Coronavirus on the darknet Pt 2: The scams keep on coming
This is a continuation of our previous discussion (linked below) about how the global pandemic has created an incredible surge in COVID-19 related scams on the dark web. DarkOwl analysts have been tracking the developments in DarkOwl Vision and have consolidated a round-up of some interesting, concerning, and, in some cases, comfortingly human findings.
See Part 1 of our COVID scam coverage here
A COVID-19 Vaccine
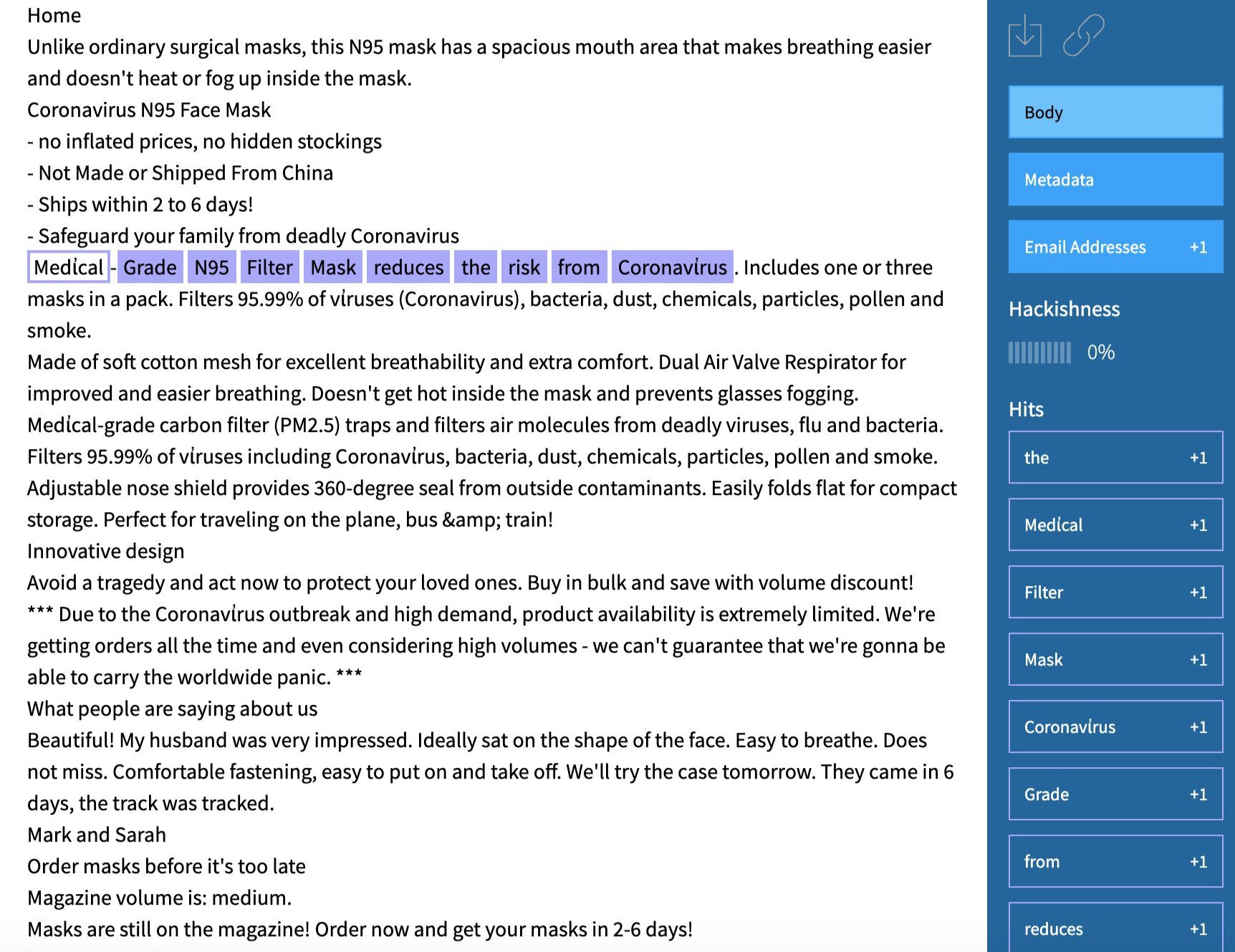
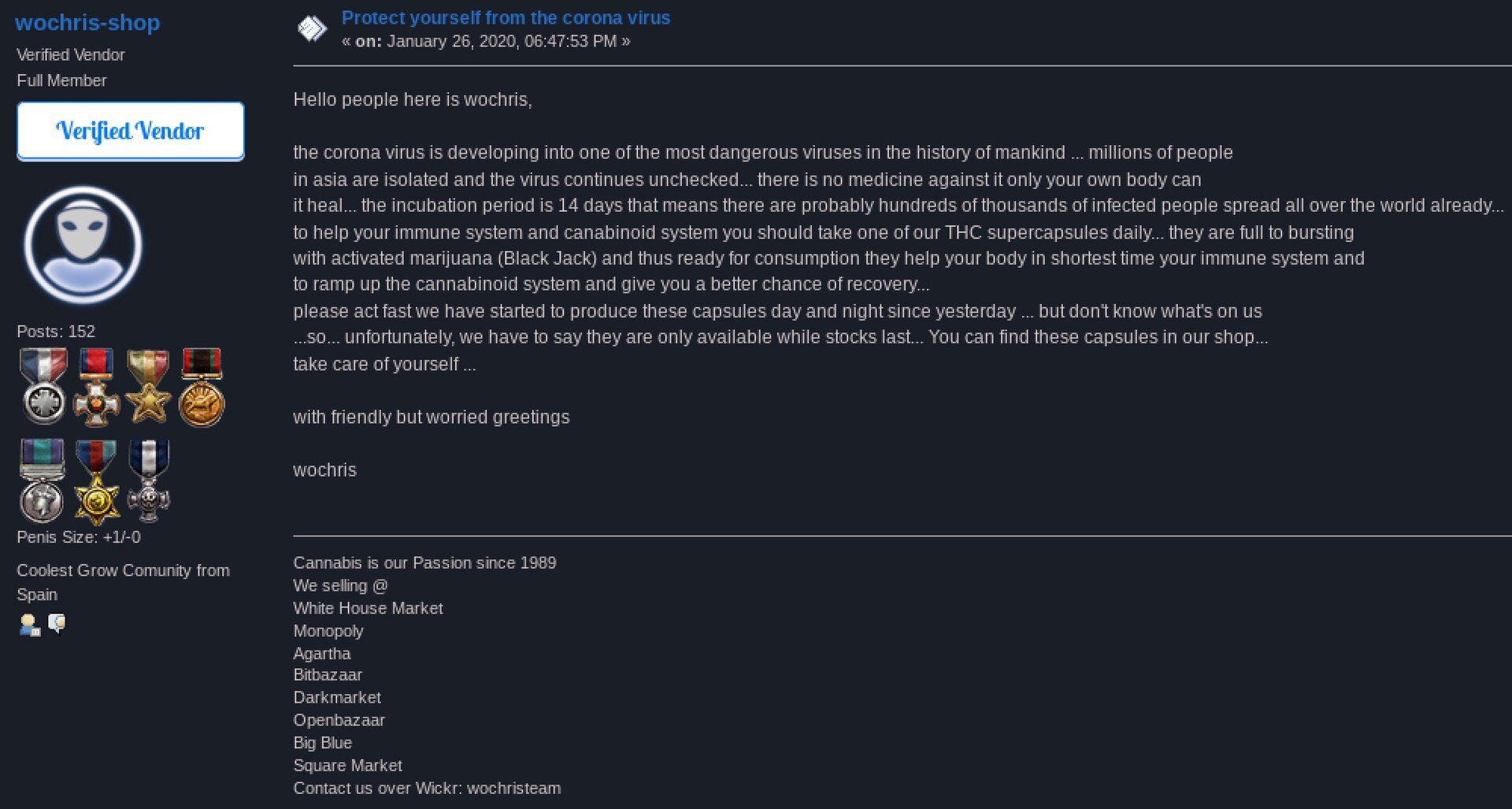
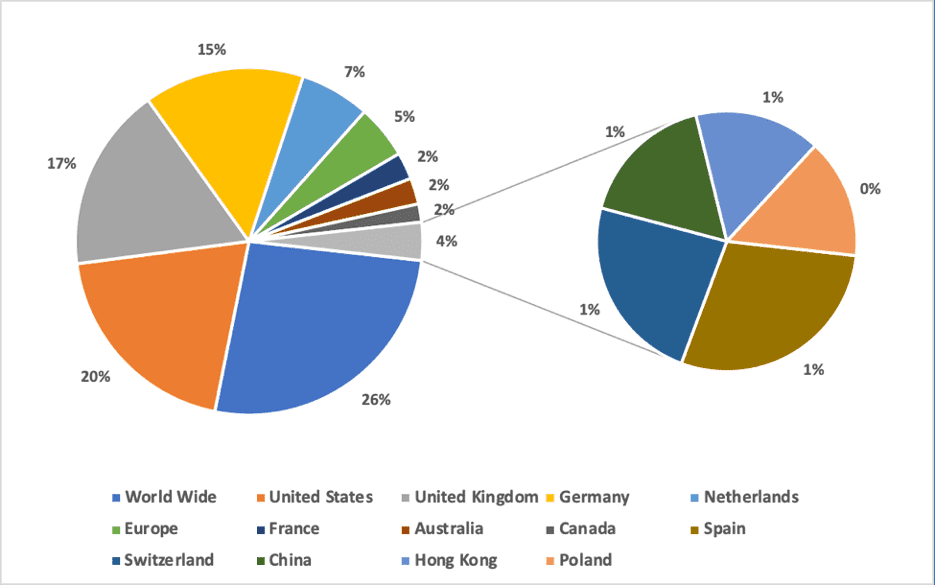
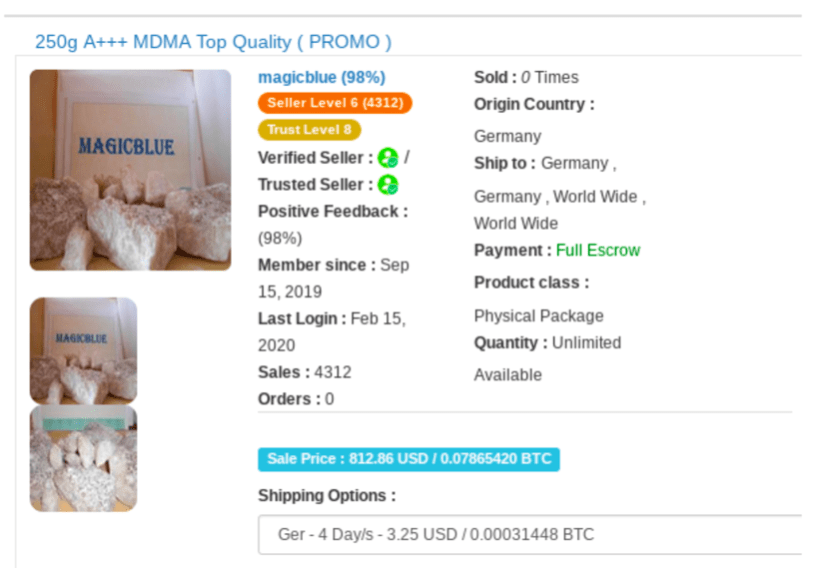
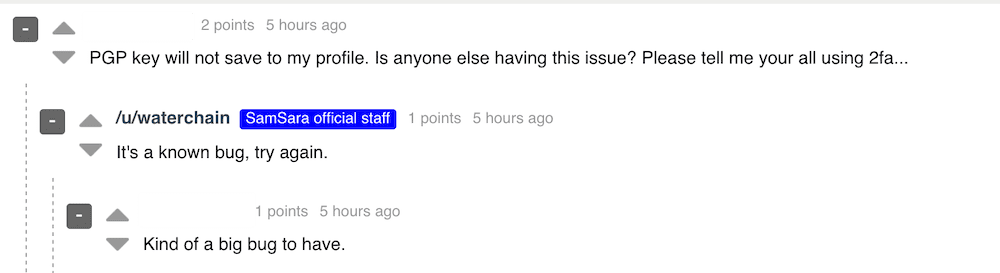
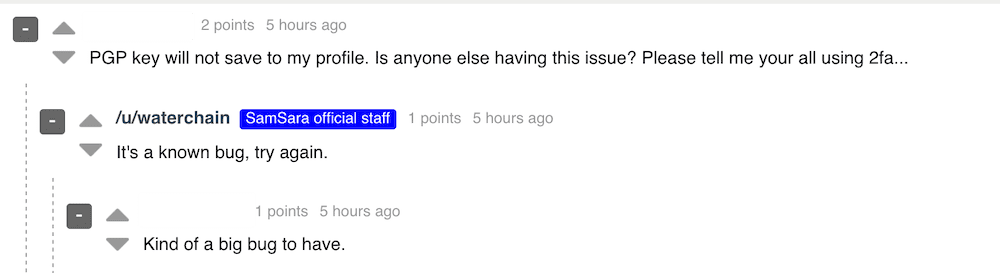
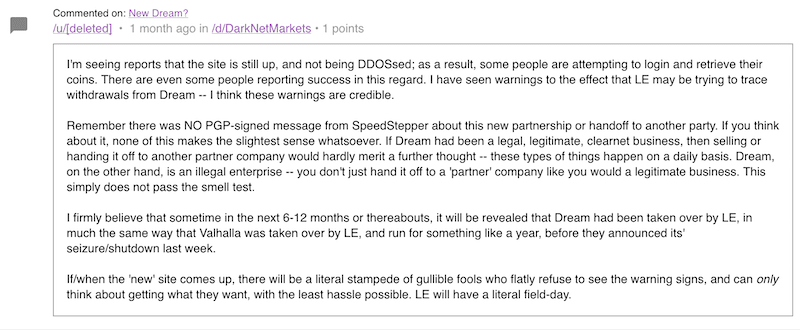
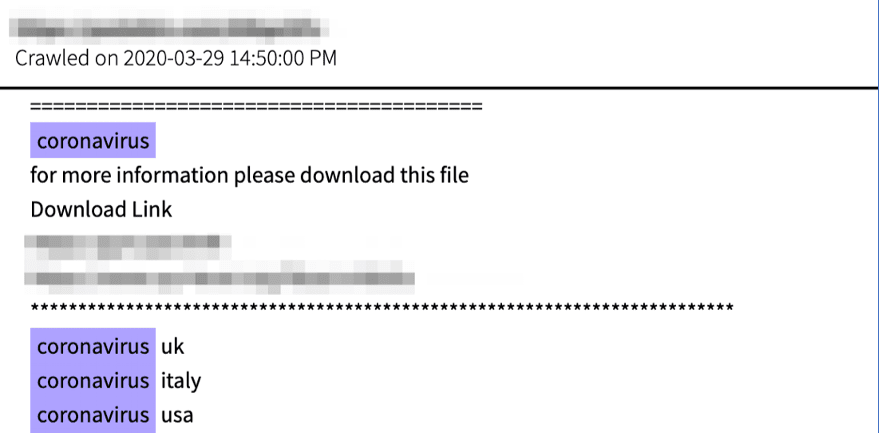
The most recent pandemic related scam to surface on the dark web is a hidden service dedicated to the COVID-19 vaccine. According to a new Tor hidden service, appearing on the dark web the week of the 18th of March, Technology Minister Ofir Akunis confirmed Israeli scientists had developed the first vaccine for the