What are IoAs?
November 13, 2025
Cybersecurity might as well have its own language. There are so many acronyms, terms, sayings that cybersecurity professionals and threat actors both use that unless you are deeply knowledgeable, have experience in the security field or have a keen interest, one may not know. Understanding what these acronyms and terms mean is the first step to developing a thorough understanding of cybersecurity and in turn better protecting yourself, clients, and employees.
In this blog series, we aim to explain and simplify some of the most commonly used terms. Previously, we have covered bullet proof hosting, CVEs, APIs, brute force attacks, zero-day exploits, doxing, and data harvesting, indicators of compromise. In this edition, we dive into indicators of attack.
Indicators of Attack (IoAs) 101
An Indicator of Attack (IoA) is a behavioral pattern or activity that reveals a cyberattack is in progress or about to occur. IoAs focus on detecting an attacker’s intent and methods in real time, enabling organizations to identify and stop malicious actions before they cause major harm.
Rather than relying on evidence of past breaches, IoAs highlight the attacker’s tactics, techniques, and procedures (TTPs) as they unfold, providing early warning of active or emerging threats.
IoA vs IoC
It’s important to distinguish IoAs from indicators of compromise (IoCs). IoAs focus on the behaviors and tactics that suggest an attack is currently in progress or about to occur, while indicators of compromise tell you that a compromise has already happened. Both are crucial for a comprehensive cybersecurity strategy.
DarkOwl and IoAs
Examples of IoAs in the Darknet that DarkOwl Monitors
- Malware and exploit kits: Advertisements for or discussion of high-quality malware designed to evade detection or exploits that can be used in an attack.
- Tools for malicious activity: Evidence of groups using specific tools to disable security software, like an EDR (endpoint detection and response) killer, to facilitate an attack.
- TTPs: Discussion and sharing of attack techniques on darknet forums, which indicates active development and use of new methods.
How DarkOwl Helps Identify IoAs
- Entity API: This tool helps identify and contextualize entities like IP addresses and domains within the collected darknet data, which is crucial for correlating indicators and assessing threats in real-time. With Entity API, users can quickly and efficiently identify, monitor, and target particular threats in the darknet that are relevant to their particular needs and use-cases.
- Vision platform: This platform collects and indexes vast amounts of darknet data, allowing for the identification of potential attacks in progress by searching for relevant keywords and patterns. Vision UI is the industry leading platform for analysts to simply, safely, and comprehensively search darknet data.
- Threat intelligence: By monitoring forums, marketplaces, and other sources, DarkOwl can identify the latest threats and attack methods being discussed and sold on the darknet. With 227,500 pages of darknet content scraped and indexed every hour, DarkOwl’s collection database is continuously expanding.
DarkOwl helps detect both through its darknet intelligence by identifying attacker tactics, techniques, and procedures (TTPs). Examples include advertisements for malware or exploit kits, discussions of attacks on darknet forums, or the use of tools, all of which indicate a potential or ongoing attack.
Product Highlight: Actor Explore

In today’s digitally driven world, the landscape of cyber threats is ever-evolving and increasingly sophisticated. As businesses and individuals become more dependent on technology, the need to protect sensitive data and critical infrastructure from cyber attacks has never been more critical.
One effective approach to enhancing cybersecurity is to track and monitor cyber threat actors. The actors that are responsible for conducting attacks; individuals or groups with malicious intent, often targeting organizations, governments, or individuals. Understanding why they are operating, what they hope to achieve and what methodologies they are using can assist analysts in protecting infrastructure and predicting future activities. Identifying and monitoring the tactics, techniques, and procedures (TTPs) of cyber threat actors, is also an important step to gain insights into actor’s strategies. This information can be invaluable in understanding how attacks are executed and identifying potential vulnerabilities in an organization’s defense.
With DarkOwl’s Actor Explore users can review analyst curated insights into active threat actor groups on the darknet and wider. We explore the motivations behind the groups, the tools they have used and searchable attributes to pivot on within DarkOwl Vision. Tracking available information about threat actors such as their motivations, TTPs, victims and activities can provide valuable intelligence which allows analysts to predict behavior and take proactive steps to protect their organizations.
Product Highlight: DarkSonar API
With cyberattacks increasingly on the rise, organizations need better intelligence to safeguard themselves, employees and customers from incidents such as data breaches and ransomware attacks. This rise in illicit cyber activity only increases the need to protect against and determine the likelihood of these attacks. The darknet contains data critical to understanding criminal behavior and security risk, and companies need an understanding of their exposure on the darknet to determine risk and take mitigating actions.
