One Year Later: A Look Back at the Ukraine Conflict and its Impact on the Global Criminal Digital Ecosystem
February 24, 2023
Blog now available in Report form > See PDF Version here.
Exactly 365 days after Russia invaded Ukraine in 2022, the Ukraine-Russia conflict shows no sign of ending and an adjacent global cyberwar continues to wage in underground corners of the internet. However, its effects are substantial with impacts felt across numerous sectors of our society and western economies. While cruise missiles and artillery shells rain on villages across Ukraine, the digital underground has experienced its own mix of chaos and drama, impulsive and unpredictable shifts with criminal communities that have had to quickly adapt to an ever-dynamic global geopolitical climate.
In this research, we’ll look at how ransomware shifted from an affiliate-driven extortion-based crime model – purely motivated by financial gain – to a quite effectual digital weapon deployed to disrupt key supply chains and carry out cyber espionage operations.
Shifts in Digital Landscape Due to Cyberwar: Key Takeaways & Analyst Observations
In the last year, cybersecurity attacks against industrial control systems (ICS) skyrocketed in volume and sophistication, with infrastructure across Russia, Ukraine, and NATO countries directly targeted. Ukraine has experienced varying degrees of ICS attacks, including widespread electricity outages due to new strains of wiper malware developed by Russian hackers. Nevertheless, Ukraine’s cyber defenses were stronger than anticipated and ineffective cyberattacks resulted in Russia resorting to using cruise missiles to plunge towns into darkness and disarray.
With this anniversary of the Ukraine invasion, we found once harmless online communities of Mr. Robot fans, cyber vigilantes and hacktivists of all ages evolve into highly specialized cells of militarized cyber warriors willing to wage digital war on behalf of their collective personal beliefs and societal causes.
The use of Telegram and non-Tor based peer to peer networks rose exponentially in use in the last year with threat actors relying on the instant messaging chat platforms for coordinating their cyber campaigns and sharing targeting and reconnaissance data. If anything, the cyberwar has also demonstrated that distributed denial of service (DDoS) attacks is still a highly effective tactic for disrupting and distracting SOC analysts and network defenders, especially when conducted in conjunction with offensive cyber operations in support of military and intelligence initiatives.
Kinetic & Cyberwar Recap: Initial Invasion Preceded by Cyberattacks
Several days before troops and tanks rolled across the border of Ukraine on 24 February 2022, Russia-aligned darknet threat actors defaced government websites, conducted DDoS attacks against banks, spewed propaganda and disinformation, and leaked sensitive Ukrainian citizen data from key government servers they had compromised. The invasion was also preceded with the Russia’s debut of WhisperGate and HermeticWiper malware variants that they deployed in ransomware-style attacks against key academic institutions, non-profit, and government organizations.
Exactly one hour before the invasion, Russia hit critical KA-SAT satellite infrastructure with DDoS attacks followed by EL MIPS malware used to infect Viasat satellite modems and routers with AcidRain destructive wiper malware, knocking thousands of customers offline. The two-punch cyberattack resulted in an immediate and significant impact to critical military communications across Ukraine.
IT Army of Ukraine Emerges
Ukraine’s cyber response plan was carefully crafted by its Minister of Digital Transformation – Mykhailo Albertovych Fedorov – who coordinated one of the most successful, multifaceted information operations campaigns ever witnessed in history.
Less than 48 hours after the invasion, Federov bravely sought out assistance from the darker corners of the internet – posting across darknet criminal forums and chatrooms – calling for help in conducting offensive cyber operations against Russia and in turn, formed the first ever IT Army of Ukraine. Ukraine setup a dedicated Telegram channel – amassing hundreds of thousands of hacktivists and cyber mercenaries as followers – where the Ministry shared critical targeting data and digital tools for safely conducting attacks against Russian infrastructure and services. The Ministry has since formed smaller specialized teams when they realized Russian nation state threat actors were monitoring the public Telegram channel to mitigate the cyber-attacks and began countering with their own disinformation operations.
The IT Army of Ukraine not only helped Ukraine successfully turn offensive in the digital realm, but also was the foundation for a highly successful psychological operations campaign deployed across social media and open-source news media that called on major retailers, western companies, and suppliers to stop trading with Russia for their war crimes and atrocities.
Zelensky’s nightly address to the Ukrainian people and the world – shared on Telegram and Facebook – shaped public perception and helped Ukraine not be forgotten and to this day continues to receive international financial aid, humanitarian support, and global solidarity.
