The Art of Combolist Cracking and Credential Stuffing
December 01, 2022
The Science of Credential Stuffing
DarkOwl regularly reviews topics designed to inform both corporate and personal entities of threats discussed on the darknet. In this blog, we will cover credential stuffing to augment other research activities like, “The Darknet Economy of Credential Data: Keys and Tokens” and “Zoom Accounts For Sale on the Darknet Highlight On-Going Need for Better OPSEC” which also discuss credential data risks. We will discuss the motivations and techniques behind combolist cracking and credential stuffing attacks and explore some of the recent darknet communities that rely on credential stuffing operations for their own criminal agendas.
Automation and the Credential Stuffing Attack Methodology
Credential stuffing – often shortened to simply ‘cred stuffing’ – is the process of automatically testing exposed username and password combinations against website login forms for potential account take over (ATO) or malicious exploitation. When we think of darknet threat actors we often visualize sophisticated computer users, with elite programming and scripting skills, conducting cyber operations at scale with numerous monitors of black screens and scrolling green text. Credential stuffing utilizes customized and readily available scripts to test thousands (if not millions) of credential combinations against web applications for verification automatically.
In software development lingo and even some corners of the darknet, this process is described as technically a form of “fuzzing” or ‘black-box’ testing of a website or web server application. Many of these scripts and functional utilities are in circulation for free across darknet communities – with tutorials and instructions – and available for the novice cybercriminal interested in entering the ‘cred stuffing’ market little knowledge of elite scripting or hacking.
Wordlists & Wordlist Generators
Wordlists and compromised lists of email address and password combinations are the foundation for credential stuffing operations. Many multi-million record data leaks in circulation on the darknet like Collection #1-5, RockYou, and the Compilation of Many Breaches (COMB) make potential username/password combinations easily discoverable and exploitable at scale. Such leaks are utilized as input for credential stuffing scripts and applications. Wordlists are also in regular circulation amongst darknet threat actors, and some are already integrated into Linux distributions favored by pen-testers and hackers alike.
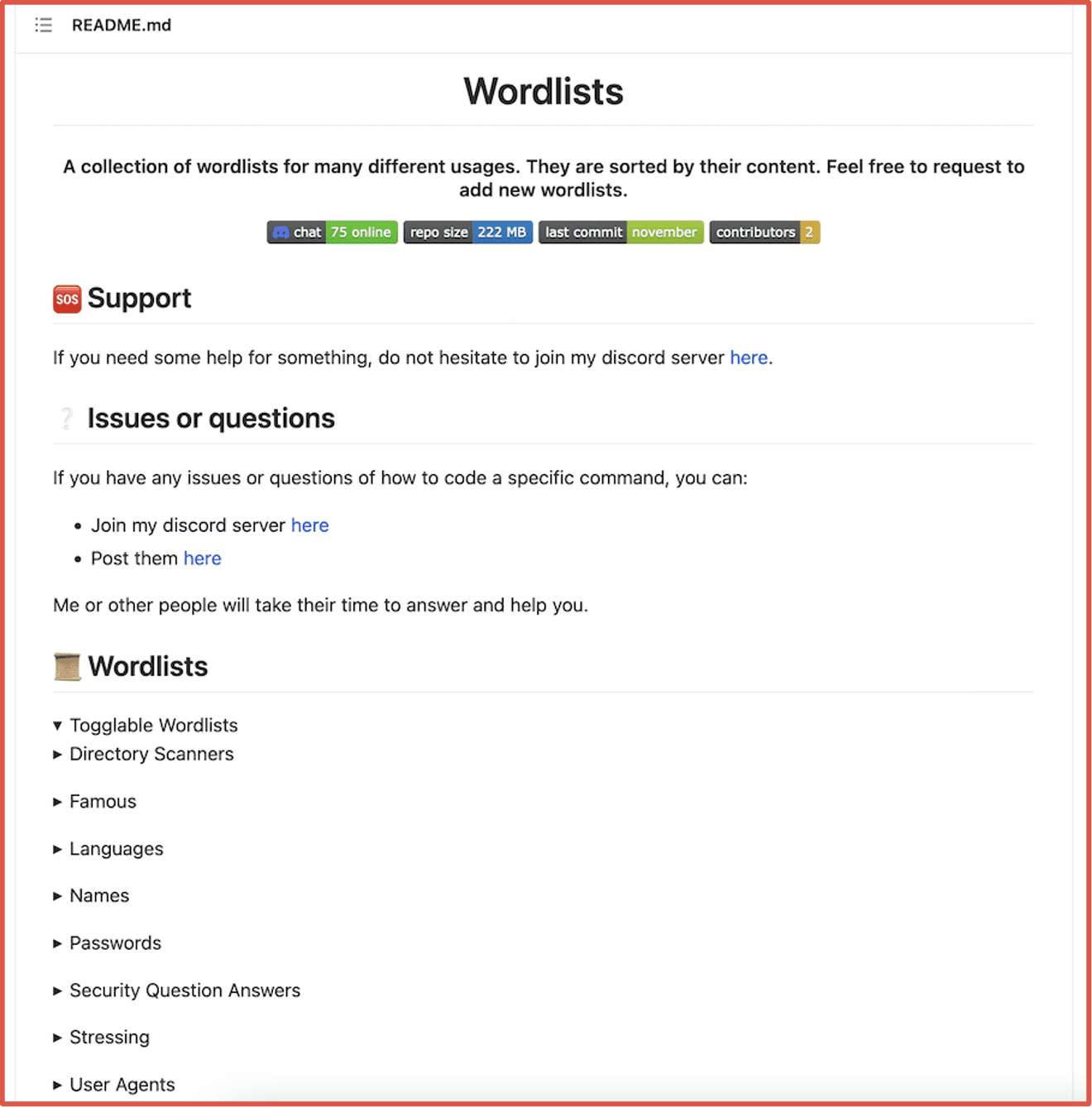
Figure 1: Wordlist Github Repository Popular with Offensive Security Specialists, Source: https://github.com/kkrypt0nn/wordlists
There are numerous Wordlist generator utilities one could use to automate the creation of random strings of a specified length of alphanumeric characters, symbols, and common dictionary words. DarkOwl analysts have observed mentions of CeWL and Pydictor on forums popular with Chinese threat actors and others like BEWGor (yes, pronounced “booger”), Crunch, and the Common User Passwords Profiler (CUPP) across other deep web communities.
