Cybercriminal Arrests and Disruptions: 2023 Look Back
April 23, 2024
Although cyber actors continue to successfully target victims globally, extorting and fraudulently obtaining large sums of money, Law enforcement are becoming increasingly adept at capturing these cybercriminals and holding them to justice.
Throughout 2023 there were a number of notable arrests and prosecutions. In this blog, DarkOwl analysts summarize what are arguably the biggest law enforcement actions of 2023 globally.
Conor Brian Fitzpatrick AKA POMPOMPURIN
In March 2023, an individual named Conor Fitzpatrick was arrested by the FBI in upstate New York. He was accused of being the administrator of popular dark web forum BreachForums.

Fitzpatrick was charged with hacking, wire fraud, and possession of child abuse imagery. He admitted to the majority of these offenses upon his arrest and was facing up to 40 years in prison. In January 2024, he was sentenced to 20 years’ supervised release. Fitzpatrick will have no access to the internet for the first year of his home confinement and must register with state sex offender registries.
Prosecutors said the following:
“By creating a platform for hackers and fraudsters to connect and conduct business, the defendant made it possible for BreachForums members to commit exponentially more crimes and more sophisticated crimes than any could have done alone.”
However, soon after Fitzpatrick’s arrest, BreachForum was back up, being run by his reported partner Baphomet. It remains to be seen how this will continue.
The Hive Ransomware Gang’s Takedown
In January 2023, the FBI announced they had successfully disrupted the Hive Ransomware group that has targeted more than 1,500 victims in over 80 countries around the world, including hospitals, school districts, financial firms, and critical infrastructure.

Since 2022, the FBI had successfully infiltrated the servers for the group and was able to provide decryption keys to their victims. This led to them, in partnership with European partners successfully seizing the infrastructure used by the group. Unlike disruptions which were attempted by Law Enforcement later in 2023 and into 2024, this appeared to disrupt the group.
In December 2023, French authorities arrested a Russian national in Paris for allegedly helping the Hive ransomware gang with laundering their victims’ ransom payments. They also seized €570,000 worth of cryptocurrency. This highlights that even after infrastructure is seized, authorities globally will continue to hunt the individuals perpetrating the crimes.
Denis Gennadievich Kulkov

Kulkov was identified as the mastermind behind the Try2Check credit card checking operation. In May 2023, the DOJ unsealed an indictment charging Kulkov with access device fraud, computer intrusion, and money laundering in connection with his operation of Try2Check, the primary service offering “card-checking” to cybercriminals in the stolen credit card trade. Kulkov reportedly earned over $18 million from the scheme.
According to the DOJ:
“The Try2Check platform catered to cybercriminals who purchased and sold stolen credit card numbers in bulk on the Internet, offering criminals the ability to quickly determine what percentage of the cards were valid and active. As such, Try2Check was a primary enabler of the trade in stolen credit card information, processing at least tens of millions of card numbers every year.”
Despite being wanted by the U.S. Secret Service, he remains in Russia, beyond U.S. authorities’ reach.
Interpol’s Arrests in Africa
In April 2023, Interpol’s Africa Cyber Surge II operation led to the arrest of multiple individuals and the seizure of assets worth millions across Africa. These operations targeted groups involved in various cyber crimes including business email compromise (BEC), romance scams, and credit card fraud. They were also able to seize, or takedown infrastructure linked to the group’s operations.
The operation led to the following:
- Cameroon: 3 suspects arrested for $850,000 online art scam.
- Nigeria: 1 individual arrested for defrauding a Gambian victim.
- Mauritius: 2 money mules arrested linked to messaging platform scams.
- Gambia: 185 malicious IPs taken down through proactive measures and partnerships.
- Cameroon: 2 darknet sites shut down by authorities.
- Kenya: 615 malware hosters taken down by authorities.
Ragnar Locker Ransomware

