Understanding Risk to Corporations and Individuals
August 30, 2022
NEW: Download this report as a PDF.
Risk is a word regularly used across information security circles and CISO agendas. Companies are aggressively attempting to identify and mitigate any cybersecurity risk that could lead to potentially extensive financial and reputation damage, especially from a high-profile cybersecurity attack or data breach. Meanwhile, individual persons also struggle to know how concerned they should be in mitigating their own personal risk to when, not if, their sensitive personal information appears on the deep web and darknet.
In this blog, DarkOwl analysts revisit and review the domain of risk, taking a closer look at the threats corporations and individuals face and how risk is calculated and mitigated. Underground digital communities within hidden and anonymous networks are an integral role in identifying the threats at play, and DarkOwl works alongside its partners to help provide the critical monitoring of potential markers of risk using its darknet search platform.
Darknet 101
The darknet is a layer of the internet that was designed specifically for anonymity. It is more difficult to access than the surface web, and is accessible with only via special tools and software – specifically browsers and other protocols.
You cannot access the darknet by simply typing a dark web address into your web browser. There are also darknet-adjacent networks, such as instant messaging platforms like Telegram, the deep web, some high-risk surface websites.
What is Risk and What is the Darknet’s Role in Risk Calculations?
Risk is traditionally thought of as a multiplier of likelihood and severity, or consequence of outcome; however, in cybersecurity the definition is expanded for consideration of intention or threat.
For example, in a personal risk scenario, one’s leaked credentials (e.g. usernames, e-mail addresses and passwords) might appear in commercial data breach leaks, which poses one degree of risk, but the minute those same credentials appear in conjunction with direct malicious intent to cause financial or direct harm, their personal risk increases dramatically.
Quick definitions:
darknet: Also referred to as the “dark web.” A layer of the internet that cannot be accessed by traditional browsers, but requires anonymous proxy networks or infrastructure for access. Tor is the most common.
deep web: Online content that is not indexed by search engines, such as authentication required protected and paste sites and can be best described as any content with a surface web site that requires authentication.
high-risk surface web: consists of areas of the surface web (or “regular” internet) that have a high degree of overlap with the darknet community. This includes some chan-type imageboards, paste sites, and other select forums.
For a full list of darknet terms, check out our Glossary.
DarkOwl has observed similar specific targeting frequently in the darknet. The same would be true for the intention of an attack against a corporation or government organization, but this is understandably much harder to quantify.
The U.S. Department of Homeland Security (DHS) defines risk as the “potential for an unwanted outcome resulting from an incident, event, or occurrence, as determined by its likelihood and the associated consequences” such that: likelihood is defined as “the chance of something happening, whether defined, measured or estimated objectively or subjectively, or in terms of general descriptors (such as rare, unlikely, likely, almost certain), frequencies, or probabilities” and consequence is given as “the effect of an event, incident, or occurrence, including human consequence, economic consequence, mission consequence, psychological consequence.”
The DHS risk assessment model is more simply defined as a function of three variables: threat, vulnerability, and consequences with full recognition. In organizational risk calculations, threat includes anything that can cause harm to the organization and that could expand to include threats from natural disaster (wildfire, hurricanes, and earthquakes) or even a significant hardware / backup failure that triggers a disruption in services or production and not necessarily exclusive to cybersecurity attacks by external malicious entities.

There are numerous interpretations, philosophies, and variations on this formula and luckily organizations are given extreme flexibility in conducting internal risk assessments by applying risk models of varying degrees of detail and complexity of threat identification and vulnerabilities – of which cybersecurity has become increasingly critical.
Threat calculations are often tied to scenarios with likelihoods of occurrence that involve an adversary’s intent, capability, and targeting. When we look at the darknet’s role in risk and threat vectors, especially when considering the risk to a company’s brand or stakeholders, malicious threat actors who conduct operations in the underground (e.g. cybercriminal organizations, nation state actors and proxies, and cyber opportunists) proactively hunt for and attempt to exploit sensitive data for personal financial gain by whatever means possible, often manipulating unpatched vulnerabilities and crafting new exploits in the wild.
DarkOwl analysts also regularly witness critical corporate and personal information actively shared across various underground digital communities in the darknet and deep web and have categorized the types of vulnerable data at risk accordingly, delineating corporate and individual personal risk, with careful consideration that these two are intricately interrelated due to the fact humans are one of many risks corporate organizations must consider when calculating their cybersecurity risk. The region where corporate and individual risk overlap is of most critical consideration as well as the extent and volume of readily available information for threat actors to launch their attacks.
