What is Credential Stuffing?
August 28, 2025
Cybersecurity might as well have its own language. There are so many acronyms, terms, sayings that cybersecurity professionals and threat actors both use that unless you are deeply knowledgeable, have experience in the security field or have a keen interest, one may not know. Understanding what these acronyms and terms mean is the first step to developing a thorough understanding of cybersecurity and in turn better protecting yourself, clients, and employees.
In this blog series, we aim to explain and simplify some of the most commonly used terms. Previously, we have covered bullet proof hosting, CVEs, APIs, brute force attacks, zero-day exploits, doxing, data harvesting, and IoCs. In this edition, we dive into credential stuffing.
Credential Stuffing 101
Credential stuffing, often shortened to ‘cred stuffing’, is a widespread technique utilized by cybercriminals to test if historically exposed e-mail addresses and password combinations are valid logins across multiple commercial websites. Opportunistic cyber criminals automate the testing of large ‘combo lists’ containing compromised e-mail addresses and passwords against commercial websites and once a successful authentication occurs readily steals the PII (personally identifiable information) and financial information, often saved, on the e-commerce shopping platform’s user profile.
Wordlists and compromised lists of email address and password combinations are the foundation for credential stuffing operations. Many multi-million record data leaks in circulation on the darknet make potential username/password combinations easily discoverable and exploitable at scale. Such leaks are utilized as input for credential stuffing scripts and applications. Wordlists are also in regular circulation amongst darknet threat actors, and some are already integrated into Linux distributions favored by pen-testers and hackers alike.
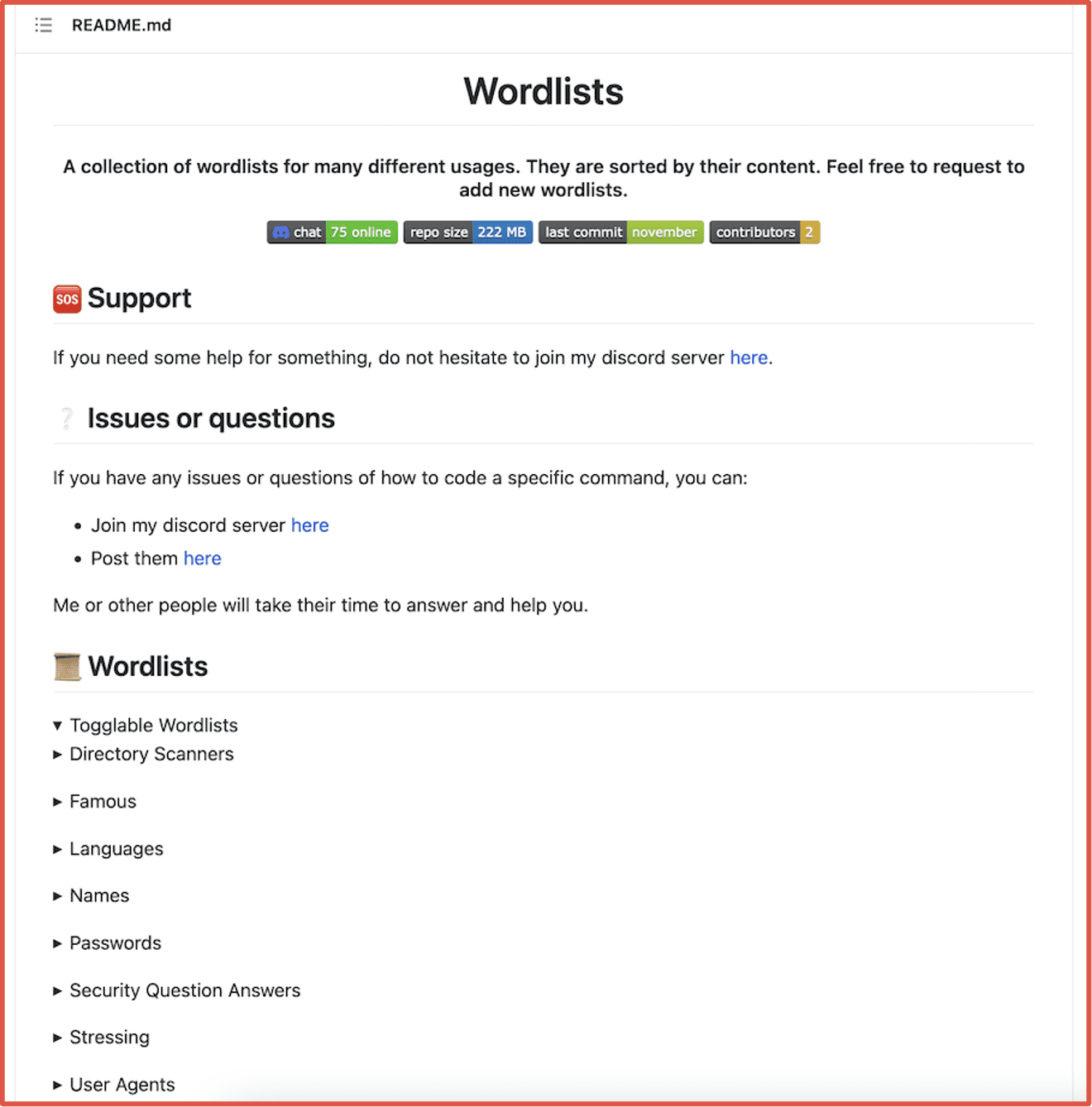
Figure 1: Wordlist Github Repository Popular with Offensive Security Specialists
Credential stuffing using malicious software and botnets affects not only the individuals but also the commercial organizations whose user accounts are surreptitiously accessed, as many immediately assume access was achieved due to vulnerabilities with the commercial service provider’s technical configuration instead of a simple credential stuffing technique conducted en masse. The uncertainty potentially erodes consumer and stakeholder confidence warranting that commercial agencies consider credential stuffing in their internal security frameworks and corporate risk assessments as well.
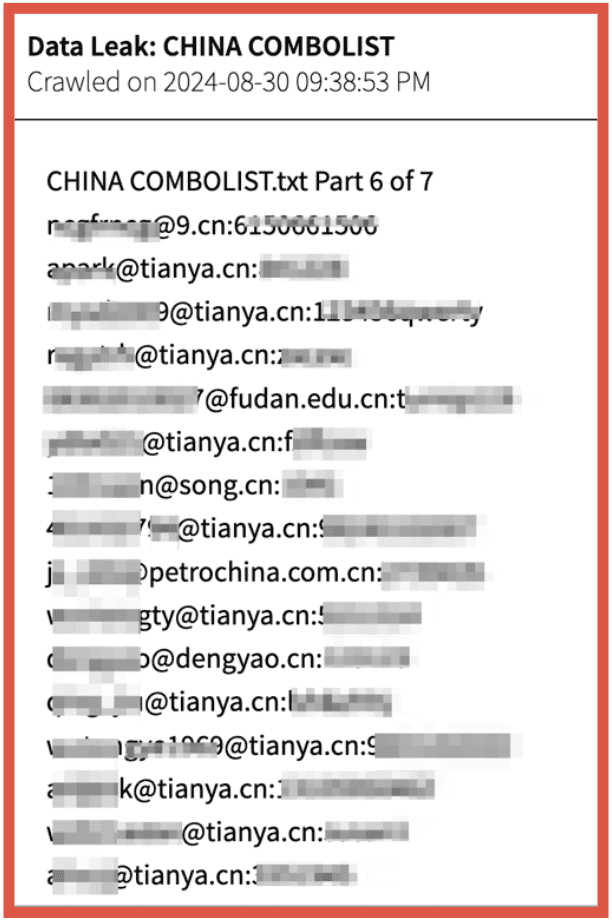
To the left we see an example of a combolist (a list of email addresses and password combinations that may be used in a brute force attempt or credential stuffing operations to gain unauthorized access to servers and services) that was leaked and posted on a darknet site. Databases from data harvesting will often include usernames and passwords, fullz (full identity profiles), financial records or health records. These are all often highly confidential or sensitive and can cause a lot of harm and headache when posted without consent.