War Divides Darknet Criminal Gang Alliances
In the early weeks of the cyberwar, several prominent darknet criminal communities – many rich with both Russian and Ukrainian based threat actors – were forced to choose sides in the war. Conti openly aligned with their Russian motherland, resulting in their quick demise and the release of their source code, internal private chats, and details of their botnet infrastructure. Conti’s key members were doxed and the long-believed software development collaboration between Conti and Trickbot was confirmed.
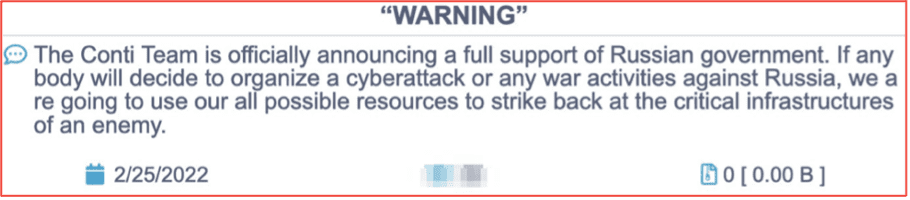
Figure 1 – Source: Conti Service Hosted on Tor Anonymous Network
While the US government has a $10 Million USD bounty for additional details on members of the Trickbot and Conti gangs, many members of the once most successful but now-defunct ransomware group have simply shifted to other ransomware operations and evaded arrest. This resulted in the quick rise of Blackbyte and Blackbasta ransomware and Karakurt’s extortion as a service operations. In the fall, a new ransomware group emerged called “Monti” which uses the same tactics, techniques, and procedures (TTPs) as Conti as well as the same encryption methodologies. Threat researchers continue to debate whether Monti is a doppleganger or an evolution of Conti spawned by previous Conti members.
Other ransomware gangs like STORMOUS – known for their ransomware attack against Coca-Cola – quickly ended up having their servers attacked and their services taken offline, not long after announcing their allegiance to Russia. Arvin Club, defaced STORMOUS’s Tor service and leaked the contents of STORMOUS’s SQL databases on their Telegram channel.

Figure 2 – Source: Arvin Club Tor Service
The splintering of darknet communities continues to this day across various criminal sectors of the darknet. Many a darknet discussion forums include a multi-paged Ukraine war related thread where information for-and-against the invasion has been heatedly contested. There is significant increase in offensive activity from Russia-aligned threat actors like Killnet and the IT Army of Russia, who proliferate the Kremlin’s propaganda in support of debunked conspiracy theories, e.g. US biological warfare research and neo Nazism in Mariupol and across eastern Ukraine, with hopes to recruit underground sympathizers who can assist with cyberattacks against Ukraine and NATO targets.
For example, earlier this year, Killnet announced their intent to target hospitals and medical institutions across multiple NATO countries. DarkOwl confirmed Killnet likely collaborated with a new DDoS-as-a-service botnet called Passion, developed by a group with the same name, in their disruptive, malicious campaign.

Figure 3 – Source: Killnet Telegram Channel
[TRANSLATED FIGURE]
It’s very simple – for the support of the Nazis of Ukraine, we demolish all the grids of medical institutions in these countries:
- USA
- Portugal
- Spain
- Germany
- Poland
- Finland
- Norway
- Netherlands
- United Kingdom
This information is not worth your sideways glances. Better remember the Donbass – the shootings of hospitals, schools and kindergartens. These creatures crave death every minute and stimulate their dream with the help of heavy weapons.
Wake up, fellow countryman – before it’s too late! @KILL FIRST!
