Dark Horizons: Will the Top Threats of 2023 Continue into 2024?
January 18, 2024
Introduction
Like the years before it, 2023 was busy in cyber security and the dark web with many attacks, emerging threats, and law enforcement activity. As technology becomes more and more entwined with our daily lives, the vectors for attack and the threats in the cyber realm increase, whether on a personal or corporate level everyone needs to be aware of emerging threats and how they can best protect themselves. As we enter 2024 it is important to be aware of what we are likely to face.
In this blog, DarkOwl analysts take a look at what we saw emerge in 2023 and review the most persistent threats which are likely to continue, grow in sophistication and make an impact in 2024.
Dark Web Activity
During 2023 on the dark web several marketplaces were taken down by law enforcement action and several threat actors arrested. However, new markets and actors emerged to take their place. When BreachForum was seized, and its administrator arrested, a Telegram channel and shortly after, a new site quickly took its place.
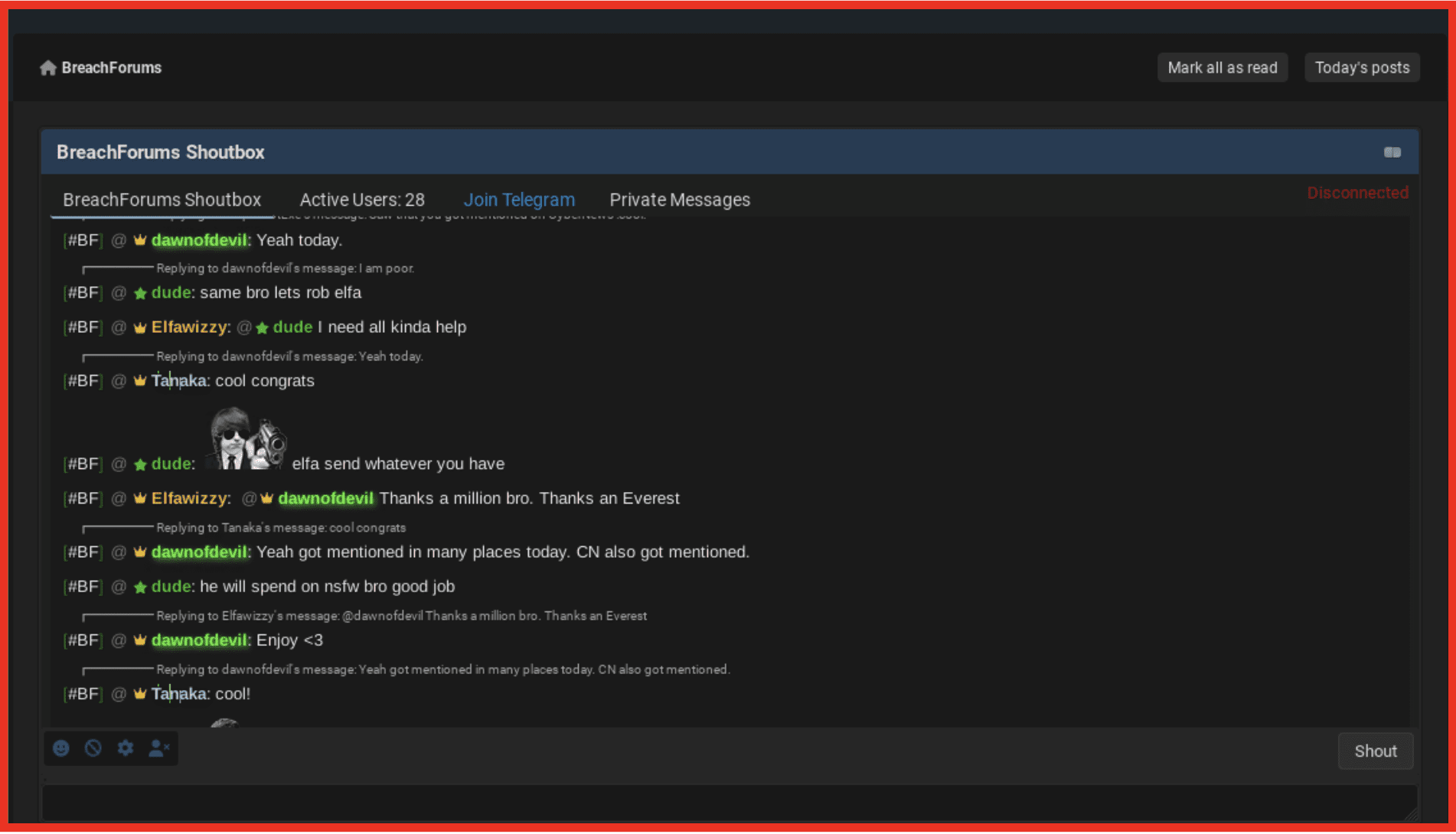
Figure 1 – BreachForums Shout Box
The dark web continues to be a place where threat actors can buy and sell illicit goods, discuss hacking activities, and share data and information to enhance their nefarious activities. This is not going to change in 2024.
