October 12, 2023
Introduction
When Hamas militants entered Israel along several fronts on 7 October 2023, Israel and the world were shocked. As events have unfolded this has turned to disbelief that Hamas were able to mount such a complex and successful attack without prior intelligence to indicating an attack. In the months and years to come people will surely reflect on the entirety of intelligence failures that lead to these events, but initial reports seem to suggest that Hamas succeeded by “going dark.”
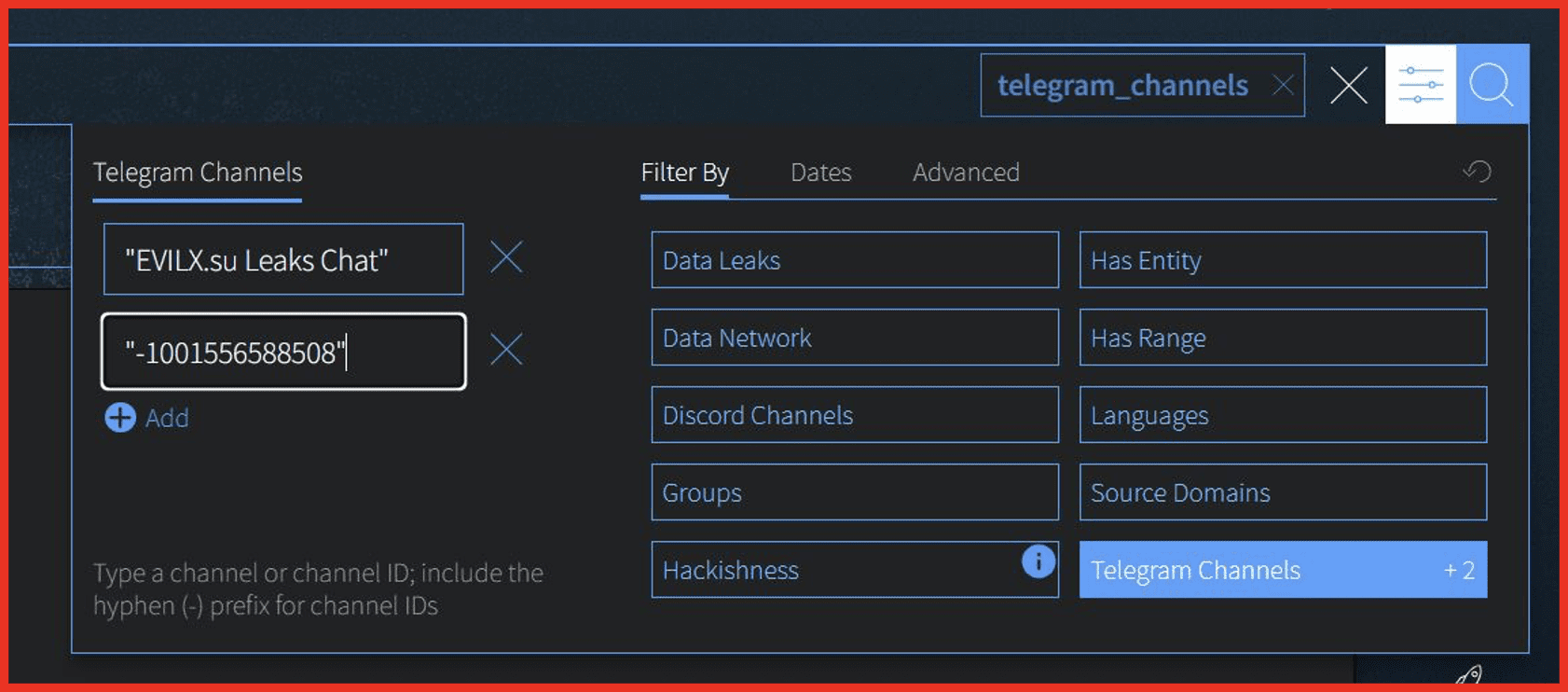
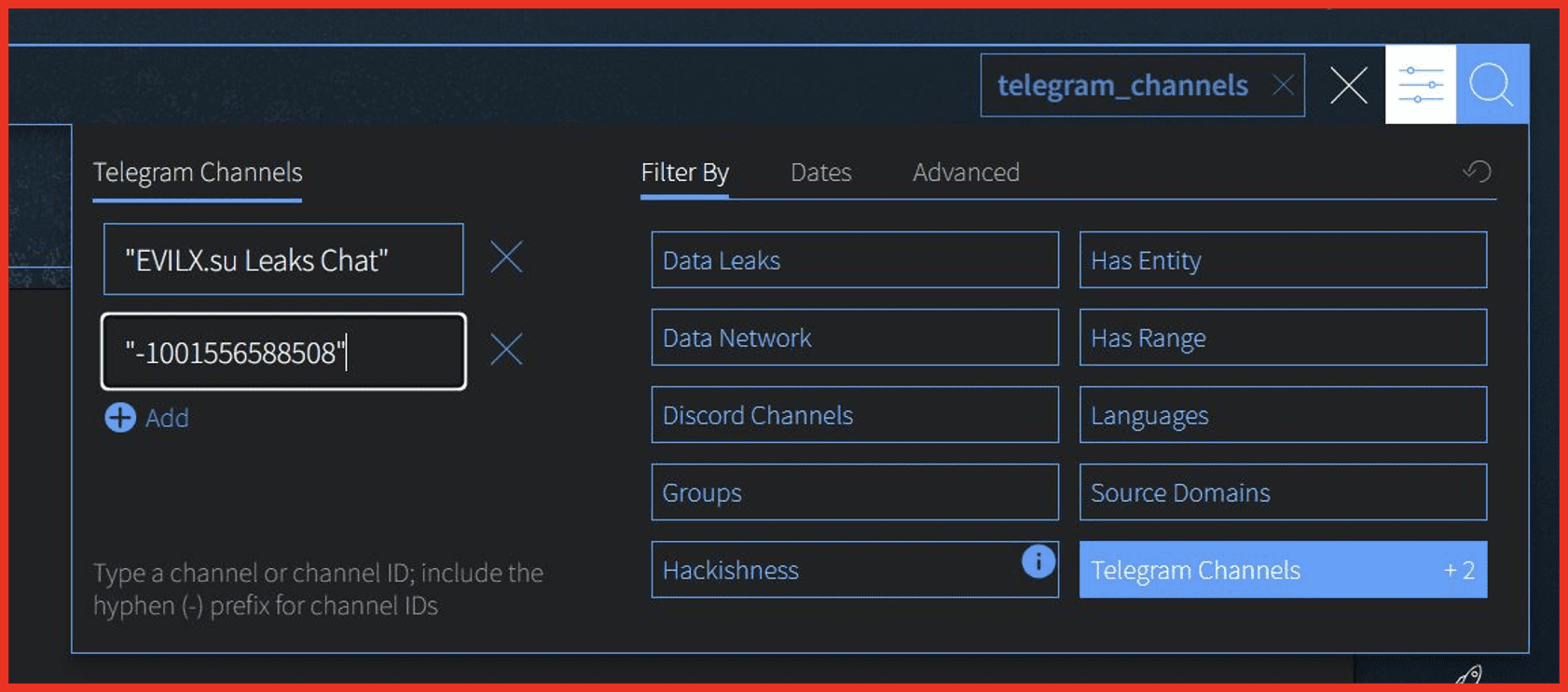
DarkOwl analysts reviewed our coverage of Hamas linked Telegram channels to identify if there was any change in their activity preceding the assault. We identified that there was a period of inactivity in the run up to the attacks for some but not all the channels. This could have been a coincidence, and we have seen no hard evidence suggesting that the period of inactivity was a precursor to the invasion. However, it is important to monitor the activity of pro Hamas Telegram channels to establish if there were any patterns to the posts.
In this blog, we review some of the channels we are currently monitoring.
Hamas Telegram Channels Go Dark
DarkOwl has been tracking several Telegram channels which are linked to Hamas or are pro-Palestine. These channels actively share information related to their “cause” with messages from Palestinian officials and military statements from al-Qassam Brigades. While most of these channels were making several posts a day, a pattern has emerged where a period of inactivity ensued before the attacks.