DarkSonar, a relative risk rating based on darknet intelligence, measures an organization’s credential exposure on the darknet. DarkSonar enables companies to model risk, understand their weaknesses and anticipate potential cyber incidents. In turn, organizations are able to take mitigating actions to protect themselves from loss of data, profits, and brand reputation.
DarkSonar in the Wild
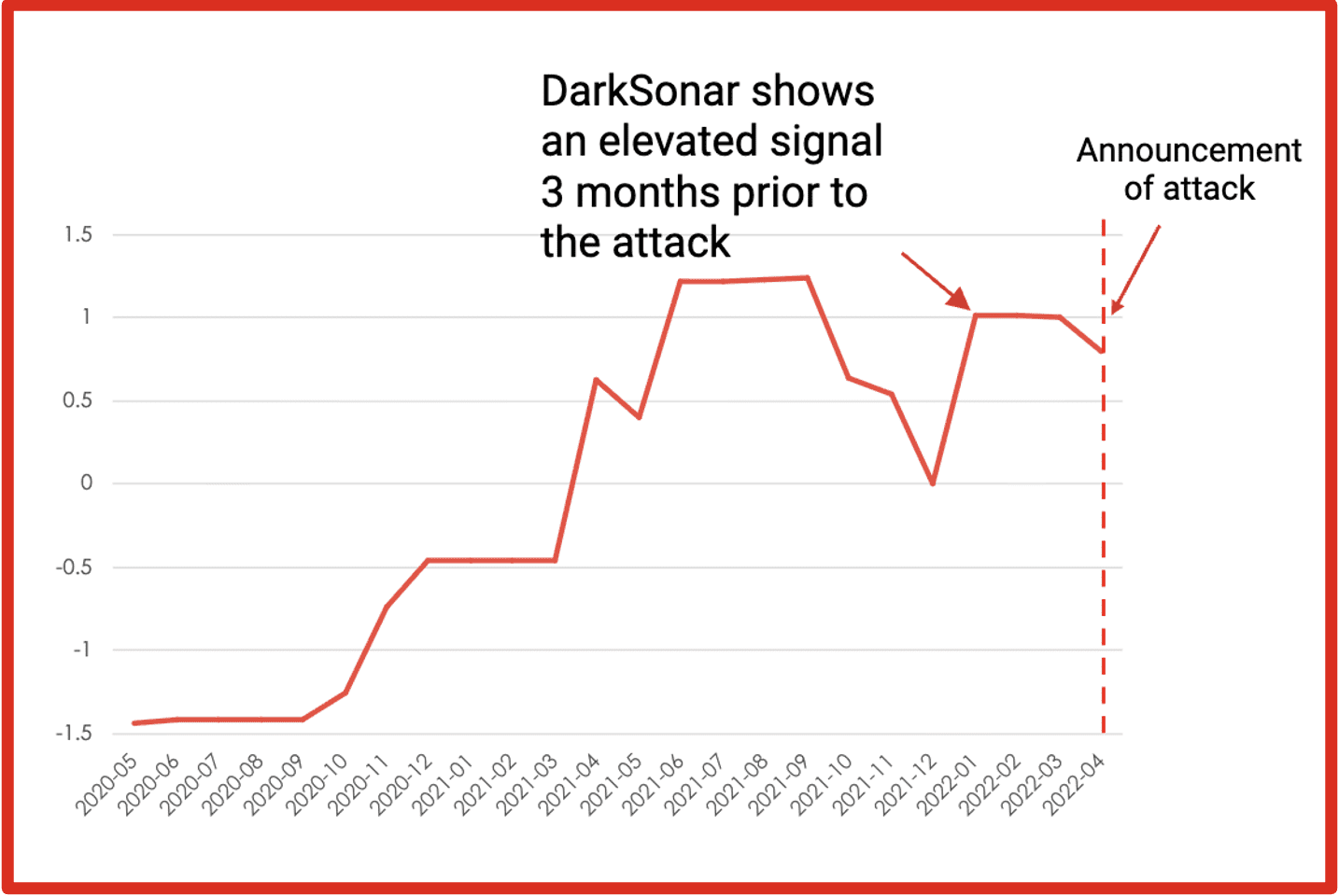
General Motors
In April 2022, General Motors disclosed that it suffered a credential stuffing attack. The attackers accessed customers’ personally identifiable information (PII)and redeemed reward points for gift cards.
