Password Hygiene and Awareness: Trends from the Darknet
May 05, 2023
In honor of this week’s World Password Day, we took a look at how different password trends have evolved over the past year. In doing so we found that many people are still making common password mistakes, such as using their favorite year or using highly popular (and crackable) strings of characters like “123456”. Read on for a breakdown of these trends, as well as some additional insights from our data science team.
Passwords on the Darknet
Credentials are one of the most sought after and frequently exchanged digital goods in the darknet economy. In many cases, large quantities of compromised accounts will be combined and reshared across multiple darknet and deep web forums, including dark web adjacent platforms such as Telegram. Criminals leverage this data in a variety of ways. For example, some may use a credential cracking or “stuffing” tool to cross reference emails with other password lists – or use common password conventions to guess the password – and verify an active email and password combo. In the gravest of cases, when active corporate accounts are discovered, they can be used to gain initial access into a company’s network and allow the intruder to commit a crime such as ransomware.
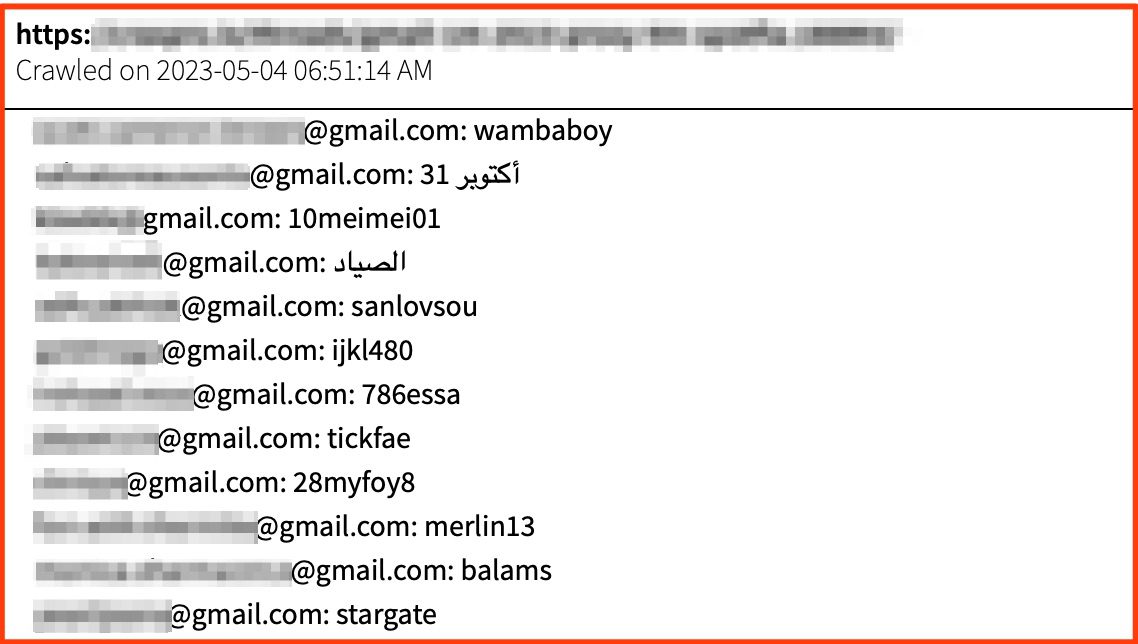
Credential lists also sometimes appear with an email + hashed password combination. However, this is less common and is considered moderately less risky as it requires the threat actor to go through the process of unencrypting the password to make use of it.