Credential stuffing campaigns exploit password reuse and utilize email address and password combinations to attempt logins outside of the source of the original leak. Although you can’t prevent commercial services getting breached and usernames, email addresses, and password combinations getting leaked, you can follow some simple steps to ensure you employ robust password hygiene and reduce the risk of a password getting brute forced or exploited in a credential stuffing campaign. We review this steps later on in this blog.
Credential Stuffing in the Wild
The North Face
In a customer notice letter in June, The North Face revealed that on April 23, 2025, it was discovered that customer information was stolen in a credential stuffing attack. Exposed information includes full names, purchase histories, shipping addresses, email addresses, dates of birth, and phone numbers.
Hacking Forums Seized in “Operation Talent”
In January, the hacking forums Cracked[.]io and Nulled[.]to were seized following an international law enforcement operation dubbed “Operation Talent.” The joint operation involved law enforcement departments from the United States, Italy, Spain, Europe, France, Greece, Australia, and Romania. Additional impacted sites included starkrdp[.]io, mysellix[.]io, and sellix[.]io. As highlighted by CyberScoop, SellIX allowed users to create storefronts for illicit goods while StarkRDP—the remote desktop hosting service—“was allegedly leveraged by threat actors to anonymize attacks.”
The seizure of multiple major online forums linked to cybercrime reflects ongoing international law enforcement efforts to crack down on cybercrime by dismantling infrastructure used for illicit activity. Cracked[.]io and Nulled[.]to in particular were known for hosting cybercriminal activity, including “password theft, cracking, and credential stuffing attacks.” Similar large scale law enforcement operations have been observed in recent years, including the takedown of BreachForums in May, 2024.
New Atlantis AIO platform automates credential stuffing on 140 services
In March Bleeping Computer reported a new cybercrime platform called “Atlantis AIO” which automates credential stuffing attacks on over 140 online services. Atlantis AIO features modules for brute-force attacks, CAPTCHA bypass, and automated account recovery. It targets various services including email, e-commerce, banking, and VPNs. Compromised accounts are often sold on underground forums. To defend against such attacks, the article recommends using strong, unique passwords and multi-factor authentication, and for websites to implement rate limiting, advanced CAPTCHAs, and suspicious behavior monitoring.
Actor Spotlight: ShinyHunters
ShinyHunters is a cybercriminal group known for their high-profile data breaches and relentless pursuit of sensitive information, and has carved out a reputation as one of the most prolific and dangerous actors in the cybercrime arena. They are known to infiltrate company databases, exfiltrating sensitive information, and then selling this data on underground forums or using it for extortion purposes. They are not shy about sharing this information on dark web sites created to share exfiltrated data. ShinyHunters utilize advanced hacking techniques to gain unauthorized access to company systems. They often exploit vulnerabilities in web applications, engage in credential stuffing attacks, and use phishing campaigns to steal login credentials.
How to Avoid Being Exploited in a Credential Stuffing Campaign
Everyone can follow some simple steps to ensure you employ robust password hygiene and reduce the risk of a password getting brute forced or exploited in a credential stuffing campaign.
- Turn on multi-factor authentication (MFA) for important accounts like financial and banking sites.
- Use an automated complex password Manager like Lastpass, BitWarden, or 1Password.
- Don’t reuse passwords. Have unique password for every login and streaming service you sign up for.
- Choose passwords at least 16 characters in length.
- Include symbols and numbers for increased complexity.
- Avoid using passwords with dictionary words or names.
- Don’t use sequential numbers or the word “password”
- Don’t use the year of your birth or anniversary in your password.
Keep up with DarkOwl. Follow us on LinkedIn.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