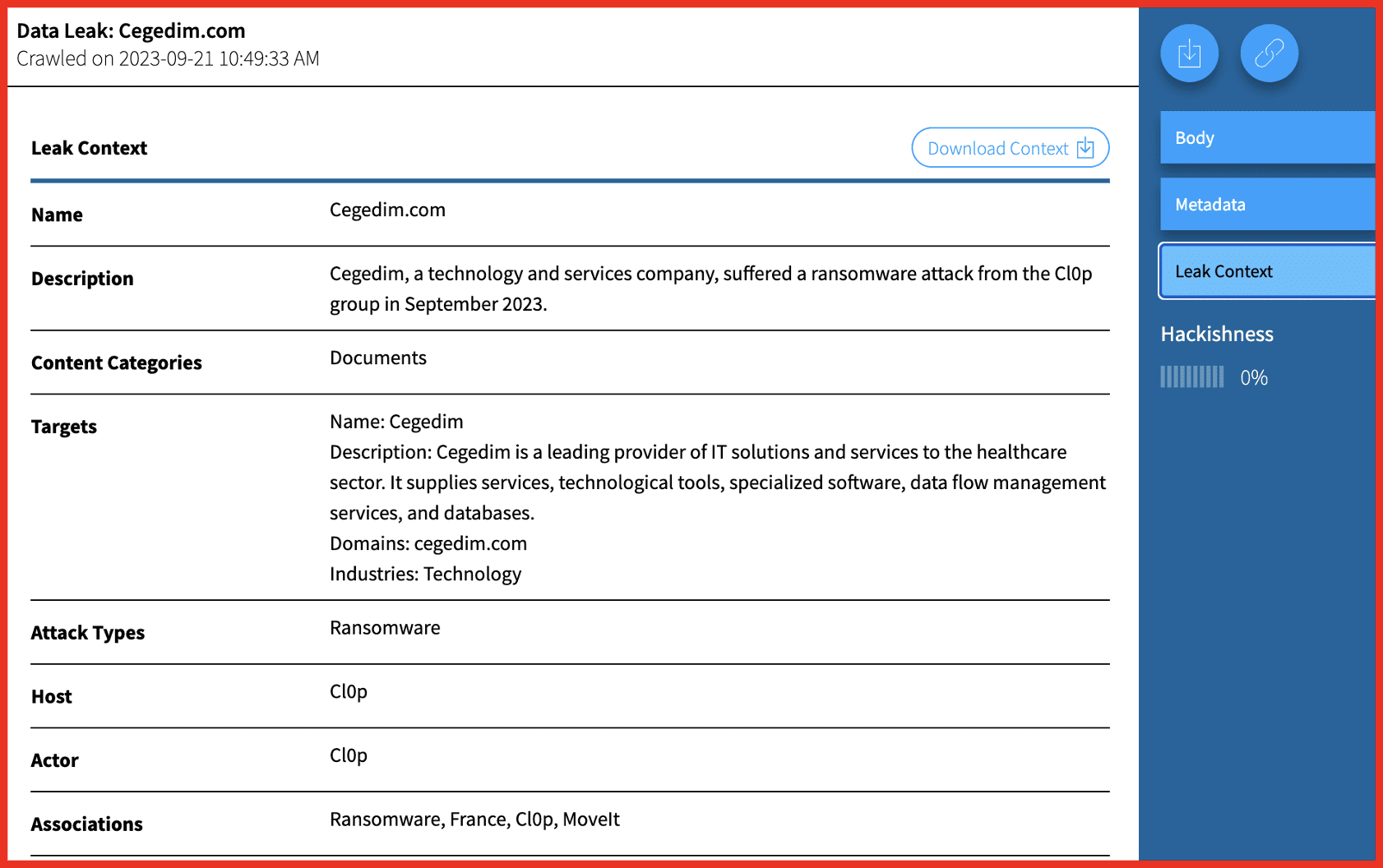
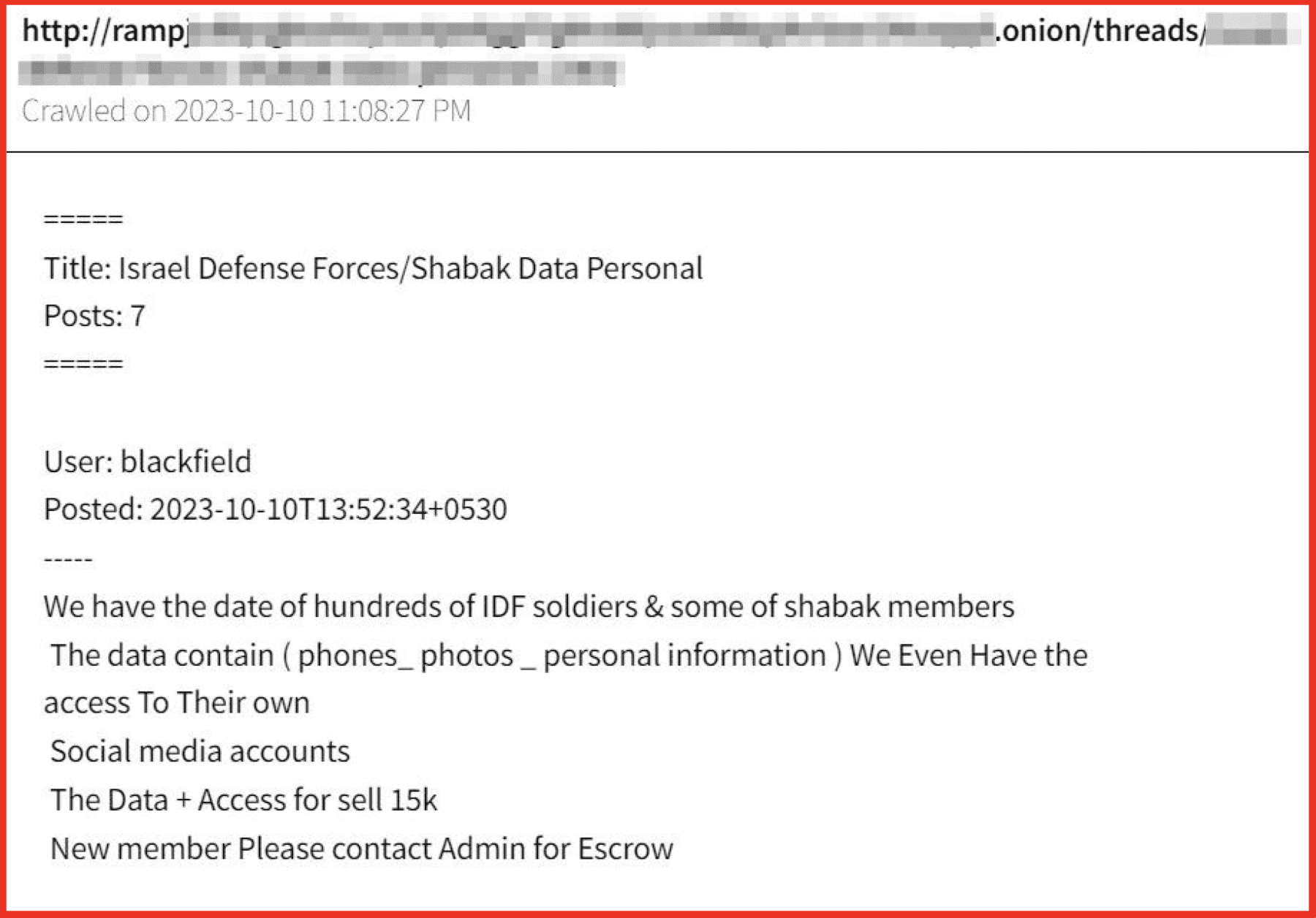
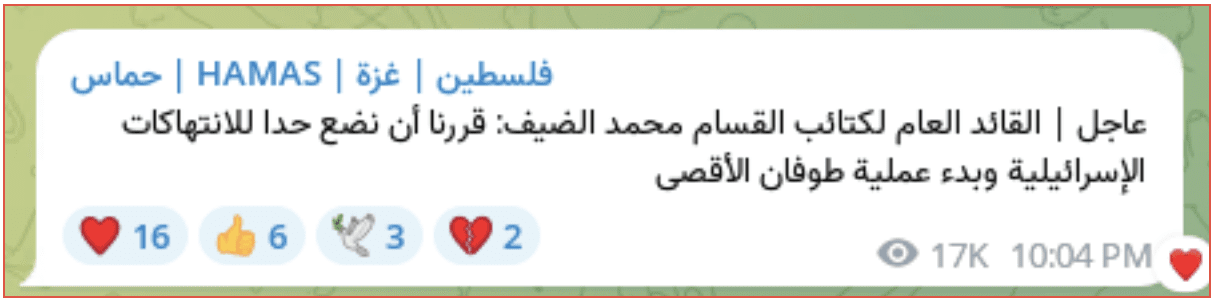
The telegram channel حماس | HAMAS | فلسطین | غزة, which translates to Hamas | Hamas | Palestine Gaza, has over 66,000 subscribers. The description of the channel claims to provide a media network, with speed and credibility and exclusive firsthand news. Regular posts were made until 4 July when they stopped, with no explanation. The next post was made at 8:04am local Gaza time on 7 October.