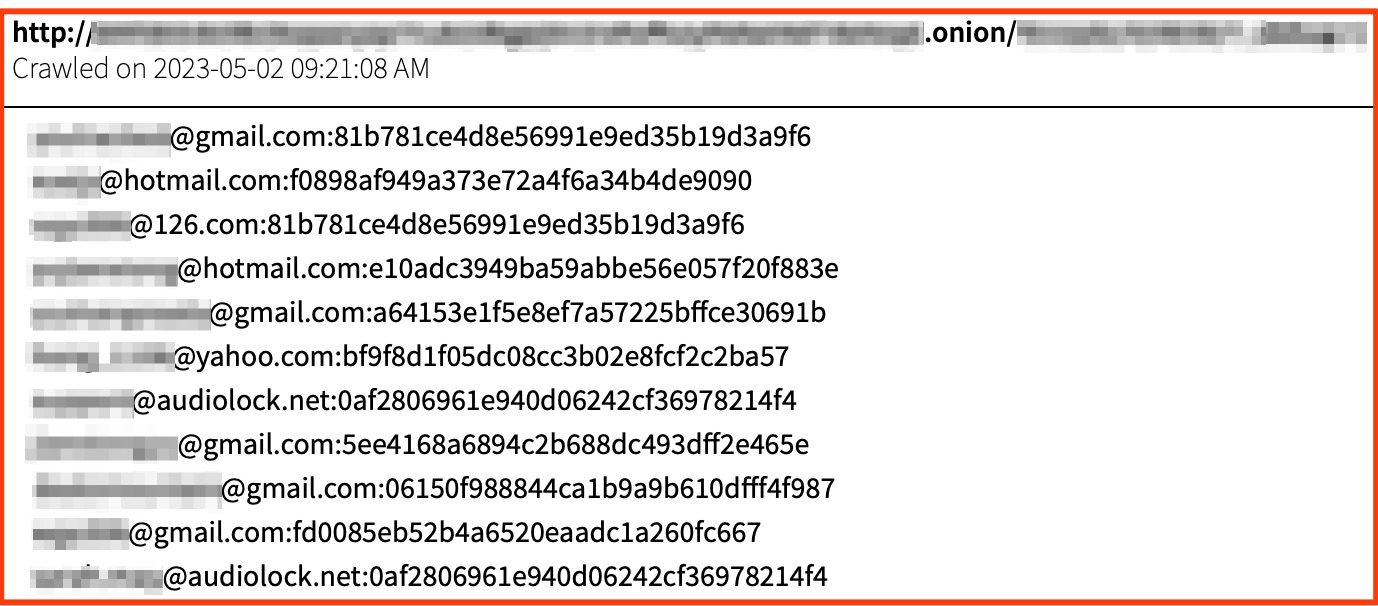
Changes in Password Volumes in DarkOwl Vision
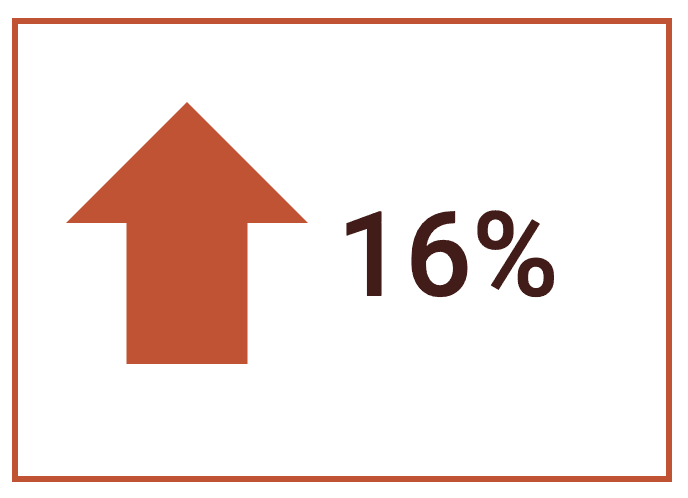
Overall, we saw a 16% increase in the total number of email addresses in our darknet data. In 2022, we detected 8,680,000,000, which has since risen to 10,069,116,483 total compromised emails. Though this does include some that did not have associated passwords, an exposed email still poses a degree of risk.
Of the exposed emails in our dataset, over 50% of them appeared with an associated password. The total number of email and password combos detected currently is 5,681,306,514 – up from 5,460,000,000 last year.