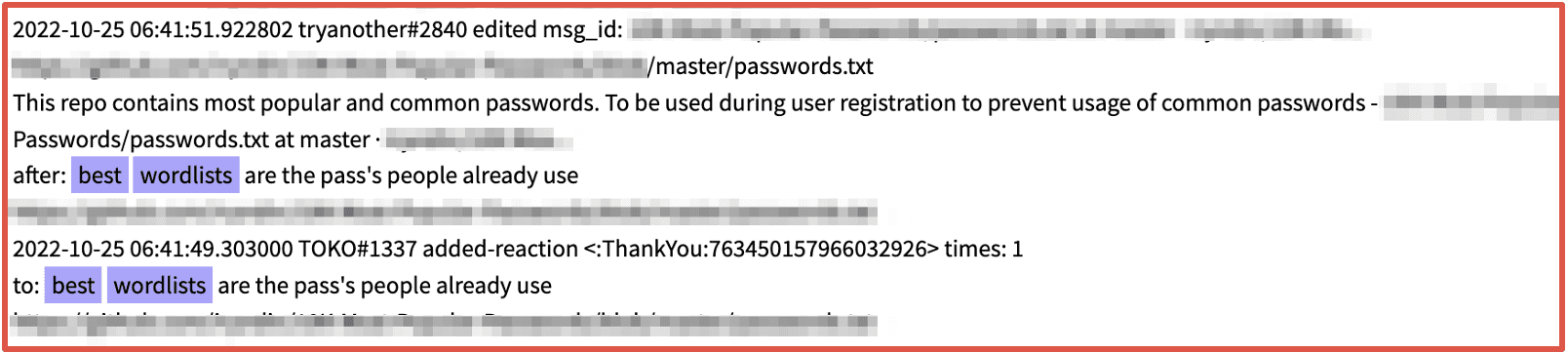
Figure 2: Source DarkOwl Vision
Another user on Telegram enthusiastically referred other channel members to a repository containing Bopscrk, advertised as a “smart and powerful” wordlist generator that combines wordlist data and personal information for the account targeted like date of birth and favorite musical artists, to generate customized permutations of passwords with higher probability of success.
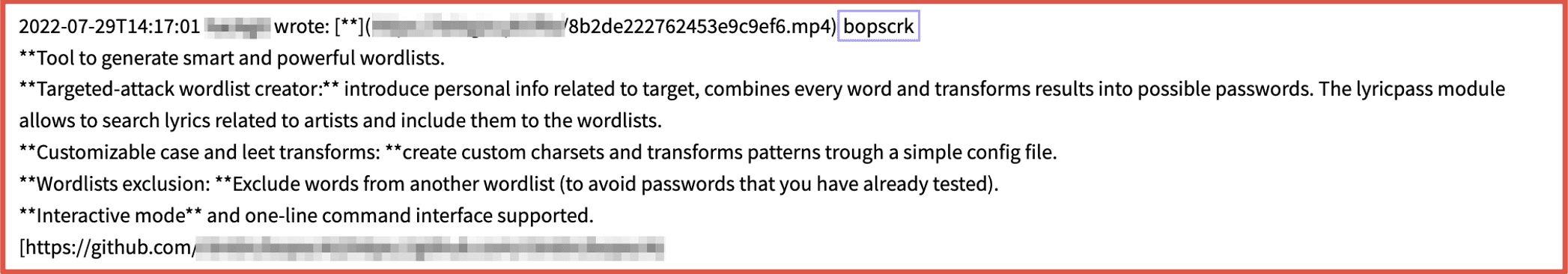
Figure 3: Source DarkOwl Vision
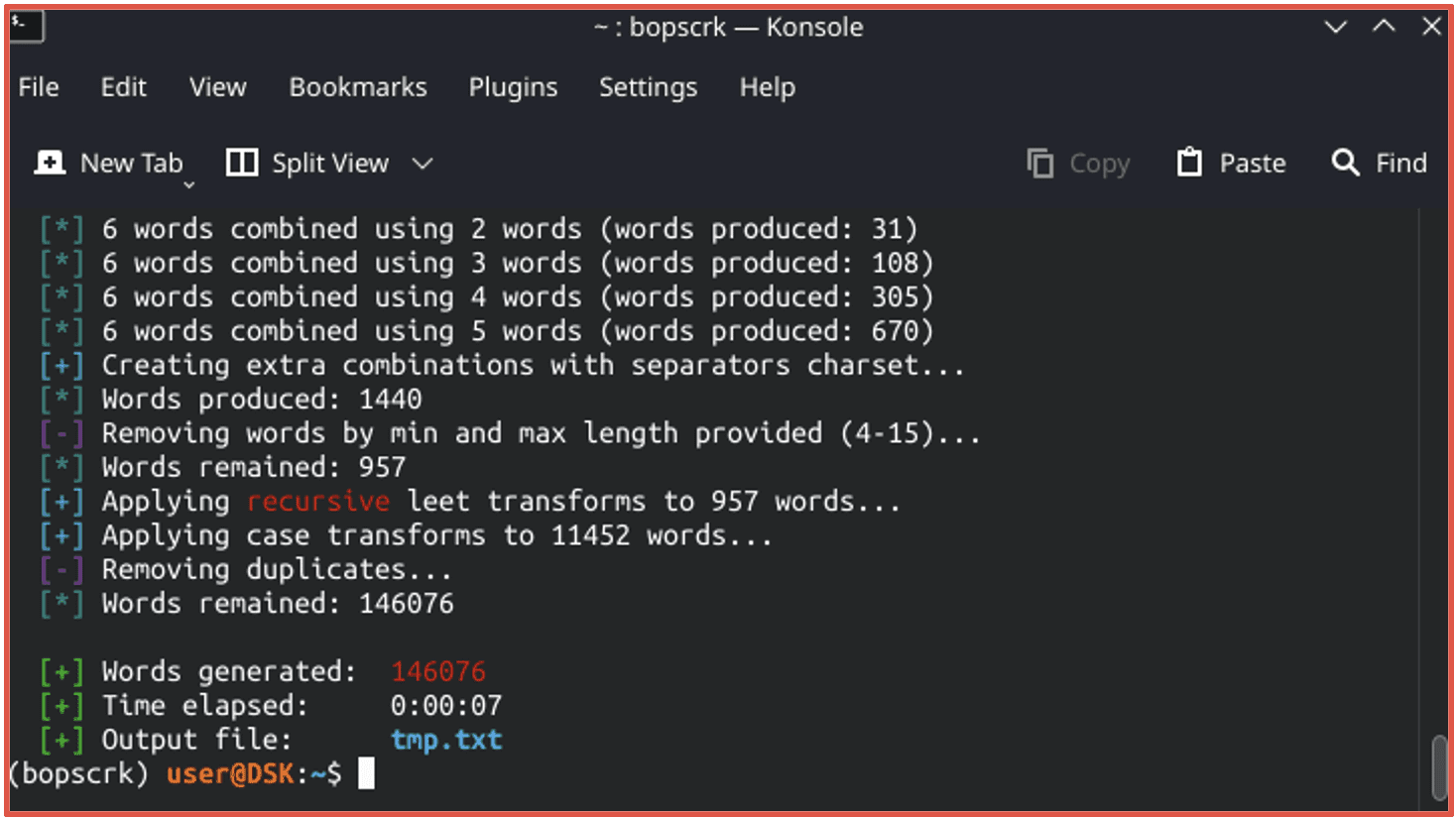
Figure 4: Source Redacted
Links to wordlist text files and wordlist generators are shared across darknet forums and chatrooms that facilitate ATO and many of them are hosted on Github. As of time of writing, there