novel coronavirus that was available to ship Worldwide via DHL. 1 packet supposedly includes 10 20ml vials of the COVID-19 vaccine for only $10 USD, payable by Bitcoin.
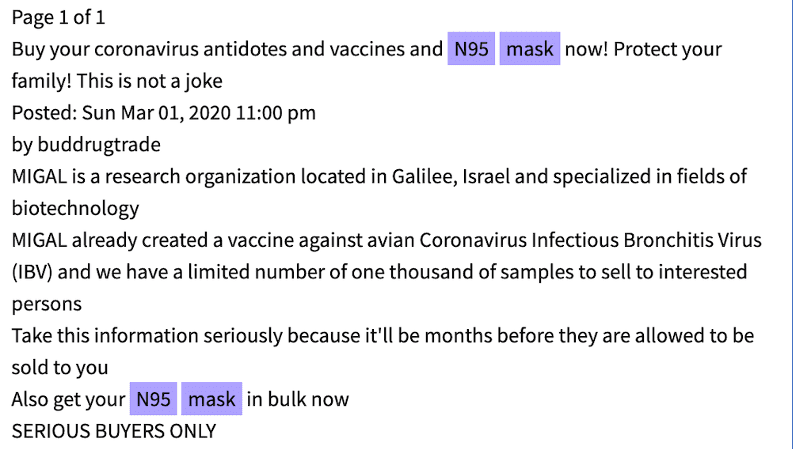
Original Source: http://d5jzfmy5d3oqlia4pnfu37pztv2n3eknxdoi57ycwywb2klkt42b43ad[.]onionOriginal Source: http://d5jzfmy5d3oqlia4pnfu37pztv2n3eknxdoi57ycwywb2klkt42b43ad[.]onionThis is not the first “Israeli” based antidote offered on the dark web. DarkOwl Vision captured an advertisement posted by darknet user, buddrugtrade, back on March 1, 2020. The post suggesting that MIGAL, a research institute in Galilee, Israel, had created the vaccine against a strain of the coronavirus that they had available to sell. They also included N95 Masks on the same classified.
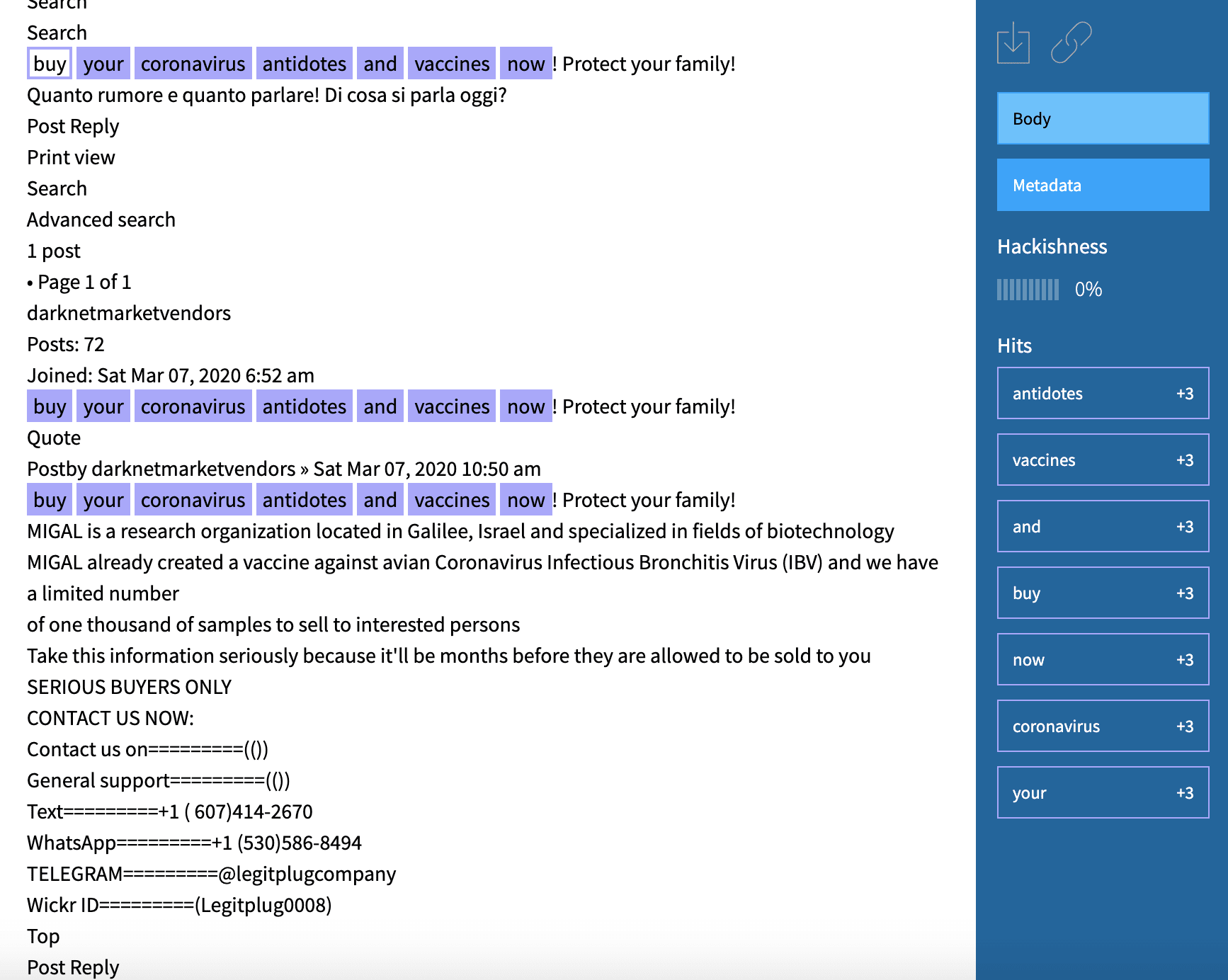
Source DarkOwl Vision MD5: d08ea9018d6fe955ed66502e82bc42f2A similar offer for the vaccine appeared as recently as the end of March with a scammer offering vials of the vaccine for $115 USD. The advertisement suggests the owner only has 5 vials available to sell with hopefully more in the future.