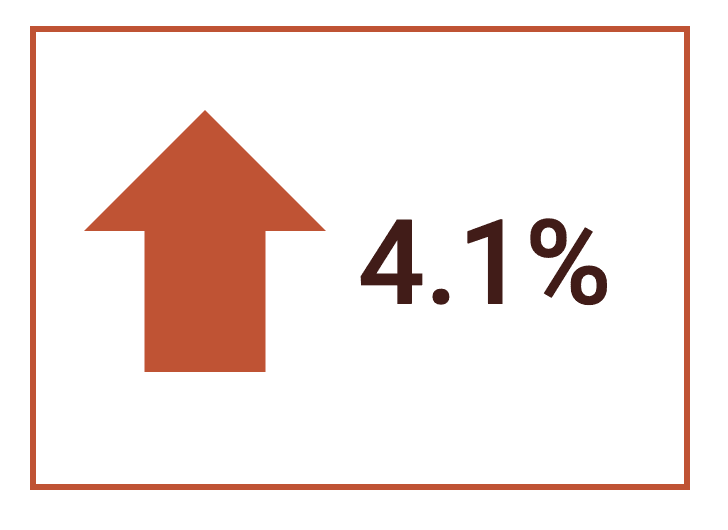
Alarmingly, the number of plain text passwords with an associated email jumped by over a fifth in the last year. We detected 5,160,309,835 with plain text passwords as compared to last year’s 4,285,451,030.
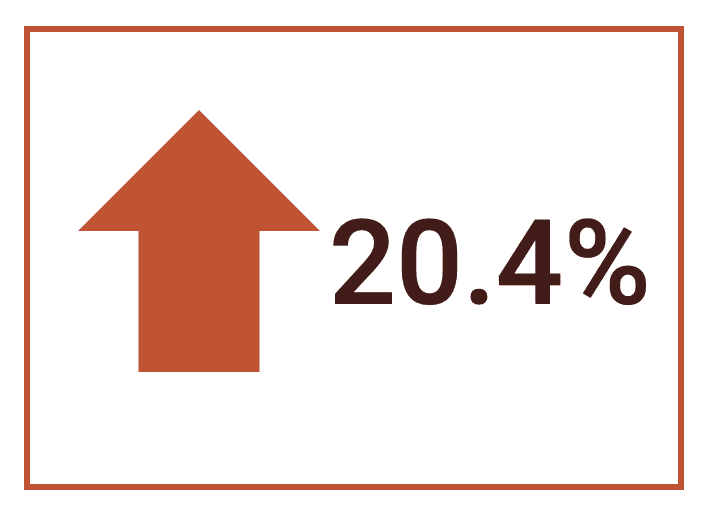
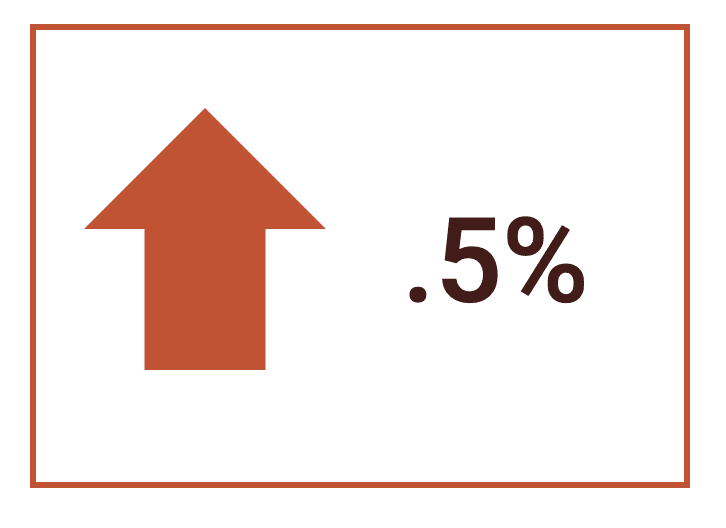
Overall, the number of emails with associated hashed passwords remained fairly consistent. 2022 analysis indicated 518,566,724 hashed password and email combos, which has only risen slightly to 520,996,679 this year.