are over 5,000 repositories containing wordlists on Github alone. Dictionary lists in English are the most common, but other languages are also available.
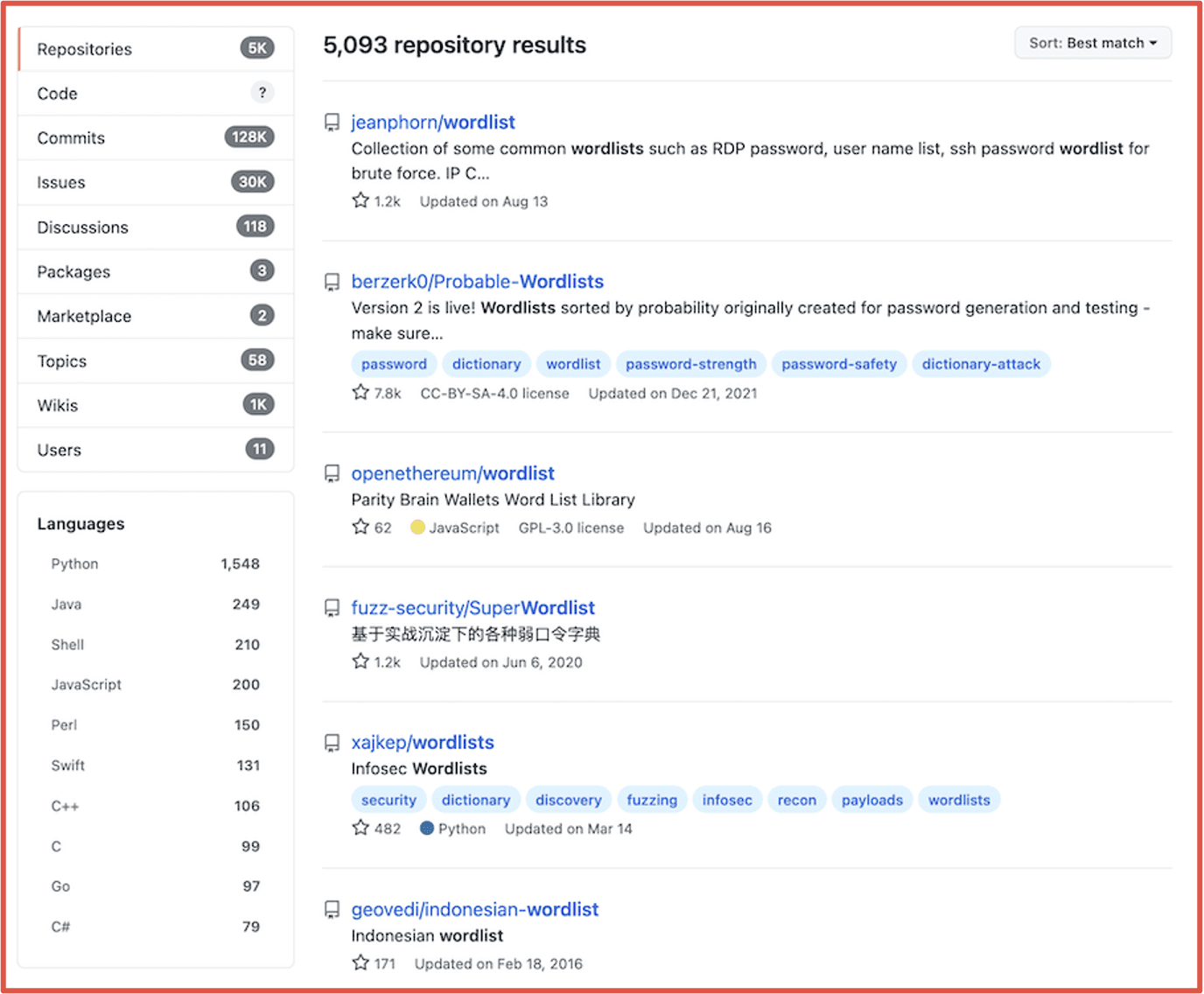
Figure 5: Summary of Wordlists Available on Github, Source: https://www.github.com
Scalable exploitation of stolen or compromised data will persist and we anticipate the development of more sophisticated automation utilities and maintenance of existing lists to continue. Since offensive security specialists will also continue to develop and utilize wordlists for their network vulnerability assessment activities, cybercriminals will leverage these where available. Anything that is readily in use for offensive security purposes will also be exploited for malicious gain.
