Data Privacy Day: Why It Matters More Than Ever
January 28, 2025
Data Privacy Day, observed annually on January 28, is a global effort to raise awareness about the importance of data privacy and safeguarding personal information. As our lives become increasingly digital, the relevance of protecting personal data has never been more crucial. Whether you’re an individual managing your online presence or a business handling sensitive customer information, understanding data privacy is vital, as well as understanding the risks that are posed to you or your organization when your data privacy is breached.

The History Behind Data Privacy Day
Data Privacy Day traces its roots to the signing of Convention 108 in 1981, the first legally binding international treaty dedicated to privacy and data protection. It began in Europe and later gained global recognition, evolving into a day for reflecting on data practices and empowering individuals and organizations to protect their information. Laws have also been created in both Europe, with GDPR, (General Data Protection Regulation) and in the US such as CCPA (California Consumer Privacy Act)., which means that organizations need to comply and ensure that they are not only protecting their own data, but any data they come into contact with which may belong to others such as customers or employees.
Why Data Privacy Matters
Preventing Identity Theft
Personal data breaches can lead to identity theft, financial fraud, and other cybercrimes. In 2023 alone, millions of people suffered from scams due to compromised personal data. These types of attacks can be devastating and cause untold financial hardships.
Personal Risk – Social engineering attacks
Exposed data can be used to build a picture of an individual which can then be used to inform social engineering attacks which can lead to further data loss and reputational damage. Furthermore, providing too much data about yourself can leave you open to physical risk, such as doxing attacks or stalking.
Building Trust in Digital Spaces
For businesses, trust is currency. Transparent data practices help companies build customer loyalty and comply with regulations like GDPR and CCPA.
Enabling Informed Choices
When individuals understand how their data is collected, stored, and used, they can make informed decisions about the digital platforms they engage with. Arguably social media companies and advertising agencies hold more data on us than governments. It is important to know how our data is collected, stored and used by these organizations.
Protecting Personal Freedom
Data privacy is not just about securing information; it’s about preserving freedom. Unauthorized data collection and surveillance can infringe on fundamental human rights, such as freedom of expression and association.
How to Observe Data Privacy Day
Educate Yourself