In October 2023, Europol announced that it had disrupted the infrastructure associated with the Ragnar Locker Ransomware group. In addition, French authorities arrested a key individual linked to the gang, who was said to be a central developer. Further individuals were also interviewed in Spain and Latvia. Two suspects associated with the ransomware crew were previously arrested from Ukraine in 2021. A year later, another member was apprehended in Canada.
This highlights that the most effective way to take down a ransomware group is not just to seize the infrastructure but also arrest the individuals behind it.
Warzone RAT Malware Operation
In February 2023, the FBI announced that it had dismantled the Warzone RAT operation, arresting two individuals associated with the malware – in Nigeria and Malta. They also indicated that they had seized multiple domains.
The Warzone RAT malware, was a Remote Access Trojan (RAT), which enabled cybercriminals to browse victims’ file systems, take screenshots, record keystrokes, steal victims’ usernames and passwords, and watch victims through their web cameras, without their knowledge or permission.
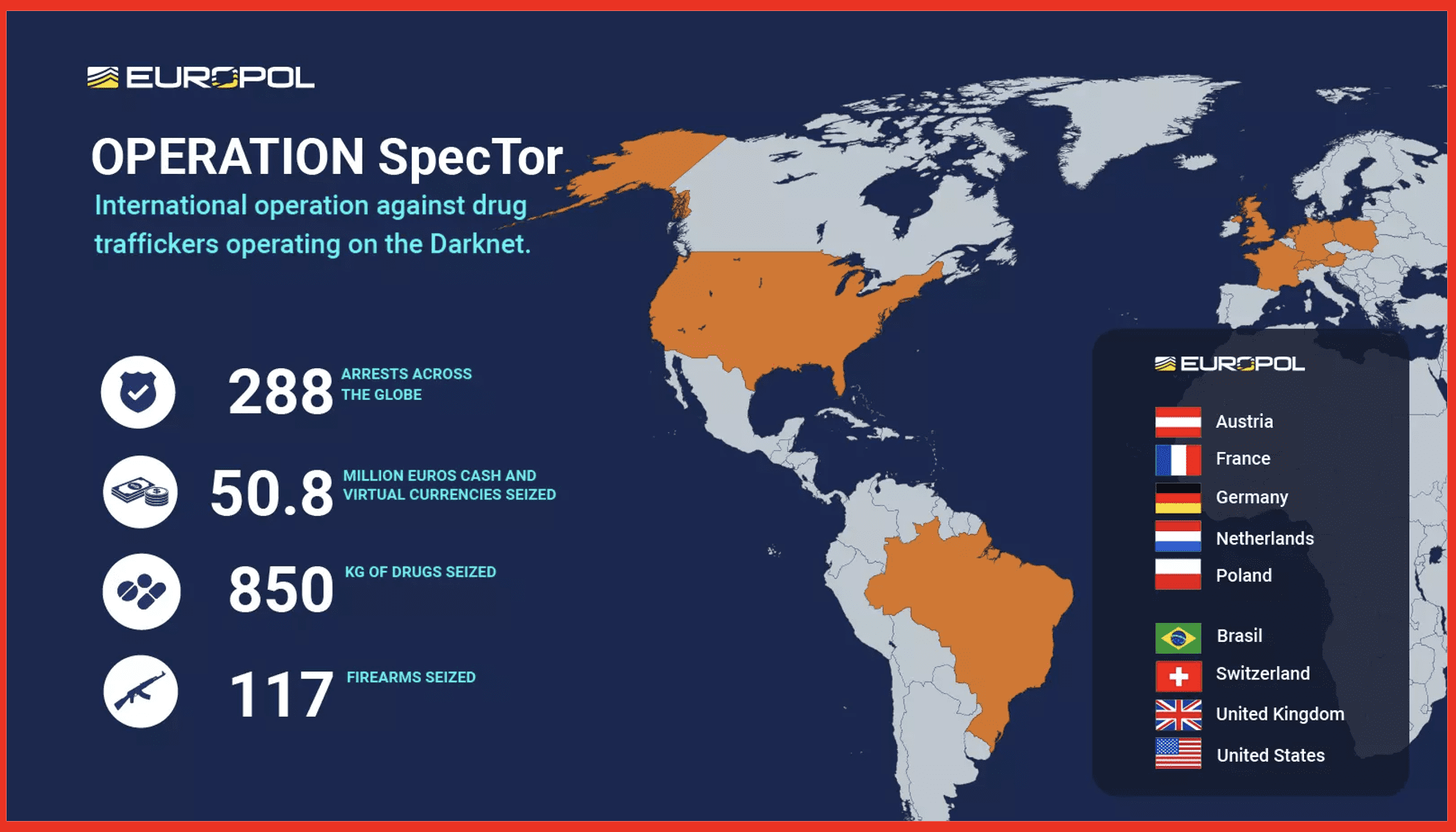
Operation ‘SpecTor’

In May 2023, the FBI spearheaded 288 arrests across multiple countries, taking down the dark web Monopoly marketplace responsible for selling drugs. It was reported to be the largest international operation against darknet trafficking of fentanyl and opioids. The operation also seized 117 firearms, 850 kilograms of drugs that include 64 kilograms of fentanyl or fentanyl-laced narcotics, and $53.4 million in cash and virtual currencies.
Lapsus$ Arrests
In August 2023, two teenagers in the United Kingdom were found guilty of conducting cyberattacks against Uber, Nvidia, Rockstar Games, and Okta, among others as part of the criminal gang Lapsus$. Arion Kurtaj, an 18 year old from the UK was sentenced to indefinite detention in a hospital.

As well as hacking major companies he was also accused of blackmailing employees and causing millions worth of damage to the companies that he targeted. He also leaked data that he had stolen from them. Another individual was also found guilty of similar charges but could not be named due to his age. This case highlighted that young individuals that are perpetrating hacking crimes results in difficulty prosecuting them because of their juvenile status.
Conclusion
Only some of the law enforcement action that took place in 2023 are described in this blog. Law enforcement are becoming more and more successful in their operations against cybercriminals both in terms of arrests and seizure of infrastructure – including on the dark web.
However, events this year (2024) have already shown that some law enforcement action is not enough to take down groups, particularly ransomware groups. Notable activity against BlackCat/ALPHV and LockBit have shown to only take the groups out for a matter of days, when no arrests take place. BlackCat are reported to have recently conducted an exit scam after a high-profile ransomware was paid, and Lockbit seem intent on revenge after their recent skirmish with the law.
It is unlikely that law enforcement will be able to eradicate cybercrime and the game whack-a-mole will continue. However, the events of 2023 show that the law enforcement bodies globally are taking action and standing up to the criminals creating dire consequences for some, which will hopefully deter future threat actors.