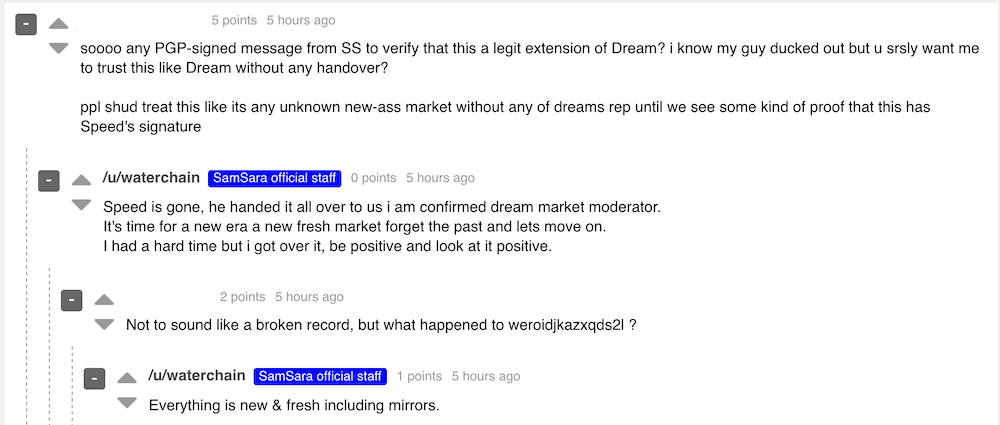
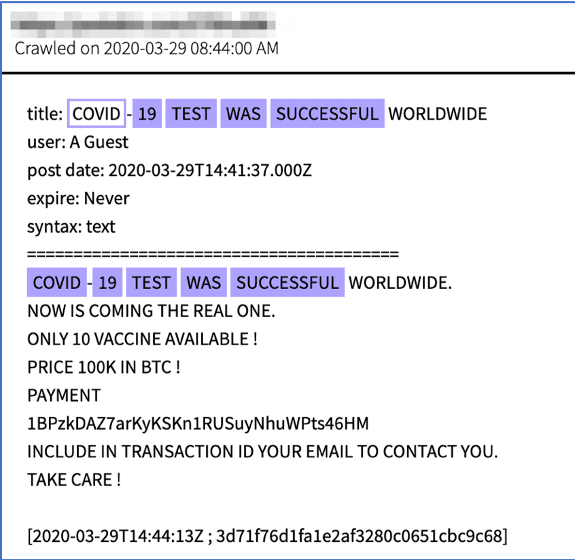
Original Source: http://dccvdpx2tksoyue5p5cpzqwhwyv4njkfaa3p7km7eyh6kke2atwfoiqd[.]onionSource DarkOwl Vision MD5: 3d71f76d1fa1e2af3280c0651cbc9c68Another scammer has a higher price in mind for the vaccine. On 29 March 2020, multiple pastes, titled, “COVID-19 TEST WAS SUCCESSFUL,” were observed around the dark web consisting of an offer for 10 vaccines for $100K in BTC. “Now is coming the real one” the offers reads, as if to suggest the previous offers were not effective or legitimate.
Multiple Offers for COVID-19 Blood Samples
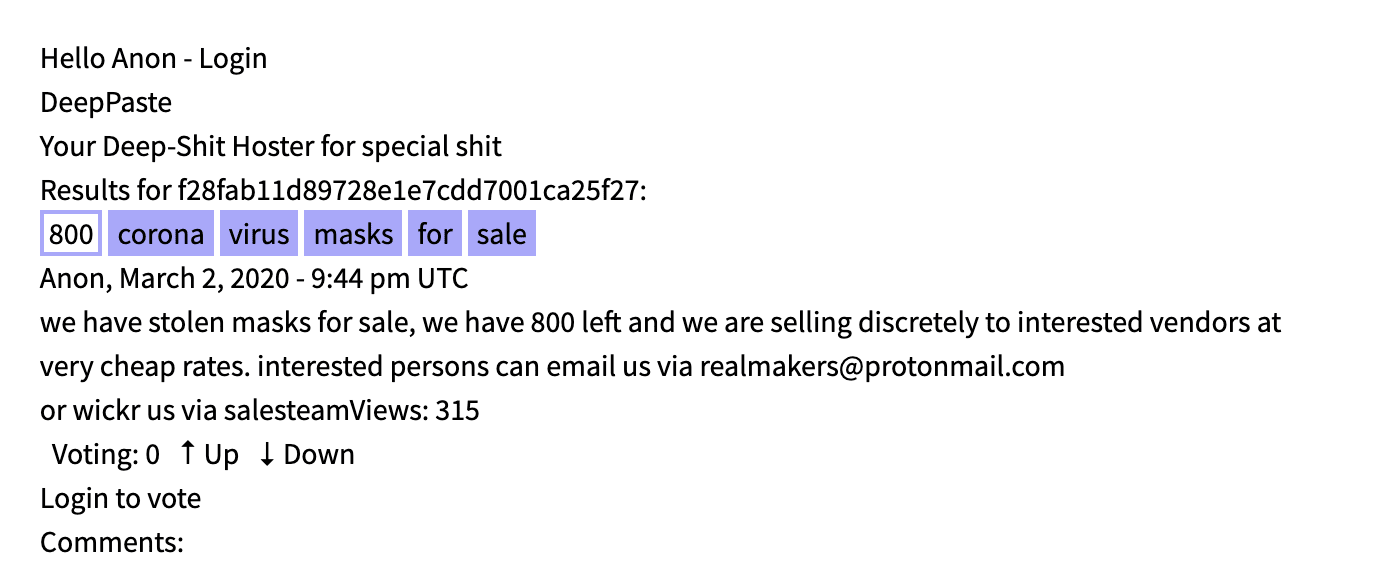
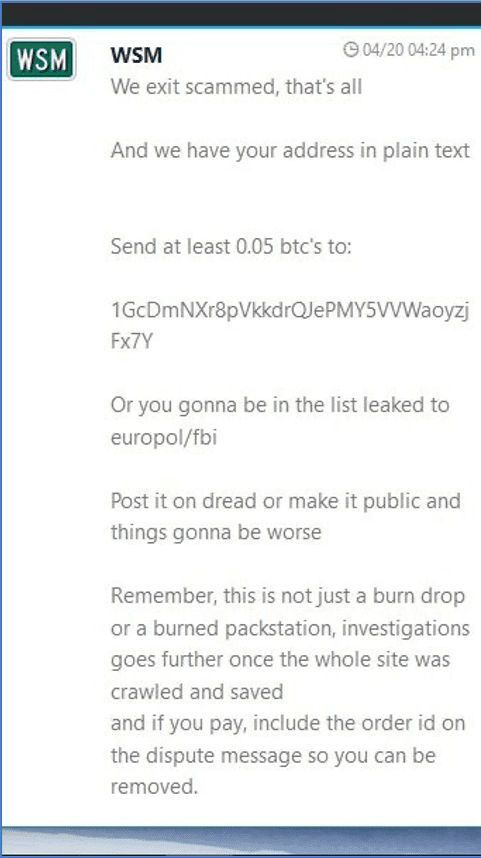
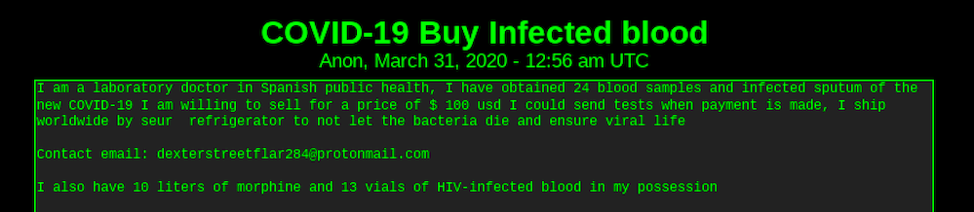
DarkOwl continues to witness numerous scammers offering samples of the virus via blood samples and saliva. The most recent scammer’s listing, at 12:56 UTC, 31 March 2020, attempted to imbue legitimacy into their listing, stating that they were a “laboratory doctor in Spanish public health” who successfully obtained “24 blood samples and infected sputum of the new COVID-19.” This scammer offered 24 samples for $100 USD (less than $5 per sample) and concluded their classified with even more additional bioterrorism-related material: “I also have 10 liters of morphine and 13 vials of HIV-infected blood in my possession.”