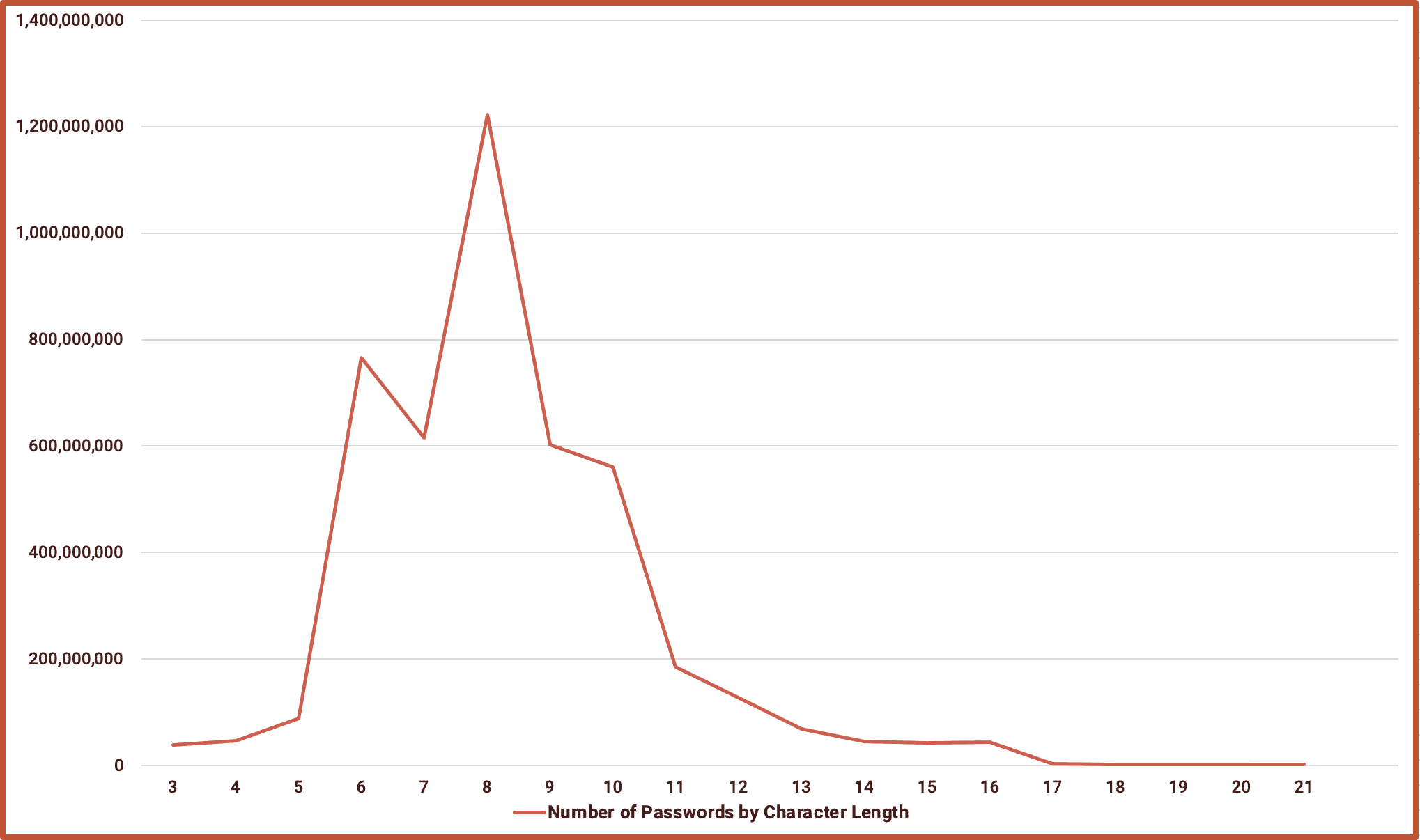
Password Lengths
Of the plain text passwords we analyzed, 8 characters is by far the most common password length. We expect to see that number shift in coming years as companies implement more rigorous password policies including multi-factor authentication (MFA).
