August 15, 2023
With just a few keystrokes, a malicious actor can gain access to a network, determine the scope and worth of information available, and then steal and encrypt the data, preventing access to it. Organizations have hopefully prepared themselves for these kinds of cyber incidents, known as ransomware attacks, by having an up-to-date system backup from which they can restore data and continue operations. Despite business continuity suggestions and planning advice, backups are still not a regular entity despite how common and how popular ransomware attacks have become in the past decade. Even changes from one year to another witness more stealth movement and larger impacts in the ransomware ecosystem.
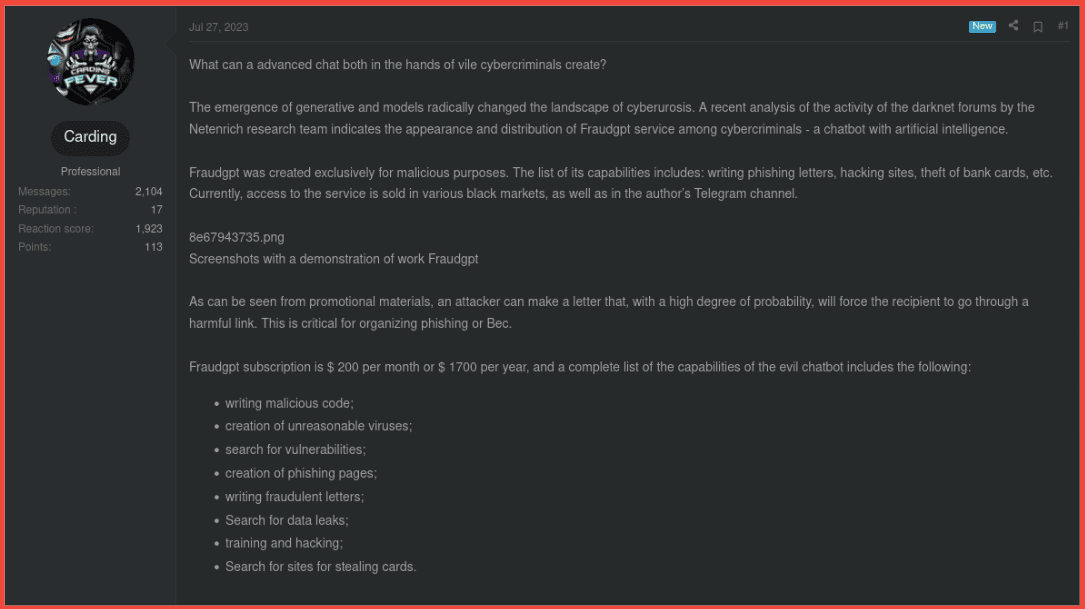
Ransomware’s explosion has been sustained for years. As tech advances, so do the actor tactics, techniques, and procedures (TTPs). Heading towards the final quarter of the year, it is imperative to explore the 2023 mindset of ransomware actors: They are pursuing “target rich, cyber poor” industries that will make them money by selling data, exploiting the victims they target, the partners and third-party services linked to the victims, and infiltrating supply chains. While double-, triple-, and quadruple- extortion practices are still around, actors are also adapting/changing their encryption processes to better emulate protective services such as anti-virus and file scanning software to blend in and provide no red flags to technical and cyber practitioners. This allows for a long-term, stealth presence in networks which facilitates lateral movement to collect as much information as possible.
Ransomware is quickly evolving, and it is imperative to pay attention to its trends and try to get cyber practitioners, government, law enforcement (LE), Computer Emergency Response Teams (CERTs), and more collective bodies to take strides towards prevention and disruption of ransomware groups. With the use of artificial intelligence (Al) and internet of things (IOT) growing, the attack surface is larger than ever and must be addressed. Private and public partnerships (PPP) are one of the most effective ways to share intelligence and indicators of compromise (IOCs) to combat ransomware as the holistic problem it is.
Key Findings:
- 2023 ransomware profits are up as of the middle of the year
- This profit margin is expected to increase
- Multi-extortion layers and techniques are more common, and this is expected to continue throughout all ransomware operations
- As groups are caught by law enforcement or shut down to preemptively avoid legal actions, they are recruited into other groups and share expertise, tools, and TTPs
2022 Compared to 2023
Ransomware is a cybercrime phenomenon impacting every industry, large and small. Additionally, there is a “hacktivist” angle to ransomware incidents, accompanying the criminal faction. Fringe groups are using the easily available ransomware as a service (RaaS) market to procure simple ransomware kits and then go attack. The 2022 Conti leaks showed the world that ransomware organizations are operating more like businesses than criminal groups, well-funded and organized. Furthermore, after Conti’s decline, more organizations are witnessing splinter groups and “copycat” actors, working together to have a maximum impact spreading ransomware and gaining profit and data.
January 2023 saw the highest number of ransomware incidents ever reported for the month of January, with 33 reported incidents. The unreported incidents must also be considered: Organizations often choose to keep cyber incidents private, and malicious cyber actors don’t keep the most trustworthy stats and data. In July of 2023, data emerged demonstrating that 2023 is on track to be the most active ransomware year per reported incidents. According to some reviews, actors have already made ~$450 million dollars up to June 2023, and are on track to make approximately $900 million dollars if the rate of attacks continues through the second half of the year.
Ransomware incidents are expected to continue at a high pace, especially as hacktivists all over the world side with their chosen nation, government, or ideoloqv and then proceed with the intent to attack an organization who differs from the chosen ideology. This is in addition to technology trends like cloud computing and the IOT space increasing access points and increasing the overall attack surface area, allowing malicious actors more opportunities to enter a network. Available payment data for 2023 also indicated that ransomware is the only criminal market that saw an increase in profit while scamming, malware, and fraud operations all witnessed a decline in profit and revenue.
Changes in TTP: Extortion at Entry Level
Much like the cybersecurity industry changes and adapts to protect and defend, ransomware actors also change and adapt to remain effective and profitable. A focus on continued extortion techniques, higher profitization and a surprising change to encryption practices all emerged in 2022 and 2023 and are expected to continue throughout 2023 and into 2024.
Traditional ransomware incidents involve unauthorized access to a system where actors steal sensitive data, encrypt it, and demand money from the victim for restored access. There is a new level of harassment implemented by ransomware actors, making their attacks multi-layered and more impactful: Extortion.
Double, Triple, and Quadruple Extortion
With double extortion, ransomware actors conduct a traditional attack and encrypt data. However, if an organization restores their data from a backup and does not pay the ransom, the actors then threaten to sell it on criminal forums, sell it through a bidding process, or permanently prevent access to the stolen data if there is no payment. This way, the reputation of the organization still suffers when it is revealed there was a security incident. Actors demand payment to keep quiet about the incidents if the organization can salvage data access on their own.