Due to Law Enforcement activity, onion sites continue to increase their security and rules for participating on forums and marketplaces. The captchas have become increasingly difficult and outstrip those usually found on the surface web. They have also developed methodologies to make it more difficult to scrape the sites and require memberships. In 2024 DarkOwl expects these trends to continue as we work to ensure we can continue to provide coverage of these sites and the activity on them. It will be increasingly important moving forward to pay attention to the TTPs (tactics, techniques, and procedures) of threat actors on the darknet as their sophistication grows.
Messaging Apps
Over the last year, threat actors increased and affirmed their use of other means of communication such as Telegram and Discord. The messaging app, Telegram, has become a very popular means of communication particularly because of the company’s stance on cooperating with law enforcement, which they rarely do, and refusing to ban or removing content, with the only exception being posts which relate to Islamic extremist material.
While the use of Telegram was promoted by the Russia/Ukraine war, events such as the Hamas/Israel conflict in 2023 cemented their use, not only as a means of communication but also as a way of delivering news, both factual and not – what we call disinformation, with many using Telegram channels as a source of media. As we enter an election year in the US, and other countries, it is likely that Telegram will be extensively used to share political rhetoric from multiple sides and should be closely monitored.
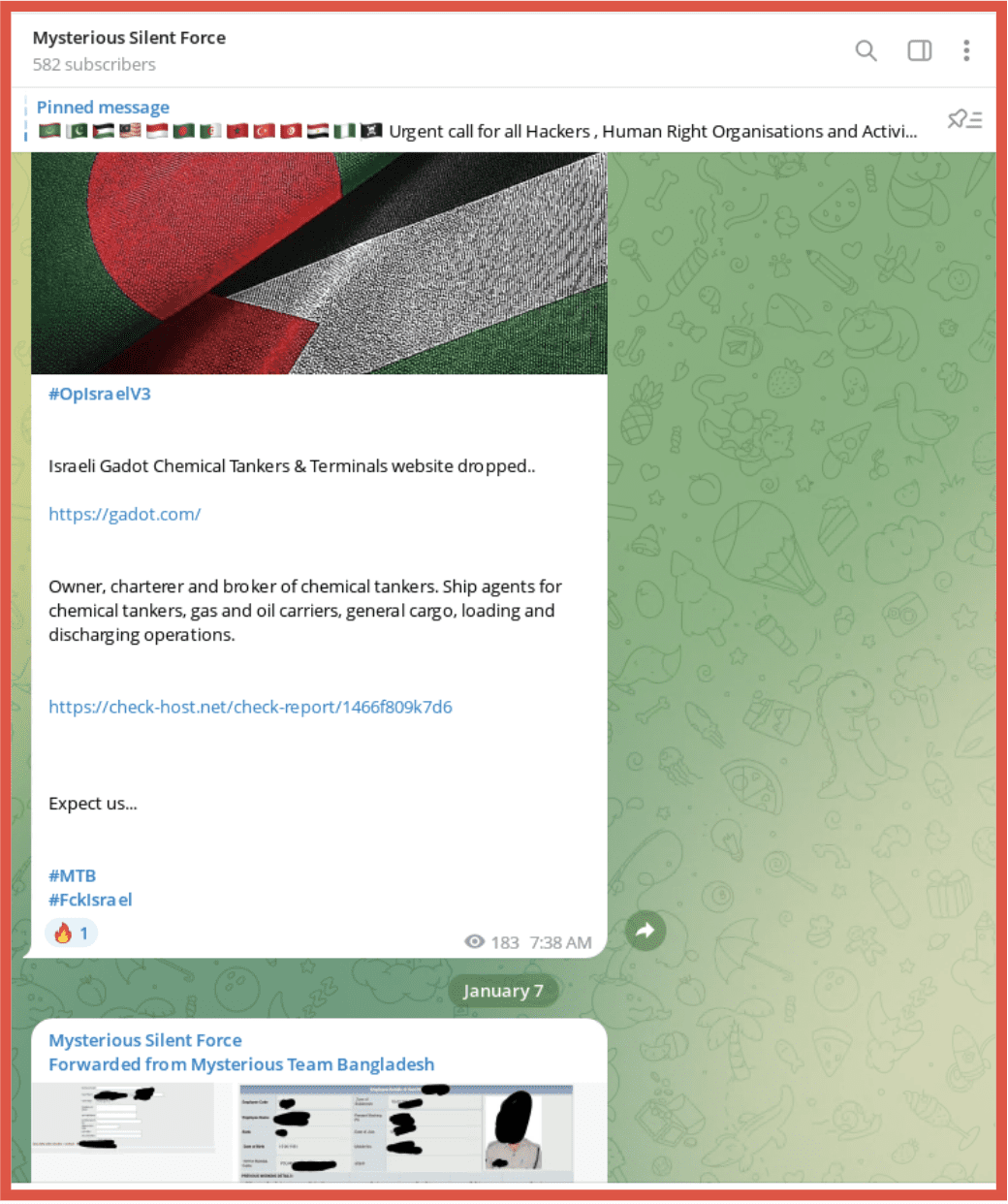
Figure 2 – Telegram Channel for Mysterious Silent force a hacktivist group supporting Hamas
Cyber threat actors, particularly hacktivist groups, have also used Telegram to publicize their activities, often naming victims or proposed victims and sharing victim data for others to download. DarkOwl continues to monitor Telegram for new and emerging groups and assess that the use of Telegram for the above purposes is likely to continue.
Discord had a turbulent 2023 – it was disclosed that sensitive US military information was shared on one of their servers. In reaction, they reviewed a number of their servers and closed those. They also closed any associated accounts that they deemed to be nefarious in nature. However, the gaming platform continues to be a popular place for threat actors and other individuals conducting nefarious activity to interact. DarkOwl will continue to monitor this in 2024.
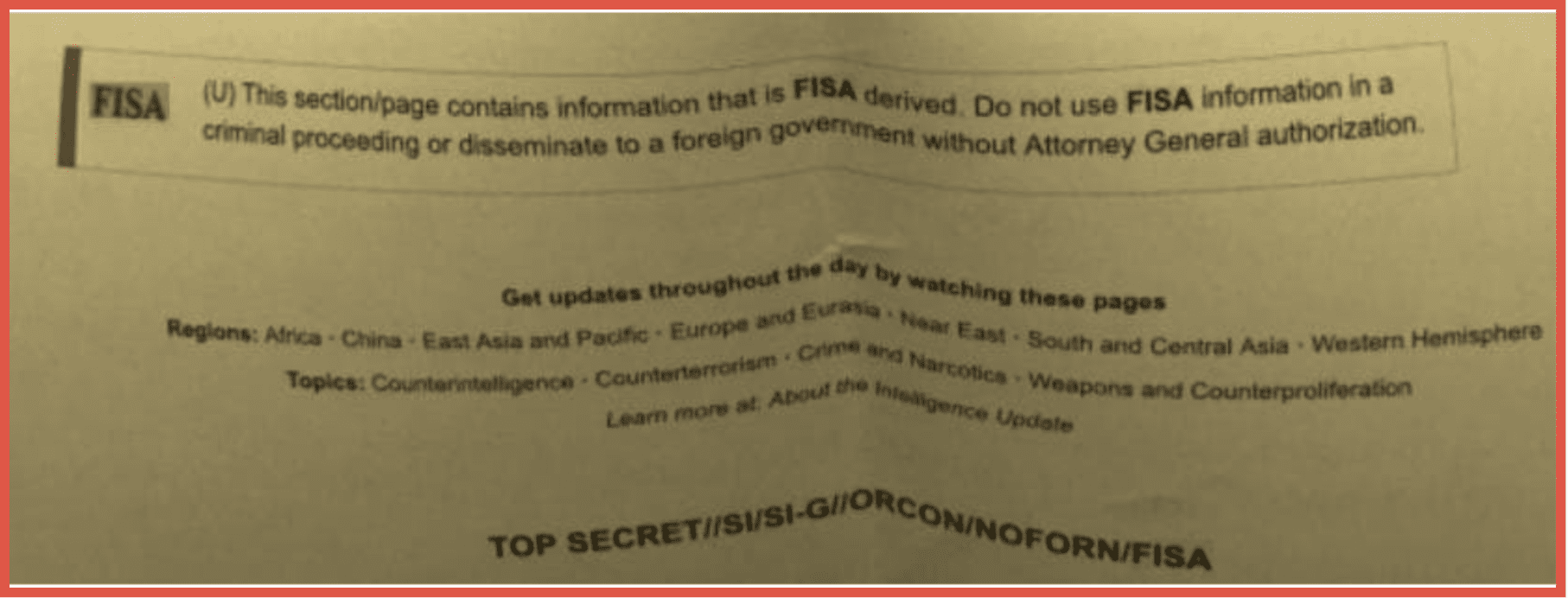
Figure 3 – Example of classified document shared on Discord
Ransomware
In 2023 Ransomware continued to be a huge threat, with 4671 attacks reported in 2023. Although some groups were disrupted, to varying degrees of success by both law enforcement and other threat actors, new groups emerged with new methodologies and techniques, and some could argue less “rules” with all organizations being “fair game” including healthcare and schools. It is expected that Ransomware attacks will increase in 2024 to unprecedented levels.