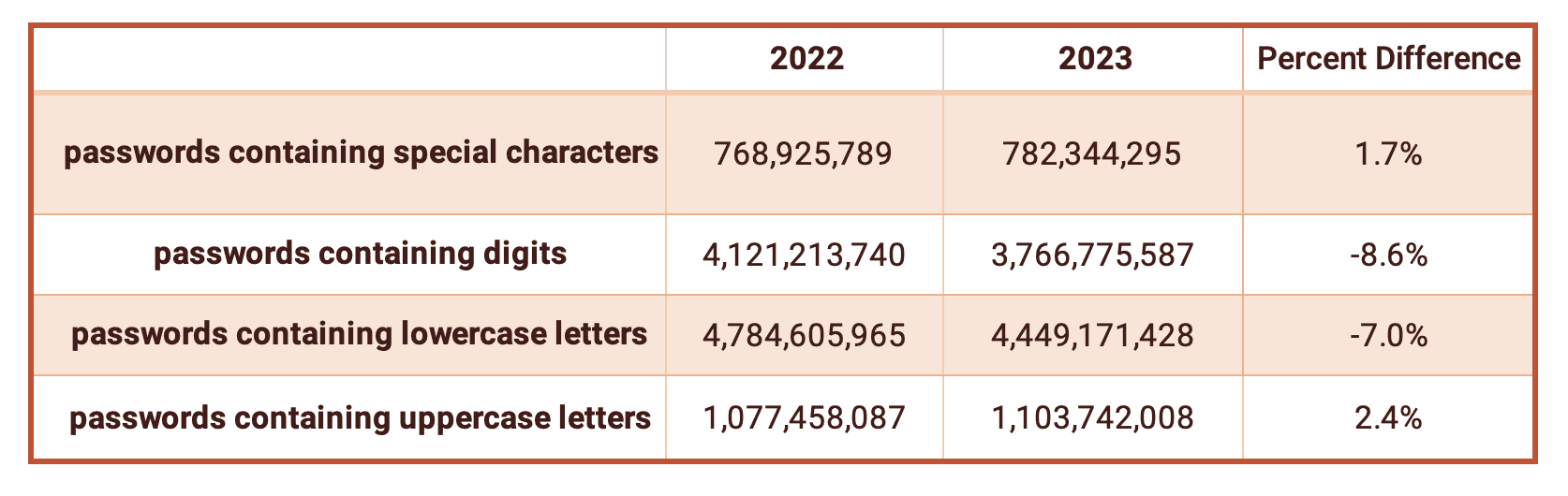
Password Strengths
A positive trend of note is that over the past year, we saw an increase in the total number of “strong” passwords. Per industry standards, “strong” passwords are defined as containing special characters, digits, lowercase, uppercase, and length greater than 8 characters. Overall, we detected 643,498,941 passwords that are considered “strong” – up from 637,000,000 last year.
On the flip side, we saw a decrease in the number of passwords using digits by nearly 10%. Using digits, as well as special characters is highly recommended as a method of defending against password crackers. Unless an 8-character password includes numbers and symbols, the password can be potentially brute forced.
Common Patterns Persist
Perhaps out of laziness, a common trend that we see consistently with passwords is the use of strings of digits or characters that can be easily made on a keyboard. This unfortunately appears to be a persistent trend, with the number of people using “123456” or “123456789” increasing across the board.