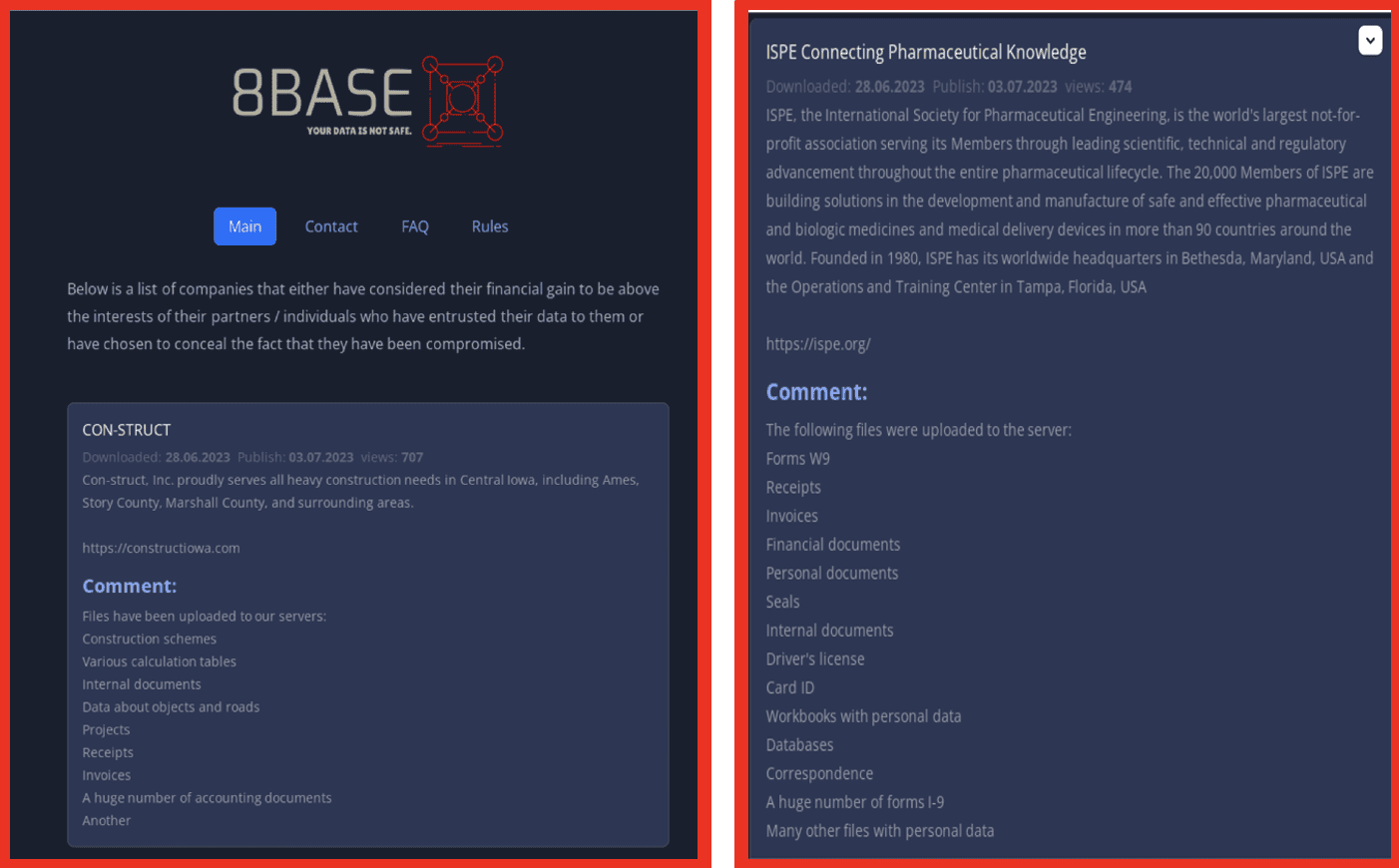
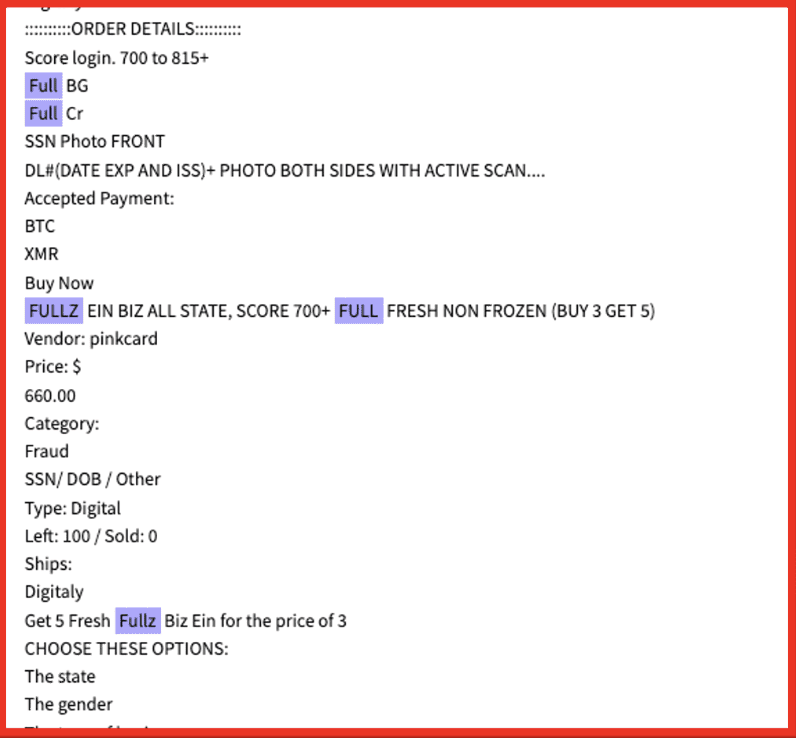
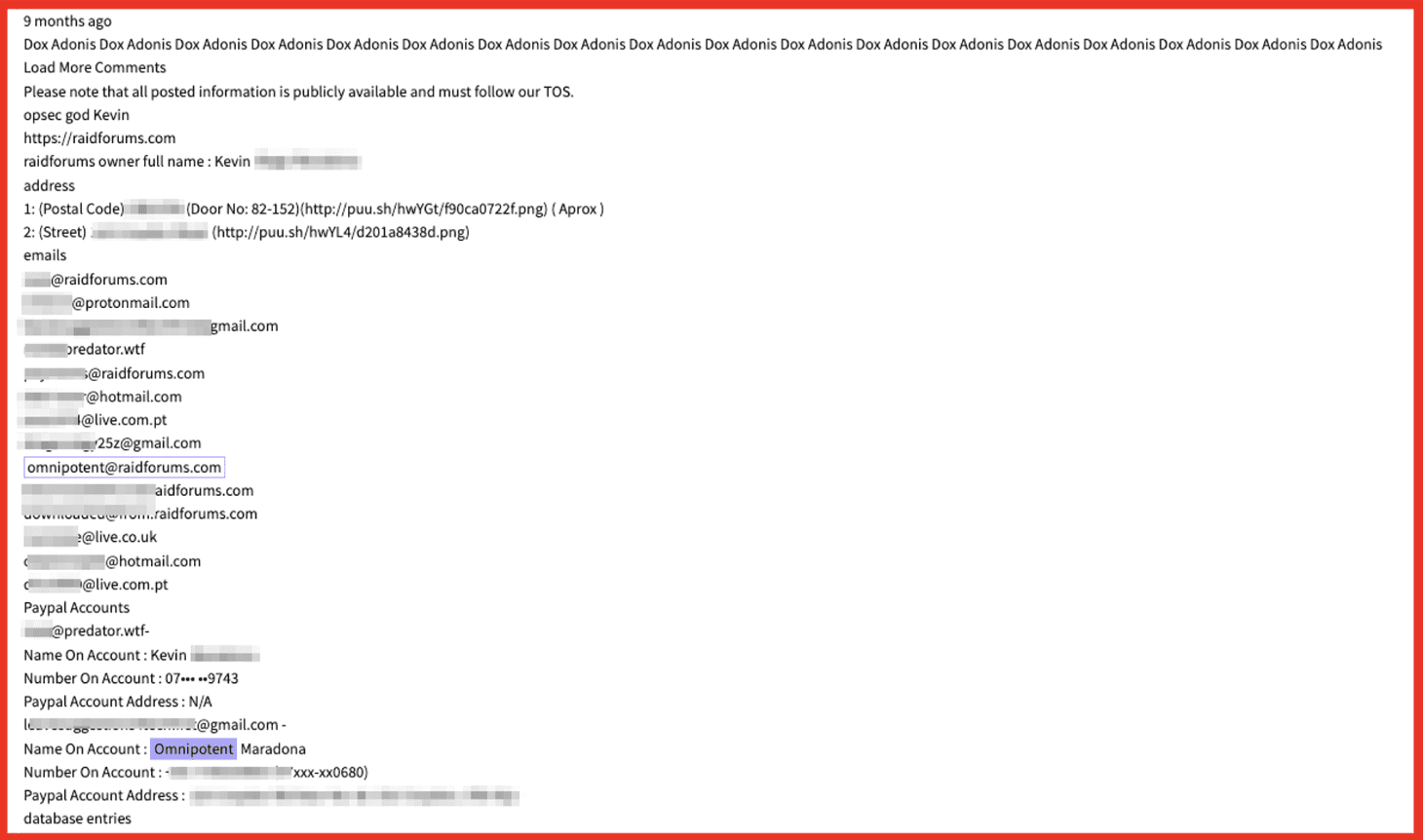
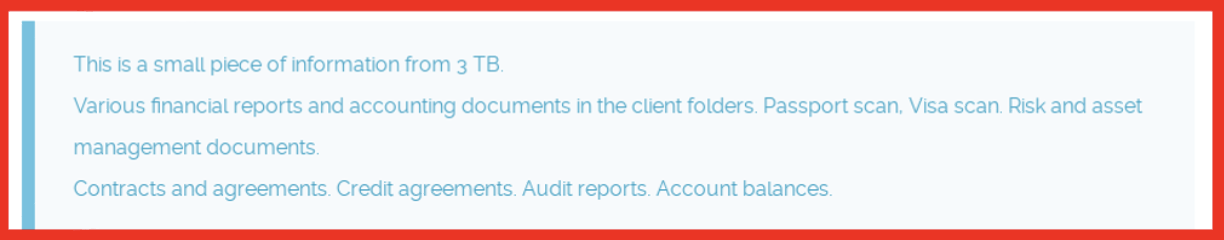
As of June 2023, Base ransomware gang operated a prolific double extortion ransomware campaign. They listed victims from the legal, pharmaceutical, medical, agricultural, and many other sectors on their website:
Figure 1: Source: Base8 ransomware’s onion site
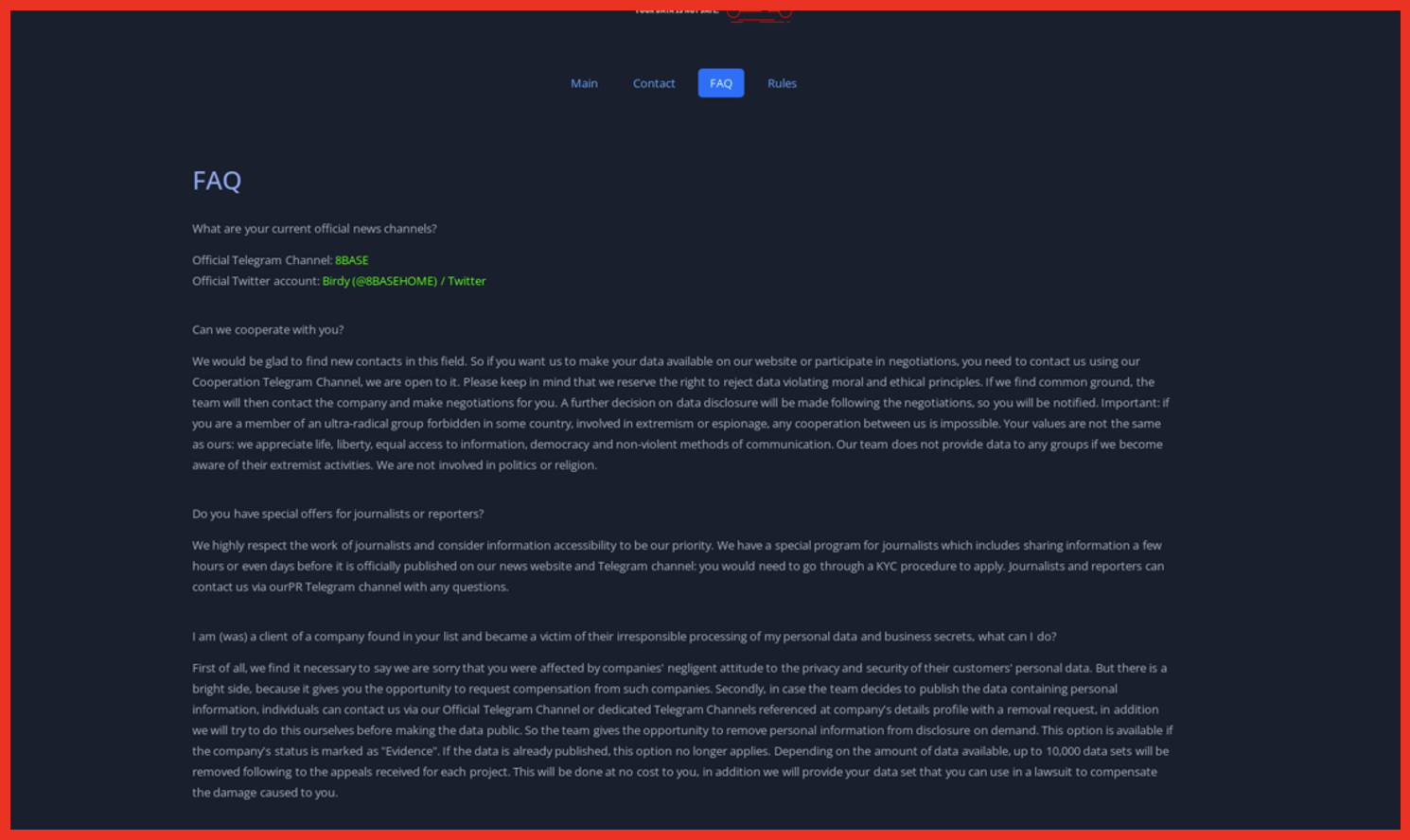
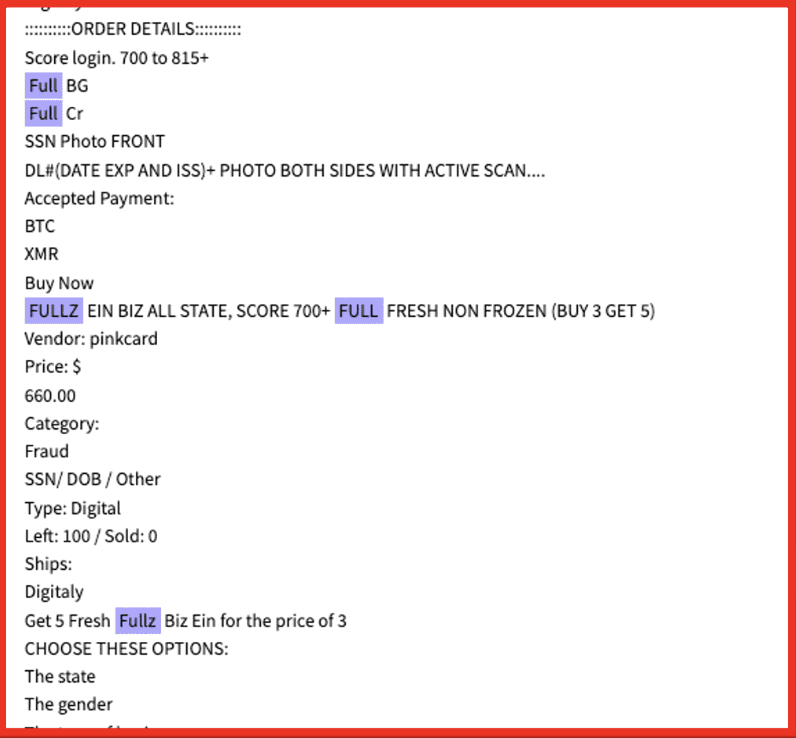
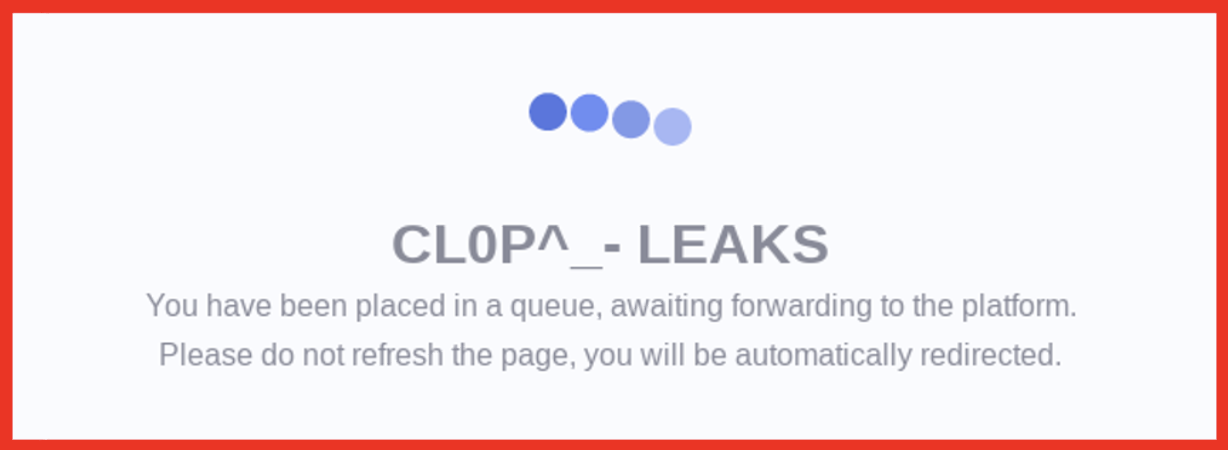
