number of individuals than other darknet marketplaces. Furthermore, DarkOwl analysts identified that each of the leak sites analyzed have a robust Telegram component.
The reliance and usage of Telegram by leak sites is a distinct feature which traditional darknet marketplaces do not have. The Telegram channels associated with the leak site will typically be run by the administrator of the site. Data can be bought and sold on some of the leak site-affiliated Telegram channels. The biggest difference between a Telegram channel and a darknet marketplace is that on Telegram there is a lower bar to entry. A marketplace will usually require a login, password, and ask the user to pass anti-phishing captchas. Unless a Telegram channel is private, anyone can join a public channel. Potentially less sophisticated users with little darknet know-how could learn about and use the markets from their Telegram channel—as could law enforcement and bots.
Leak Sites
DarkOwl analysts have seen the emergence of new leak sites which differ from leak sites and victim blogs associated with ransomware groups because they are not affiliated with any specific ransomware or hacker group. These act as third-party vendors of leaks and leaked information. Many sell stealer logs, accounts, combo lists, and proxies as well as dumps of leaked data. Accounts available for sale include accounts to VPNs, pornographic sites, streaming services, and mail access. Data can be purchased directly from the darknet leak site or from its Telegram channel. The Telegram channels attached to leak sites are for discussion and are where users can ask for data or DM the admins.
Unsafe
A leak site known as “Unsafe” calls itself a security blog with “published personal data leaks, commercial and military secrets, and compromising information on famous people and public organizations.” They include a disclaimer that they are not a hacking team, but all their data is from hackers. According to them, their blog is a platform for buyers and sellers as well as a middleman service to help parties negotiate (for a fee).
Each listing keeps a count of the number of times the data has been viewed, the size of the data offered, a link to the company’s website, the company’s revenue, and their country of headquarters. “Proofs” are uploaded for each targeted company. Data in these proofs include full passport photos, ID cards, personal information, sensitive company information, sensitive HR information, financial information, screenshots of texts, credit cards, graphic pictures (including pornographic imagery), and more. Interested buyers can get in contact to buy the data through the Tox IDs provided; one for Support and other for a Sales Manager. All of the data posted is listed as being compromised either on October 23, 2022, or November 26, 2022. DarkOwl has not verified the authenticity of any of the data that is provided on this site.
The information included in the proofs are open to everyone to view. This could indicate that the data in the proof may be used to attract other cybercriminals to encourage them to buy the full data-set which they can leverage for their own criminal means.
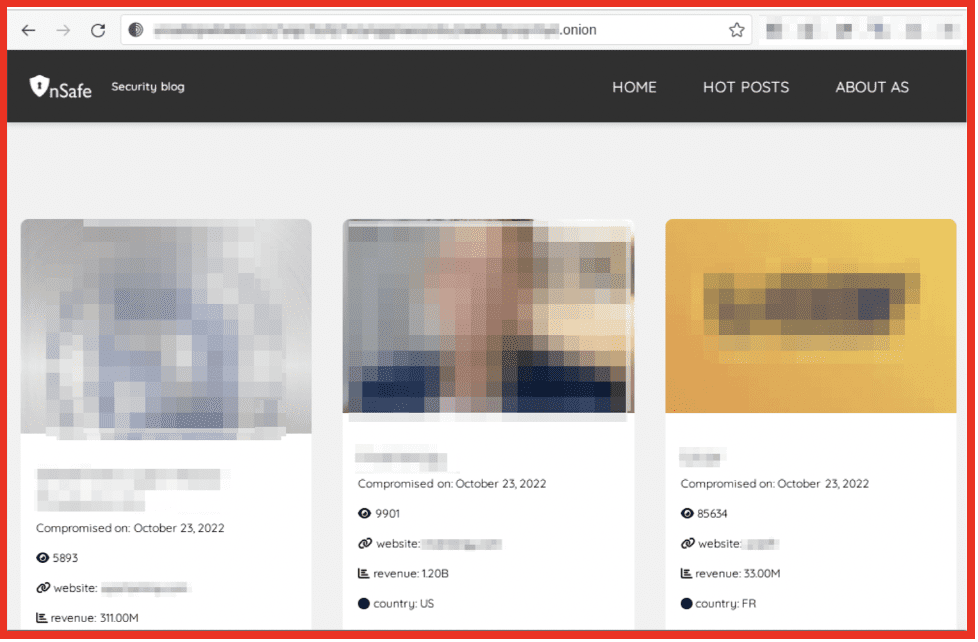
Figure 3: Home Page for Unsafe Security Blog; Source: Tor Anonymous Browser
DataCloud
The leak site DataCloud offers combolists, stealer logs, logs, and account access to e-mail services. Interestingly, access to a Yahoo mail account is the only product for sale (for $120), all other data from listings can be downloaded. Analysis indicates that a user can join the site via a subscription-based model. On the site all data is uploaded by the admin. DataCloud has multiple associated Telegram channels, which appear to be used for different purposes.