Likewise, the more accumulated data a threat actor has access to for an individual or a corporation increases the risk accordingly.
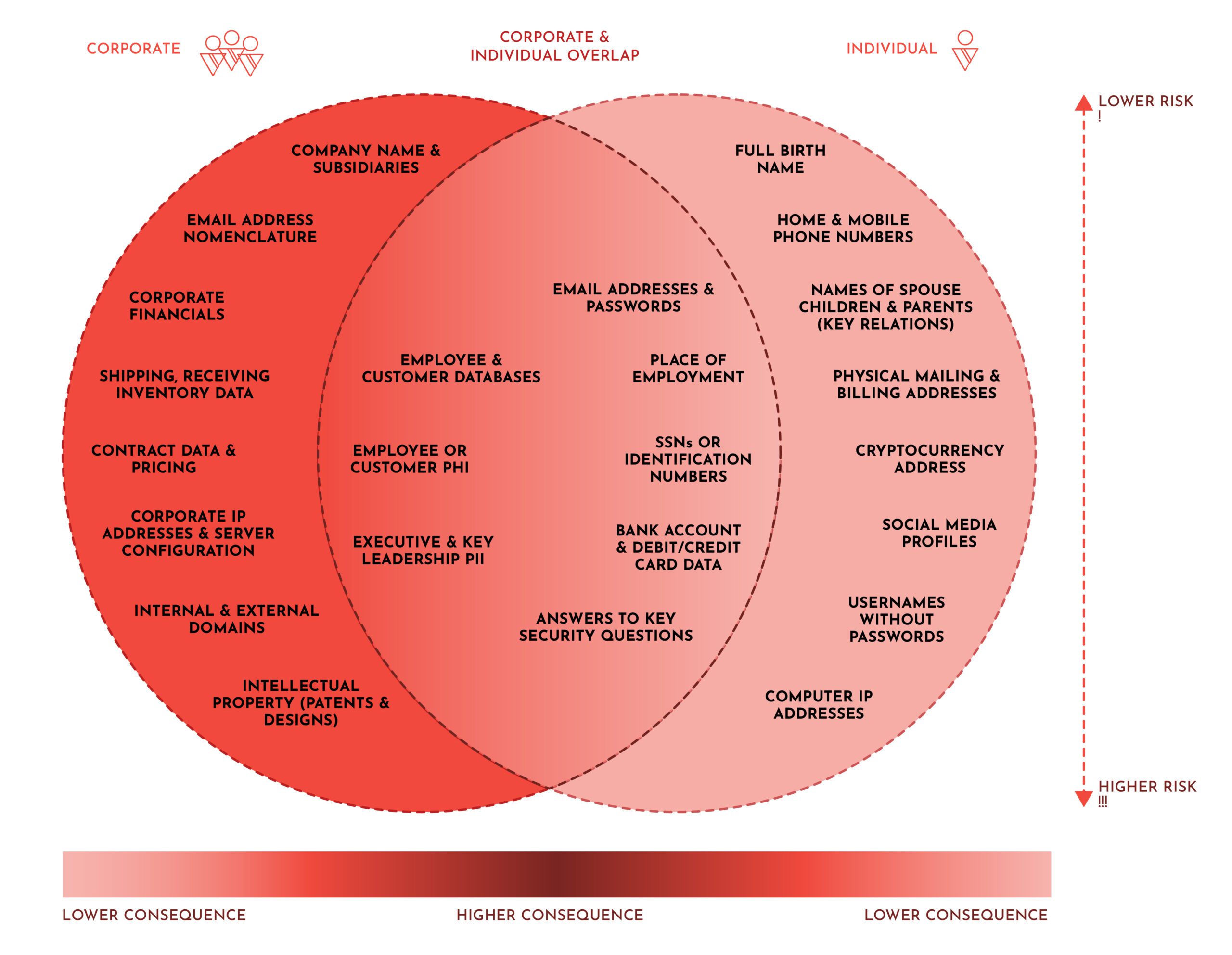
Figure 1: Visualizing the Threat to Corporations and Individuals
Corporate Risk and The Darknet
The possibility of a cybersecurity attack against a corporation feeds a number of different corporate risk calculations: the loss of customer data presents a significant risk to a company’s brand, reputation and stakeholders; there’s moderate risk for loss of sales due to counterfeit goods offered on the darknet and direct reputational attacks on discussion forums and social media; there is direct risk via the executives and key leadership of an organization for business e-mail compromise (BEC) phishing attacks or financial extortion through physical threat to executive’s family; and, there is risk to attack via third (and fourth) party vendors and suppliers.