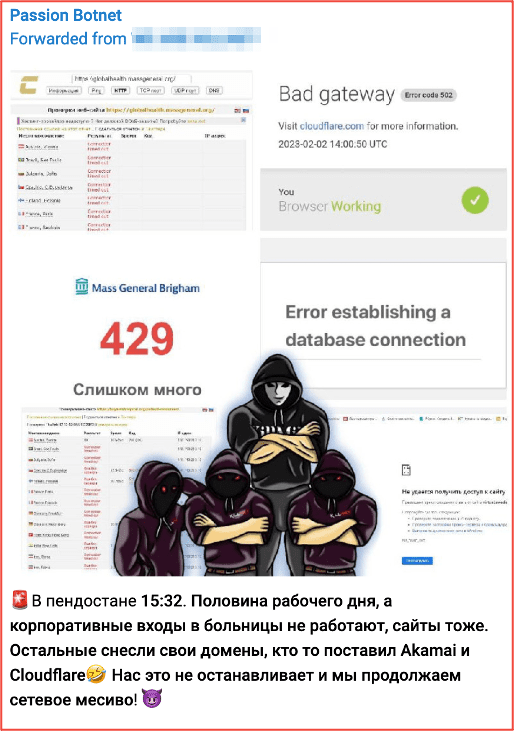
Figure 4 – Source: Passion Botnet Telegram Channel
[TRANSLATED FIGURE]
In Pindustan 15:32. Half of the working day, and corporate entrances to hospitals do not work, websites too. The rest demolished their domains, someone put Akamai and Cloudflare 🤣 This does not stop us and we continue the network mess! 😈
Anonymous Responds with Largest Global Operation to Date, #opRussia
The Anonymous Collective publicly responded to Ukraine’s call for help, and simultaneously carried out hundreds of offensive cyber campaigns against Russia in the group’s largest operation to date, #opRussia.

Figure 5 – Source: YouTube
Anonymous’s support contributed to the success of Ukraine’s information operations and illuminated the advanced capabilities of cyber cells like GhostSec, NB65, GNG, GhostClan, and dozens of others. Hundreds of databases surfaced on the darknet that were used for follow-on offensive operations, including Russian government credentials, sensitive military operational data, the personal identities of prominent and influential members of the Russian oligarchy along with their investments, and sensitive internal communications from the Russian FSB.
After Russia withdrew from the Kyiv suburb of Bucha, and the atrocities and war crimes of rape and murder of its citizens were revealed, anons successfully identified the identities of Russia’s 64 Motor Rifle Brigade military personnel responsible. Anonymous also hacked CCTV cameras of a CDEK shipping location to expose Russian military personnel shipping stolen goods from Ukrainian homes. Hacktivists followed with cyberattacks against CDEK servers containing customer data to exfiltrate the identities of the Russian military personnel by name.

Figure 6 – Source: Anonymous Twitter Account
Anonymous hacktivists successfully interrupted Russian television, Russian streaming services, compromised hundreds of CCTV cameras across Ukraine and Russia, defaced Russian EV car charging stations, and ATM machines. Sensitive internal data from the Central Bank of Russia and Sberbank appeared on darknet forums and marketplaces along with numerous other critical infrastructure providers like Gazprom, ROSCOSMOS, Transneft, and hundreds of other Russian military contractors and suppliers. Anonymous echoed the Ministry’s call for commercial companies to pull out of Moscow on social media and threatened companies that they would become the Collective’s next targets if they did not comply. Shortly after, KelvinSec infiltrated Nestle’s internal servers for their continued operation in Russia and leaked several databases containing their customer data and shipping details.
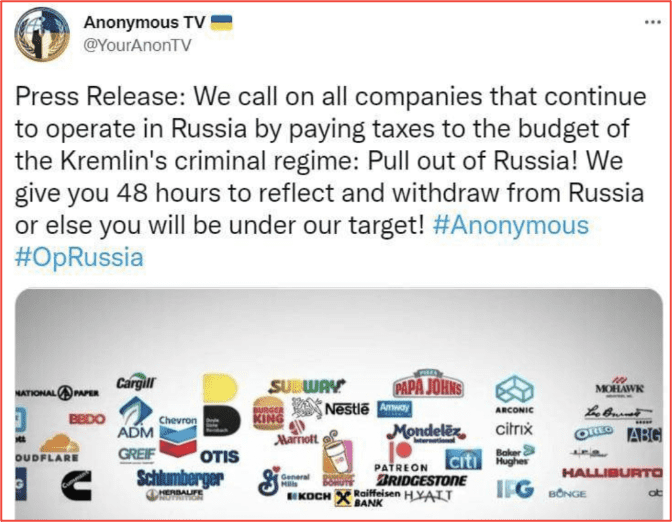
Figure 7 – Source: Anonymous Twitter Account
Hacktivist campaigns against Russia continue to this day. Earlier this week, Russia’s Ministry of Emergency Situations confirmed that air raids sounding across Moscow was indeed the result of hacked radio stations broadcasting fake air raid signals. The IT Army of Ukraine also called for DDoS attacks against Russian television stations and broadcasting companies, 1TV and VGTRK, during Putin’s state of the union speech where he claimed America provoked the invasion of Ukraine and called for a suspension of the START nuclear arms treaty between Russia and United States.