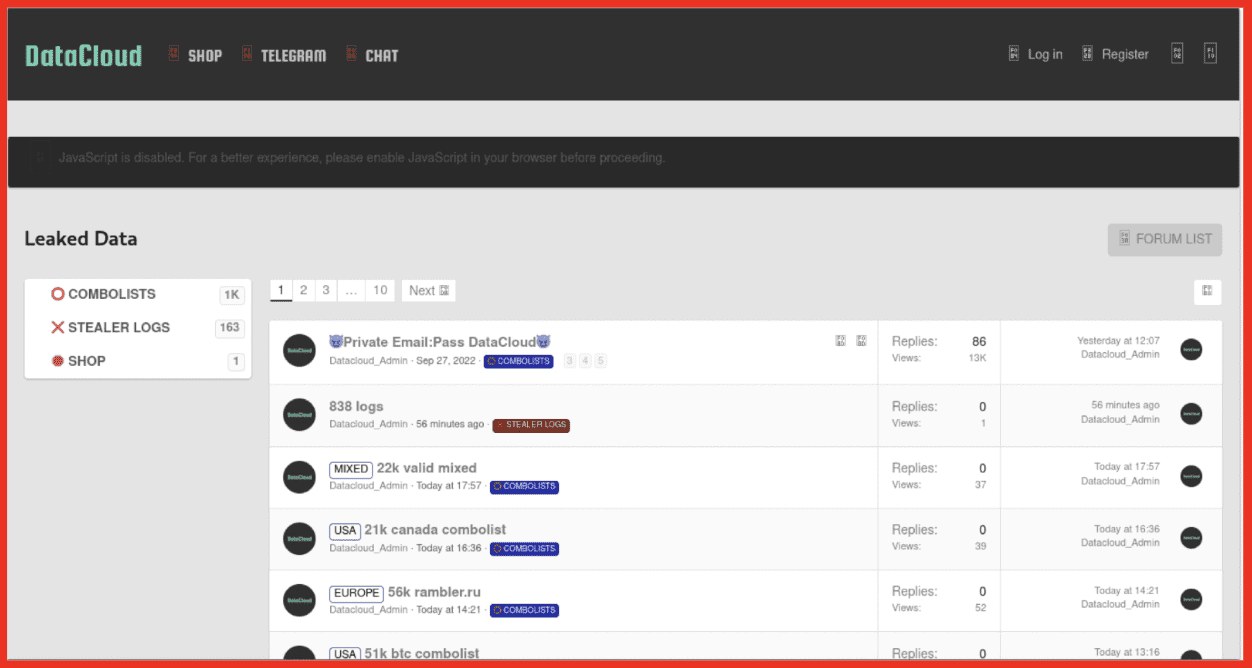
Figure 4: DataCloud advertising Combo Lists and Leaked Data; Source: Tor Anonymous Browser
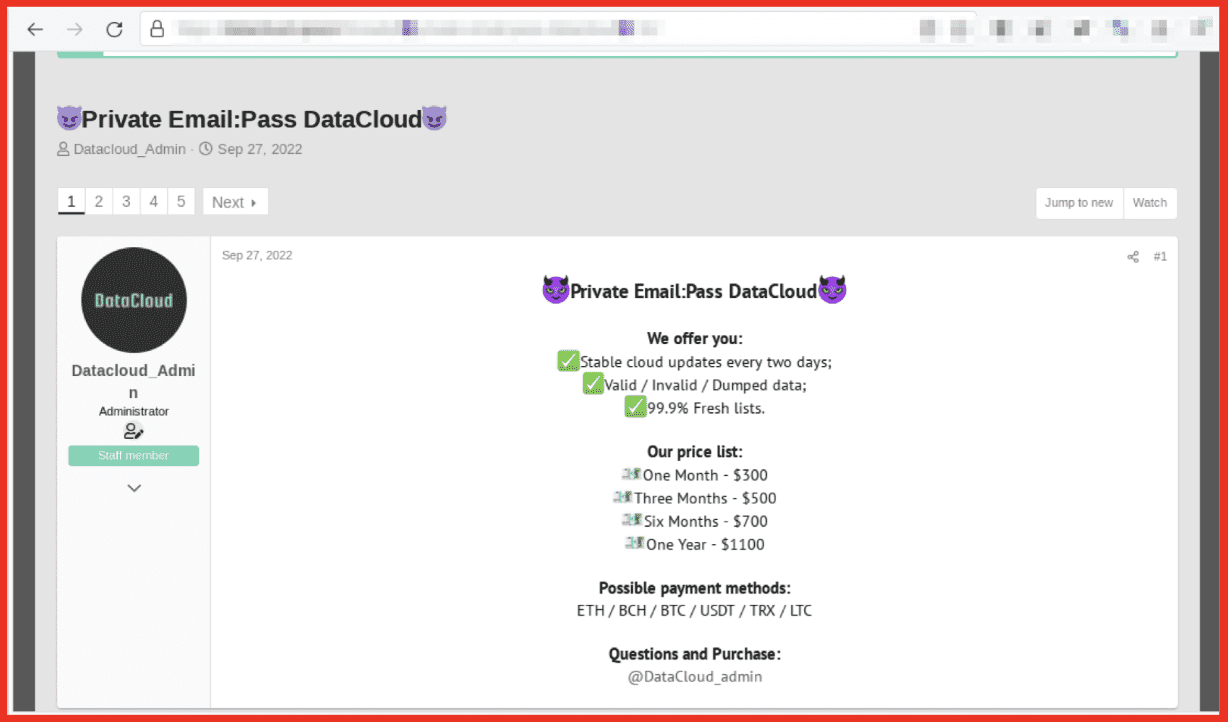
Figure 5: DataCloud Subscription Options; Source: Tor Anonymous Browser
One Telegram channel is linked under the “Telegram” tab of the site and is used by the admin for posting what appears on the site. In this channel the DataCloud admin directs users to their site, referred to as their forum. Only the administrators post in this Telegram channel.
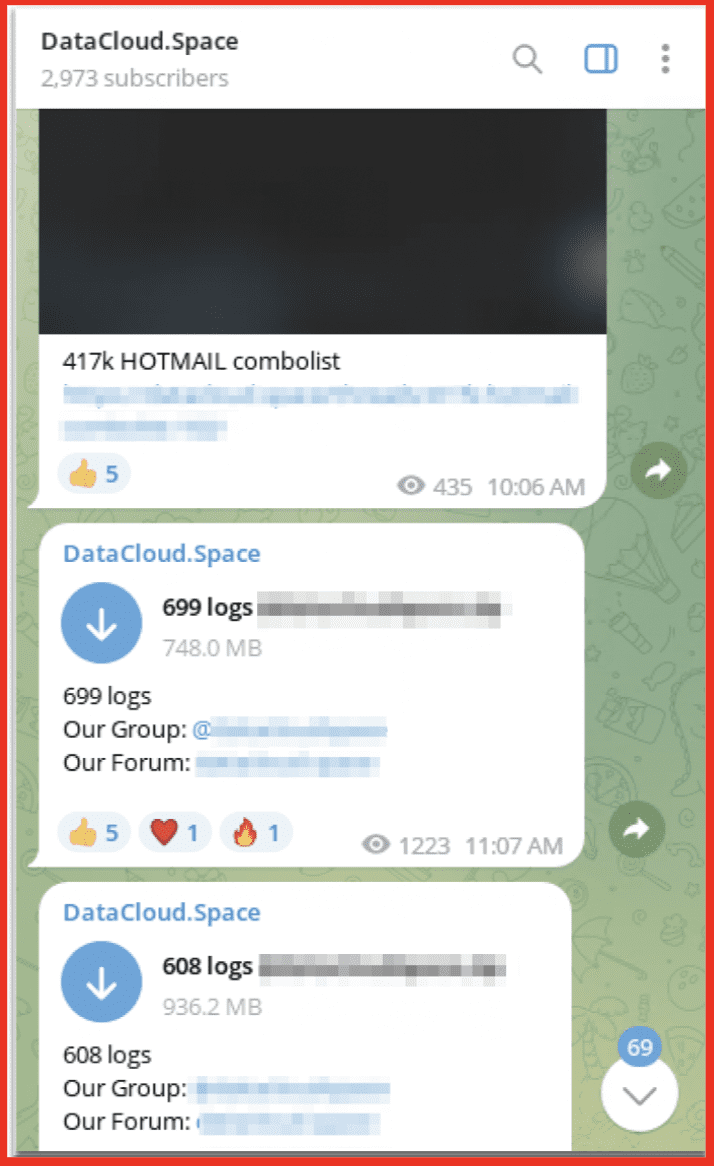
Figure 6: DataCloud Associated Telegram Channel; Source: Telegram
The other Telegram channel is linked under the “chat” tab and acts as a forum for the site’s users and visitors. Many darknet marketplaces have a forum component where users can post questions, comments, or anything they want to about the marketplace and beyond. This Telegram channel attached to “chat” is essentially the marketplace’s forum but run on Telegram. This channel is still run by the DataCloud admin; however, it is used by members to request specific data from each other or to advertise data they have. This channel can be used to facilitate direct deals, either for free or for a fee, between users.