Takeaway: DarkSonar’s email exposure signal detected an abnormal increase in plaintext and hashed credentials in the months leading up to the attack.
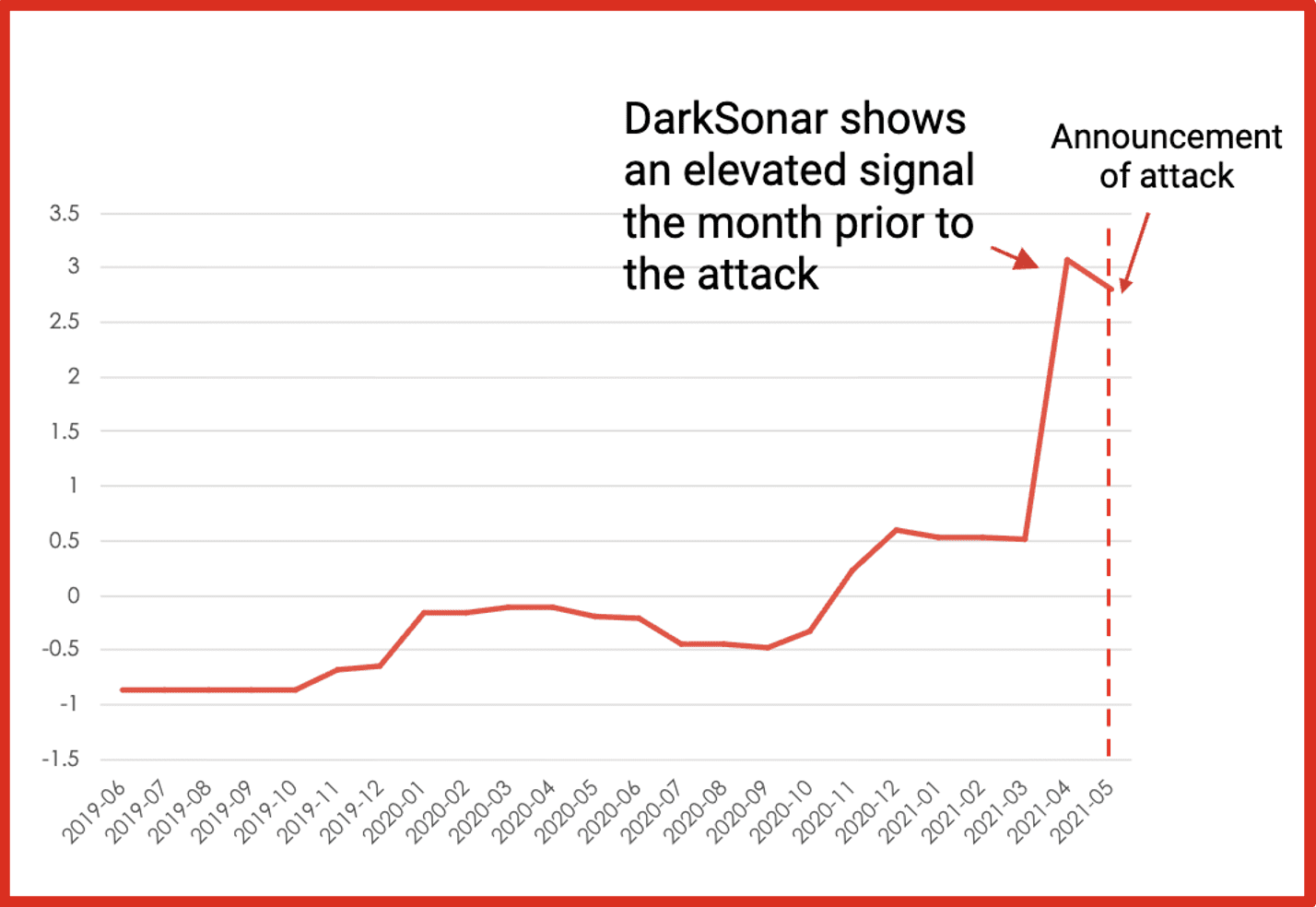
Colonial Pipeline
In late April 2021, hackers gained entry into the networks of Colonial Pipeline Co. The hack took down the largest fuel pipeline in the U.S. and led to shortages across the East Coast was the result of a single compromised password, according to a cybersecurity consultant who responded to the attack. The virtual private network account was no longer in use at the time of the attack but could still be used to access Colonial’s network, he said.