Credential Validation Applications & Proxy Lists
Once a threat actor has several wordlists in their arsenal, they will utilize credential stuffing utilities and botnets to test various username and password combinations (called ‘combos’) against web applications and websites. Often cybercriminals will reuse web application testing programs like OpenBullet or SentryMBA that were originally designed for good but are now coveted and circulated by cybercriminals for optimizing crime. Older programs like Vertex and Apex work similarly to Sentry, but struggle to authenticate with more enhanced SSL or HTTPS secured websites.
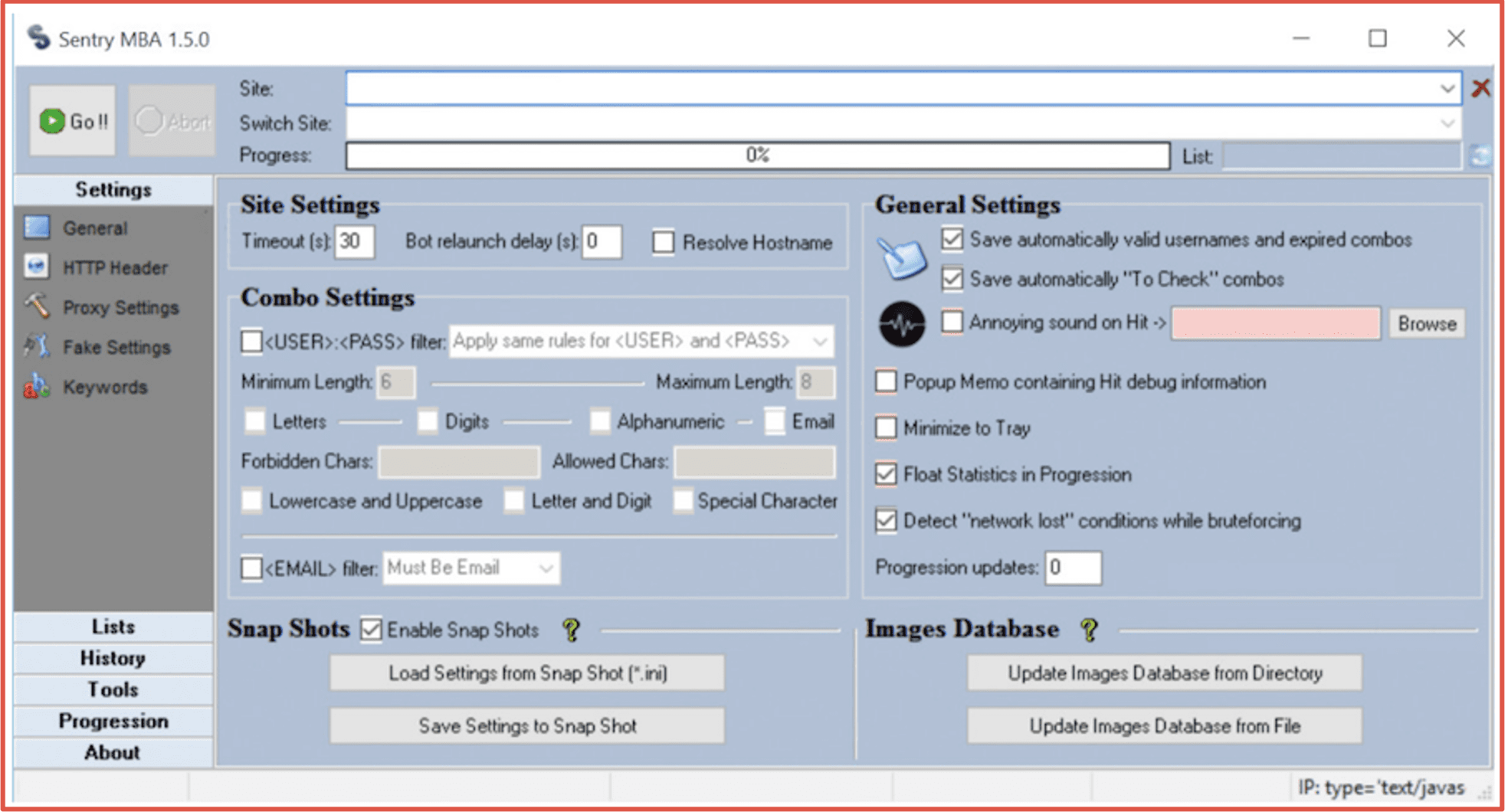
Figure 6: Screenshot of SentryMBA Application
Credential stuffing programs are traded hand-in-hand with proxy lists in order to conduct operations while resembling organic network traffic and obfuscate the reality that all the account logins originate from the same IP address. Programs such as AzLiquidGold, SlayerLeecher, BlackBullet, STORM and Snipr were designed by hackers with the pure intent as proxy-enabled scrapers and “combo-checkers.” Residential proxies are available for purchase for under $5 USD on most darknet forums and marketplaces.