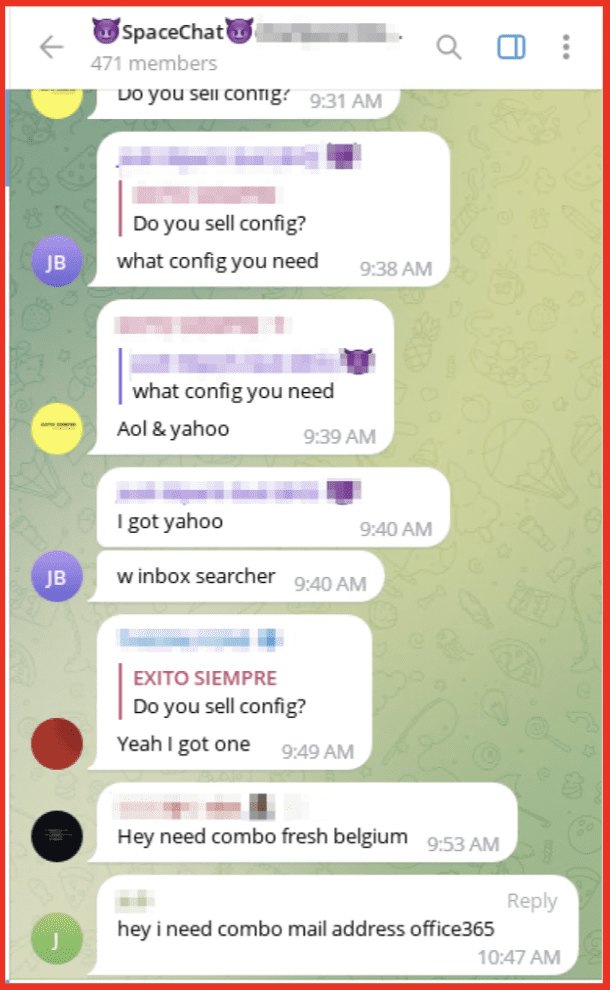
Figure 7: DataCloud Associated Telegram Channel; Source: Telegram
Leak sites that use Telegram channels in conjunction with their website can use feedback and requests from Telegram to curate their data to their customer’s needs. DarkOwl analysts have observed that Telegram plays an integral role in the new leaks sites used just for data downloading and purchasing. Telegram appears to have a more integral role in leak sites than in other darknet marketplaces, almost as if Telegram was an extension of the leak site itself rather than auxiliary.
SQLi Cloud
A leak site that uses a similar structure to DataCloud is SQLi cloud. This site focuses mainly on stealer logs and combolists, which are largely offered for free. Requests can be posted in the Marketplace section where other users can respond.
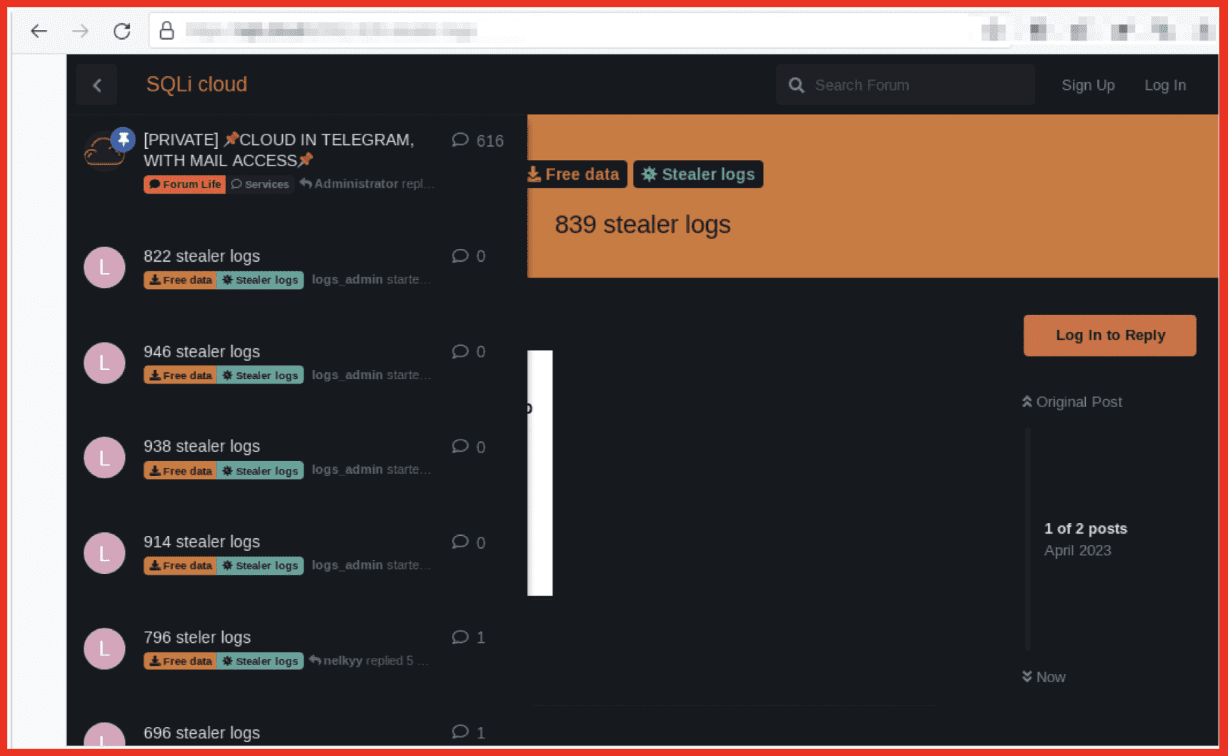
Figure 8: SQLi Cloud Offers Stealer Logs; Source: Tor Anonymous Browser
Similar requests to those found in the marketplaces section of the SQLi site can also be found on their Telegram channel. In this Telegram channel an account called “SQLi administrator” posts updates and responds to others in the chat. The channel is also used for requests for specific datasets. However, as with anywhere on the darknet, users must be wary of scammers.
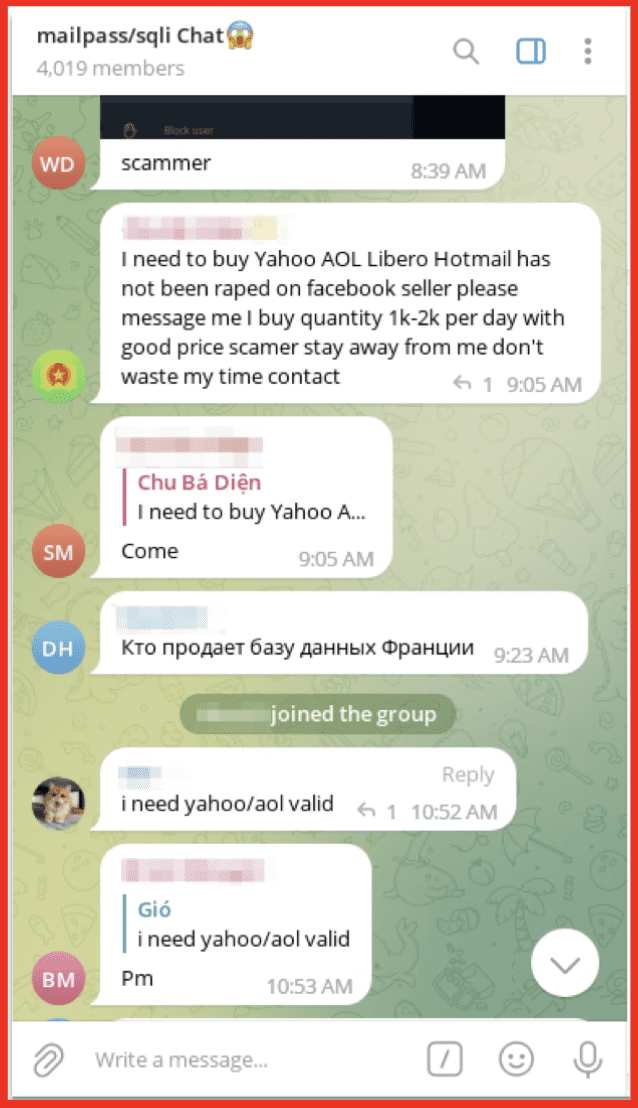
Figure 9: SQLi Associated Telegram Channel; Source: Telegram
Leak Sites on Telegram
“Cracked group” is a Telegram channel offering data for sale. The data found on this channel ranges from streaming data and stealer logs to data identified by the country it has been taken from e.g., “Vietnam data.” There is an admin for the channel which moderates the channel and posts details of the data available.