The consequences of an attack against a corporation can include:
- Unauthorized access to a corporate network
- Misuse of information by an authorized user
- Loss of access to corporate data (via deletion or encryption)
- Disruption of service or productivity
- Reputational loss and damage to brand or corporate image
The Risk of Unintentional Data Compromise
While large commercial data leaks receive press coverage, with phrases like “millions of records of user data exposed” there is an unknown number of organizations that have likely secretly dealt with a critical cybersecurity incident without ever disclosing the breach to their customers or users due to the consequences of reduced consumer confidence.
Extortion-as-a-service is an increasingly successful sector of the underground criminal ecosystem and involves stealing sensitive personal or corporate information and then leveraging unauthorized access to this information to force the victim to pay, essentially blackmailing the victim, in exchange for quasi protection of their data. Threat actors utilize hacking forums and discussion boards across the deep web and darknet to explore potential vulnerabilities, sometimes expressing interest in specific industries, companies, and individuals, then finally sharing or selling the sensitive information they have stolen – resulting in significant reputational and/or financial loss for the victim organization.
Counterfeiting Risk is Brand Risk
The darknet is home to a lesser-known segment of corporate brand risk with offers of counterfeit goods on darknet markets. The sale of counterfeit physical goods is a persistent and viable market in the underground economy. DarkOwl’s SaaS product suite can be utilized to protect corporate brand reputation and value through automated monitoring and alerting for various forms of brand mentions. In this blog, we discuss this extensively.
Executives and Key Leaderships are Critical Targets
Some criminals utilize traditional open-source intelligence (OSINT) techniques to uncover the names, e-mail addresses and family relationships of an organization’s executives and key leadership to conduct pointed phishing campaigns via e-mail, SMS or traditional in-person and telephone-based social engineering to gain malicious access to a corporate victim’s network.
Vendors and Other Third Parties Increase Risk
Nation-state actors and cybercriminals are increasingly sophisticated and opportunistic seeking to exploit third and fourth party suppliers and vendors to cause harm against the victim organization. Third parties include any unit an organization works with including but not limited to vendors, such as suppliers and manufacturers, partners, affiliates, distributors, resellers, and agents. Third parties may have access to information such as: corporate sensitive data, financial data, contract terms and pricing, strategic planning data, intellectual property, credential data, personally identifiable information (PII) of customers and employees and protected health information (PHI) and can unknowingly contribute to a threat actor gaining unauthorized access to a corporate network.
While it is not always overtly clear who or what organization a threat actor may be intending as their next target, monitoring the darknet and deep web for mentions of a company’s name, along with names of its executives and key leadership, and network information such as domains, e-mail and IP addresses can be a helpful marker for quantifying the potential threat or intent of harm against an organization. DarkOwl’s Score API are one of many potential quantifiable metrics a corporation can use to measure and understand a company’s business risk. Scores can also be utilized for self-risk assessments, as well as brand monitoring and vendor risk management.
Individual Risk and the Darknet
DarkOwl has observed several criminals specialize in trade of other critical PII such as national identification numbers, mailing and billing addresses, dates of birth, social media profiles, and even more concerning financial data like bank account numbers and credit and debit card numbers along with their card verification values (CVVs), expiration dates and security personal pin codes.
Individuals are at Risk of Social Engineering
Personal individual risk increases with the extent of the information exposed, where and how it has been distributed. Cybercriminals are increasingly creative in their techniques to gain access to this illicit information with astute social engineering and mass phishing campaigns. Criminals actively seek to obtain an individual’s sensitive personal information necessary for a financial institution’s security verification process such as one’s mother’s maiden name, historical personal residence and billing addresses and answers to key security questions, sometimes obtained through links to phishing website or “fake” copies of popular commercial websites with username and password login form fields, sent through “SMS bomb” or spam e-mail phishing attacks. A popular technique — both discussed openly with methods traded in underground forums — is sending out fake mobile phone notifications. Spammers text delivery notices via SMS with a link to a phishing URL (often a shortened URL, e.g. “bit.ly”) for companies like DHL or UPS that are designed to harvest the victim’s mobile IP address, IMEI number, mobile phone model and software version along with sensitive personal information input by the victim in search for the non-existent package.