CL0P successfully utilized a zero-day vulnerability to target high profile victims, releasing their data on their dark web leak site. This provided an example of different techniques that ransomware groups can use successfully. The group were able to release data on a large volume of victims in a short amount of time, increasing their profile in the process. We assess ransomware groups (and all hackers) will continue to seek to exploit these types of vulnerabilities. Highlighting the need for a robust and secure supply chain.
Figure 4 – Header from CL0P leak site
Lockbit was by far the most active ransomware group in 2023, although they did not always receive the same coverage as other groups. The group was reported to have 1041 victims in 2023 – an increase of 304 from 2022. There is no indication that this group is slowing down, at the time of writing, the group had posted 9 new victims on their leak site – almost one for every day of the year so far. These groups will continue to be a threat into 2024 unless successful law enforcement action is taken.
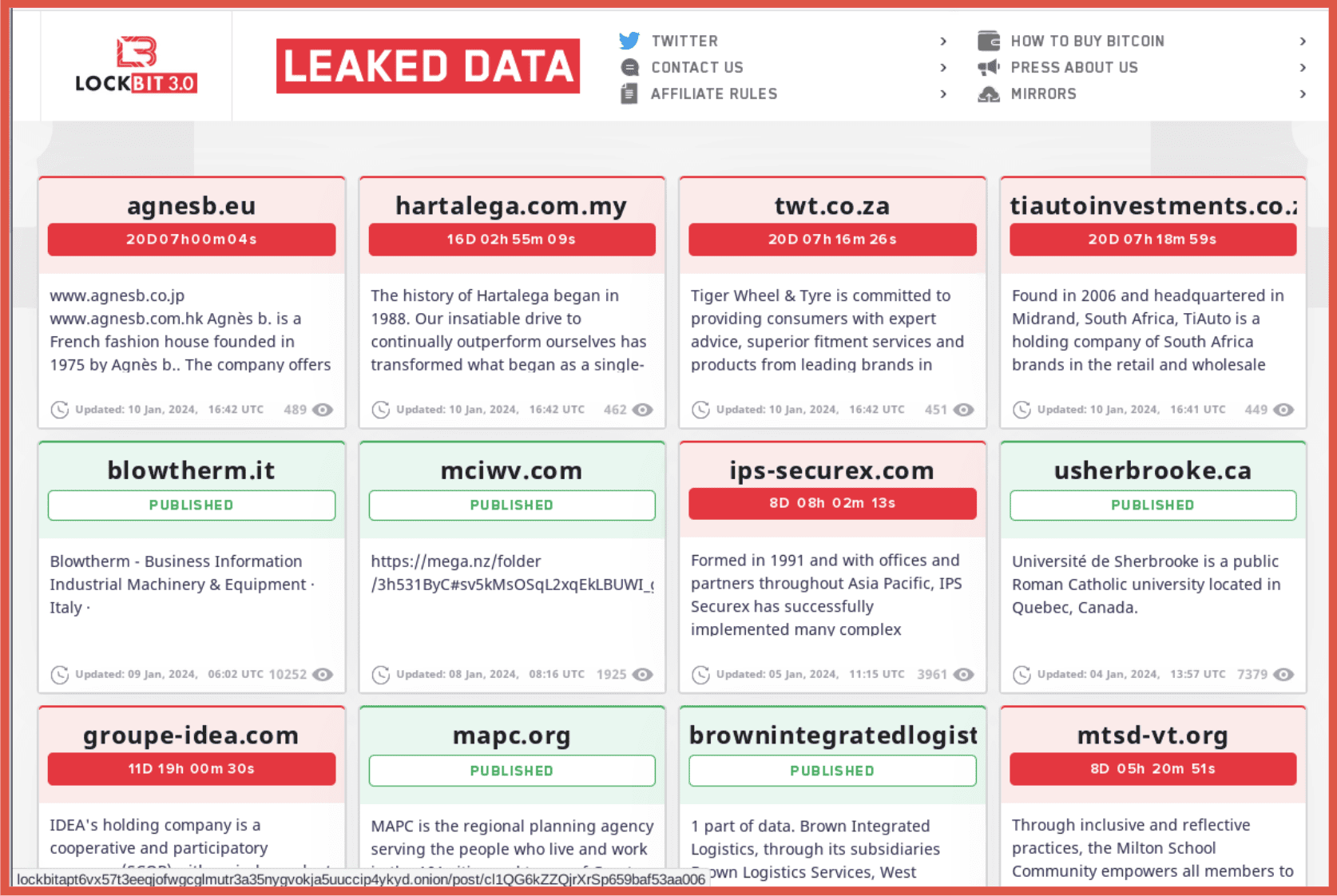
Figure 5 – Lockbit 3.0 Leak site
Although BlackCat/ALPHV appeared to suffer a disruption by law enforcement at the end of 2023 they were quick to bounce back with a new leak site and victims. This event highlighted the difficulties that law enforcement has in combatting ransomware groups, although infrastructure can be removed and decryptor keys released the groups are unlikely to be fully disrupted until the individuals are arrested, something that is not always possible given their geographical location. DarkOwl expects this to be a continuing frustration for law enforcement into 2024 which adds to the prediction that Ransomware will grow and continue to be a threat.
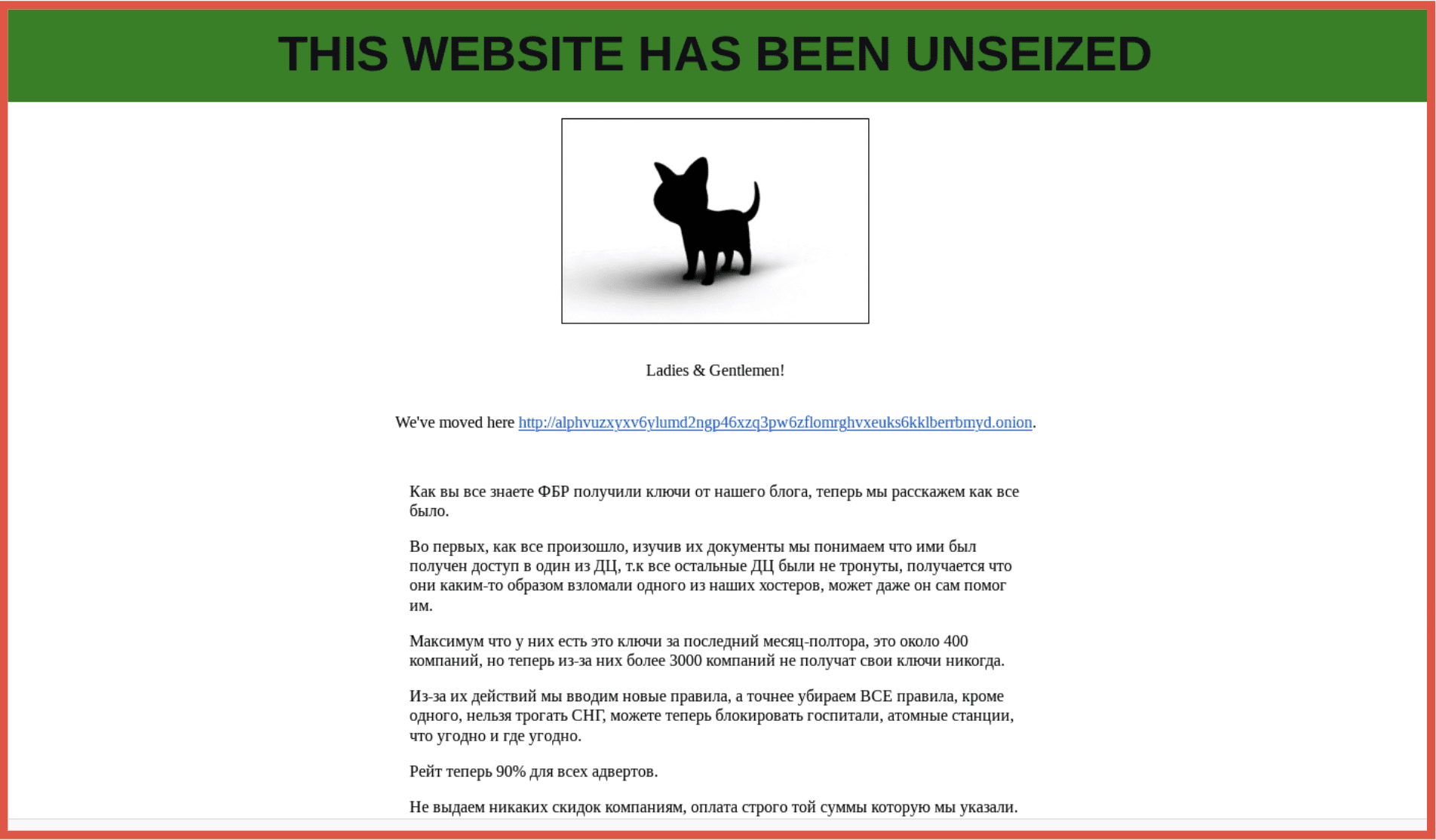
Figure 6 – BlackHat group take back their leak site and announce a new one