Demonstrating the continued organizational efforts of ransomware groups, 8base also offers their contact information, a FAQ section, and a detailed rule section for their victims. This continues to prove the developing professional and organizational caliber of ransomware groups, which was previously revealed as Conti’s efforts and business acumen was detailed in 2022:
Figure 2: Source: Base8 ransomware’s onion site
Figure 3: Source: Base8 ransomware’s onion site
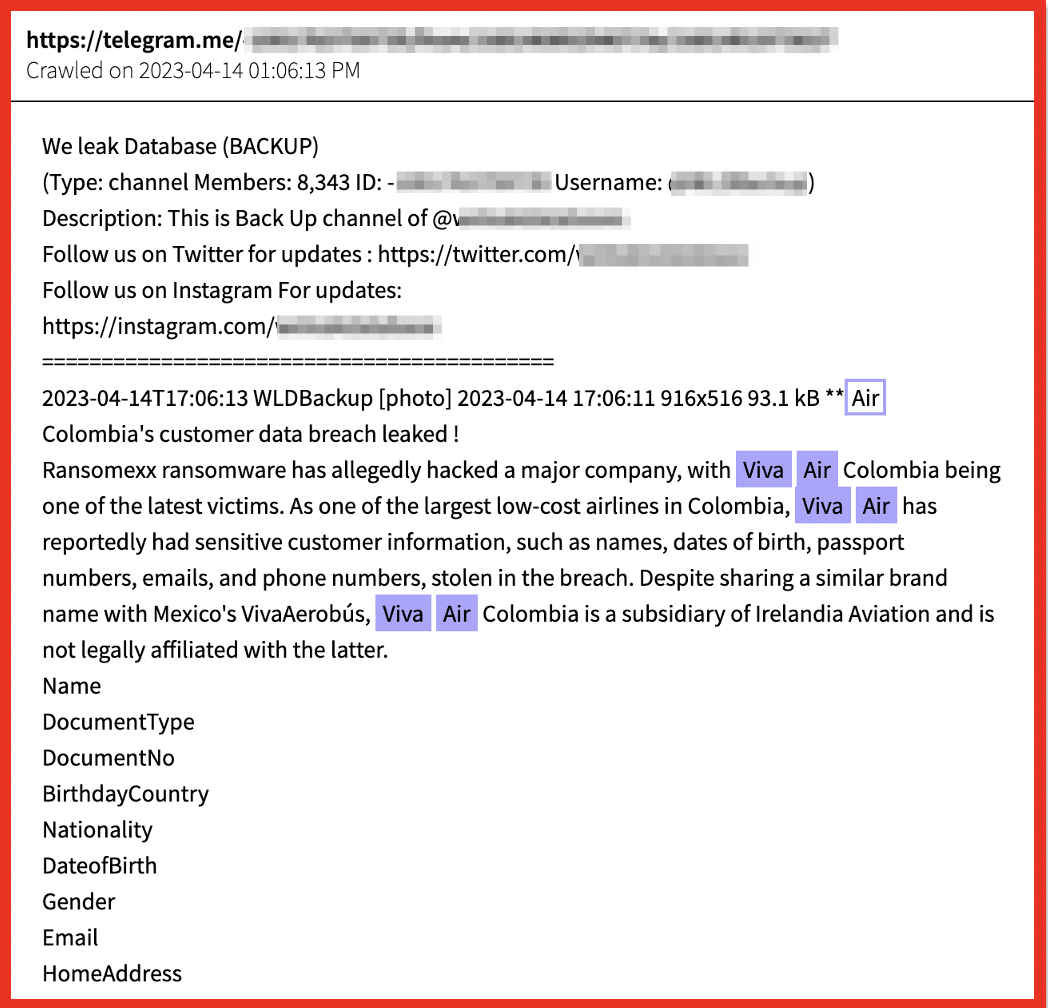
8base’s operations reveal another trend: A pivot from procuring personally identifiable information (Pll) operations only, and going after blueprints, sensitive documents of physical layouts for buildings, and those related to critical infrastructure and key resources (CI/KR). Ransomware is no longer just about getting and selling Pll; now, more sensitive documents are stolen and sold on DDW forums. This is a hybrid security issue, both physical and digital. Ransomware gang Cl0p, who has made headlines in 2023 for penetrating hundreds of organizations, is also a prolific double extortion group.