The Risk of Password Reuse and Credential Stuffing
Credential stuffing is a widespread technique utilized by cybercriminals to test if historically exposed e-mail addresses and password combinations are valid logins across multiple commercial websites. Opportunistic cyber criminals automate the testing of large ‘combo lists’ containing compromised e-mail addresses and passwords against commercial websites and once a successful authentication occurs readily steals the PII and financial information, often saved, on the e-commerce shopping platform’s user profile.
Circling back to the overlap between individual and corporate risk, credential stuffing using malicious software and botnets affects not only the individuals but also the commercial organizations whose user accounts are surreptitiously accessed, as many immediately assume access was achieved due to vulnerabilities with the commercial service provider’s technical configuration instead of a simple credential stuffing technique conducted en masse. The uncertainty potentially erodes consumer and stakeholder confidence warranting that commercial agencies consider credential stuffing in their internal security frameworks and corporate risk assessments as well.
The Risk of Identity Theft and Financial Fraud
While a personal e-mail address or password leak is easily mitigated by using complex passwords and password managers, the greatest threat to an individual is financial fraud and/or personal identity theft. When credit card numbers are leaked in association with this type of account information, it can easily be leveraged to create new illicit accounts or to commit bank fraud. This risk his heightened even further when associated billing formation is included, such as a mailing address or the credit card’s CVV number.
Individual Risk Calculations
Ultimately, what does the fact any of your personally identifiable information is on the darknet really mean? Your level of concern is directly correlated to your individual risk and calculating individual risk using information exposed on the darknet is measured by not only the location of and volume of credentials and PII exposed, but also a factor of time – that is, how long the information has been available and the likelihood of exploitation by a malicious actor. Of course, this likelihood of occurrence increases immediately once there is direct intent and targeting of the person either individually or in conjunction with a campaign against a corporation, regardless of what types or volume of personal data is already accessible.
- E-mail address and password leaks: Individual risk increases slightly with the website where the credentials have been used, i.e. banking application or health portal. Individuals can mitigate risk by using unique, complex passwords and password managers.
- Personal financial data like credit and debit cards: Individual risk is higher if the card is still in use. Most banks have fraud prevention and do not hold the cardholder responsible for illegal purchases with stolen credit and debit card data.
- Identity verification information: Individual risk increases with the more sensitive data accessible to a threat actor. For example, if a bank account number along with the full name of the account holder, their physical residential addresses, and other key identity verification information such as their mother’s maiden name, the name of their first dog, and secondary school mascot is obtained, then a threat actor has enough information to impersonate them and take control of the account. Compromise can be mitigated by visiting the bank in person with a form of identification (passport or driver’s license), closing down the compromised account, and opening a new one.
Only an individual can ascertain the degree of personal cybersecurity risk they are comfortable with, given the types of information they have shared publicly and the value they place on their personal information, their individual brand, and digital reputation. In a hyper-connected society that is increasingly reliant on networked digital information systems to function, everyone’s exposure and subsequent risk is increasing to some extent. For some individuals, this risk is gradual and others exponential.
It’s Risky Business Regardless
Threats posed to individuals and corporations from the darknet where sensitive corporate or personal information is leaked by cybercriminals is diverse. Criminals employ increasingly sophisticated social engineering and technical attack vectors to pilfer information that could lead to full identity theft for an individual or corporate extortion with multi-billion ransom demands.
While the science of cyber risk calculations is still relatively nascent, the factors and data points outlined above can offer those in charge of assessing and underwriting risk contextual information as it pertains to the deep and dark web. By better understanding how threats manifest in these underground communities, individuals and corporations will be able to more accurately identify indicators of compromise and assess the security posture of their digital footprint. The deep web, anonymous networks, and various chat platforms will continue to be home for trading these commodities of data and DarkOwl will continue to assist its clients and partners to help provide the most comprehensive darknet database necessary for critical monitoring of potential markers of cybersecurity risk to corporations and individuals.
Download this report as a PDF
To understand the role darknet data plays in your corporation’s risk posture, contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