Takeaway: DarkSonar detects plain text credentials available on the darknet.
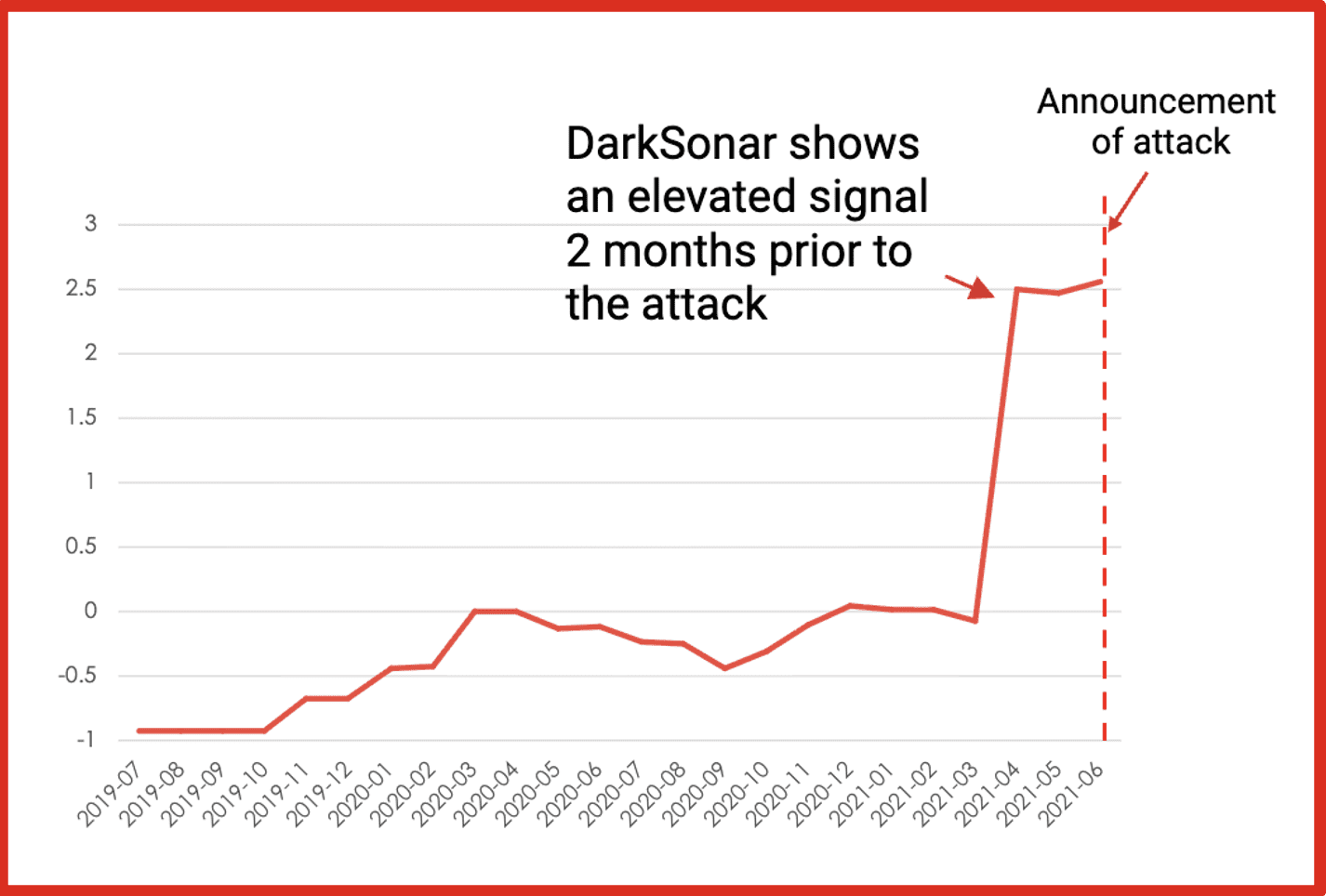
FujiFilm
In early June 2021, Fujifilm’s company servers were infected by Ransomware. While they have never released the specific details, it is believed to be the Qbot Ransomware. Qbot is typically initiated by phishing.
Takeaway: DarkSonar detected an increase in email exposure which can be used as part of a phishing attack.
Contact us to learn more.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