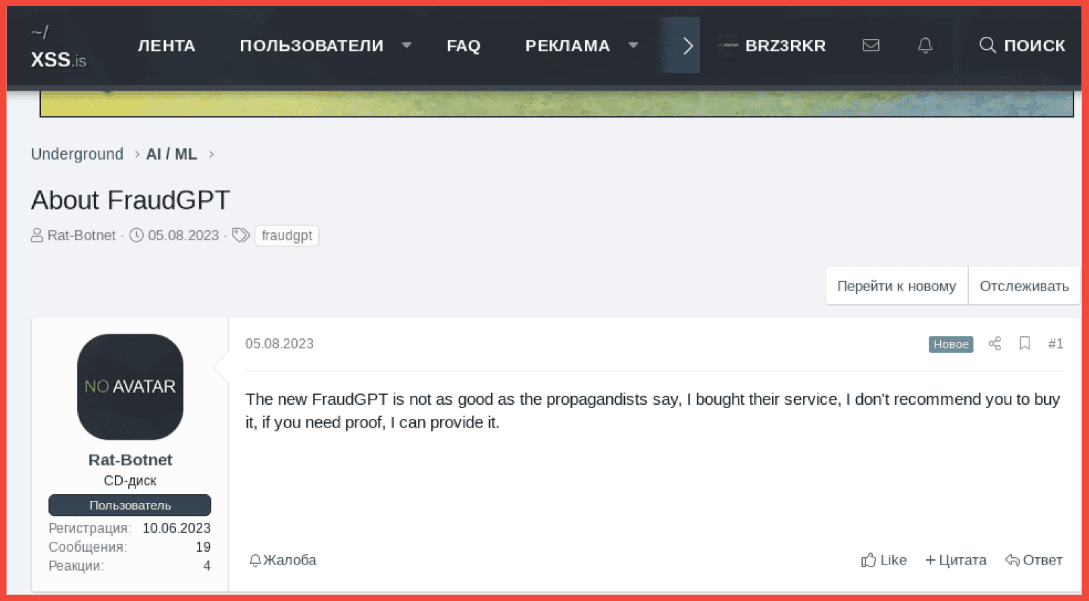
With triple extortion, the same process occurs as above, with the added threat (the third layer of extortion) including a distributed denial of service (DDoS) attack to the ransomware threat. The DDoS ensures an extra level of chaos and prevention of services while sensitive data is also stolen and encrypted. Ransomware groups Killnet, Avaddon, and Darkside are some examples of triple extortion ransomware operators. Extortion became quite popular during the Covid-19 pandemic, and criminal forums on the darkweb started to sell and offer extortion services and software to further ransomware operations.
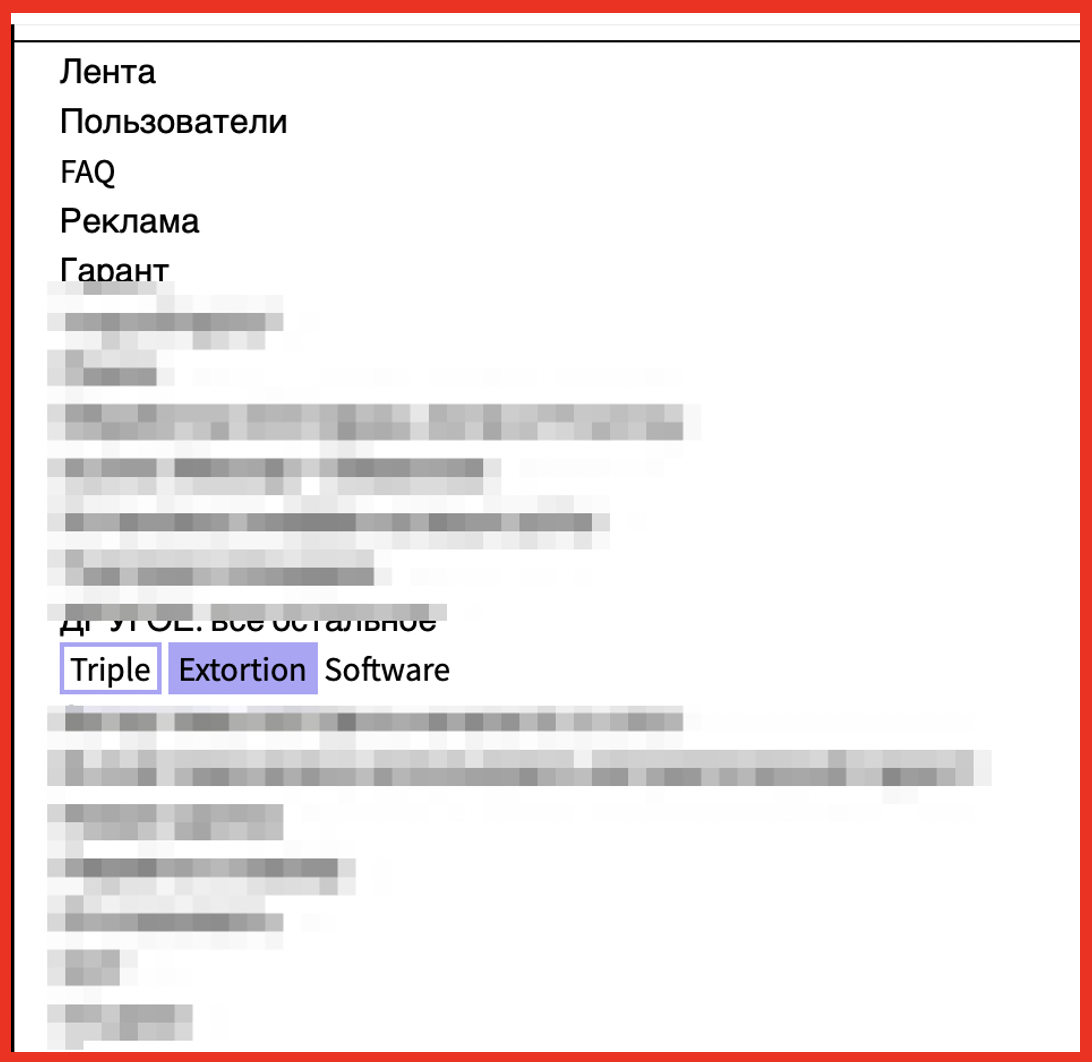
A 2022 post on criminal market XSS offers triple extortion software for purchase:
Figure 4: Source: DarkOwl Vision UI
Quadruple extortion entails everything above, with the addition that ransomware actors threaten to directly contact partners or other customers of the organization, threatening the reputation as well as adding the risk of legal action against the entity that was breached. BlackCat and the now defunct DarkSide ransomware gangs were some of the noted users of quadruple extortion in their operations.