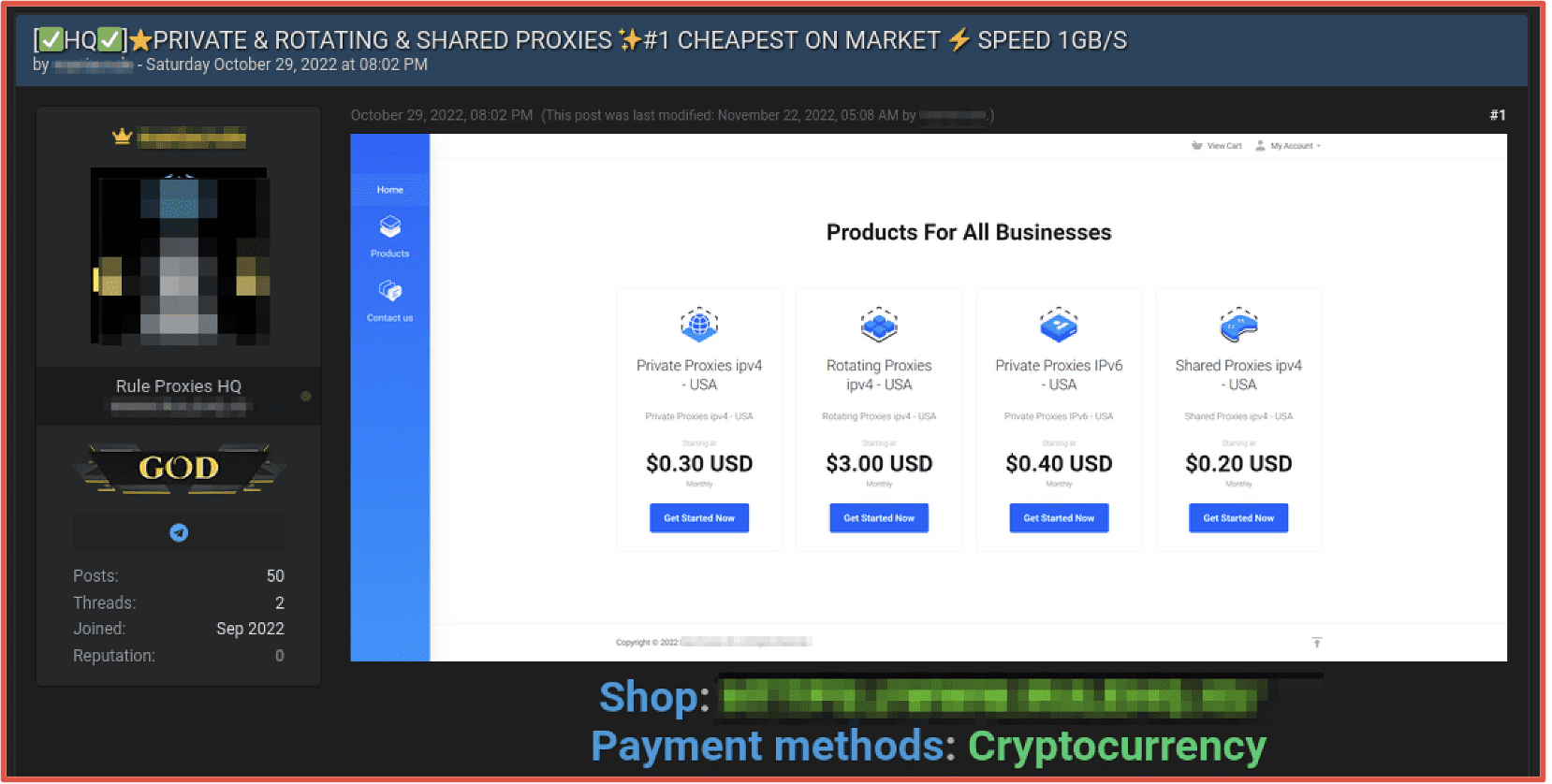
Figure 7: Source Darknet Forum Tor Browser
Credential Stuffing and the Darknet Data Community
There are numerous deep web and darknet forums and Telegram channels that support the credential stuffing economy of the darknet. Users in the darknet often refer to those in the business of validating and circulating authentication user/password combinations through the process of credential stuffing as “crackers.” Actors share validated credential data on darknet forums and describe them as “freshly cracked” on markets and Telegram groups. Other accounts on offer are described as “logs” – which can be confusing when the vernacular is mixed with malware-based information “stealer log” offers. However, in the credential stuffing and cracker community, “logs” is short for “logins.”
