Netflix Password Policy: Cybersecurity Angle
May 26, 2023
Netflix’s recently implemented password policy is receiving widespread complaints for corporate greed and increasing profit margins, but have you considered the degree to which cybersecurity was factored into this decision?
In this blog, DarkOwl analysts highlight password sharing concerns, look at current activity on the darknet targeting Netflix accounts using DarkOwl Vision and predict how the new password policy may affect fraud.
Cybersecurity Concerns
The importance of password hygiene and password protection is no secret. It is a constant topic of discussion in security trainings and amongst the security community – every day we hear of another commercial data or app breach. At this point, everyone can assume their email address and/or password has been leaked on the darknet or deep web.
Credentials are one of the most sought after and frequently exchanged digital goods in the darknet economy. In many cases, large quantities of compromised accounts will be combined and re-shared across multiple darknet and deep web forums, including dark web adjacent platforms such as Telegram. Criminals leverage this data in a variety of ways. For example, some may use a credential cracking or “stuffing” tool to cross reference emails with other password lists – or use common password conventions to guess the password – and verify an active email and password combo.
Netflix Targeted on the Darknet
Most are guilty of it – sharing a streaming account password with friends a family. After all, there are so many streaming services and we want access to them all! We also know that password sharing is bad practice. Password sharing enables various types of threat actors to gain unauthorized access to a Netflix account. According to Dark Reading:
- “Sharing a password undermines control over who has access to an account, potentially leading to a greater risk of unauthorized use and account compromise;
- Once shared, a password can be further distributed or changed, locking out the original user;
- Worse yet, if the shared password is used across multiple accounts, a malicious actor could gain access to all of them;
- And sharing passwords can also make users more susceptible to phishing and social engineering attacks.”
Netflix is regularly targeted on the darknet. DarkOwl analysts are currently closely watching to see what happens to unauthorized account access after the new password policy.
Currently we see Netflix targeted in the following ways:
Netflix Stealer Logs
Stealer logs are typically harvested by threat actors using a form of malware known categorized as “info stealers,” such as Raccoon and Redline, and use this data to maliciously gain access to online accounts. The below is an example DarkOwl analysts found on Russian Market (Genesis market replacement).

Source: DarkOwl Vision
Selling Netflix Accounts
The vendor below found selling a Netflix account for $4.95 USD on a traditional darknet marketlace, ASAP MARKET.

Source: DarkOwl Vision
Netflix Full Access Accounts
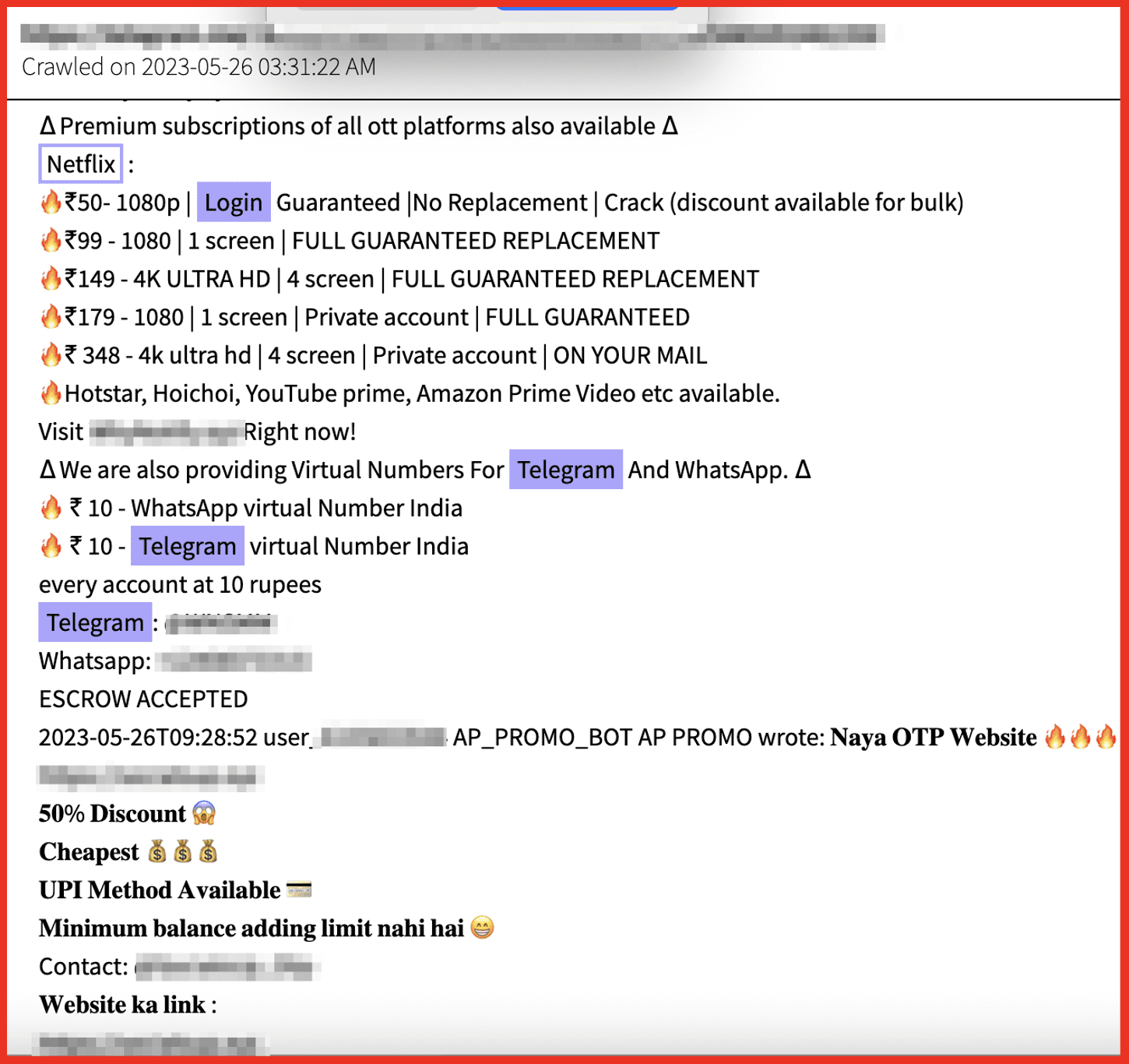
DarkOwl analysts found Netflix full access accounts being used to to bypass 2FA on Telegram. The post below shows a Telegram user selling various types of Netflix logins in Rupees, suggesting these threat actors are from/living in India.
Conclusion
DarkOwl analysts predict that the updated Netflix password sharing policies will likely combat a lot of the fraud observed on Telegram markets where people sell another person’s Netflix account for as little as a few dollars. However, we all know that cybercriminals and cybercrime are getting more and more sophisticated and creative and it won’t take long for fraudsters to find a new way to continue nefarious activity and reap financial benefits. The DarkOwl analyst team is observing the darknet and taking notes. Keep an eye out for part 2 once the policy has been in place longer for updates of darknet activity targeting Netflix.
Curious how darknet data applies to your use case? Contact us.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