Stealers, RATs, and Ransomware
Infostealers take information from web browsers, chat platforms, email clients, cryptocurrency wallets, and more applications. Similar to ransomware, they have exploded in popularity among the criminal underground. Like all malware, infostealers vary in capability but focus on procuring tons of personal data to sell, use, and reuse in malicious operations.
RedEnergy, a new Stealer-as-a-Ransomware technology, steals information from various web browsers while also facilitating ransomware activities. The entities behind RedEnergy use publicly available LinkedIn pages to target the oil, gas, and telecom sectors. After users click on a link that they expect to provide a typical browser update, RedEnergy exfiltrates data over FTP, and then encrypts the data and demands a ransomware payment.
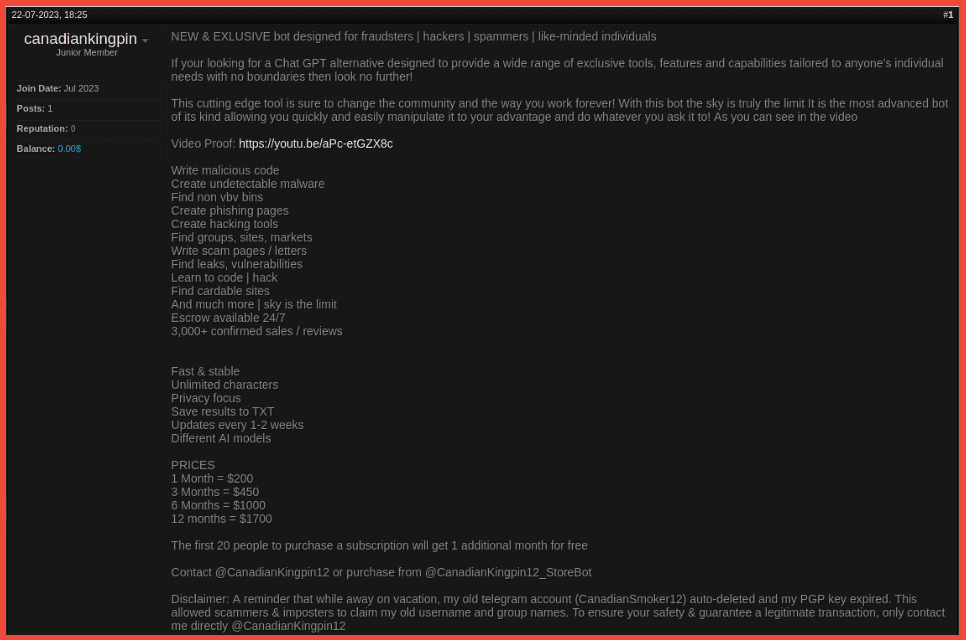
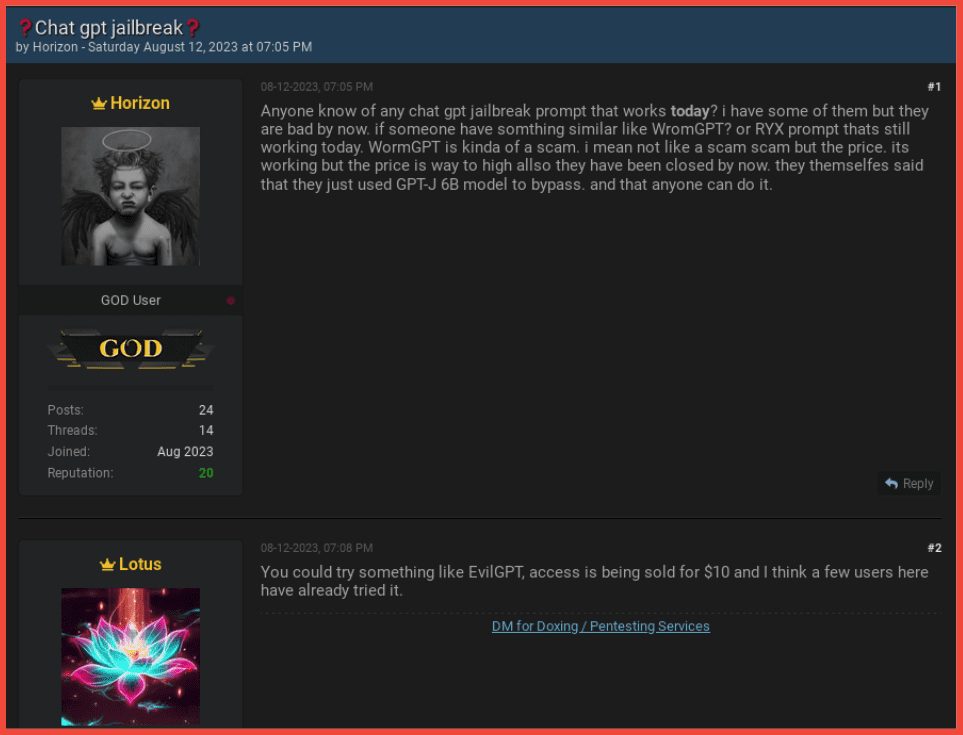
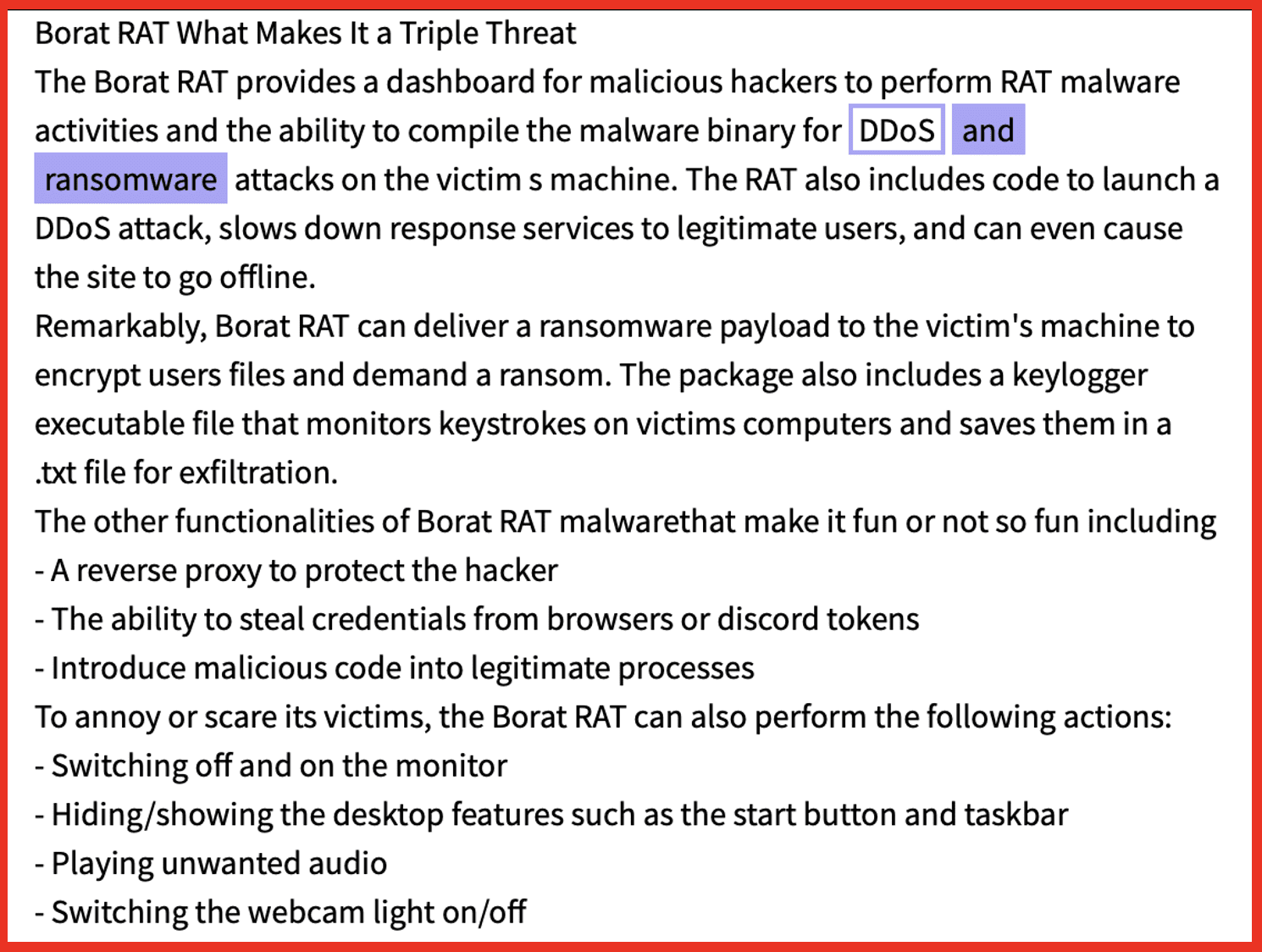
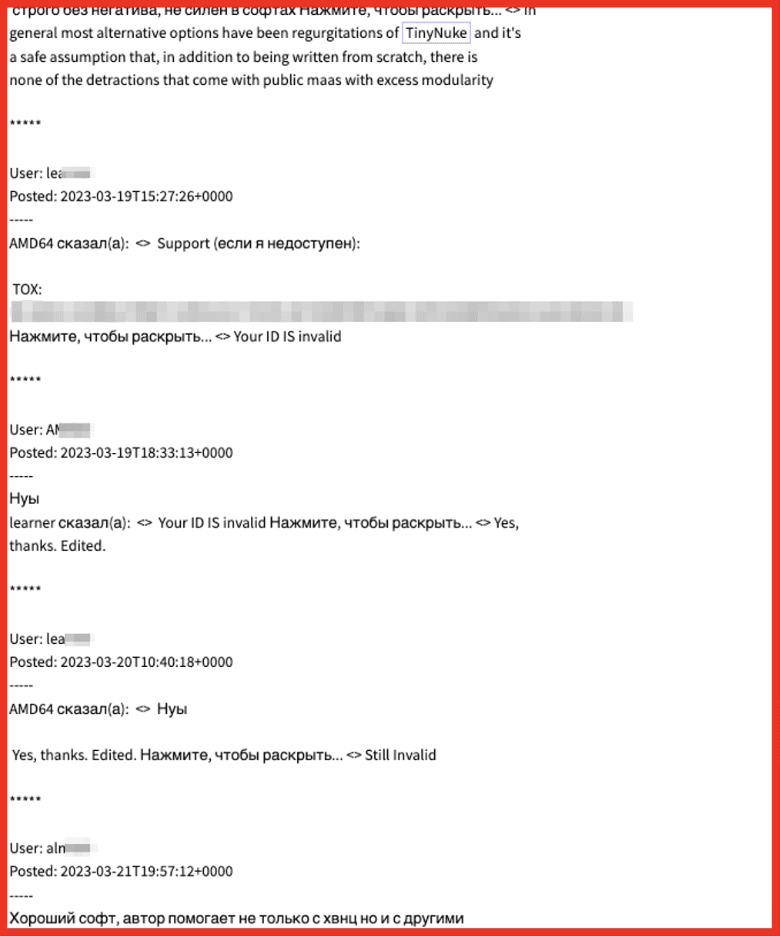