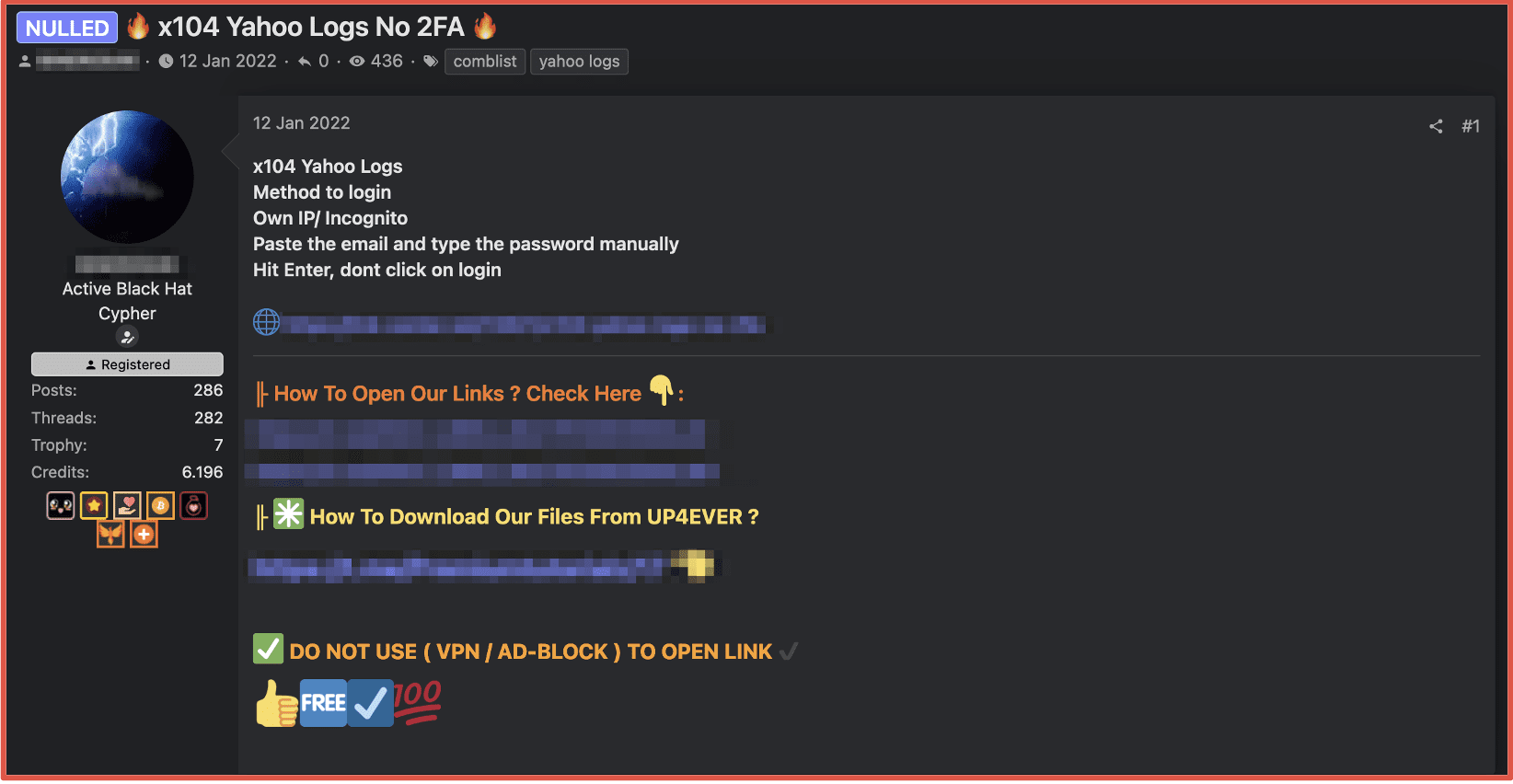
Figure 8: Source Cracking Forum via Tor Browser
Accounts are further advertised as high quality (HQ) or ultra-high quality (UHQ) with and without two-factor authentication (2FA) or described as full access (fa) indicating that some additional personally identifiable information (PII) is available to maintain persistent access the online account. Accounts for popular online commercial applications, email providers and streaming services are compiled and sold in bulk for a higher price. Some accounts sell for as little as $1.50 USD per account and combos in higher volumes, e.g. 100,000 accounts for Hotmail or Outlook for 100 Euros.
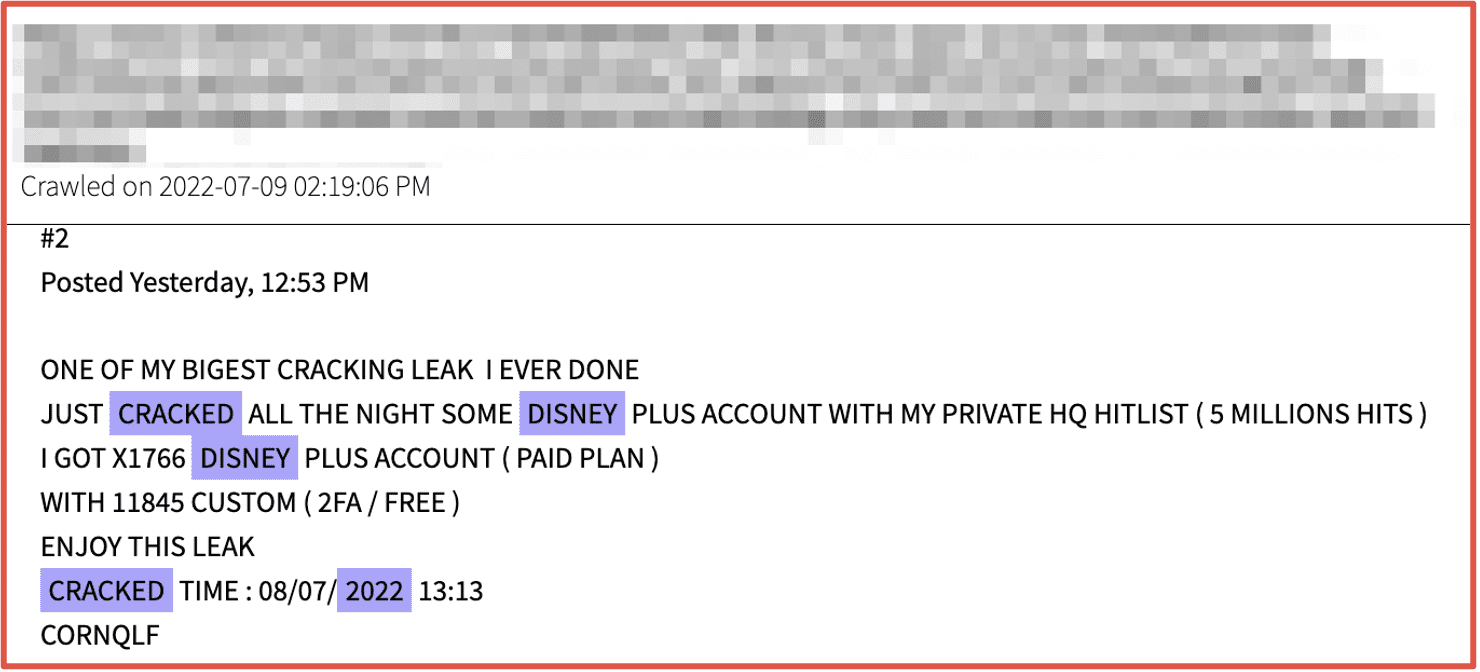
Figure 9: Source DarkOwl Vision
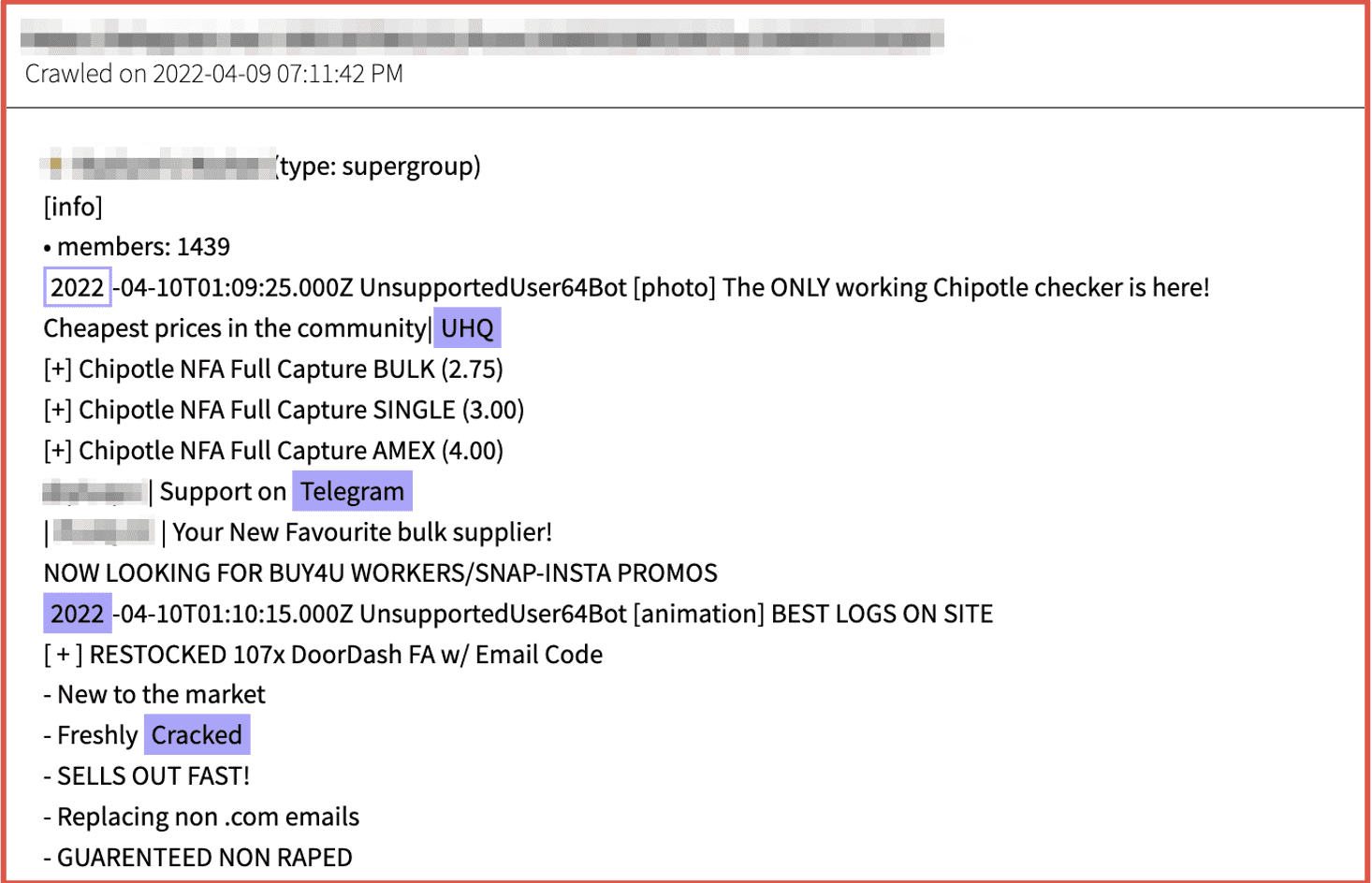
Figure 10: Source DarkOwl Vision
Higher volume databases of cracked accounts also appear on forums as “combolists” that are traded and sold for further exploitation. Some combolists are advertised by web platform, geographic region, and others are simply described as “mixed combos.” DarkOwl has observed several advertisements containing millions of verified account credentials in a single file.