Original Source: http://depastedihrn3jtw.onion/show.php?md5=0a4f6c42ec79ea79f8f0984f8e6fafcfAnother advertisement, posted 10 days earlier, stated the seller’s father was infected with COVID-19 and while at the hospital he managed to collect one syringe filled with blood that he inserted into 10 bats. The offering price is only $32 USD for the sample; a minimal payment is required to answer any questions.
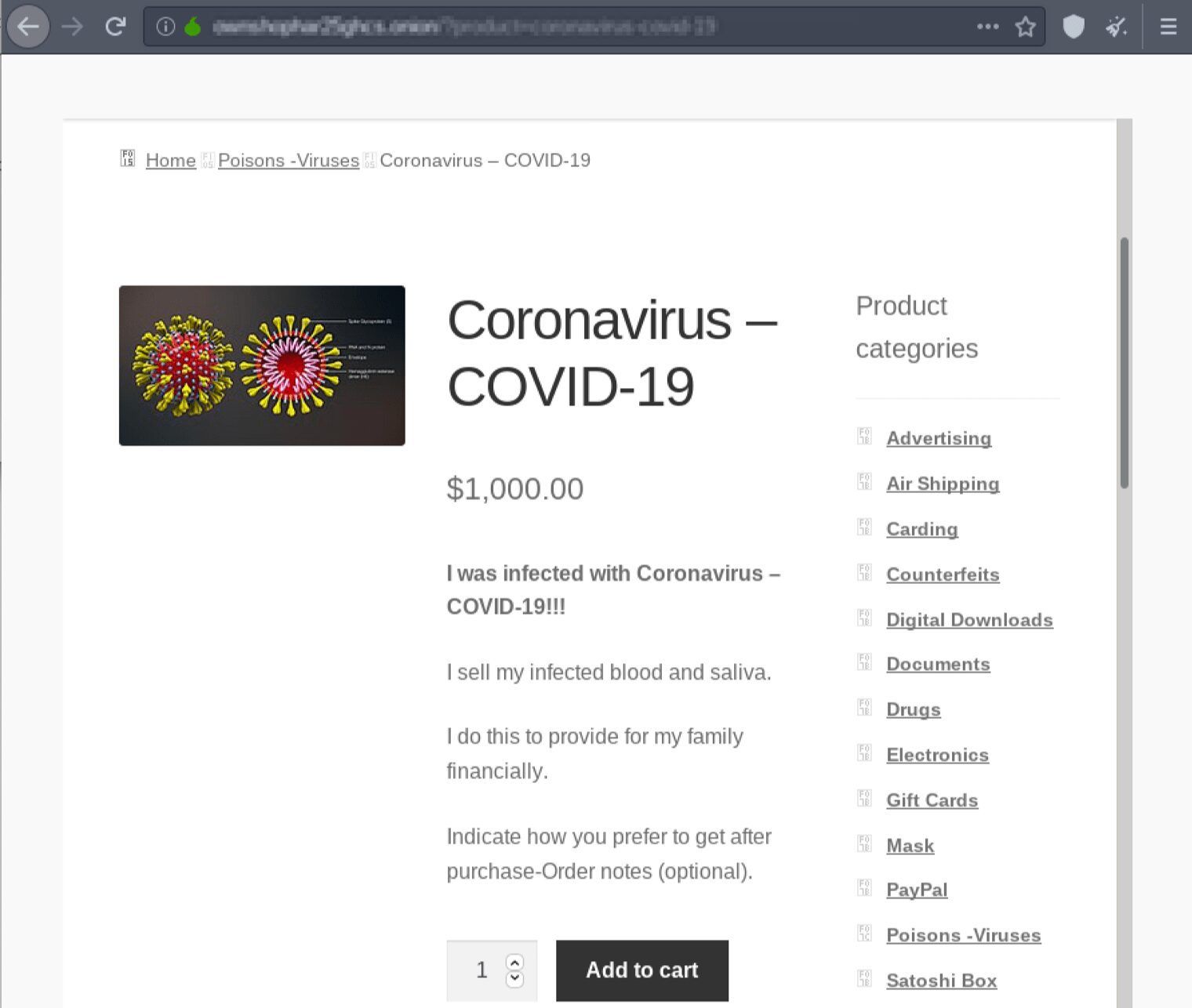
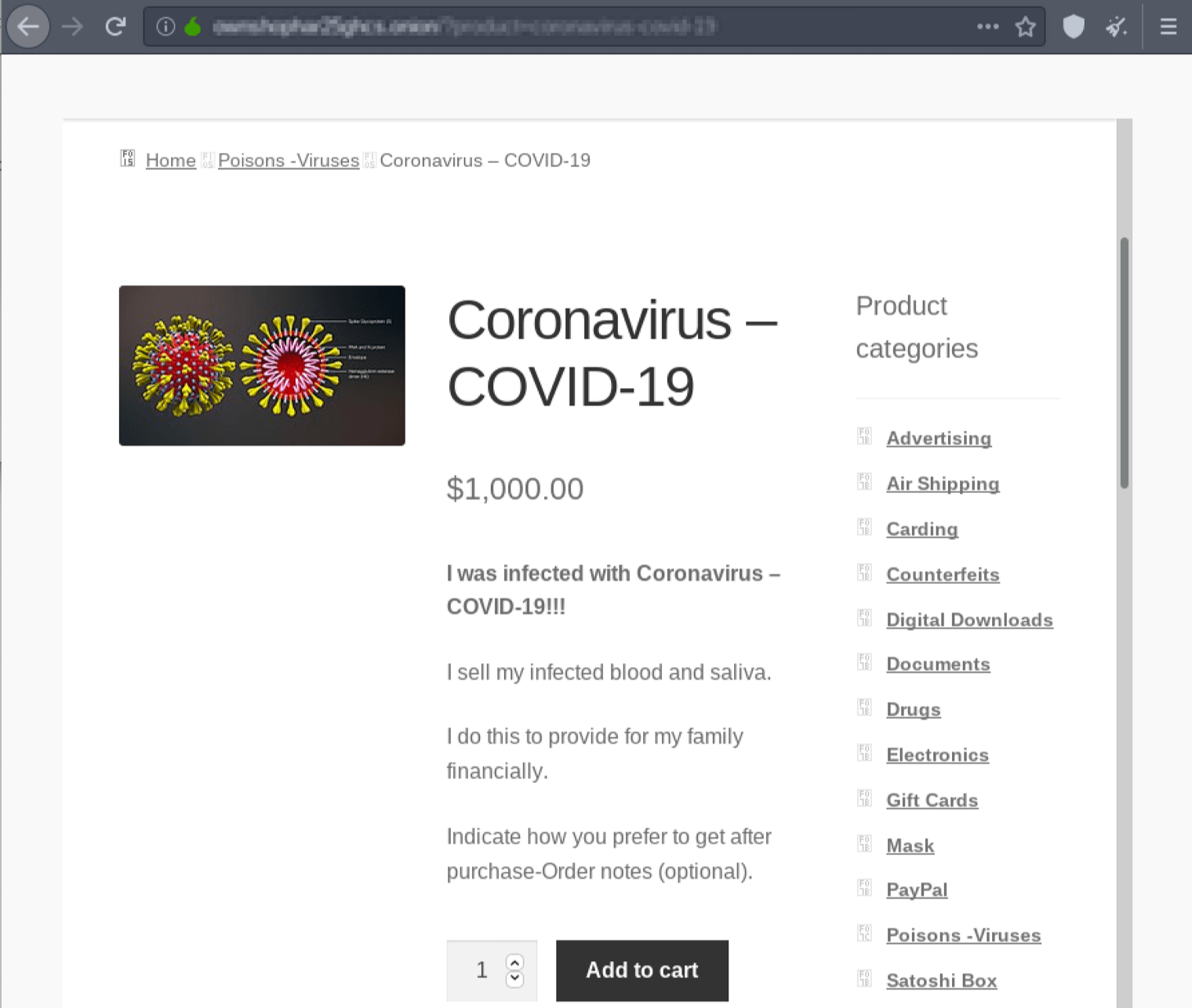
This price is considerably cheaper than the $1,000 USD offer for a blood sample and saliva observed on a darknet market in early March, but not as ominous or anarchy-inducing as an offer for the live virus by one known as drdeath41, “Great for the coworker you don’t like. Or spread it in the ghetto if you’re like that or maybe let it loose at the country club.” – Source DarkOwl Vision M5D: d87605d2f17f877991b35f8307de89a7
Original Source: http://depastedihrn3jtw.onion/show.php?md5=3e901ee29814c57c1950a0db6ca829e7Offers for Test Kits and Thermometers
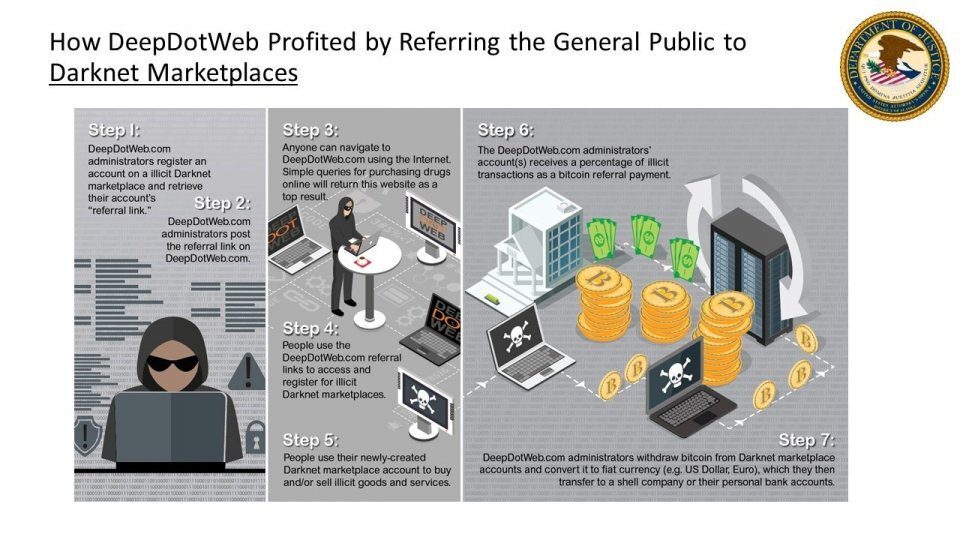
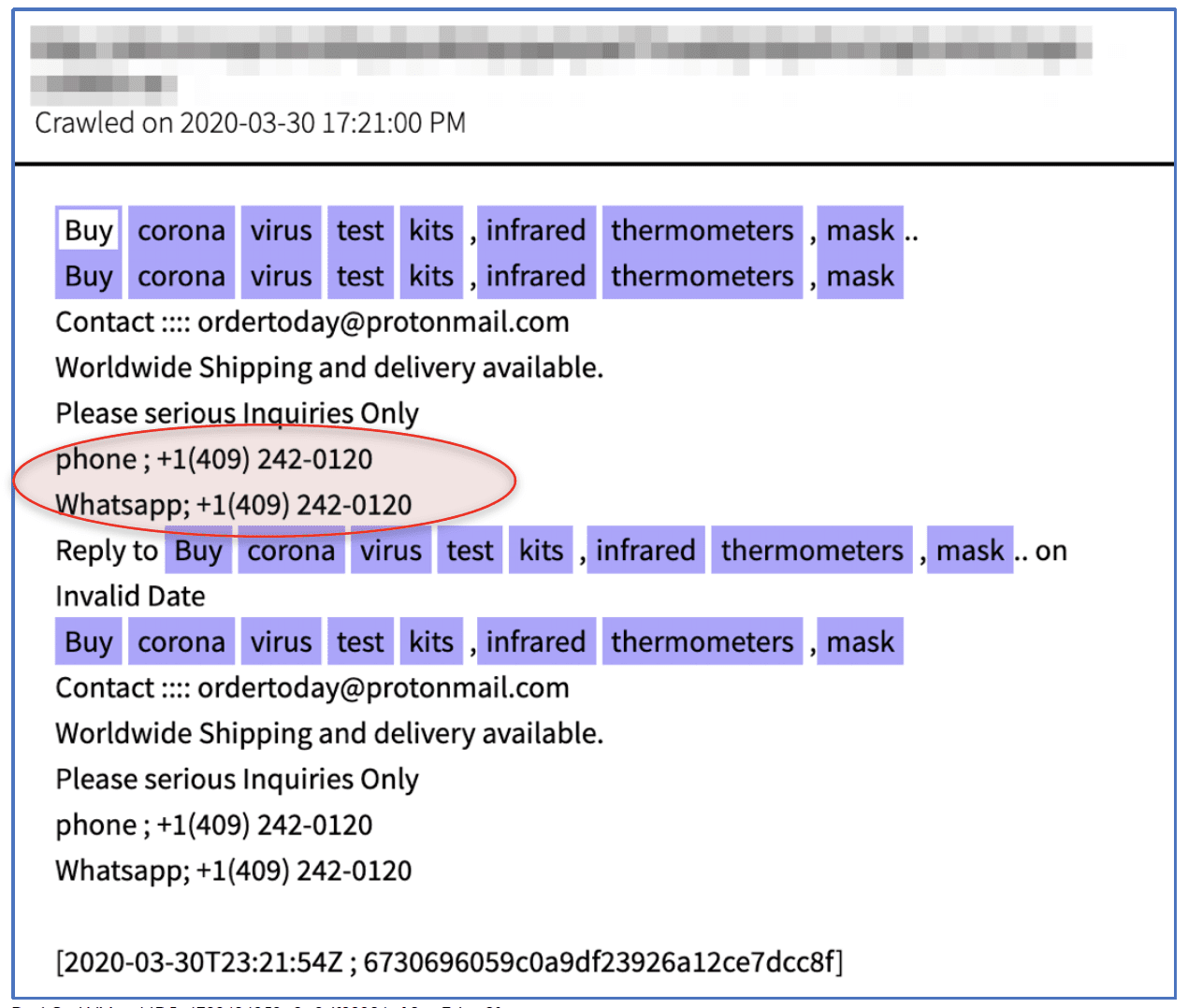
The lack of availability of COVID-19 test kits and shortage of ancillary personal protective equipment (PPE) and support equipment has one scammer offering test kits, infrared thermometers and masks. The advertisement did not include Bitcoin address or price, but provided a Texas, USA based Whatsapp for “Serious Inquiries