The combination of stealers and ransomware follows a similar combination of RATs and ransomware, which emerged in the wild in 2022. A September 2022 post on criminal market AlphaBay discusses how a RAT can be used as a triple threat in cyber operations:
Figure 5: Source: DarkOwl Vision UI
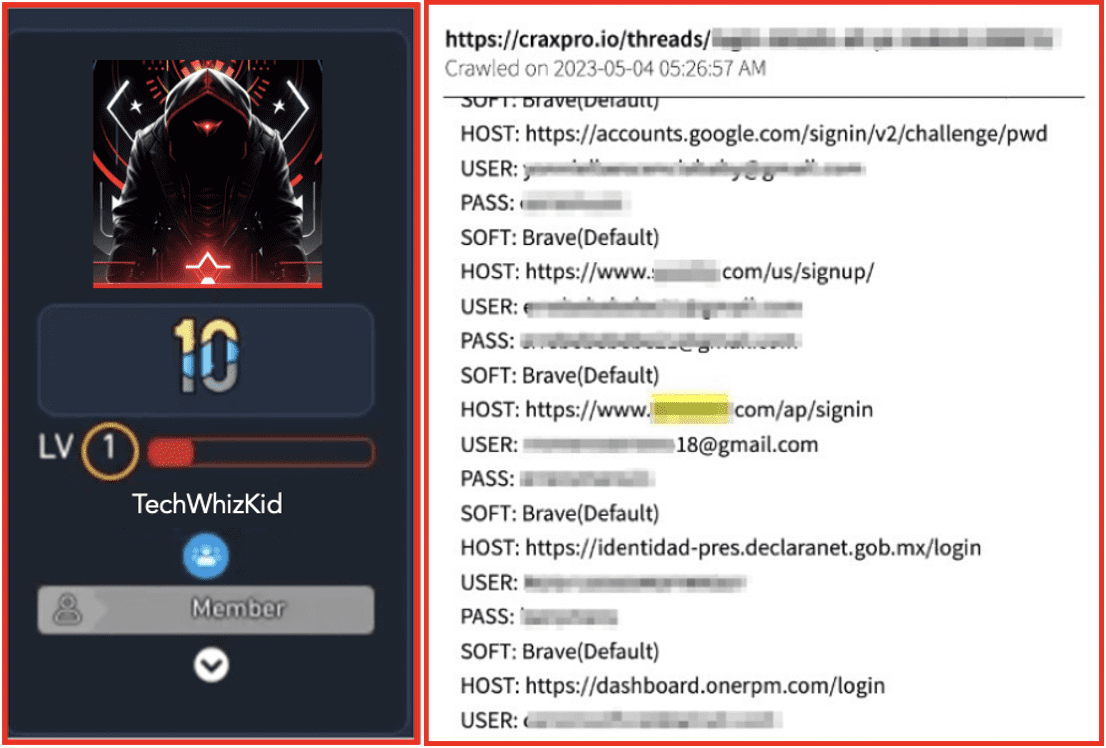
A June 2023 post on criminal market XSS details the use of ShadowVault stealer, which specifically targets Mac operating systems and can be used in Chrome, Edge, Brave, and other browsers:
Figure 6: Source: DarkOwl Vision UI
Cybercriminals are constantly evolving and combining malicious tools to procure as much information as possible from organizations while then attaching reputational damage onto the end of their operations by subjecting their victims to ransomware. The criminal underground forums facilitate the combination of tools and the advanced implementation of criminal processes to impart maximum damage to victims.