But I Have Multi-Factor Authentication…
Defensive security measures like multi-factor authentication (MFA) provide some degree of protection against account takeover using a compromised server username/password combination. Unfortunately, one cannot assume MFA is 100% effective at protecting the victim account from an ambitious cybercriminal. Many individuals disregard exposure in a combolist with such security measures in place, and will not even bother to update the account with a new more complex password. The flaw in this logic is that once a combo has been verified, especially for a target with high probability of financial or information return, such as blackmail or extortion crime, then a cybercriminal will willingly purchase the combo with more malicious intention. Using an exposed combo for a personal email account like Yahoo facilitates additional targeted phishing or social engineering on social media or other platforms to obtain additional PII to bypass MFA, e.g. security question answers, seed phrases, mobile phone numbers, and digital identity authenticator tokens.
Other leaks of personal data, such as LinkedIn profiles and telecommunications and mobile phone provider’s databases, provide the foundation for conducting a targeted attack against a victim, especially for websites with basic SMS-based One Time Password (OTP) protection. There are also tools readily available like Burp Suite that support OTP-bypass attacks installed in Kali Linux. When MFA bypassing for more sophisticated applications is required such is the case with corporate network accounts, then the cybercriminal might utilize simswapping, also known as simjacking or port-out scamming techniques.
While a simple commercial combolist and verified accounts appear for free or even relatively cheap in the darknet marketplaces, accounts with potentially higher financial return like validated accounts from banking or financial institutions and cryptocurrency wallets trade at significantly higher prices. One user on Telegram advertises individual Coinbase accounts for sale at $60-100 USD depending on the value of the wallets. Even cold wallets have been successfully compromised using sophisticated social engineering methods that cyber fraud criminals pride themselves on.
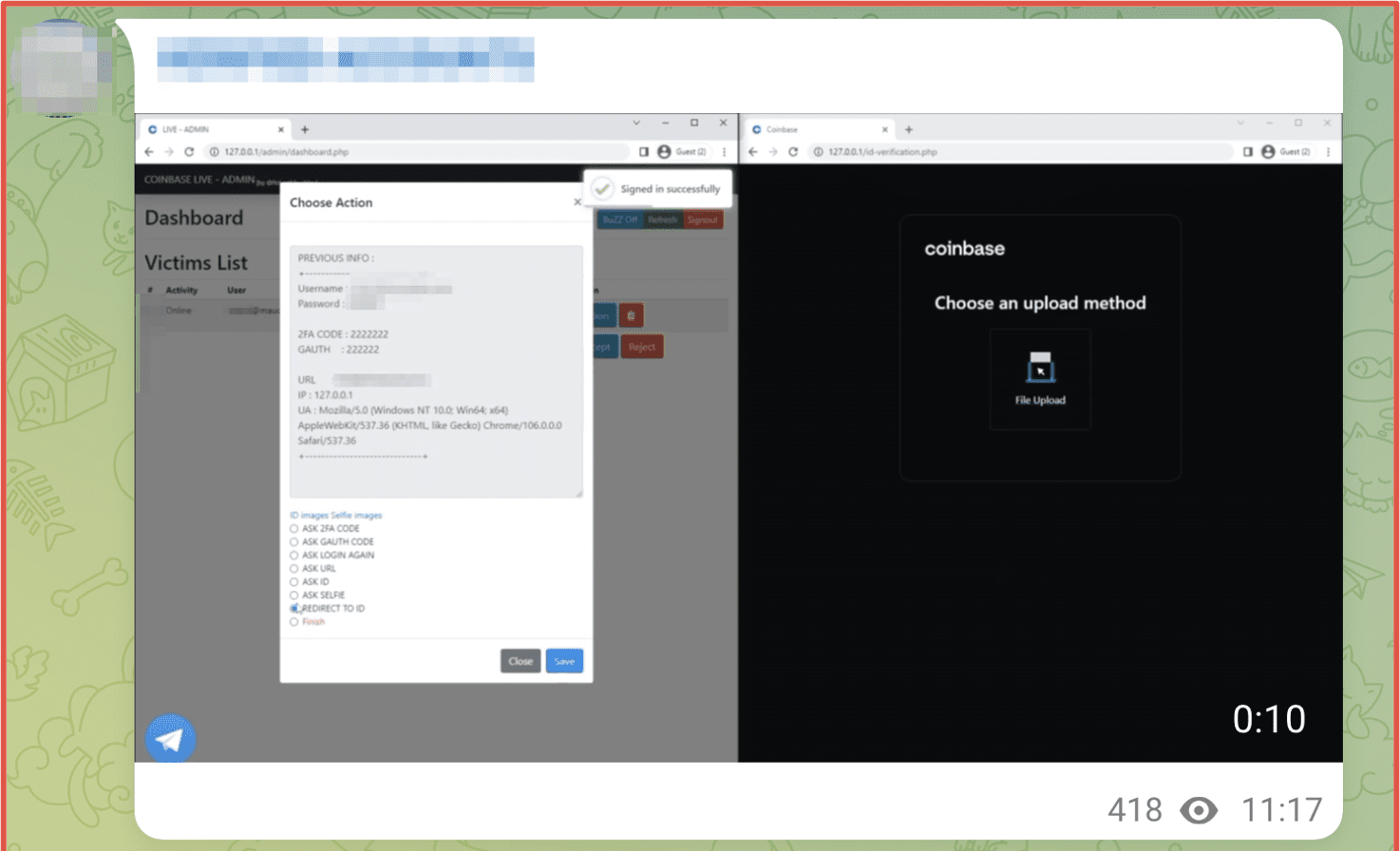
Figure 12: Source Telegram, Channel Redacted
In Conclusion
While credential stuffing as a technique is not new, the new tools and tactics that are emerging are increasingly sophisticated. As ransomware attacks have become more frequent in recent years and continue to be on the rise, the availability of leaked credential and user data has as well. This ultimately makes credential stuffing even more efficient as a means of brute forcing account takeovers, as there is more data for hackers to cross reference and attempt to use to gain access.
Get in touch to learn how DarkOwl can help.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