Only”. Using DarkOwl Vision to pivot on the contact information, the phone number is also affiliated with numerous other offers across the dark web for drugs with the Surface web shop, worldglobalpharmacy.com and counterfeit items under the Telegram id: @drHades.
Original Source: https://paste.depesz.com/s/XQfSource DarkOwl Vision MD5: 6730696059c0a9df23926a12ce7dcc8fURL Redirects to Abuse
DarkOwl analysts reviewed various posts to forums and darknet paste sites to uncover many of the “Coronavirus” content simply redirects the reader to a possible-malware laden URL or prompt to submit a cryptocurrency payment in exchange for information.
This has become such an issue that many domain name service (DNS) providers have turned to denying domain registrations containing the words, “covid” or “corona” to combat the growing abuse.
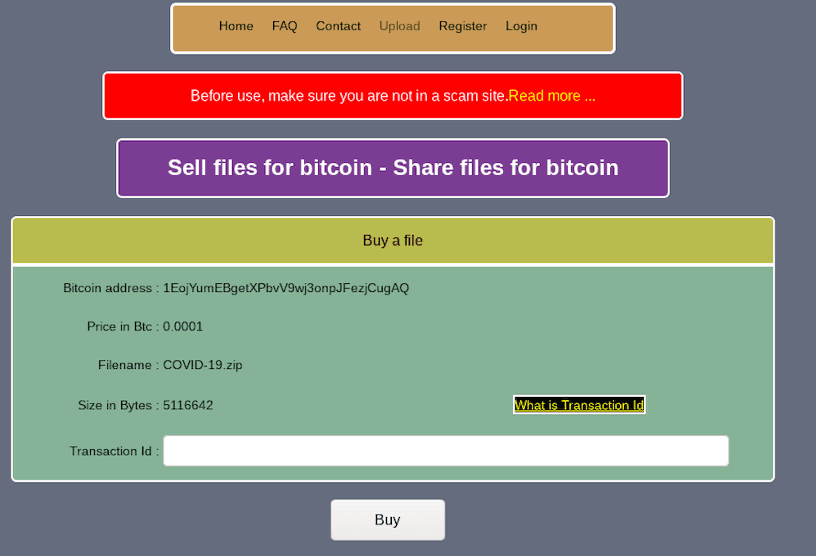
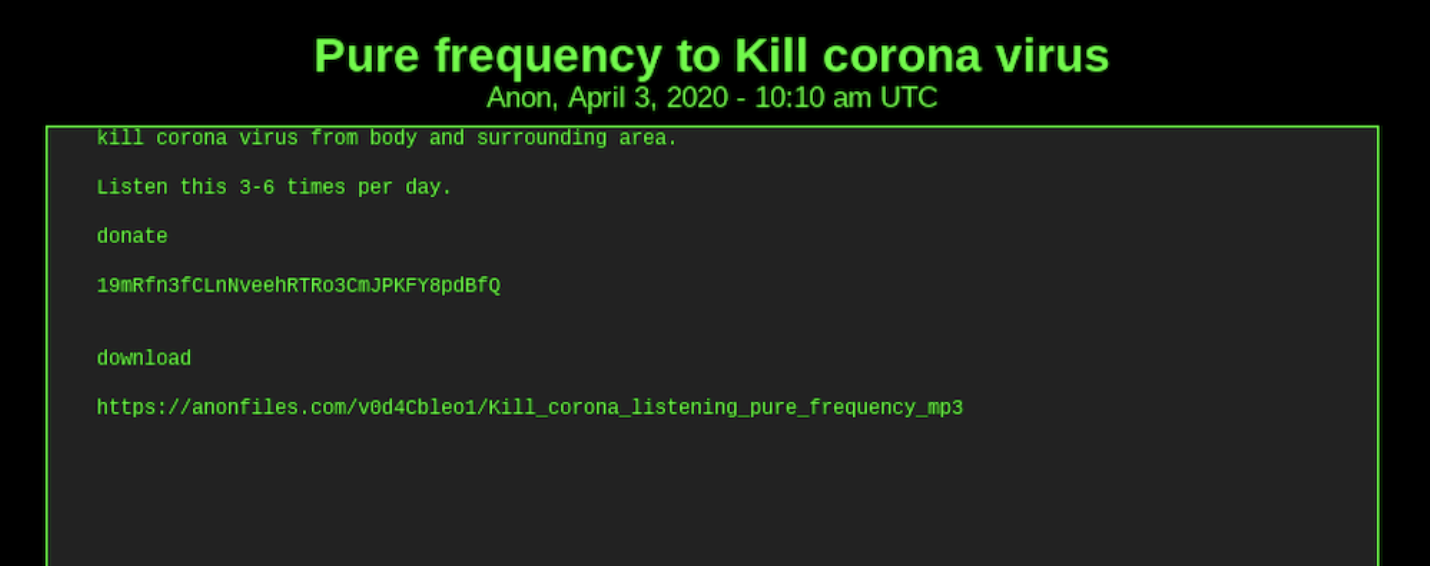
Original Source URL Redacted. Link to “Information” from dark web redirects visitor to pay for download for the COVID-19.zip file.Source DarkOwl Vision MD5: 2a48e3872b7519cc33c87a9e4e4da6beCan a Darknet Pure Frequency Kill COVID-19?
On the 3rd of April, 2020 another unexpected advertised “cure” for the coronavirus appeared on the dark web. An anonymous user posted a link to a MP3 file in the paste titled, “Pure Frequency to Kill corona virus” along with a suggestion to listen to the frequency 3 to 6 times a day for maximum results.