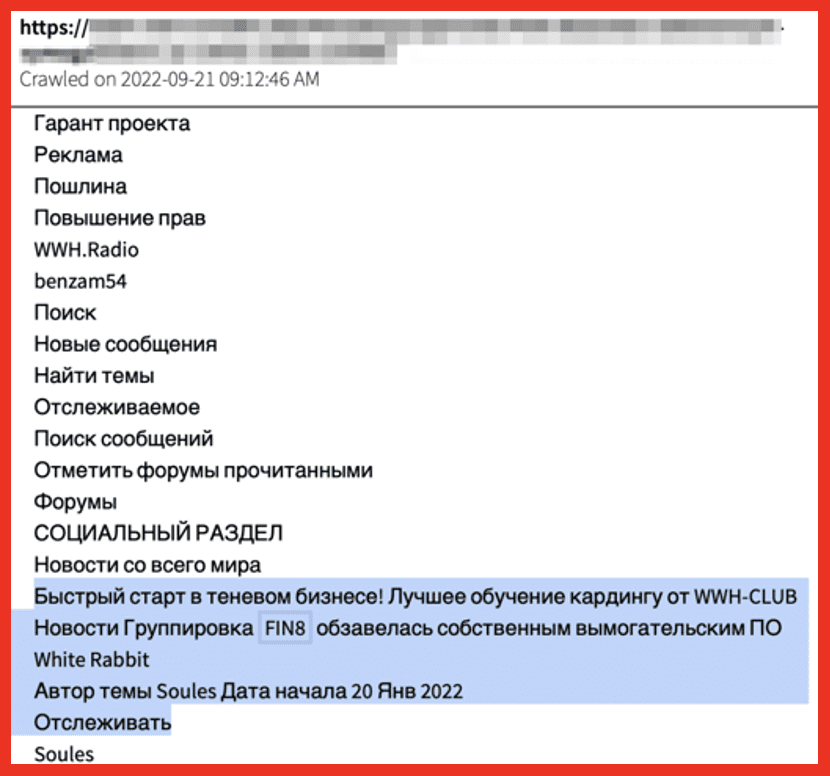
As of July 2023, the financially motivated cybercrime group FIN8, active since 2016, is now using variants of ransomware in its activities. FIN8 originally started targeting point-of-sale (PoS) systems using malware specific to PoS theft in the retail, restaurant, entertainment, and hospitality industries. Now, however, researchers have identified backdoors purportedly authored by FIN8. This additional combination of a general cybercrime group TTP combined with ransomware demonstrates that FIN8 is dedicated to maximizing their impact and profit. They also show a continued dedication to remaining undetected and updating and authoring their customized tools, all while dabbling in ransomware.
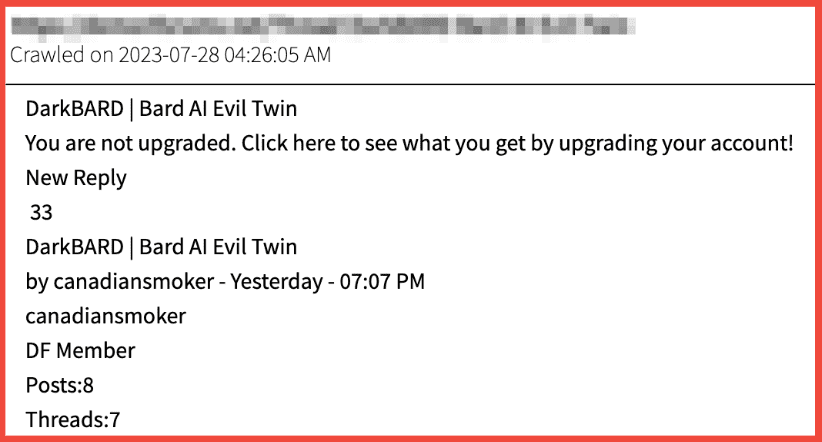
A Club IO post from September 2022, detailing FIN8’s possession of White Rabbit ransomware:
Figure 7: Source: DarkOwl Vision UI
Reduction in Using Encryption
Actors proficient in ransomware also know that encryption is a time-consuming process. Both encrypting the stolen data and then decrypting, if/when the victim chooses to pay, are costly in resources and the flow of operations. For this reason, some ransomware groups are now practicing intermittent encryption, where only small portions versus the totality of a file are encrypted. Encrypting only select portions also helps evade security tools on a network. When only parts of a file are encrypted, this emulates legitimate software practices, and there are no flags or processes on the network that stop the activity. In some instances, ransomware groups have completely forgone encryption. Karakurt, who emerged from Conti after the latter disbanded, commonly operates this way.
Future Predictions
When the pro-Russia Conti ransomware group suffered a leak in 2022, it revealed an organized group of actors operating very much like a business. Emerging ransomware groups are following this business-plan setup, establishing organized points of contact, liaisons between ransomware group operators and victims, authoring rules of engagement, and working within stringent timelines. Researchers and everyone in cybersecurity were able to learn from the leaks and inform future cybersecurity tools, processes, and potentials.
Conti’s internal chats, leaked by a disgruntled employee, revealed a professional setup replete with:
- Interviews to hire the right personnel
- Russian government involvement and funding
- Feature developments (for both deploying and improving their ransomware effectivity)
- A control panel for monitoring Conti operations, victims, and payment status
- Templates for phishing emails to use in operations
Not only are ransomware actors setting up formal, almost corporate like operations, but they are also recruiting from now-defunct groups, as well as sharing TTPs between one another to help maximize the impact of their operations. Furthermore, there are segregated “branches” of ransomware. For example, some researchers and analysts deem Karakurt the “Extortion” arm of ransomware, as that is a specialty of Karakurt.
In addition to ransomware operations continuing to focus on stolen personal information and data, automation, and the advent of Artificial Intelligence (Al) are both expected to facilitate ransomware groups further streamlining their activities. Several ransomware groups already use scripts and automation to scan for vulnerabilities and entry points to a network; this allows ransomware efforts with few personnel and minimal resources to identify appropriate targets which can easily be made into victims and earn them revenue with an attack.
Ransomware groups are also branching out from focusing purely on Windows operating systems and moving towards attacking Linux based systems. This demonstrates a new sophistication when outlining attacks and identifying potential victims. Now that Linux based operating systems are in the crosshairs, this allows for entry into attacking both IOT and container orchestration platform, such as Kubernetes, greatly expanding the attack surface.
Conclusion
Ransomware is an efficient criminal operation yielding high profit for minimal work. Due to pseudo-anonymous technology, using the dark web for ransomware operations and cryptocurrency for payments, as well as email and VPN services that do not track physical location, ransomware groups will continue their activities because the risk of punishment is minimal, and the operations are profitable. The lack of prosecution coupled with the increase of the attack surface ensures continuous and robust ransomware operations. Critical infrastructure, academic, technology, and government sectors must all raise awareness and assist in protection from ongoing ransomware campaigns.
Interested in learning how DarkOwl can help get ahead of potential attacks? Contact us.