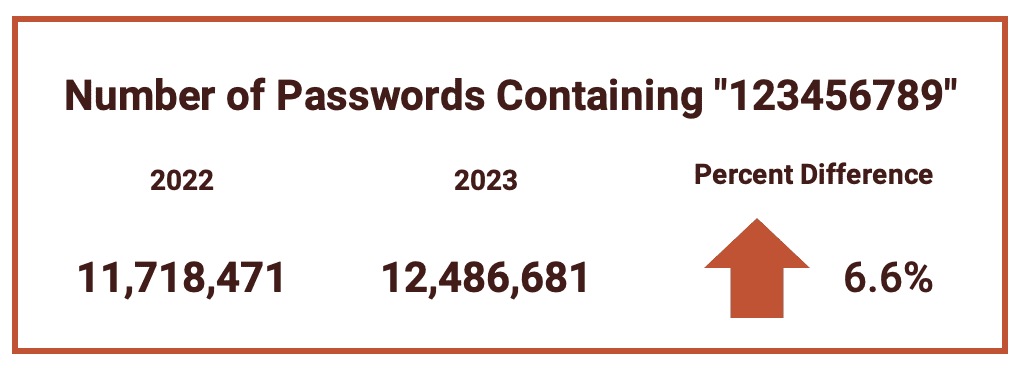
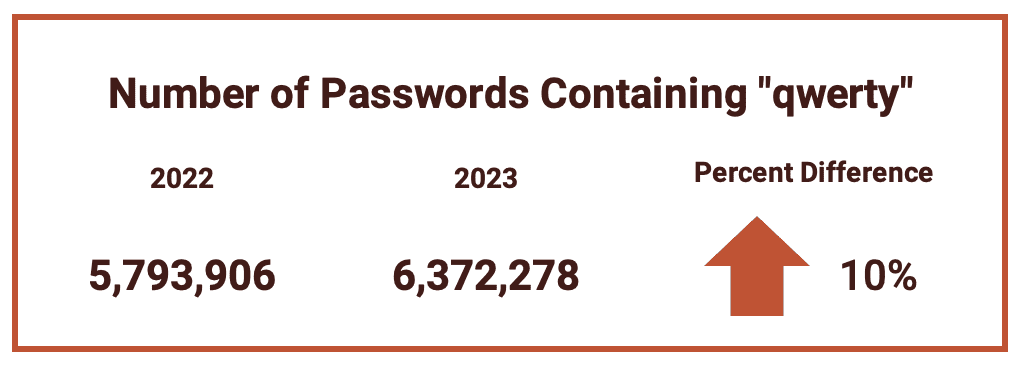
While less popular that number strings, other keyboard patterns “qwerty” remain a popular choice of password. In fact, the number of passwords containing or comprised of “qwerty” jumped by 10% this year.
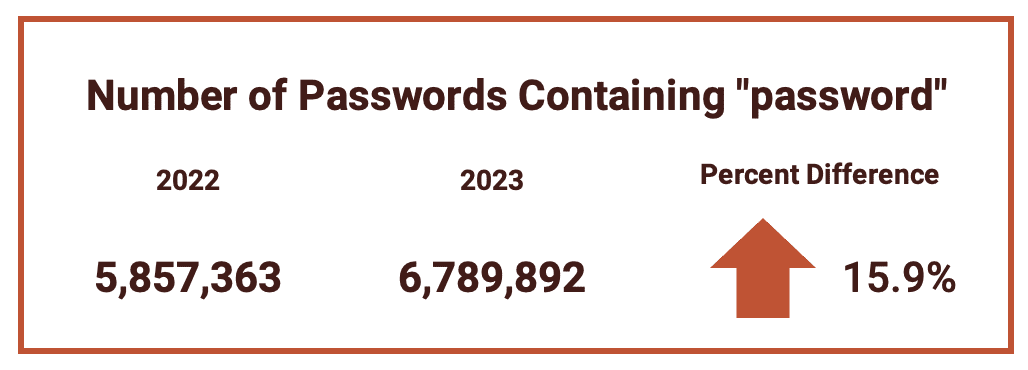
Perhaps most egregiously, we saw a massive jump in the amount of exposed email addresses who’s associated password was literally “password”.
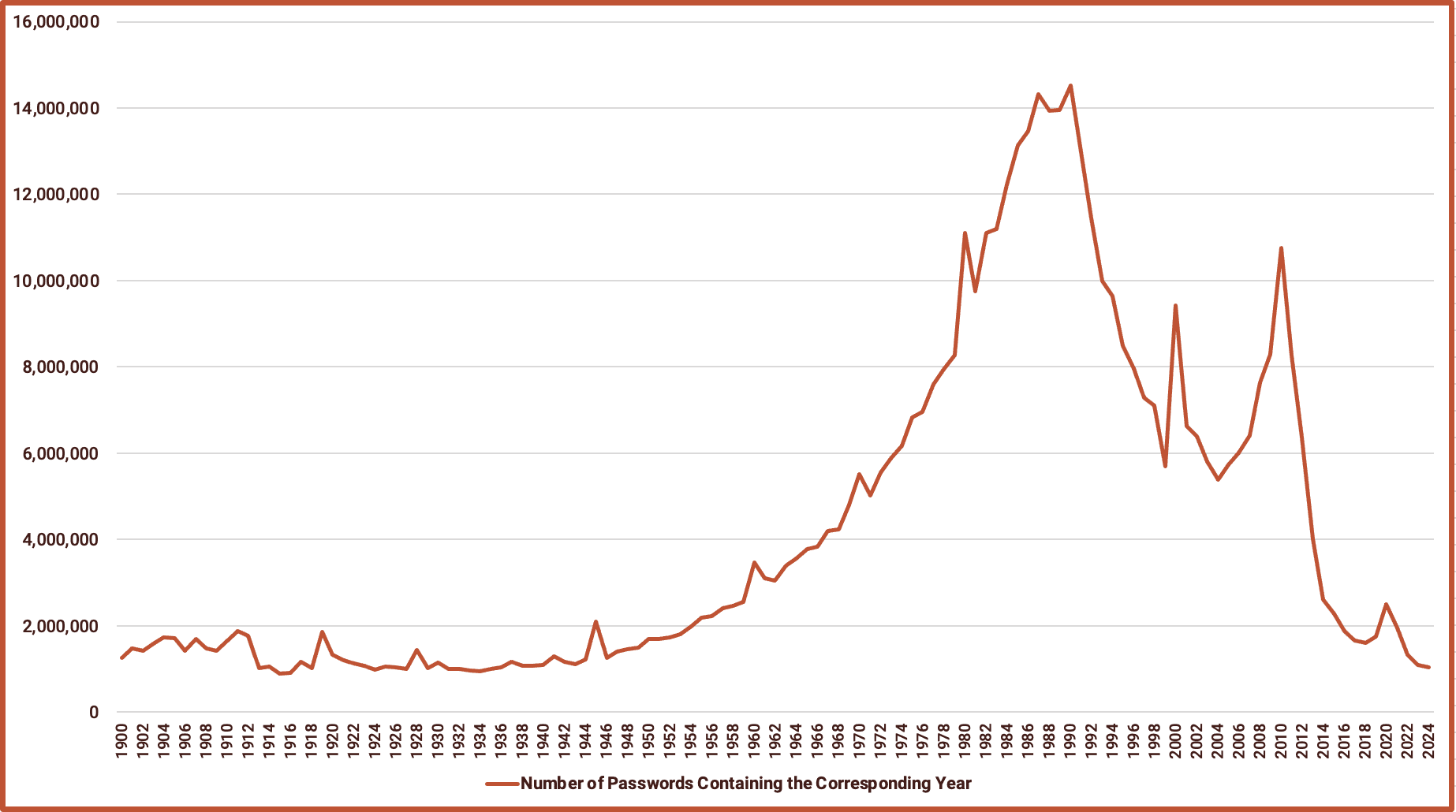
Using Your Date of Birth or Anniversary as a Password is Still a Bad Idea
A relatively sizable portion of the passwords we analyzed contained a year date, such as “darkowl1990”. Interestingly, we found 102368238 passwords with that followed a yyyy-mm-dd format, and 13223 with passwords with yyyy/mm/dd. While this is positive in that it utilizes special characters, the prevalence of users who incorporate a date into their password means that threat actors will leverage this to attempt to brute force accounts.