A trend which emerged in 2023 was double extortion being conducted by ransomware groups. However, more and more groups are emerging which simply manage extortion sites where they threaten to share data, without encrypting the companies’ data in the first place. This is a trend that is expected to increase in 2024. As decryption keys for common ransomware groups are released it becomes more costly for groups to develop new malware, high profile cases have shown that companies are willing to pay ransoms purely to stop it from being released into the public.
Credential Theft
Although it can be seemingly simple, credential theft continues to be one of the most common and lucrative methods of attack for threat actors. Stolen credentials can cause varying degrees of damage depending on who they belong to – from the loss of streaming service accounts to identity theft to network access and ransomware attacks. If individuals continue to reuse passwords, and or companies do not implement robust password policies, this will continue to be a threat. Because of this, DarkOwl analysts assess that this will continue to be a major threat in 2024.
In order to combat this crime, DarkOwl’s team continues to collect data leaks to allow organizations to identify potential risks that they are exposed to. The fallout from the 23&Me data leak in late 2023 highlighted that the risks are not just that threat actors may be able to access data, but companies are increasingly suffering large fines from regulators and lawsuits from those whose data has been stolen – increasing the risk that organizations face from data breaches.
Figure 7 – Redline Stealer Log Header
DarkOwl also expects that the selling and trading of Stealer Log information will continue throughout 2024. These logs allow threat actors to capture credentials, cookies and user agents for victims which can be used to mount attacks and steal accounts. The close to real-time nature of these logs ensures that the credentials are usually still active, increasing the success rate the threat actor is expected to have means that they are very profitable for those selling them on the dark web. DarkOwl will continue to monitor and collect this information where available.
Islamic Extremism

Figure 8 – Inspire Magazine Header
Likely linked to the ongoing conflict in Gaza, we have begun to see an increase in material linked to Islamic Extremism. In early 2024 AQAP revived the English-Language ‘Inspire’ magazine in video format. The video stated that “it is time to avenge Gaza” and provided instructions for building a ‘Hidden Bomb’ for targeting American planes, Bill Gates, and Elon Musk. Although not strictly a cyber threat, ISIS and AQAP have previously utilized online methodologies to incite violence and attract and radicalize followers. DarkOwl assess that this will continue with tensions rising in the Middle East. Our analysts continue to monitor these groups and their activities.
A.I.
Another theme of 2023 was the rise of AI with Chat GPT and Bard, among others, being released and adopted by many. Threat actors also began to adopt this technology to assist them in their attacks. As the technology matures, we expect this to be used more extensively by threat actors in 2024.
DarkOwl have seen actors selling access to AI accounts and also providing training on how it can be used to conduct attacks such as producing more believable and sophisticated phishing emails, as well as generating images which can be used for fake IDs used to circumvent financial institutions know your customer (KYC) policies. There are likely to be many other ways in which AI can be used to conduct malicious activities. DarkOwl will continue to monitor this throughout 2024.