Figure 1: حماس | HAMAS | فلسطین | غزة, telegram channel
[TRANSLATED IMAGE]
Urgent Commander in Chief of the Qassam Brigades, Muhammad Al -Dhaif: We decided to put an end to Israeli violations and start the Al -Aqsa Flood Operation
From that point on that channel is very active, with regular posts made in Arabic and many images shared, including breaching “the wall.”
[TRANSLATED IMAGE]
Young people are storming the Gaza Strip after storming the settlements and burning Israeli military vehicles.
The group I.C.C (Islamic Cyber Corps) is a hacktivist group that publishes leaked information and shares details of their hacking activities. Although it is not a very active channel, there is a noticeable gap in postings between 22 September and 7 October. From that time, they have shared more posts including information purportedly from the Israeli DOD and fact checking media stories.
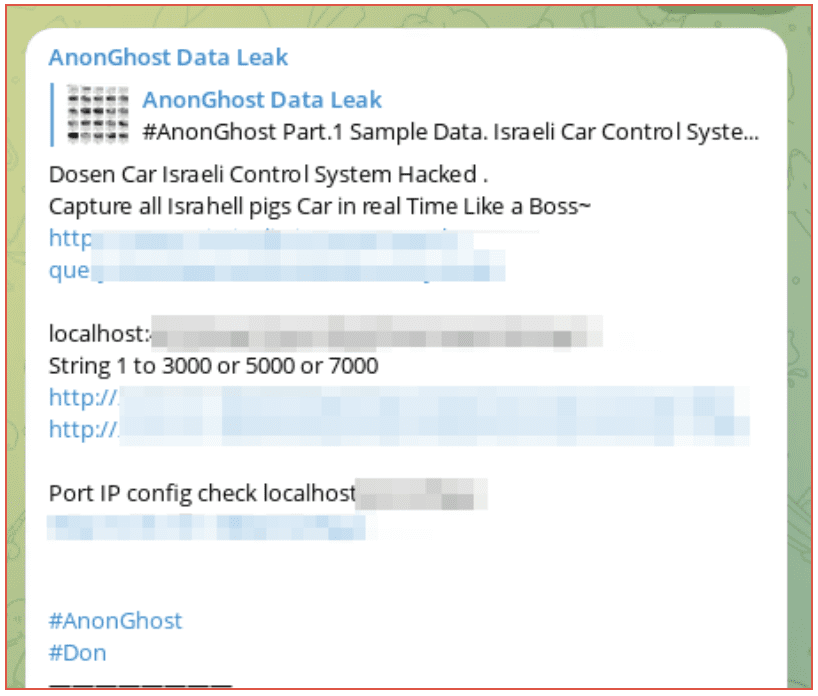
AnonGhost Data Leak channel, which is a channel dedicated to sharing leaked information obtained by the hacking group last posted on 2 April. Their next post was on 7 October when they began to leak information related to Israeli car systems, encouraging followers to capture Israelis in their cars. This group has always targeted Israel specifically, and it is worth noting they were more active on their official channel.