The most popular year detected in our data is 1990, with 14,518,056 containing that year. Years between 1990 and 1999 remain the most popular, which is consistent with last year’s analysis.
Hashed Passwords
In cryptography, hashing involves using a mathematical algorithm to map data of any size into a bit string of a fixed size. In password hashing, a ‘hash’ consists of a unique digital fingerprint (of a fixed size) corresponding to the original plaintext password which cannot be reversed. There are several different types of ‘hashing algorithms’ available for encrypting passwords.
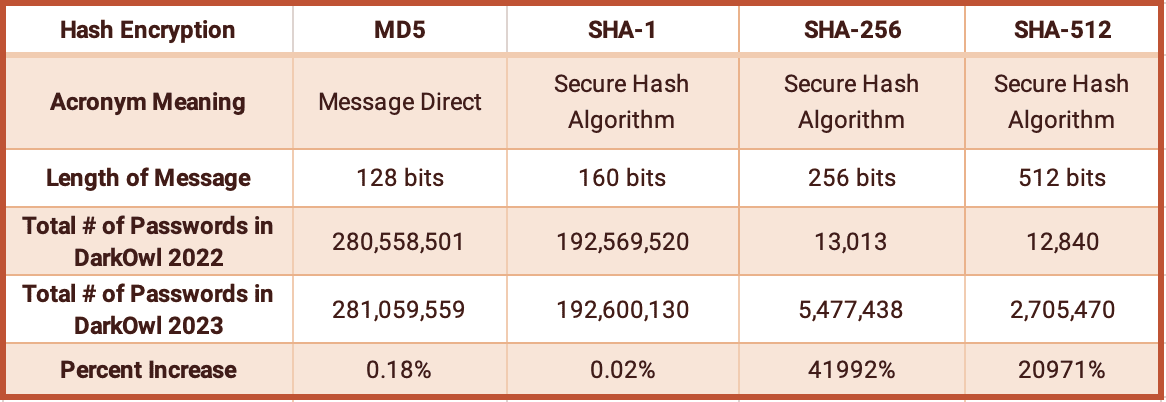
The most common hash in DarkOwl’s darknet collection is MD5, followed by SHA-1. While this is consistent with last year, we did not see an increase in hashes of this type, as one might expect to happen as more data is collected over time. On the other hand, over the past year we saw a massive jump in SHA-256 and SHA512 hashes from 2022. This suggests that these types of hashes are becoming more popular and we should expect to see this number grow in the coming years.
Other Takeaways: Trends in Password Sharing Between Accounts
According to reporting, 51% of people use the same password for their work and personal accounts. To see if our data is consistent with that account, our data team conducted an analysis to estimate the number of “shared passwords” between work and personal accounts. To do this, our data team partitioned the data into two categories: commercial email providers (gmail, yahoo, etc.) and companies (DarkOwl, Apple, Microsoft, etc.). Then, we looked for the number of accounts that had the same username between company and commercial emails, such as [email protected] vs. [email protected].
Once detected, we looked for the number that shared the same username and the same password. In doing so we found that 45% of matched accounts re-used the same password. This is likely an under-estimation due to variations in naming conventions across email accounts, but supports the notion that using the same password for multiple accounts is a highly common practice. Overall, we detected 35,085,849 instances of linked email addresses that appeared with the same password.
In addition to being able to search all collected darknet data for exposed credentials, DarkOwl extracts entities such as IP addresses, credit card numbers, bank identification numbers, and cryptocurrency addresses. This enables an organization to search specifically for relevant entities, such as server IP addresses and email addresses on the same darknet forum. Learn more about Entity API.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