Masks Are Still Readily Available
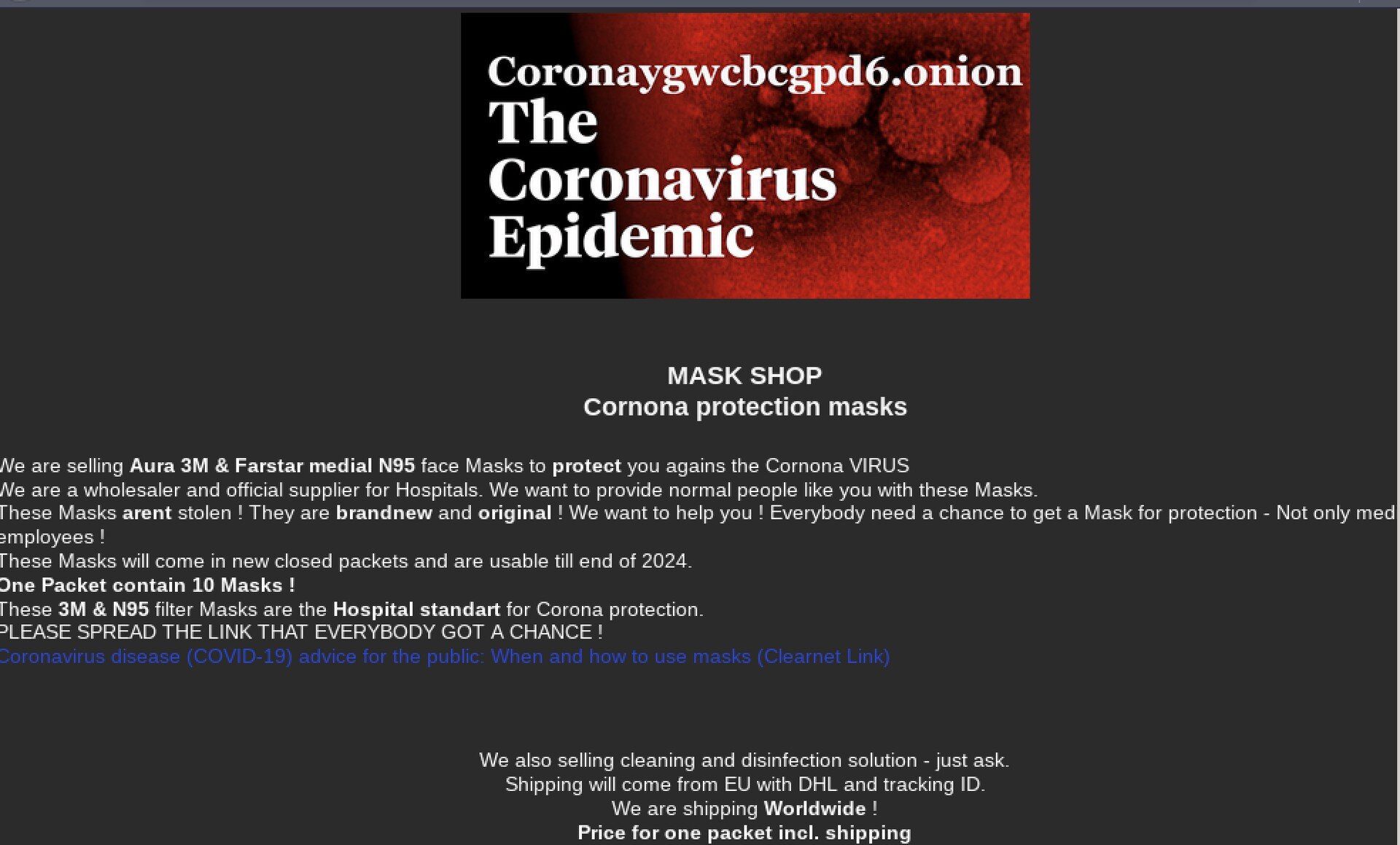
As we mentioned in our previous report, all types of masks are for sale on the dark web, including the N95 respirator type style in high demand. A Tor hidden service using “corona” in the V2 URL has “Aura 3M & Farstar medial N95 face Masks” available in packs of 10 for 80 EUROs.
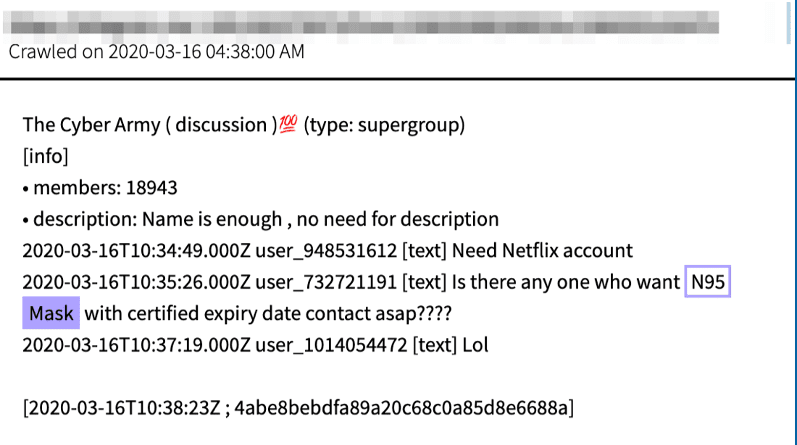
Original Source: http://coronajkkhq6dygj[.]onionDarkOwl Vision successfully captured a member of The Cyber Army Telegram group offering a N95 mask with certified expiry date on March 16, 2020.
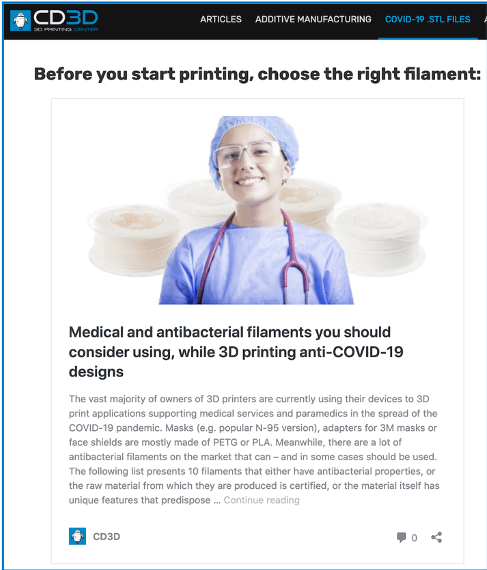
Source DarkOwl Vision MD5: 4abe8bebdfa89a20c68c0a85d8e6688aOriginal Source: https://3dprintingcenter.net/covid-19-3d-printinghealth-protective-designs/Another clever advert submitted by “Tequila_Wolf,” redirects the reader to a legitimate external link referencing a 3D printing center’s website. The website, CD3D offers designs for 3D printing protective face shields, masks for a noninvasive ventilator, and hands-free door openers.
Using DarkOwl Vision’s history, Tequila_Wolf has a remarkable dark web presence (mentioned in 76K pages), consisting of shared news articles and geo-political commentary, much of which is COVID-19 specific.
Criminals Discuss Benefits of COVID-19
Dark web user, Loserdub, submitted an interesting perspective of the COVID-19 crisis commenting in an “illegalism” channel on popular darknet forum, Raddle, that they had found police presence minimal and shoplifting easier than ever.
Another user on the forum added they use a medical face mask to conceal their identity.
Original Source: http://lfbg75wjgi4nzdio[.]onion/f/Illegalism/108236Anti-Malarial Drugs Now Available
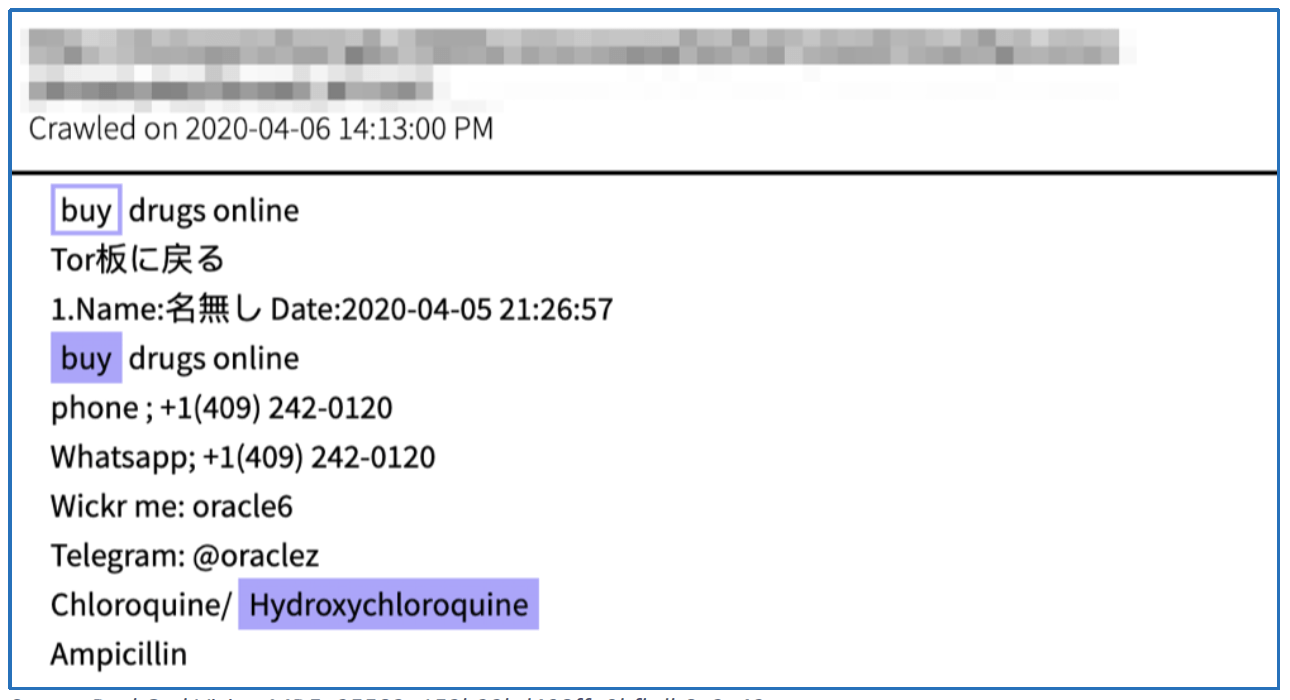
Since US President, Donald Trump suggested anti-malarial drugs such as chloroquine and hydroxychloroquine may have potential use in fighting COVID- 19, scammers have also started offering these drugs for sale on the darknet. The same scammers offering virus test kits under the telegram moniker, @drhades, shares the same phone number as listed in the advertisement for chloroquine, with telegram identification: @oraclez. This is further evidence of an elaborate scamming network on the darknet looking to profit from the COVID-19 crisis.