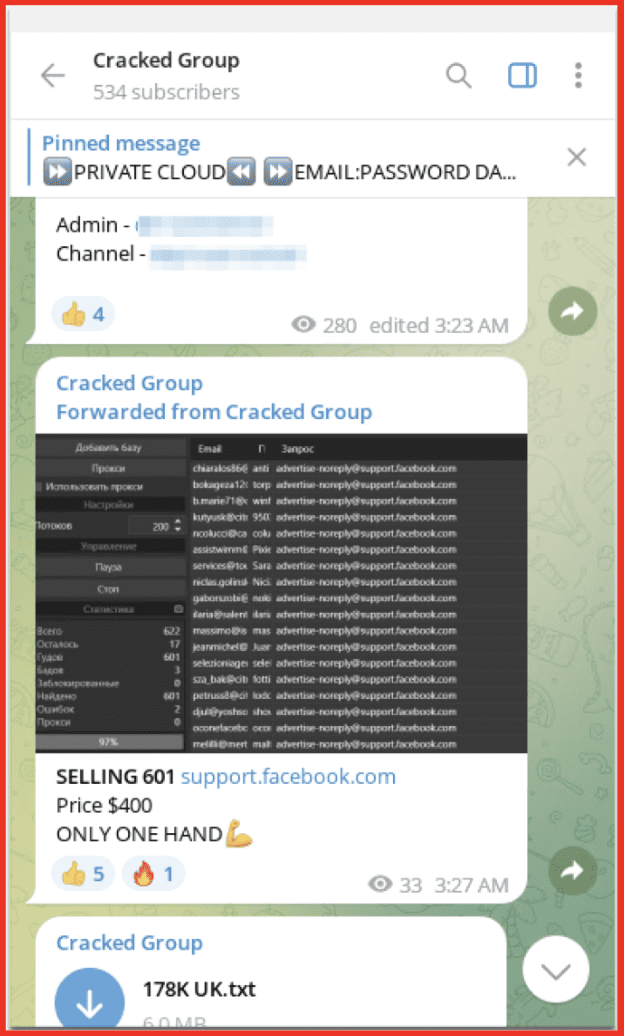
Figure 10: Cracked Group Telegram Channel; Source: Telegram
Unsafe, DataCloud, and Cracked rely mainly on Telegram or have a site with just a few pages built out. In this aspect they are more informal or sparse than would typically be found on a darknet market. All have a Telegram channel. Those with websites have a main marketplace to download data and links to Telegram channels or contact information. Most have an “About Us” page.
Other leak sites are sophisticated marketplaces and forums specializing in the sale and downloading of leaks and personal data. This category includes sites such as Shadow Leaks. Shadow Leaks has the infrastructure of a traditional darknet forum and has features like awards, credits, a forum, and even sponsors. This site offers a larger product suite. Aside from leaks and combolists, products such as programming courses, hacking tutorials, dorks, and more are available.
