Content, Content, Content: Top Research Pieces from DarkOwl in 2022
January 03, 2022
Thanks to our analyst and content teams, DarkOwl published over 100 pieces of content this year, a new record for the team. DarkOwl strives to provide value in every piece written, highlighting new darknet marketplaces and actors, trends observed across the darknet and adjacent platforms, exploring the role the darknet has in current events, and highlighting how DarkOwl’s product suite can benefit any security posture. Below you can find 10 of the top pieces published in 2022.
Don’t forget to subscribe to our blog at the bottom of this page to be notified as new blogs are published.
1. Impacts of Ukraine Invasion Felt Across the Darknet
Beginning in February, the DarkOwl team actively tracked the fallout from Russia’s invasion of Ukraine, through April. The effects of the kinetic military operation caused ripples across the global cyber space including critical underground ecosystems across the deep and darknet, resulting in the first ever global cyberwar. Read blog.
In August, CEO and Co-Founder, Mark Turnage, hosted a webinar on the topic of cyberwar, “What Does a Real Cyberwar Look Like.” Ukraine’s call for help sparked off the first ever global cyberwar which for the first time in history has been waged between two countries simultaneously with a land war. This webinar looked at what we have learned from the cyberwar to date. The transcript and recording can be found here.
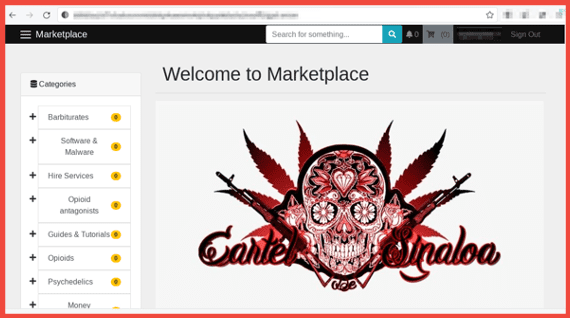
2. Darknet Cartel Associated Marketplaces
In August, DarkOwl analysts discovered multiple escrow-enabled decentralized marketplaces on the dark web that claim to be affiliated with the Sinaloa Cartel. One such marketplace called “Cartel de Sinaloa” is reportedly directly associated with the Sinaloa Cartel and Los Chapitos. Their marketplace uses the same logo – a red and black skull with “Cartel de Sinaloa” written underneath it – as the avatar of a Facebook group page operating with the same name. Another marketplace calling itself “The Sinaloa Cartel Marketplace” focuses on offering hitman for hire style services. Both services require authentication for user access, which forces visitors to create a username and password to view the marketplace past the login screen and adds protection from bots and crawlers. Read more.
3. Industrial Control Systems & Operational Technology Threats on the Darknet
Industrial control systems (ICS) and their adjacent operational technologies (OT) governs most everything societies rely on in the modern age. Manufacturing facilities, water treatment plants, mass transportation, electrical grids, gas, and oil refineries… all include some degree of ICS/OT incorporated in their industrial processes. Research from DarkOwl analysts identifies an alarming number of threats on the darknet and deep web that could effectively target and compromise Critical Infrastructure. Full report here.
4. Glossary of Darknet Terms
The darknet is home to a diverse group of users with complex lexicons that often overlap with the hacking, gaming, software development, law enforcement communities, and more. DarkOwl’s Glossary of Darknet Terms is a continually evolving resource that defines the common vernacular, slang terms, and acronyms that our analysts find in places like underground forums, instant messaging platforms (such as Telegram), as well as in information security research pertaining to the darknet. Check it out.
5. Pardon Me While I Steal Your Cookies – A Review of Infostealers Sold on the Darknet
In this research, our team reviewed some of the most widely proliferated infostealers on offer on the darknet and discovered an elaborate data exfiltration ecosystem, with low-entry cost, providing cybercriminals access to a wealth of personal information without the victim’s knowledge. We also learned many infostealers are offered in alignment with a malware-as-a-service (MaaS) or “stealer-as-a-service” (SaaS) rental model with subscriptions-based access to the malware executables and associated command and control C2 botnets. Read here.