War Causes Surge in Communication on non-Tor Anonymous Networks
Despite the discourse and upheaval between threat actors on the darknet, Tor continues to be the anonymous network of choice for victim shaming and content delivery networks hosted by ransomware gangs. The network also continues to house key discussion forums and marketplaces like XSS, exploit, and RAMP. But what is most noteworthy is the surge in Telegram popularity and its use by cyber criminals and cyberwar participants over the last year.
For example, since the war began, DarkOwl’s collection of content from Telegram has quadrupled in volume. Thousands of Telegram channels now share real-time battlefield reports, promote disinformation, and proliferate malware in use by cyber hacktivists and nation state threat actors. One of the Telegram channels that produce the highest volume of unique documents in DarkOwl Vision is a Russian channel titled, “Чат Военкоров Русской Весны” [translated] “Chat of Military Officers of the Russian Spring.” Other war-specific channels like @wargonzo, self-described as a “subjective view on war and weapons” boasts over 1.3 Million subscribers.
Expectation of Cyberattacks Against Industrial Control Systems Keeps Everyone on Edge
Russia’s use of unique wiper malware at the start of the invasion and their success in cyber-based infrastructure attacks disabling electricity grids across Ukraine in 2015 and 2016 prompted an elevated security posture of not only Ukrainian but NATO and western countries’ cyber defenses. CISA advised in April 2022 that threat actors – including Russian military operatives – could (and very possibly would) exploit vulnerable industrial control system (ICS) and critical supervisory control and data acquisition (SCADA) devices such as:
- Schneider Electric programmable logic controllers (PLCs),
- OMRON Sysmac NEX PLCs, and
- Open Platform Communications Unified Architecture (OPC UA) servers.
The ominous CISA advisory was drafted after Dragos published an in-depth report detailing the potential of CHERNOVITE’s PIPEDREAM ICS malware. More recent analysis from Red Balloon adds Siemens SIMATIC and SIPLUS S7-1500 series PLCs to the list of potentially vulnerable ICS related devices.
Throughout the last year, various hacktivists groups have targeted these specific devices to disrupt critical infrastructure. AnonGhost allegedly attacked the МонтажРегионСтрой г. Рязань [translated] Montazhregionstroy Ryazan streetlight system in Russia shortly after publishing screenshots of a Moxa control panel and dozens of IP addresses related to their systems. The provocative Anonymous adjacent cyber cell, GhostSec evolved in the technical significance and severity of their attacks they conducted against targets across Russia and Belarus with claims they successfully targeted and shutdown multiple ICS-related control panels.
Figure 8 – Source: GhostSec Telegram Account
GhostSec more recently claimed they successfully carried out the ‘first ever’ ransomware attack of an ICS-related remote terminal unit (RTU) for an unspecified victim network in Belarus. The group shared screenshots of a TELOFIS RTU968V2 terminal with the string “fuckputin” appended to the end of several files. Information security researchers have questioned the legitimacy of the group’s claims, but the idea of attacking Linux-based RTUs is not out of the realm of possibility. Newer strains of ransomware like Royal and Lockbit 3.0, which have materialized since the invasion of Ukraine, directly target ESXi found in Linux and virtual machine servers. While direct ICS-specific attacks have been less severe than anticipated, critical industrial market segments such as mining, oil, electrical and natural gas, water, food and agriculture, saw a remarkable increase in successful ransomware attacks by darknet threat actors. This coupled with a report from Chainanalysis indicating total ransomware payments in 2022 were over 40% less than the last two years, suggests the ransomware ecosystem has potentially transitioned into an instrument of geopolitical agendas instead of pure extortion crime.
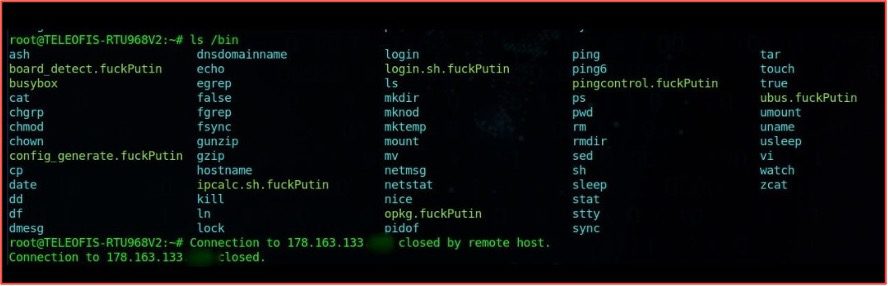
Figure 9 – Source: GhostSec Telegram Account
Earlier this week, GhostSec continued their offensive campaigns against critical Russian infrastructure with claims that they successfully shutdown Russian and Belarusian satellite receivers exposing sensitive global navigation satellite system (GNSS) data. The legitimacy of their claims could not be verified, but satellite systems have been regularly targeted by pro-Ukraine hacktivists since the start of the war.