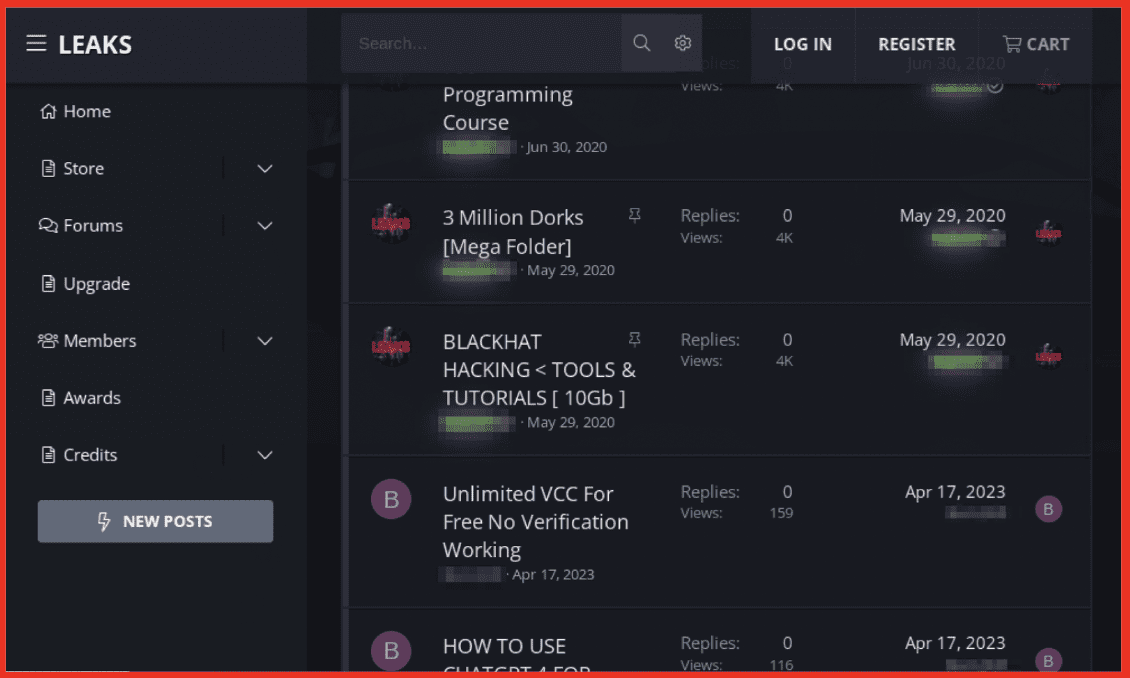
Figure 11: Shadow Leaks Site; Source: Tor Anonymous Browser
Figure 12: Data Offered on Shadow Leaks Site; Source: Tor Anonymous Browser
The sites and Telegram channels covered in this blog post are just a fraction of what is available on the darknet and darknet-adjacent sites in terms of leak sites. Some of them specialize in one area of stolen data, such as only selling credit card information. Or a site will focus on certain parts of leaked data, like stealer logs, and sell them with a few other products.
While selling personal data on the darknet is not a new concept, DarkOwl analysts have noticed a trend of sites that specialize in selling leaked or personal data which are smaller than more well-known marketplaces, yet almost exclusively dedicated to leaked data.
These sites release their leaked information differently from ransomware groups. A wide variety of products for sale such as drugs and malware are not offered. Instead, the leak site focuses almost exclusively on personal data. They have decided to specialize in offering leaked data even though they are not ransomware gangs nor are they ransomware affiliated.
Final Thoughts
As the widely popular Breached Forums was recently seized by law enforcement and shut down, the darknet community will be keen to see who takes the place of Breached Forums. Breached Forums offered a massive amount of data in one place, could vet the data posted, and was viewed by users of the forum as a trustworthy middleman service to facilitate transactions between vendors. While Breached Forums offered accountability to buying, selling, and downloading leaked data, its centralized nature also helped it become a massive target for law enforcement. The rise of leaks-focused Telegram channels and sites could point to a trend of decentralization. Relying on a hub and spoke model of decentralized darknet networks and darknet-adjacent channels offering leaked data would put darknet users at a higher risk of being scammed but potentially a lower risk of the site being taken down by law enforcement. Overall trends point to small groups and individuals selling leaked data, not just ransomware groups, highlighting that there are more decentralized avenues for individuals to buy, sell, and download leaked data.
Curious to learn how darknet data applies to your use case? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