Take time to learn about your rights concerning data privacy. Resources from organizations like the Electronic Frontier Foundation (EFF) or the International Association of Privacy Professionals (IAPP) can be helpful. Also understand the best way to protect your data and your organizations data.
Review Privacy Settings
Audit your social media and device settings to ensure you’re only sharing information you’re comfortable with. You should always have strong privacy settings so only those you want to see your data can. Also think before you post, do not post personal information online or share locations.
Enable Multi-Factor Authentication
Strengthen your online accounts by adding extra layers of security. Using an app is better than using text messages which can leave you open to OTP attacks. Also ensure you use a password manager so that you use a different password for each account. This way if data for one account is compromised it will not affect your other accounts.
Advocate for Privacy in Your Workplace
Encourage your organization to adopt robust data protection policies and provide training for employees. And make sure you practice what you preach!
Know what data has been exposed
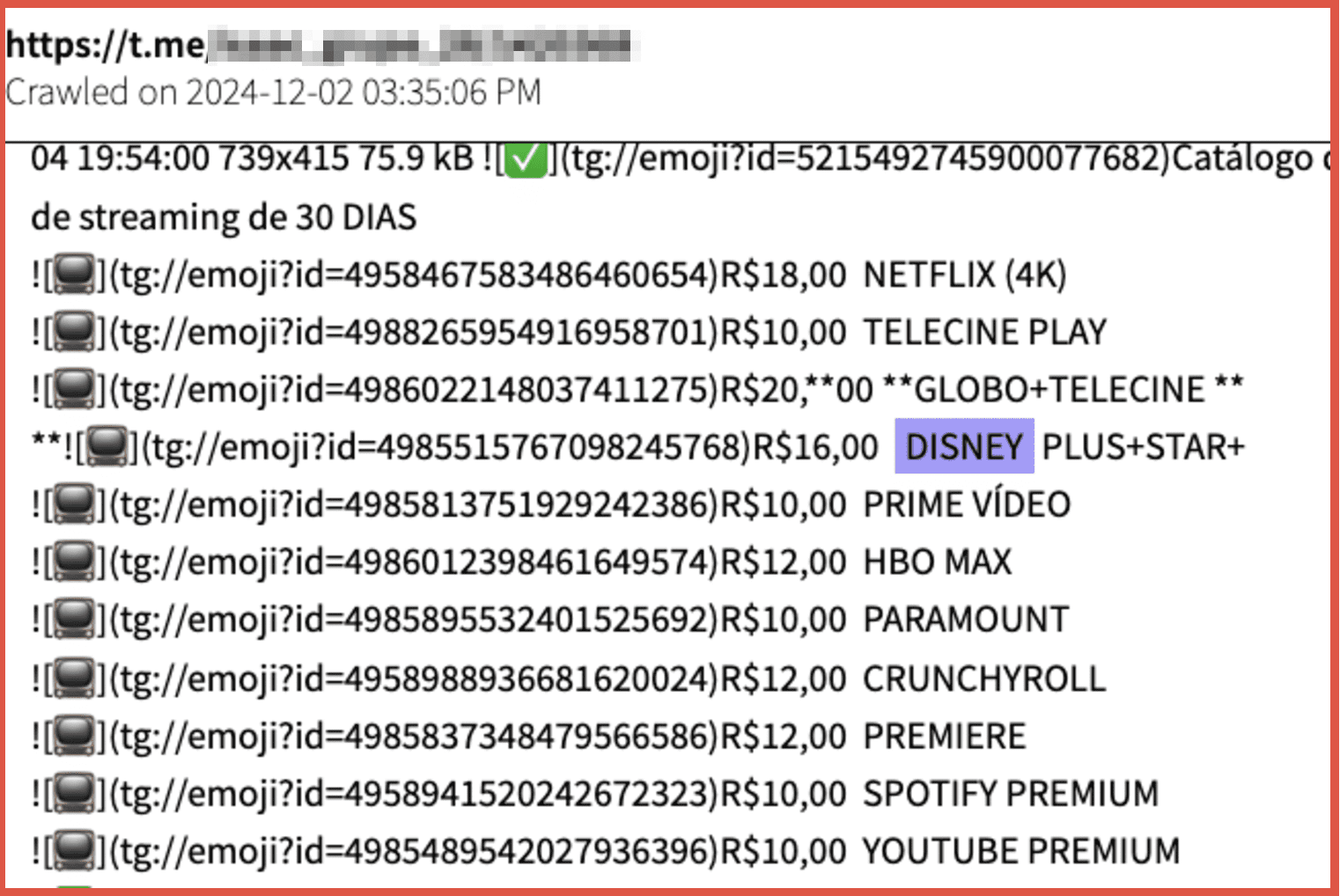
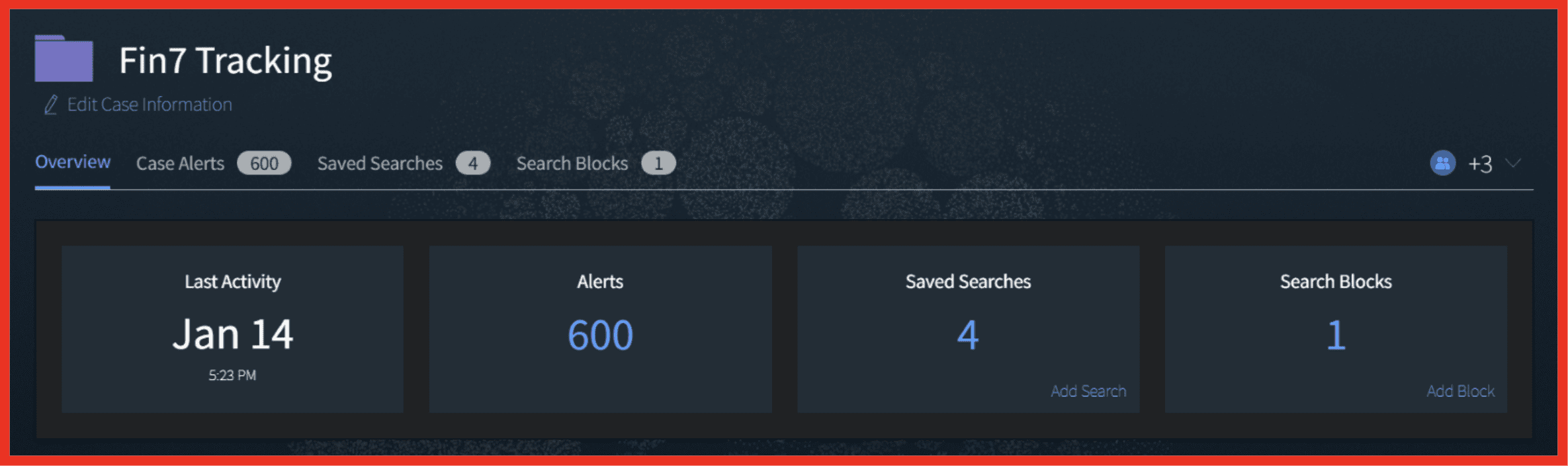
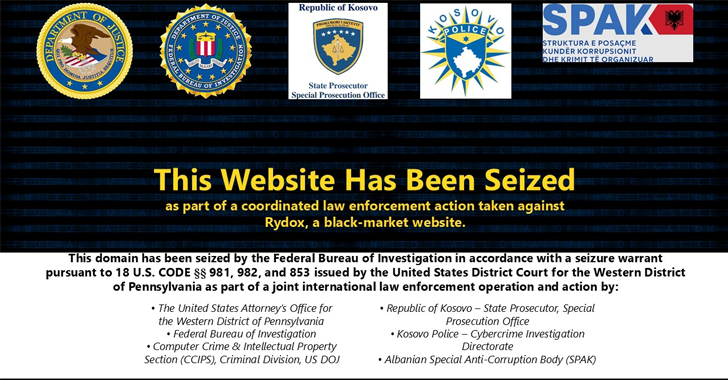
Ensure that you are aware if any of your data has been exposed and what actions you can take to prevent the data loss having an impact on you. DarkOwl will provide monitoring to alert you when your information appears in a breach.
Emerging Trends in Data Privacy
AI and Privacy
As artificial intelligence becomes more integrated into daily life, concerns about how AI systems process and store data are on the rise. These systems are built on data models and therefore data is at the heart of how they work. It is not just an issue of how they store data but what data they use to train their models. There are copyright and plagiarism concerns. But in a world where our images and our voices can be used we must expand what we view as “our” data.
Data Sovereignty
Countries are increasingly advocating for localized data storage and processing to enhance national security and privacy. Concerns are raised when data is held in countries which do not have strong privacy laws and how that data might be used
Biometric Data Protection
With technologies like facial recognition and fingerprint scanning becoming common, safeguarding biometric data is becoming a top priority.
Conclusion
Data Privacy Day is a reminder that protecting our personal information is a shared responsibility. As individuals, we need to stay vigilant about our online presence, and as a society, we must demand accountability and transparency from governments and corporations. Together, we can create a safer digital world where privacy is respected, and trust is earned.
This Data Privacy Day, take a moment to reflect on your digital habits and make a commitment to safeguarding your privacy—and that of others. After all, in an era where data is the new oil, protecting it is protecting ourselves.