6. Tensions Between China & Taiwan Realized on the Darknet
Through August and September, DarkOwl analysts took note of an increased amount of darknet activity surrounding the current geopolitical tensions between China and Taiwan. Using darknet, deep web, and high-risk surface web data, this report endeavors to shed light on the digital underground’s reaction to the countries’ political tensions stemming from China’s “One-China Principle” and its refusal to recognize Taiwan’s independence.
This report demonstrates how recent cyberattacks in August augment political criticism of Taiwan. Of particular note is the on-going barrage of leaks surfacing as a result of attacks against key organizations in both countries, and discusses the general darknet sentiment regarding China’s global reputation and their potential invasion of Taiwan. Full report here.
7. Understanding Darknet Intelligence (DarkInt)
The darknet (or “dark web”) is a thriving ecosystem within the global internet infrastructure that many organizations struggle to incorporate into security posture, but is becoming an increasingly vital component. In certain cases, that is because taking raw data and turning it into actionable security intelligence requires leveraging DARKINT – or data points sourced from the darknet and other OSINT sources that together form a risk and/or investigative portfolio. Learn more.
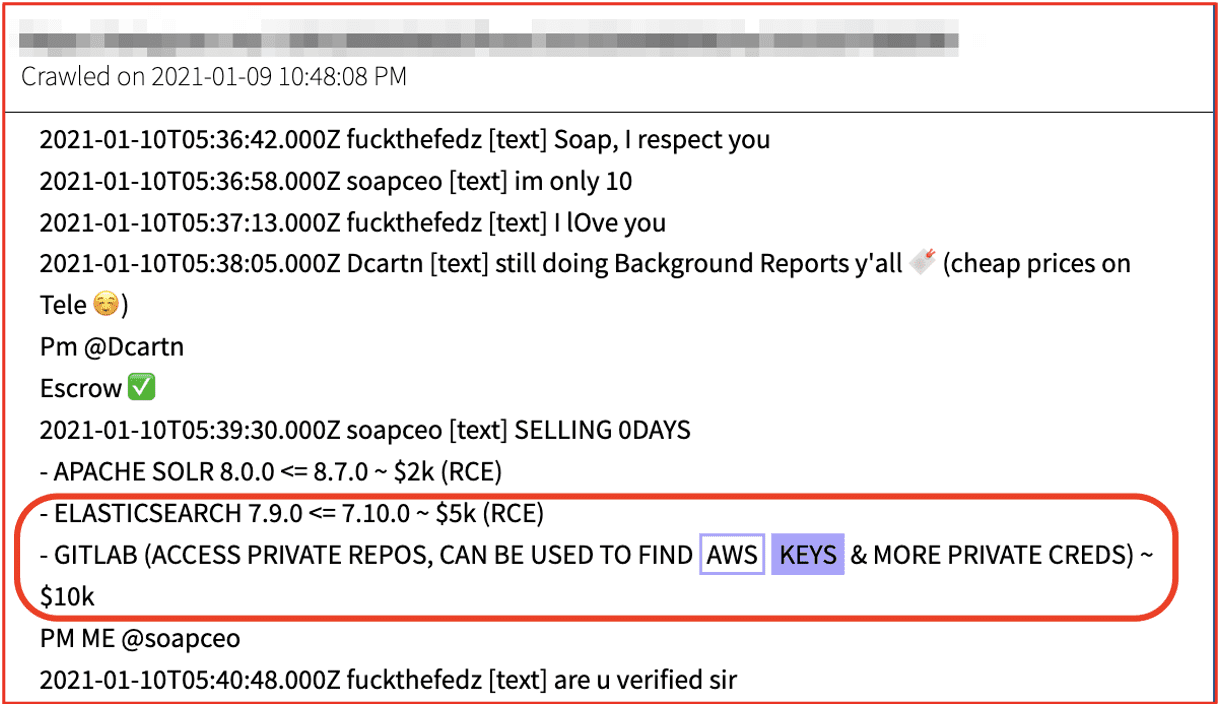
8. The Darknet Economy of Credential Data: Keys and Tokens
The darknet, which is also referred to as the dark web, is a segment of the internet that is only accessible by using specialized software or network proxies. Due to the inherently anonymous and privacy-centric nature of the darknet, it facilitates a complex ecosystem of cybercrime and illicit goods and services trade. Adjacent to the darknet is the deep web and instant chat platforms that play an increasing critical role in facilitating this illicit information availability. Pseudo-anonymous discussion forums and vendor marketplaces hosted on the deep web along with Telegram private and public channels provide additional platforms by which threat actors communicate and circulate sensitive and stolen credential data.