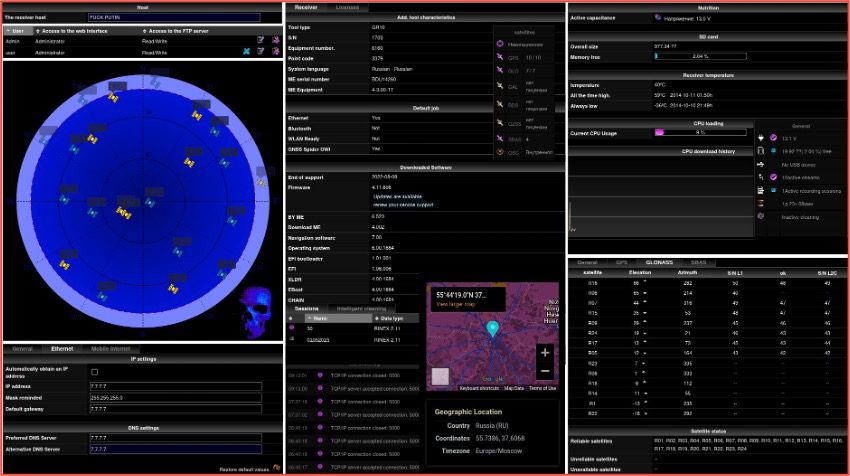
Figure 10 – Source: GhostSec affiliated Twitter account
NATO Weapons Surface For Sale on Darknet Marketplaces
While most of this report has been focused on the impacts of the global cyberwar and malicious cyber campaigns conducted for and against Russia since the invasion, we should also mention the war has also caused a surge in the availability of advanced weaponry on darknet vendor shops and marketplaces.
Black market weapons dealers previously specializing in the trade of small arms and handguns on the darknet are now offering US/NATO weapons presumably sourced from Ukraine. Over the last year, DarkOwl has had multiple detections of advertisements for Javelin ATGMs for sale for $15,000 – $30,000 USD, NLAWs for $8,000 USD, and AT-4s & RPGs for less than $1,000 USD. Last fall, Switchblade 300 and 6000 Kamikaze drones appeared in stock quantities consistent with theft from the battlefield.

Figure 11 – Source: Black Market Guns Tor Anonymous Network
Ukraine, Cyberwarfare, and the Amelioration of Hacktivism
The invasion of Ukraine and its prompting of a worldwide cyberwar has forever changed the landscape of the darknet, with alliances disrupted and key operations impacted across various underground communities. Telegram is now a critical data source for information sharing not only about the war but other criminal enterprises as collective acceptance and adoption of the chat platform over the Tor network is widespread.
The activation of hundreds of thousands of hacktivists and cyber vigilantes to help carry out highly effective cyber campaigns and concerted DDoS attacks has been realized in ways we could only have previously imagined. It also comes with chaos as unpredictable cyber cells step on top of each other and potentially compromise the country’s greater military and intelligence initiatives. That reality prompts real consideration for the possibility such hacktivists are emboldened more than ever to keep on fighting even if a peace treaty between Ukraine and Russia is drawn, or the potential use of a similarly capable online army against a western democracy by a nefarious or rogue nation state in the future.
If anything, the invasion of Ukraine and the events of the last year has shown us is that cyber is an increasingly critical component to a nation state’s military arsenal and its ability to ultimately defend its critical infrastructure, territory, and sovereignty. The Ukrainian people’s resolve in not submitting to its invading Russian neighbors has been mirrored by those who have stepped in to support Ukraine in helping protect its networks and continue to conduct offensive cyber campaigns and information operations on their behalf a year later. The modern battlefield is indeed asymmetric in the most literal sense of the word, with digital warfare also waged psychologically, economically, and socially. In increasingly hyperconnected digitally dependent societies, cyber will be an effective realm to influence and disrupt our enemies for decades to come.
To learn more about how having visibility into darknet data can combat commercial and national security threats, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