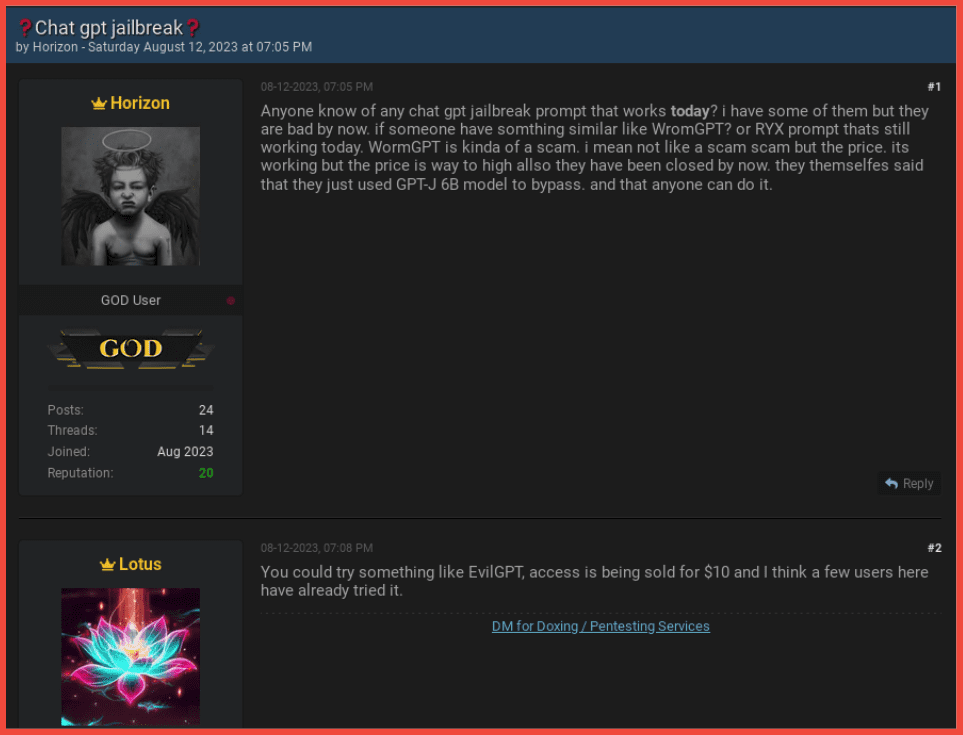
Figure 9 – Breach Forums users discuss jailbreaking ChatGPT
APT Groups
APT groups will always pose a threat. They tend to be well funded and sophisticated in nature and can be very hard to detect and disrupt, meaning that while they may have periods of apparent inactivity, they are unlikely to disappear, usually emerging in a slightly different configuration.
As geo-political tensions continue, with wars in the Middle East and in Ukraine, Iran and Russia are likely to be very active in 2024. Elections will also likely illicit disinformation campaigns and other attacks seeking to influence the outcome.
However, the country likely to pose the largest and most persistent threat is China. China has been attributed to a high volume of attacks with a range of sophistication and it is likely that this will continue. The Director of National Intelligence stated, “China probably currently represents the broadest, most active, and persistent cyber espionage threat to U.S. Government and private-sector networks.” This highlights the threat the US government believes China poses in the cyber realm. It is likely we will see attacks from them throughout 2024.
Conclusion
2024 is likely to be a busy year for Cyber Security professionals and Threat Intelligence Analysts.
In 2023 the world witnessed over 50 ongoing real-world conflicts, as estimated by the UN. Conflicts now inevitably include a cyber element whether that be through attacks, disinformation campaigns or recruitment campaigns and so we are likely to see activity related to these conflicts. Furthermore, many countries will be holding elections this year which are likely to be marred by disinformation and claims of election fraud which are likely to also have a cyber element.
The threats of ransomware and credential theft will also feature heavily in the 2024 landscape and companies and organizations should be prepared for the threats that they pose. Monitoring the dark web to identify these activities can help organizations to better position themselves for the threats that will emerge in 2024.
DarkOwl is committed to researching and providing updates throughout 2024. Don’t miss any of our research.
Explore the Products
See why DarkOwl is the Leader in Darknet Data
Products
Services
Use Cases