Figure 2: AnonGhost Data Leak Telegram Channel
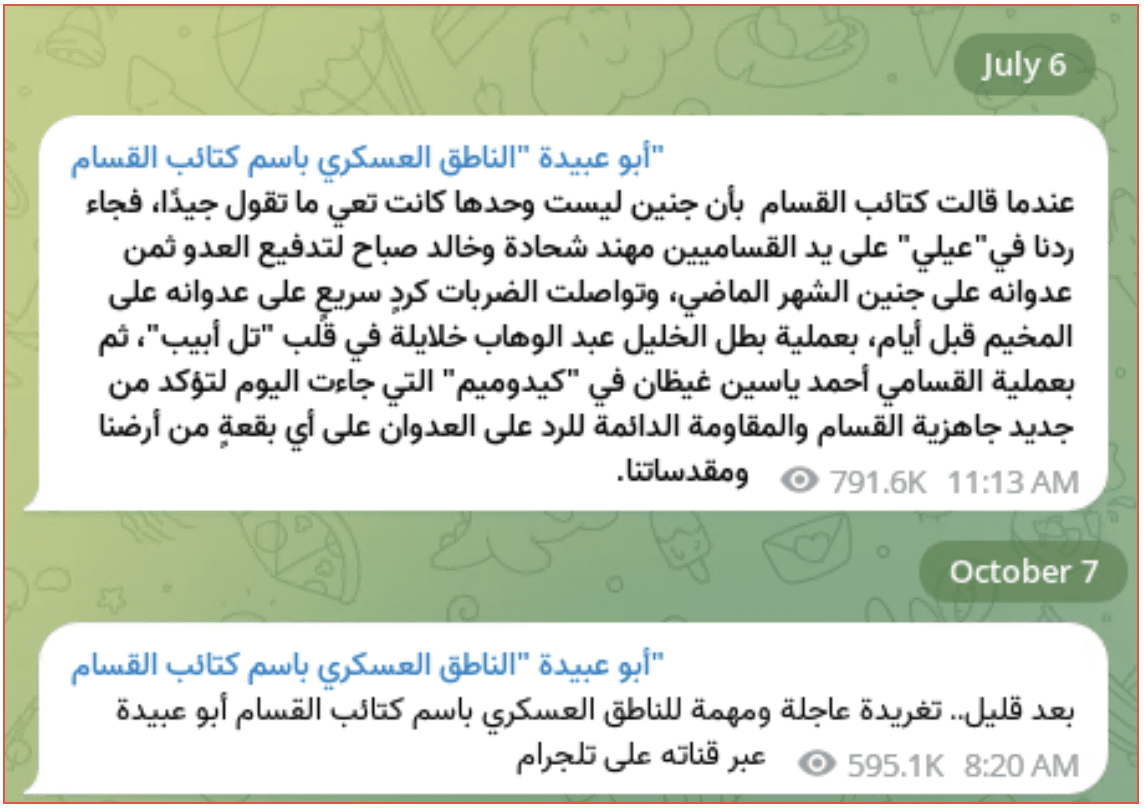
The channel “أبو عبيدة “الناطق العسكري باسم كتائب القسام” which translates to “Abu Ubaidah, Military Spokesman for the Al-Qassam Brigades” has almost 400,000 followers. The Al-Qassam Brigade is the military wing of Hamas. The channel is used to make official announcements. Although the updates are not regular, there are no posts made between 6 July and 7 October.
[TRANSLATED IMAGE]
Shortly after … an urgent and important tweet of the military spokesman in the name of the Al -Qassam Brigades Abu Ubaidah through his channel on Telegram
The channel Free Palestine 48 had a period of inactivity from 10 September until 7 October, when its first post was a video, it claimed showed “children of Gaza rejoice, playing on top of an armored truck seized by the resistance fighters.”