In this blog, we review how sensitive, server-side access credential data – such as AWS private/secret keys, Django secret keys, and API tokens – are captured, circulated, and sold across darknet marketplaces and criminal communities. Read here.
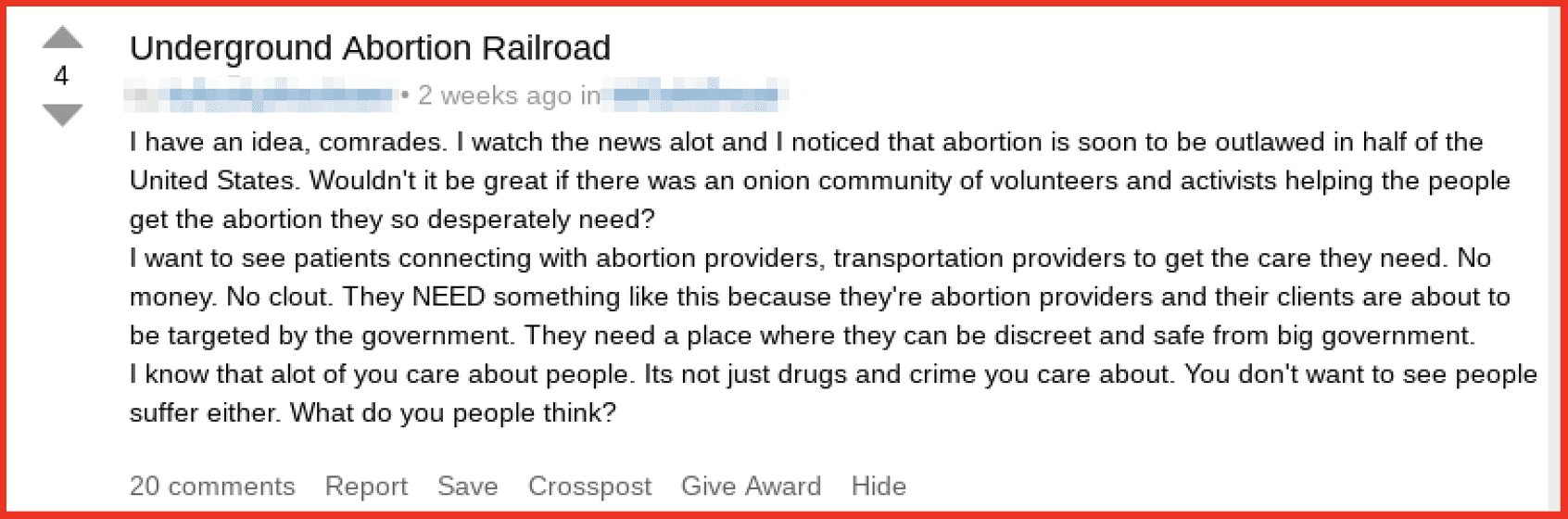
9. Darknet Economy Surges Around Abortion Rights
In June, users across darknet forums have voiced interest in abortion-related pills and services following the leaked Supreme Court documents and advocate for organized protests in support of and against the potential ruling. Once the U.S. Supreme Court officially issues their ruling, we anticipate a more concerted response from darknet marketplaces in offers for abortion related drugs and services. The darknet will also continue to be a resource for activists to organize political protests and circulate sensitive information related to the abortion debate. Read more.