Source DarkOwl Vision MD5: 35583a153b32bd408ffa9bfbdb8e2e43Quantifying Potential Increase in Darknet Usage Due to COVID-19
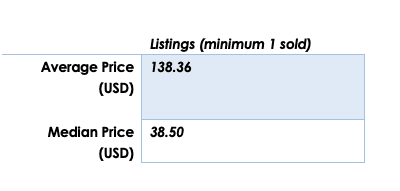
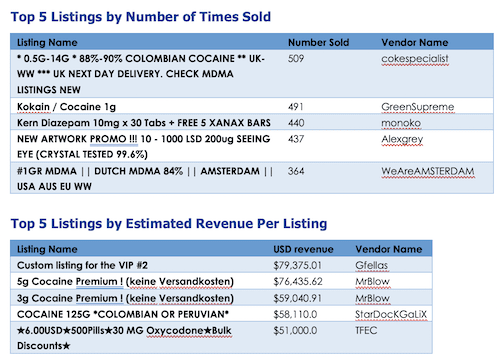
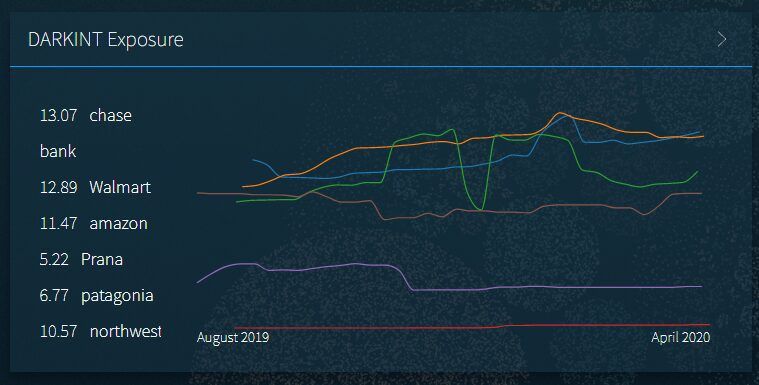
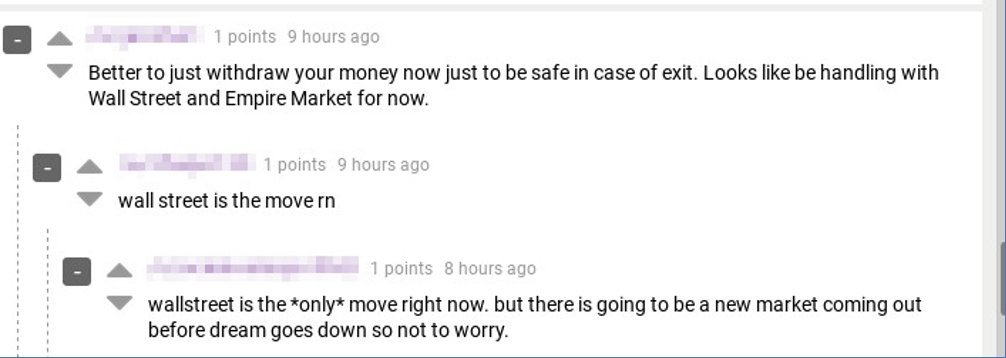
DarkOwl analysts were asked by a third party to review potential quantitative approaches to trends in darknet use due to COVID-19 and associated global government-mandated shelter-in-place orders. Hypothesis is that with more of society confined to their homes there would be an increase in darkweb drug market use and purchases. Some darknet drug forums supported this theory with new users asking how to purchase drugs from markets and some forums experiencing what could have been interpreted as a “surge” in usage.
One such forum that has had a historical presence on the darknet is Darknet Market Avengers (DMA).
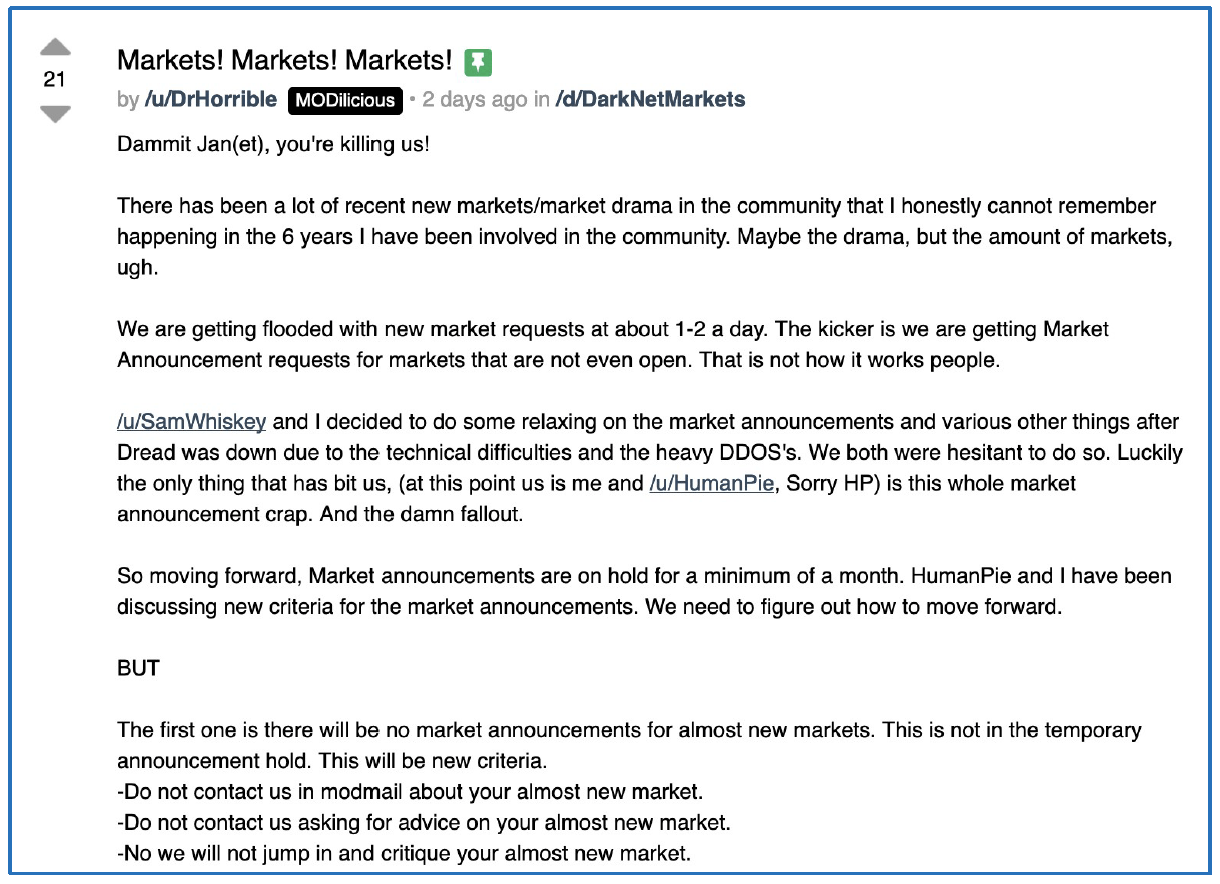
Another popular darknet forum, Dread, also suggested that Markets were experiencing a surge in usage with a thread posted by dread Mod, /u/DrHorrible, at the first of April. The moderator’s post also suggested that there were an increase in new market announcements for many markets that weren’t even online yet. After carefully reviewing market data in DarkOwl Vision, analysts determined that the markets only mad Vendor profiles public and not necessarily the users.
In many cases, even the market vendor profiles were encrypted and not easily captured by the engine autonomously. This prompted a review of forum data to see if there was any empirical evidence to support the theory of increased darknet use. This prompted a side-effort to collect hundreds of thousands of user registrations across many darknet drug-specific forums to see an exponential increase in registrations existed.
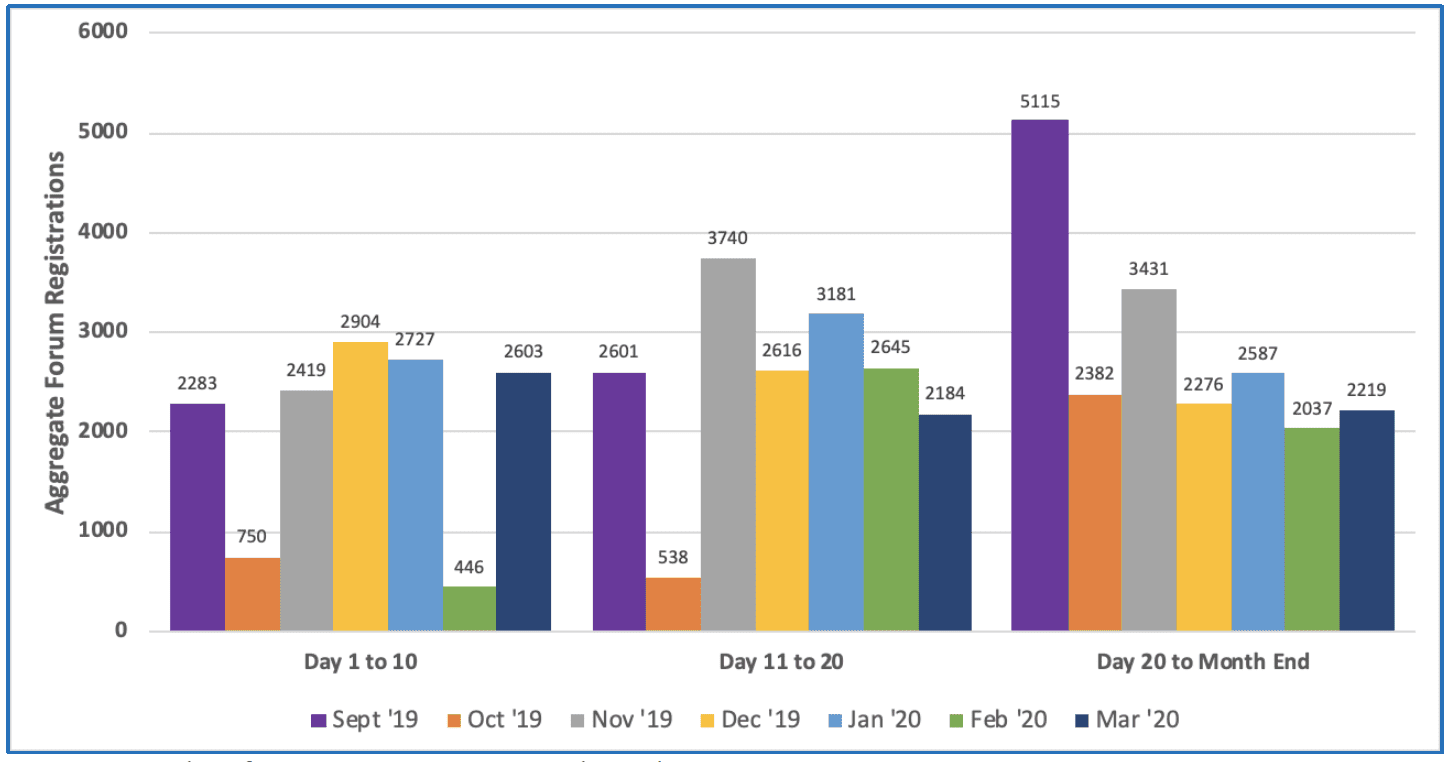
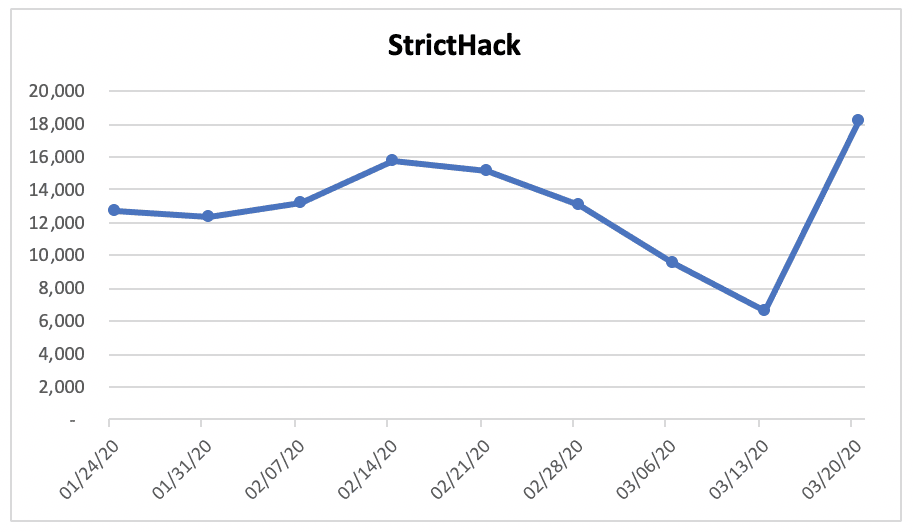
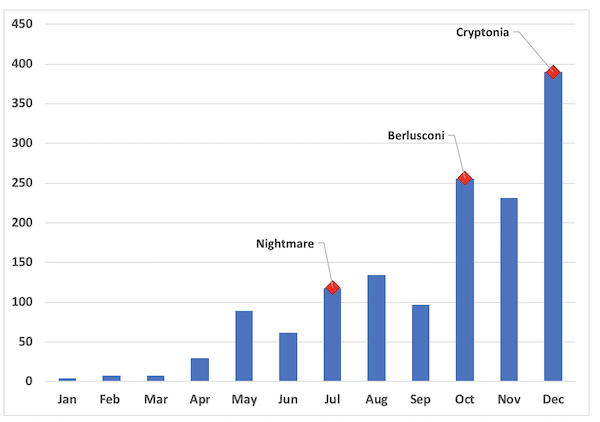
Unfortunately, the data captured from Darknet Market Avengers exhibited trends similar to the registrations recorded at Envoy, another drug-specific darknet forum. DarkOwl observed an average daily number of registrations in the last three months of about 225 new users. These numbers are consistent with the forum’s registration rate in 2019 and 2017. The forum also experienced a period of DDoS attacks in the first two weeks of October in 2019 and the first week of February in 2020 along with many other markets and forums on Tor.
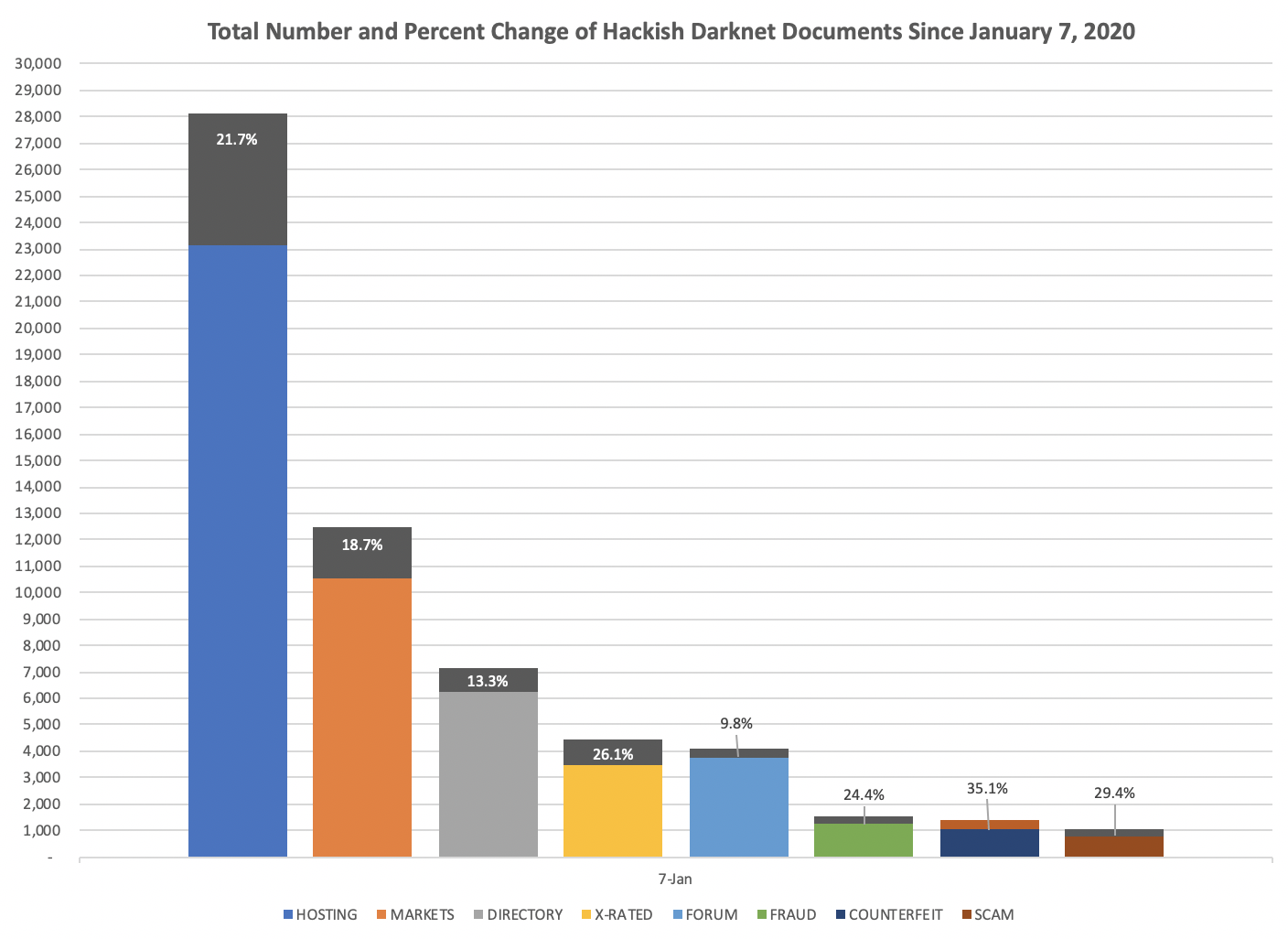
Aggregate Number of Forum Registrations on Popular Darknet Drug ForumsThese drops in registrations are evident visually as demonstrated by the monthly and weekly comparisons in the bar chart below. Unfortunately, DarkOwl did not observe data to support any assumption that darknet usage had increased in recent months, and if anything, merely confirms the darknet is conducting business as usually during the COVID-19 pandemic.
We will continue to watch as trends emerge and report back here.

![Original Source: http://d5jzfmy5d3oqlia4pnfu37pztv2n3eknxdoi57ycwywb2klkt42b43ad[.]onion](https://www.darkowl.com/wp-content/uploads/2021/12/CV2-1.png)
![Original Source: http://d5jzfmy5d3oqlia4pnfu37pztv2n3eknxdoi57ycwywb2klkt42b43ad[.]onion](https://www.darkowl.com/wp-content/uploads/2021/12/CV2-2.png)
![Original Source: http://dccvdpx2tksoyue5p5cpzqwhwyv4njkfaa3p7km7eyh6kke2atwfoiqd[.]onion](https://www.darkowl.com/wp-content/uploads/2021/12/Screen-Shot-2020-04-08-at-10.45.26-PM.png)

![Original Source: http://coronajkkhq6dygj[.]onion](https://www.darkowl.com/wp-content/uploads/2021/12/Screen-Shot-2020-04-08-at-10.55.04-PM.png)
![Original Source: http://lfbg75wjgi4nzdio[.]onion/f/Illegalism/108236](https://www.darkowl.com/wp-content/uploads/2021/12/CV2-13.png)