Figure 3: Free Palestine 48 telegram channel
Previous posts had shown pro-Palestine images and details of Saudi Arabia’s normalization talks with Israel as well as what it claims are Israeli infractions on the people of Gaza. There is no indication of why the channel did not post between these time periods. Unlike many other channels reviewed in this blog the posts are made in English rather than Arabic, likely to project its message to a larger audience.
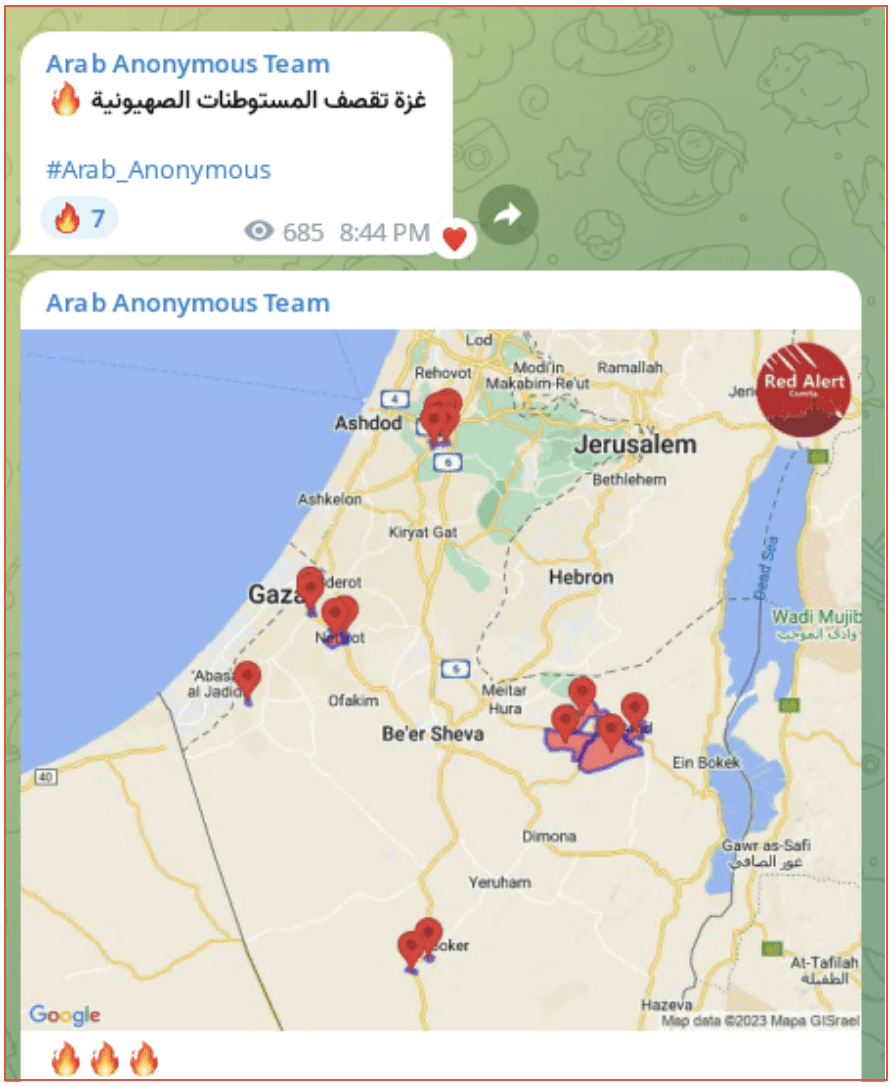
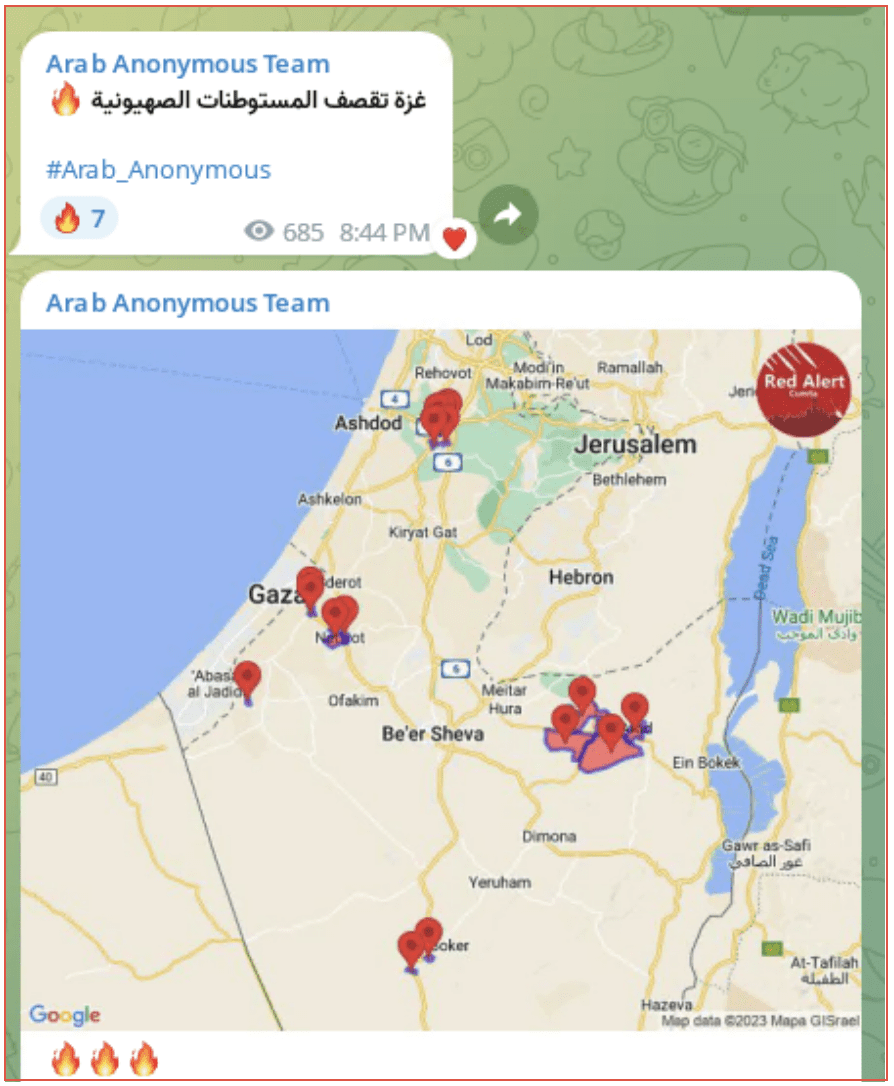
تغريدات || جيش فلسطين الإلكتروني PEA, The PalestineEArmy had not posted on their Telegram channel since 5 August. They first posted on 6 October. The majority of the posts were forwarded from the Arab Anonymous Team Telegram Channel. The Arab Anonymous Team were also inactive from 27 July to 7 October. Their first post announced the bombing of Israel from Gaza.
[TRANSLATED IMAGE]
Gaza bombed Zionist settlements 🔥
Hamas Linked Channels Stay Active
The Telegram channel طوفان الاقصئ من قلب الحدث (The flood of Al Aqsa from the heart of the event) has nearly 4,000 subscribers. The account self identifies as pro-Palestine and regularly reshares prominent religious texts. The channel was actively posting in the run up to the attacks. They did not start posting images or text related to the invasion until the afternoon of 7 October. The videos shared of the attacks including images of hostages and militants entering Israel have not been corroborated at this time.
Figure 4: Image from Sahr_2023 telegram channel
كتيبة جنين الإعلام الحربي-الحساب الاح – Jenin Military Media Brigade-Account, did not publish videos related to Hamas militants breaking through the wall. On 3 October they posted images of what appear to be militants holding pro-Palestinian images with pictures of individuals, they indicate this is “part of the participation of the Al-Quds Brigades-Kaba, the commemoration of the Jihadist launch, the Martyrs of Victory.”
Figure 5: Sarayajneen Telegram channel
The content of the posts in the days preceding the invasion continued with a similar tone, often displaying images of militants with weapons, sometimes holding images of martyrs (fallen soldiers). These images are likely intended to evoke excitement from their supporters. Although they continued sharing images of militants with weapons and messages from the brigade and posts which appear to be religious text, unlike a lot of the other channels that we are monitoring they do not share images or videos of the Hamas incursion.
المَـرْيَــ𓂆ــم𓂆 طوفـ𓂆ـان_الاقصى 🔥💚2(Al -Maryoufan_Al -Aqsa 🔥💚) is another Telegram channel that was active in the period preceding the attack. They had previously shared images of militants holding weapons, as well as some memes. Subsequent to the attack this channel regularly shared a large number of videos of the events, some of which are very graphic in nature. They also regularly make what are known as martyrdom posts — or sharing the images of militants who have been killed, from personal pictures.
Of note, a channel named Hamas Online, which appears to make official statements on behalf of Hamas in English, did not stop posting in the lead up to the activity. However if official channels had gone quite that could have been an indication that the status quo had changed. The last post made before the events of 7 October is a post in relation to the October war of 1973 which it says “bears witness that resistance is the only option to deter the Zionist colonial occupation.” Which, in hindsight does seems to be an indication of what was to come.
New Pro-Hamas Channels Pop Up
As part of our collection efforts DarkOwl is constantly searching for an adding new sources of relevance to our data collection. Since the events of last Saturday, we have identified a number of new channels which have been created in response.
Other channels were created in direct response to the conflict. للإعــلام_الـحــربـي 🇵🇸 (for war flags) was created on 8 October and has already amassed a following of over 5,000 followers. This purports to be sharing news about the conflict and updates on what has been bombed.
Conclusion
Our coverage of Telegram channels linked to Hamas or Pro-Palestine have shown that they have operated in different ways. It is unclear if any of this activity was linked to the invasion or directly linked to it. Although there were strange periods of inactivity on some of the channel, we cannot know what caused that. However there does not seem to be a clear pattern in the activity that would suggest that the periods of inactivity were in any way coordinated among the different groups. Furthermore, the number of channels that remained active would indicate there was no mandate of silence.
What is clear is that these channels are being used by the operators to spread information relating to the conflict and in the days since the invasion they have become very active sharing videos, images, and commentary on the events. While we cannot corroborate the validity of what is being shared, it is clear that Telegram is being used as a way to share news and information at a speed that is quicker than the traditional news media. In our next blog we will examine how this is being done.