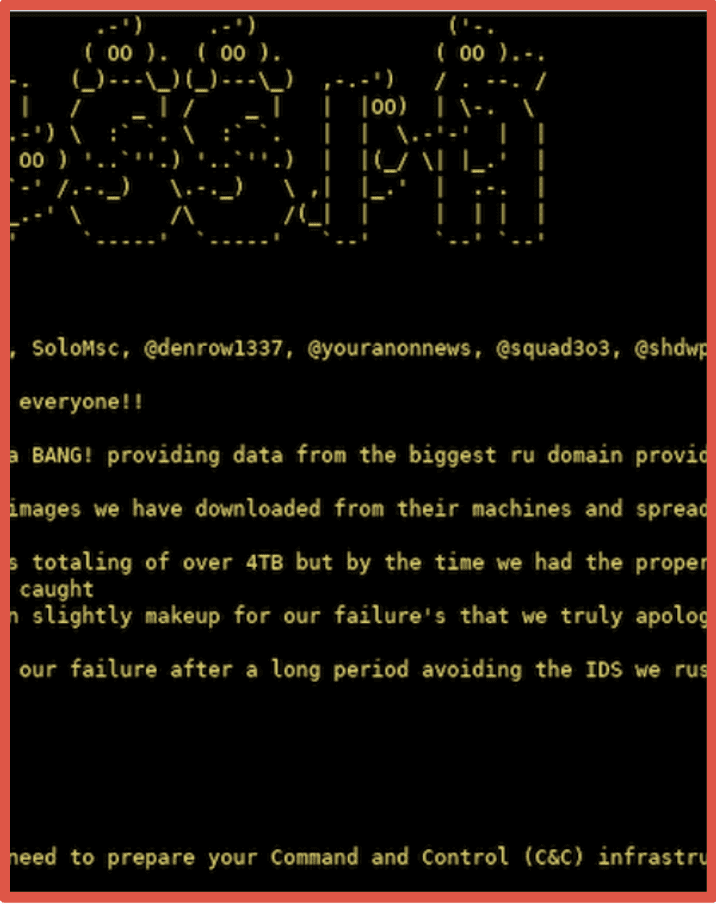
10. Dark Web Cyber Group Spotlight: SiegedSec
DarkOwl analysts regularly follow “darknet threat actors” that openly discuss cyberattacks and disseminate stolen critical corporate and personal data. Such analysis helps DarkOwl’s collection team direct crawlers and technical resources to potentially actionable and high-value content for the Vision platform and its clients. In this edition, analysts dive into SiegedSec, who formed in late February 2022, coincidently days before the invasion of Ukraine, adopted variations of the tagline, “sieging their victim’s security.” DarkOwl analysts observed SiegedSec provide proof of the defacement and/or compromise of at least 11 websites with rather juvenile and crude language and graphics included in the defacements. In April, the group claimed they had successfully defaced over 100+ domains offering proof of a hosting chat dialogue indicating the account passwords had been changed and the defacements corrected, but the group hinted they still had access to the domains. DarkOwl analysts also discovered several thousand compromised LinkedIn profiles with references to SiegedSec. Check it out.
2022, That’s a Wrap!
Thank you to everyone who reads, shares and interacts with our content! Anything you would like to see more of, let us know by writing us at [email protected]. Can’t wait to see what 2023 brings! Don’t forget to subscribe to our newsletter below to get the latest research delivered straight to your inbox every Thursday.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases