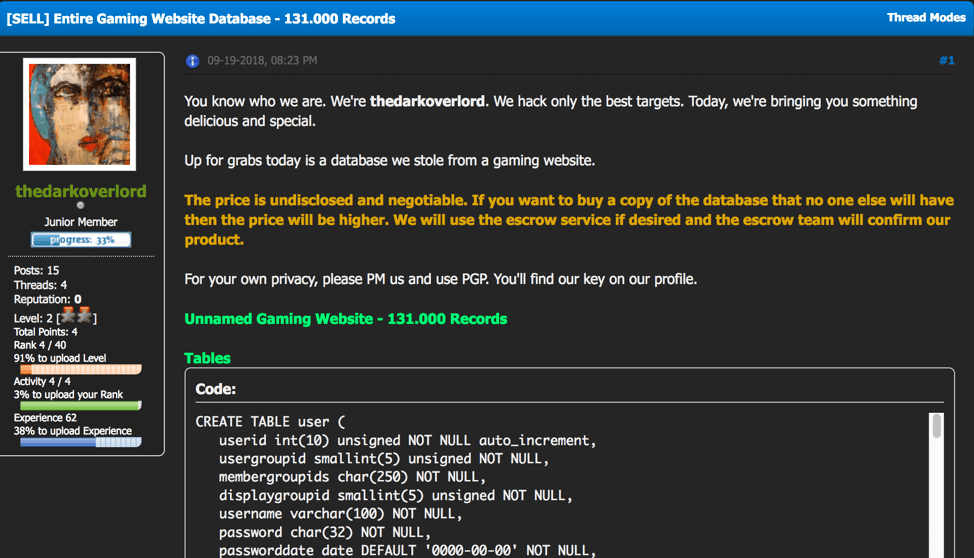
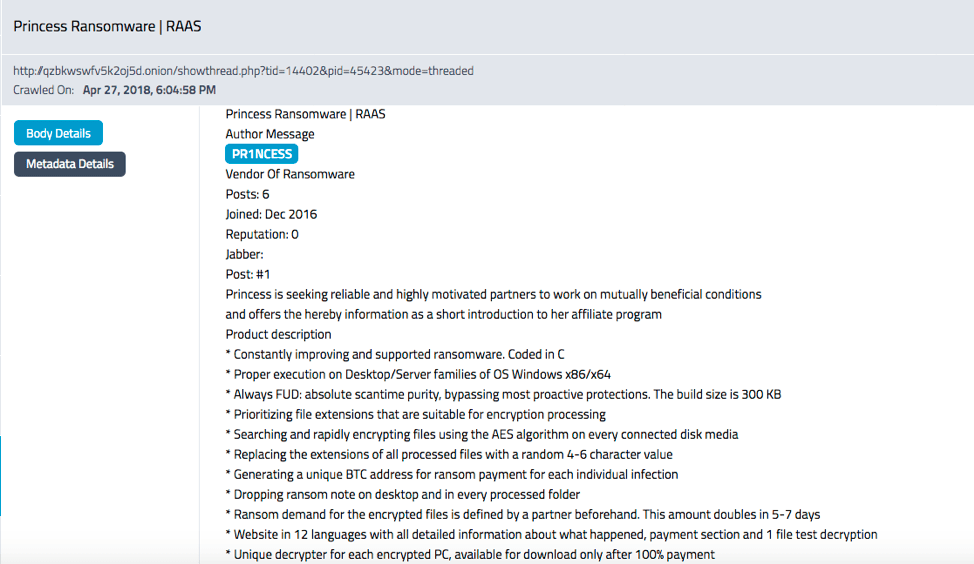
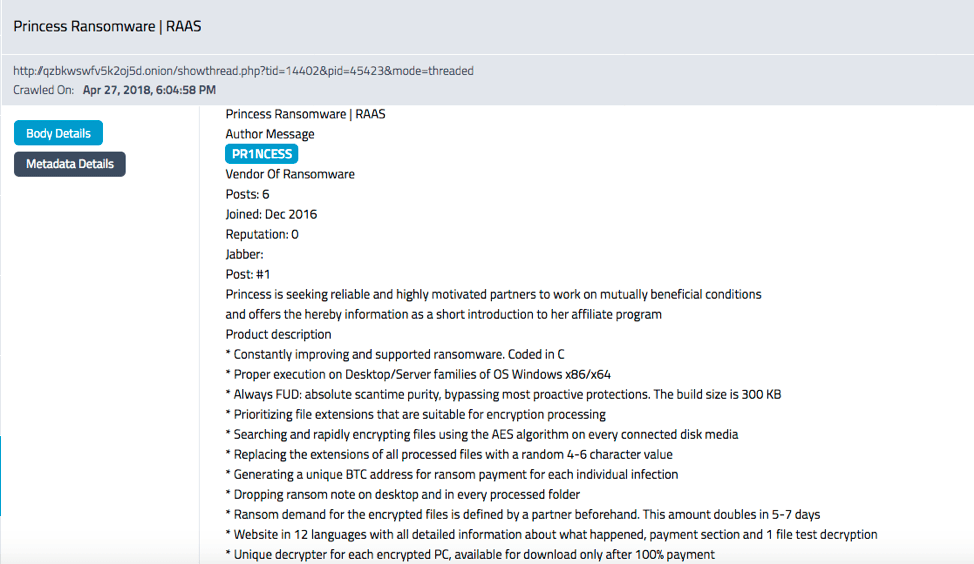
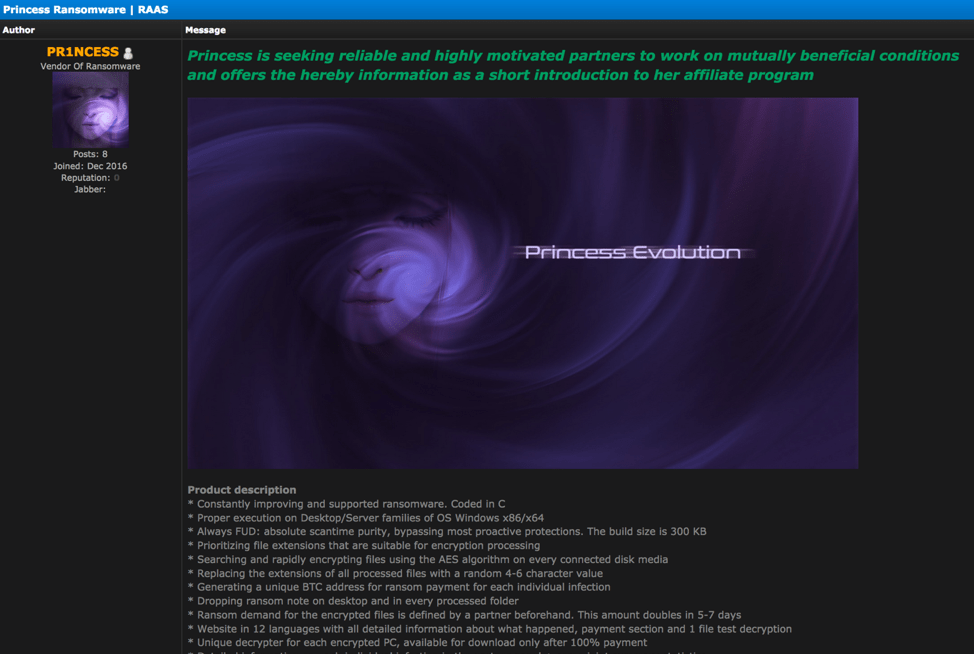
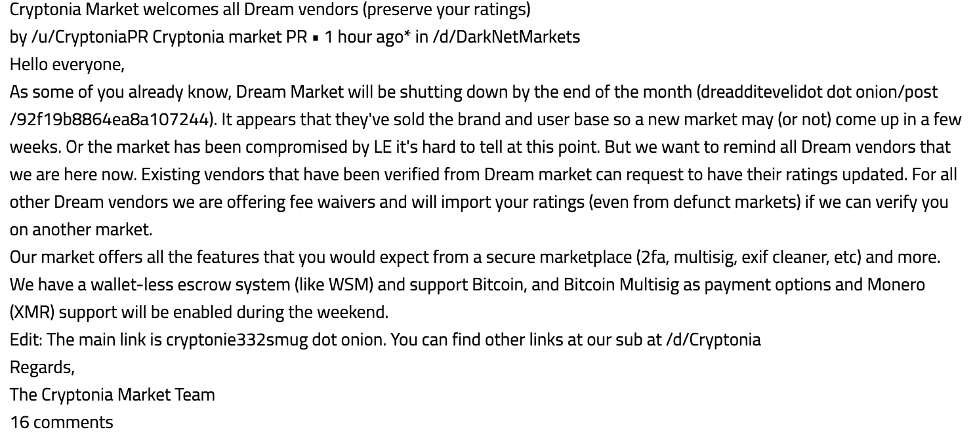
Dream Market’s Reincarnation Announced – Saṃsāra
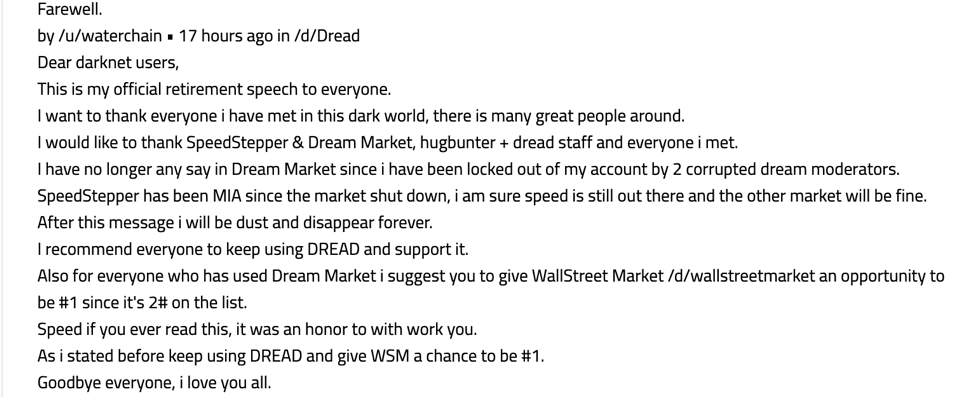
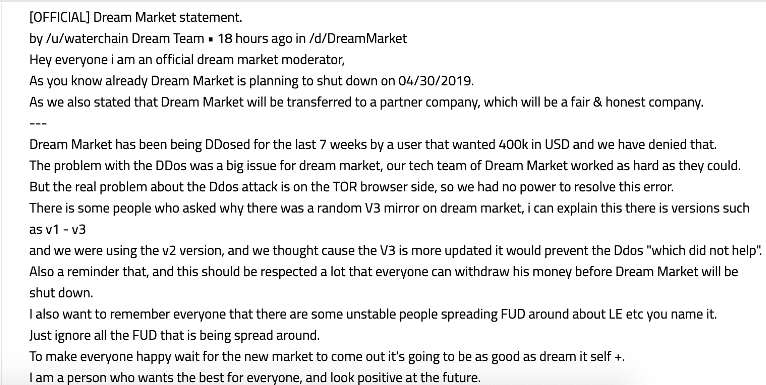
As Dream Market staff mentioned prior to their shutdown, a new market was on the horizon. On Friday, former official Dream moderator, waterchain, announced the opening of Saṃsāra, based on the source code of the infamous Dream Market. Saṃsāra is a term from eastern religious philosophy. Ironically it refers to the eternal cycle of birth, suffering, death, and rebirth.
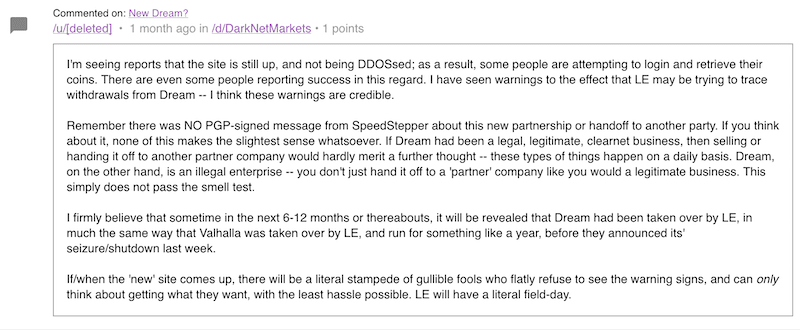
The official market announcement is received with skepticism. Many questioning its legitimacy and a number of inconsistencies with the story behind the return of the market.
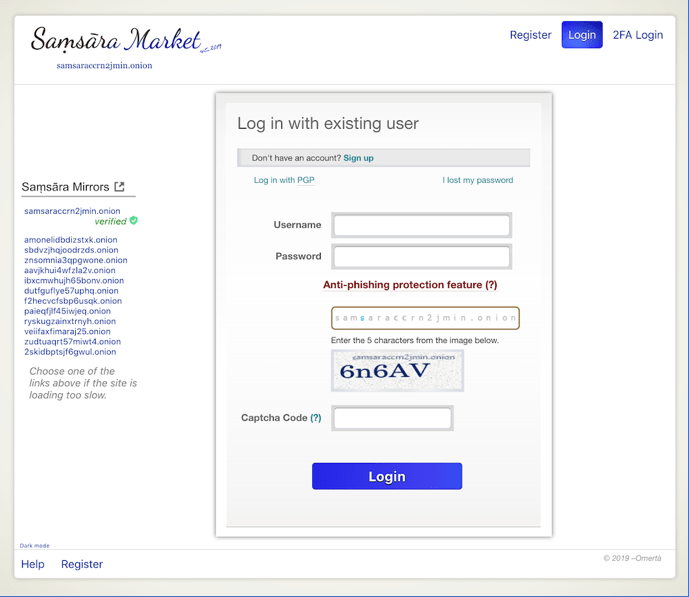
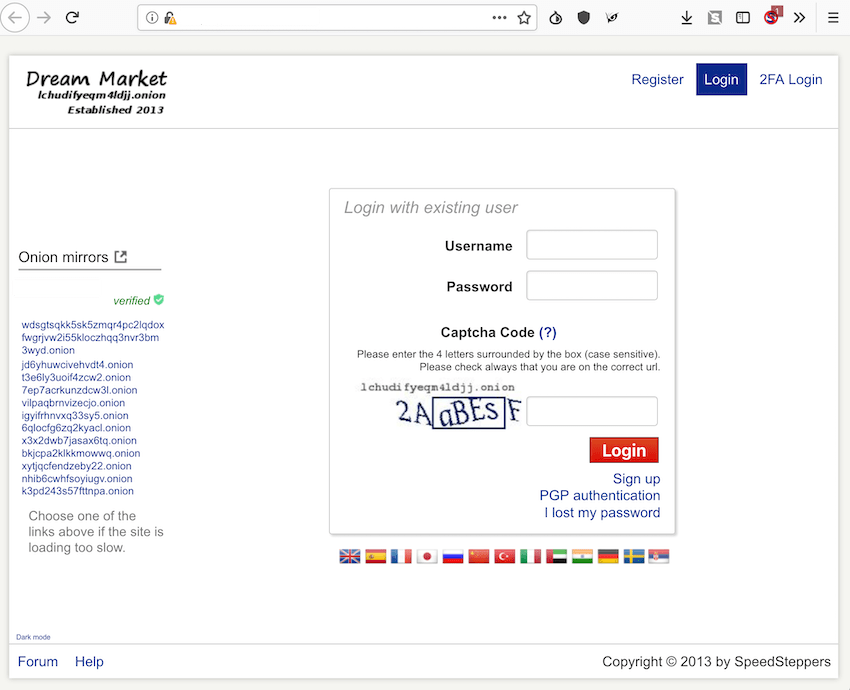
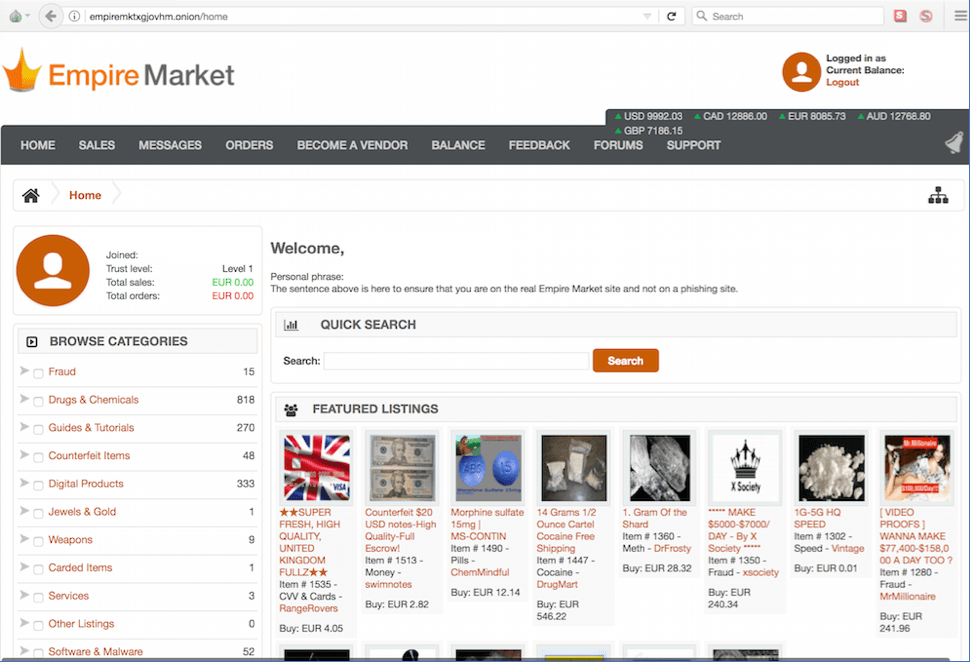
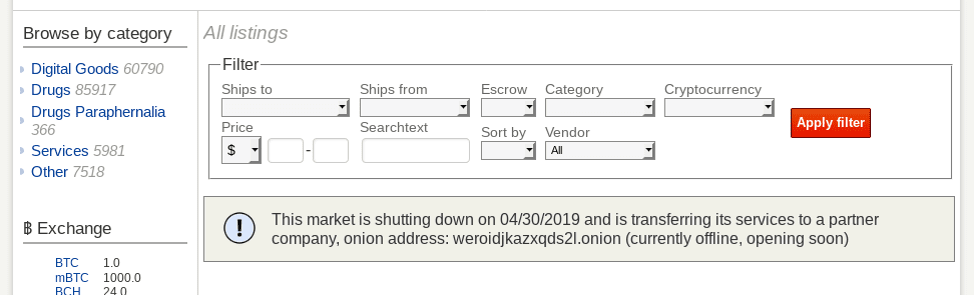
The new Saṃsāra market layout is strikingly similar to Dream, yet includes several new security elements. Admins refer to a new “anti-phishing feature” as the first of its kind that purports to completely defeat man-in-the middle attacks along with the option for a user to login with their PGP key or two factor authentication(2FA) for additional security. Once in the market, the source code is identical to the original Dream Market with the addition of a News and Community section that allows for interaction with Admins on market features. There is no mention of a traditional separate market forum like Dream supported.
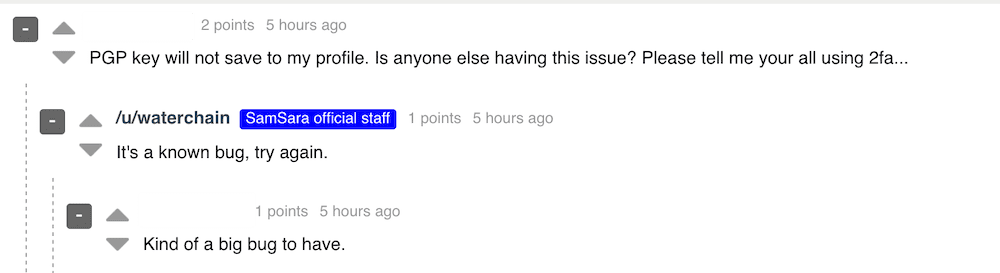
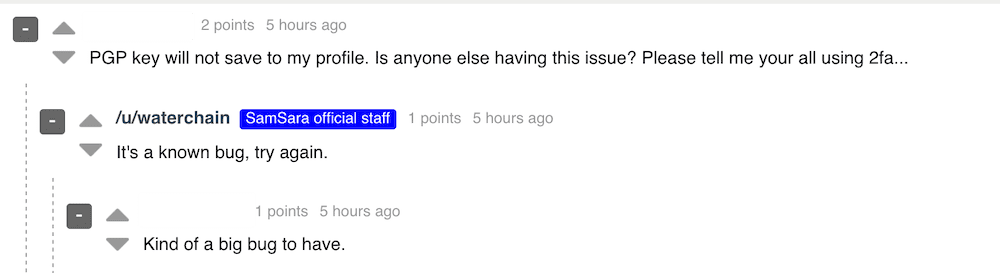
Even with a new market theme, logos, and user interface on top of Dream Market source code, within hours of the announcement, many users uncovered bugs across the cryptomarket, including issues with saving public PGP keys, which forced users to employ 2FA for additional profile security.
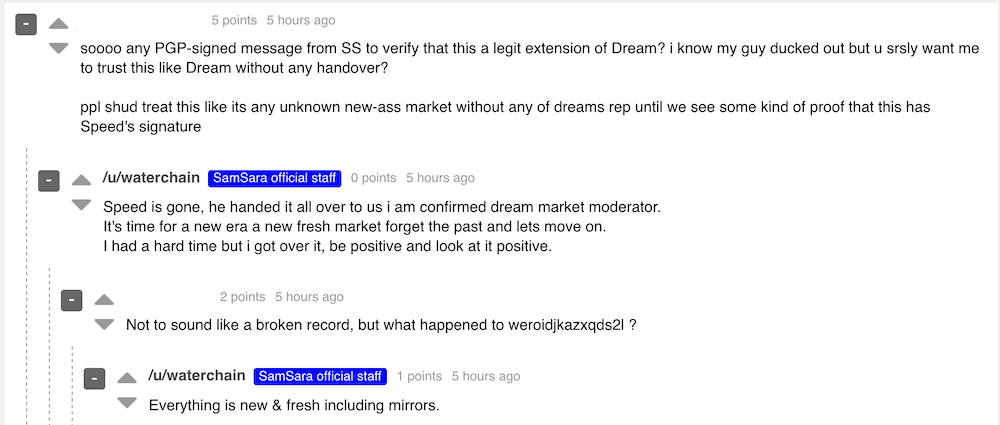
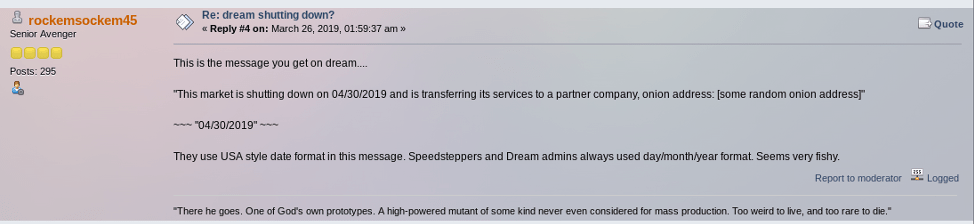
The new market administrator dismissed community concerns over the lack of presence by SpeedSteppers. Further, dismissing questions about why the new onion address as advertised for weeks on Dream Market is not listed as a valid mirror for Saṃsāra. He instead attempted to encourage people to “forget the past” and “move on” insisting numerous times that he was a former official Dream moderator, as if to validate everything he said on the forum as legitimate.
-
Others quickly noticed that waterchain’s new PGP key was created in June with only 2096 bits instead of the more secure 4096 bit key of the former legitimate waterchain. The moderator claims they lost his key in a corrupted Tails configuration. It does appear suspicious that they would choose to rebuild his key with less security, considering he is now essentially running a market instead of moderating it.
-
The market does not support Monero transactions, which is possibly a more secure and less traceable cryptocurrency than Bitcoin. There is a discussion along with member vote on the integrating XMR available through July 18th in the new Community section of the market.
-
All of the market mirrors use Tor’s legacy V2 hidden service domains instead of V3. Dream Market issued several v3 mirrors earlier this year when suffering from heavy DDoS attacks.
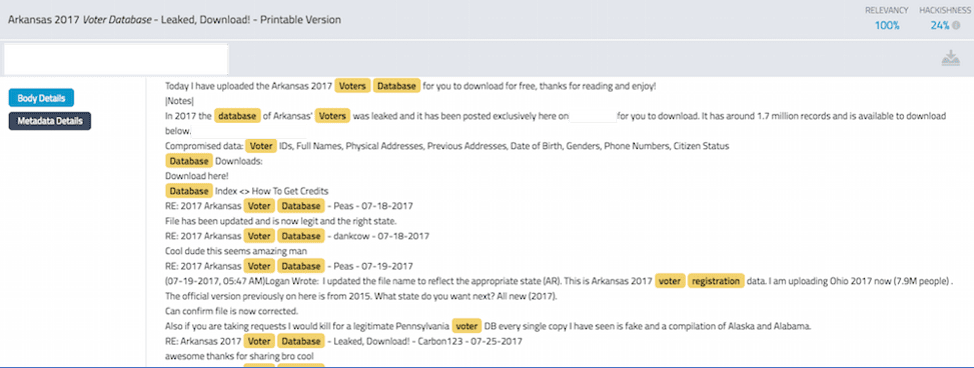
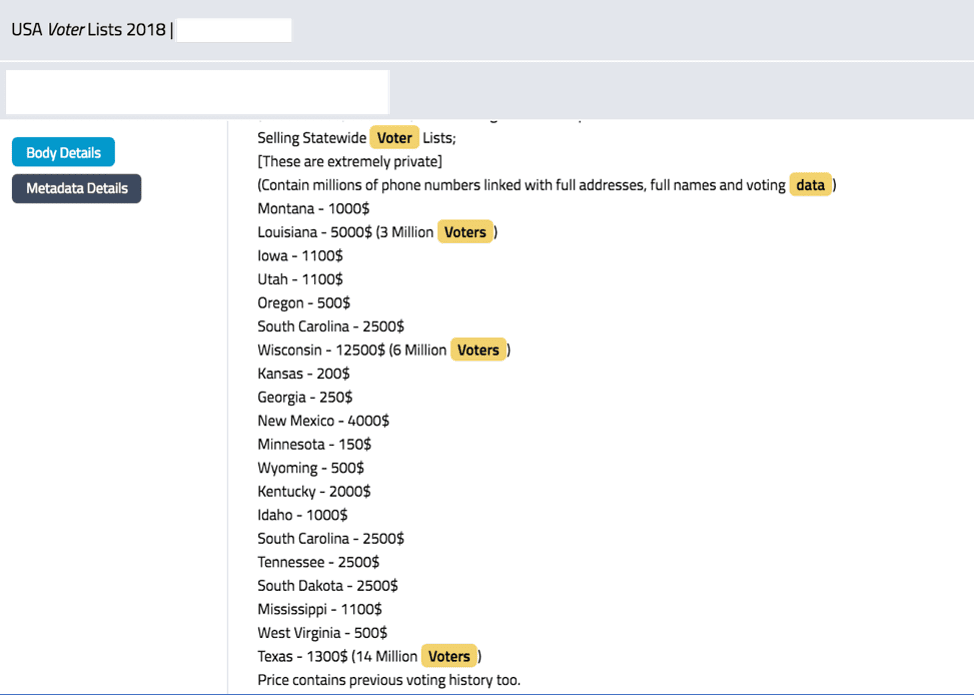
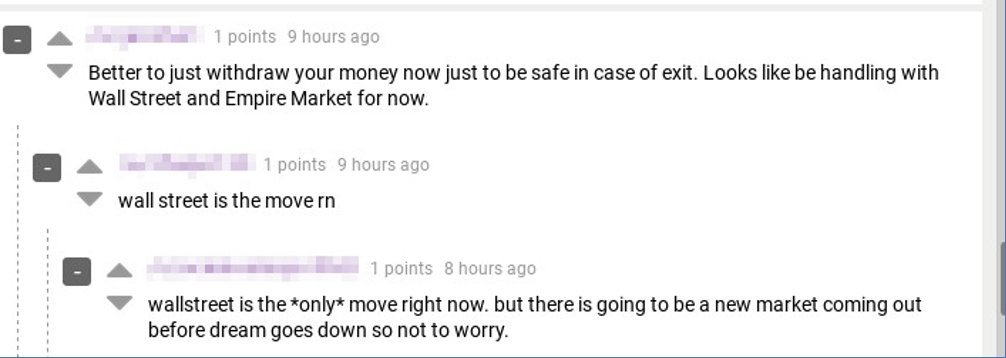
Even with these concerns, vendors are taking advantage of the limited offer of 0.025 BTC vendor bonds and over 400 market listings, consisting of mostly drugs, were online and ready for purchase within the market’s first day.
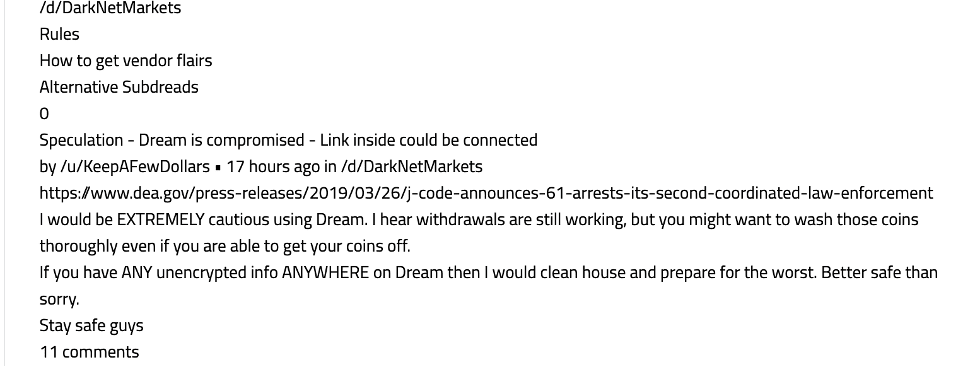
On a technical note, a few more inconsistencies appear. First, when requesting /server-status/ on the Saṃsāra url, we find what looks like a status page for another darkweb forum, Torum. Second, the HTTP-Headers also appear to leak IP addresses pointing at both a host in The Netherlands and the United States.
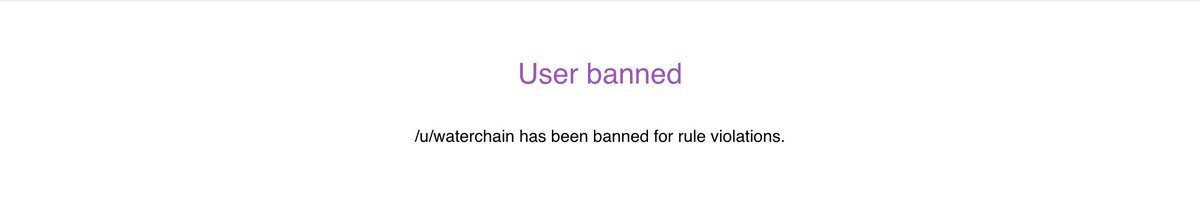
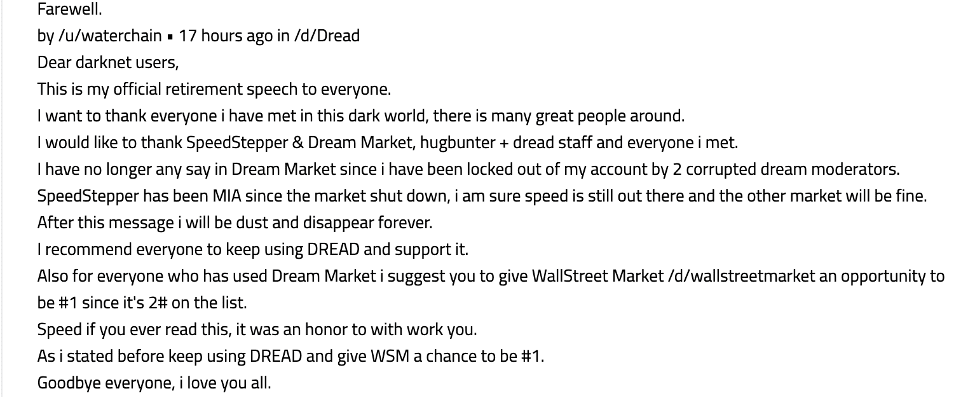
In recent days, user waterchain has been banned on Dread forum for rule violations.
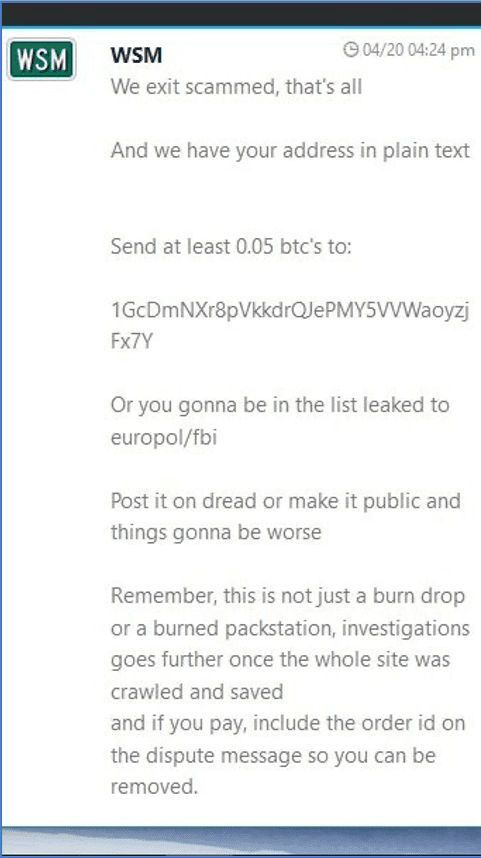
Only time will tell how long this market will be reliably online before the DDoS attacks against Saṃsāra begin. Remember to check back here for updates as more information emerges.



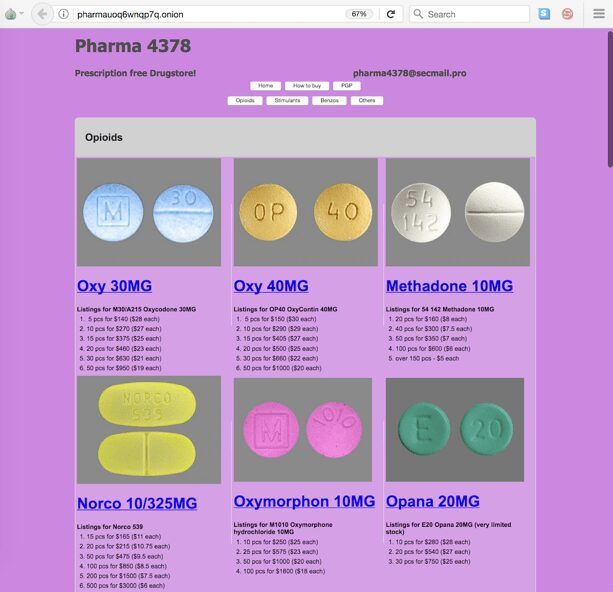
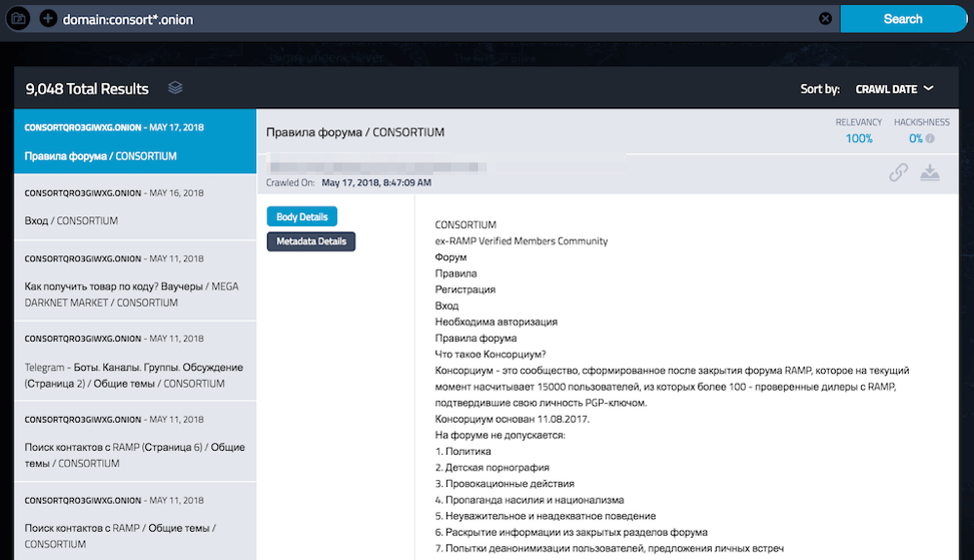 DarkOwl Vision Screenshot from Consortium Hidden Service Archive
DarkOwl Vision Screenshot from Consortium Hidden Service Archive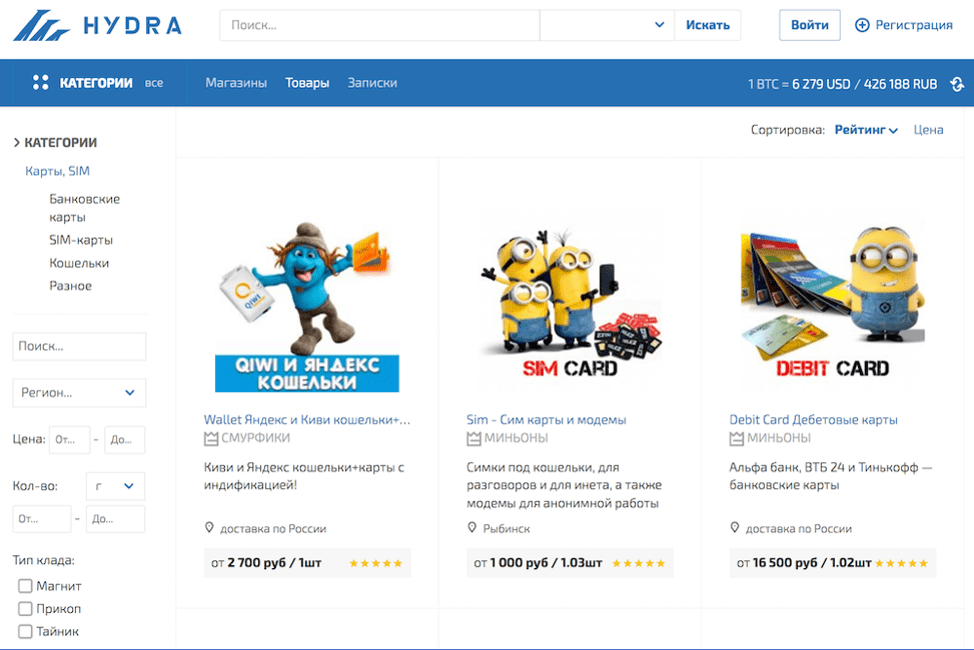
 MEGA Landing Page (http://megammpxznehakhm[.]onion)
MEGA Landing Page (http://megammpxznehakhm[.]onion)
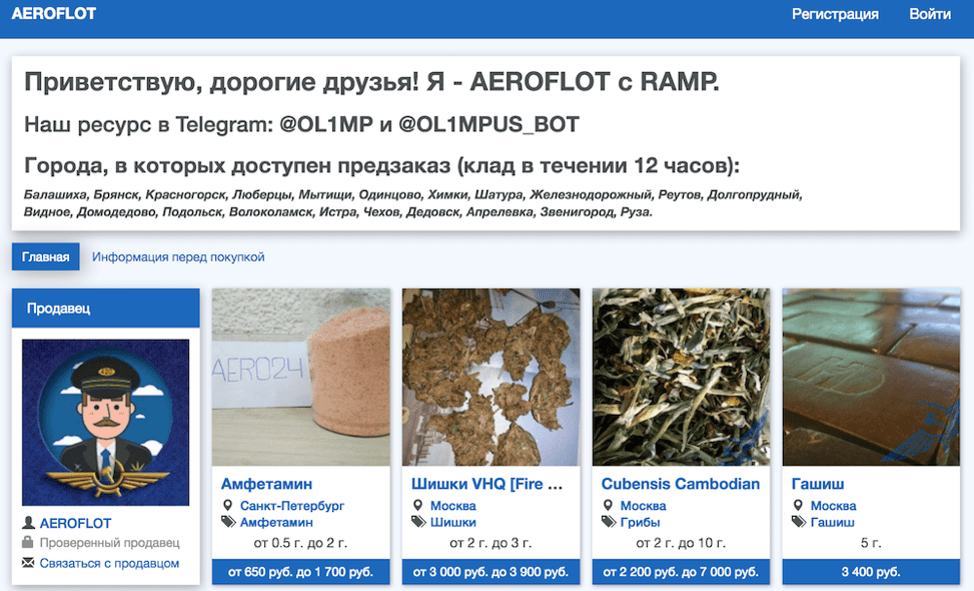
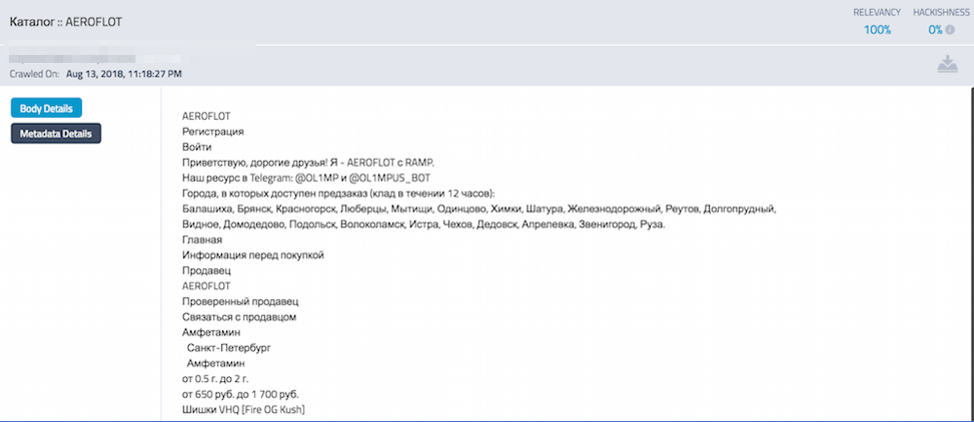 Aeroflot Vendor Shop on Tor (http://aeroflot2rumuq76[.]onion/shop/aeroflot)
Aeroflot Vendor Shop on Tor (http://aeroflot2rumuq76[.]onion/shop/aeroflot)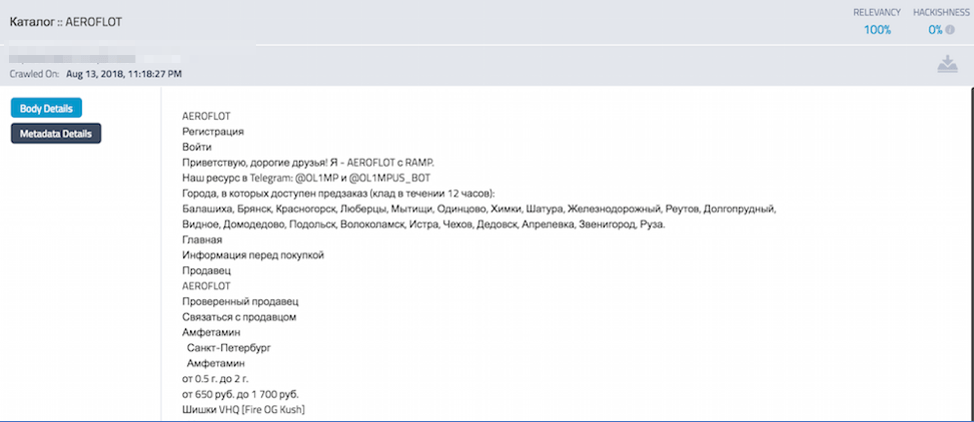
 RuTor Russian Forum (http://rutorzzmfflzllk5[.]onion)
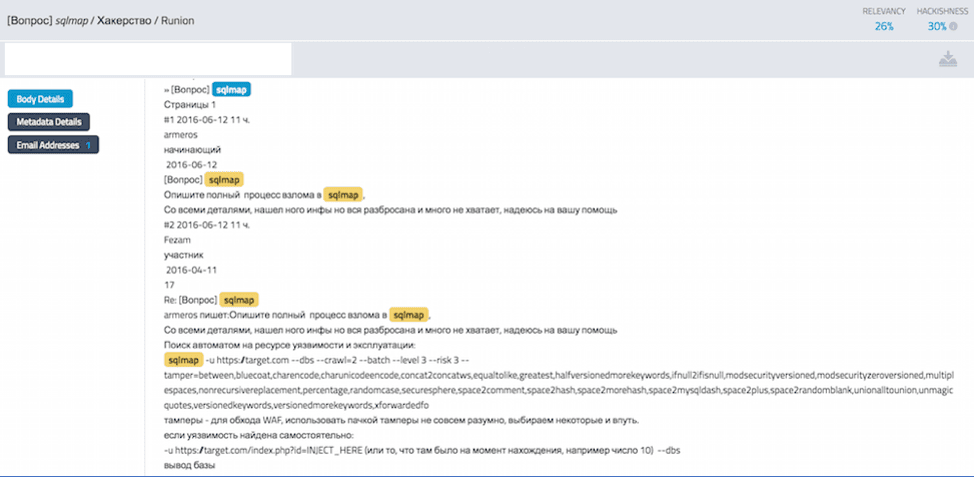
RuTor Russian Forum (http://rutorzzmfflzllk5[.]onion) Runion Darknet Forum (http://lwplxqzvmgu43uff[.]onion)
Runion Darknet Forum (http://lwplxqzvmgu43uff[.]onion)
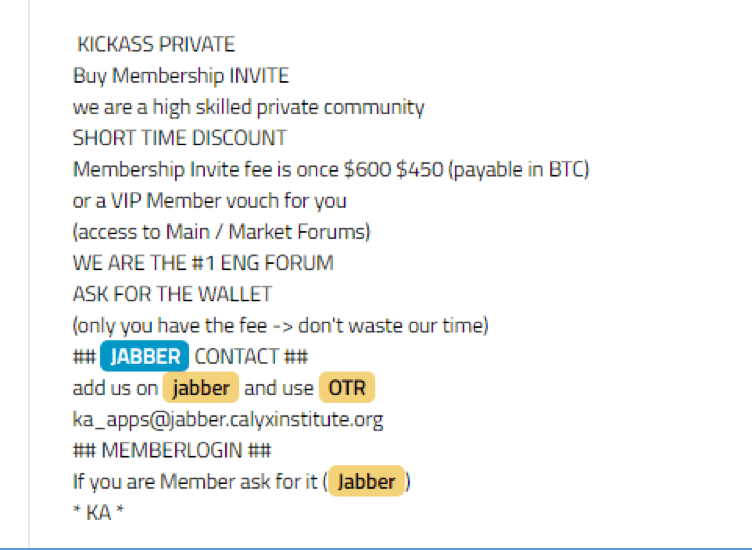
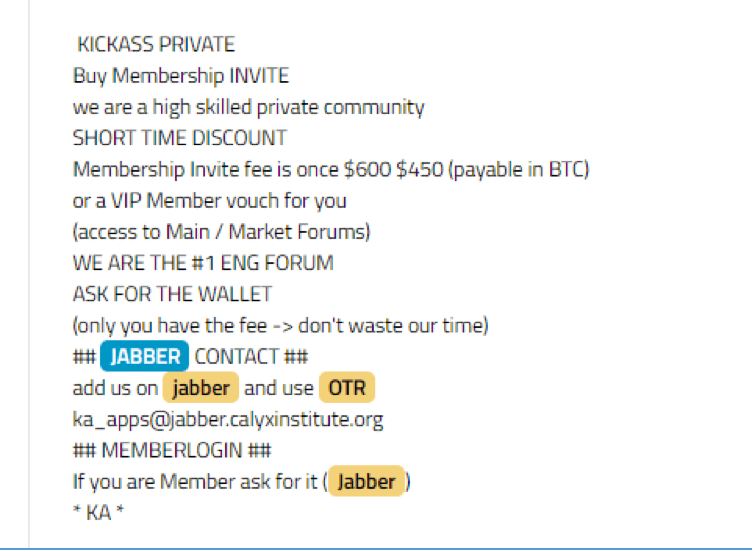
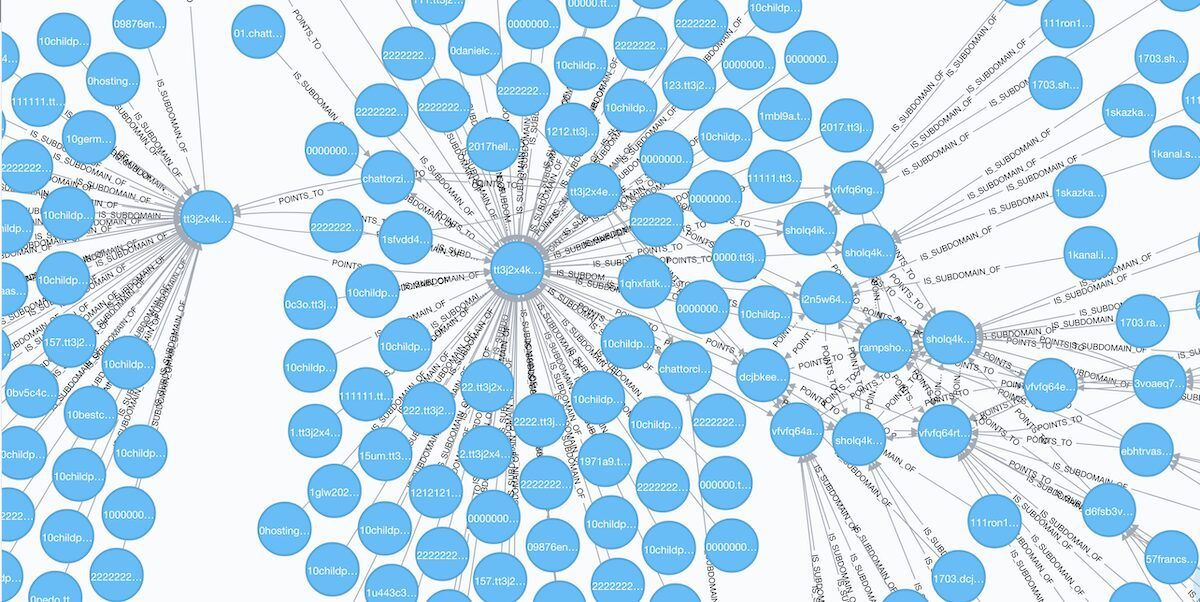
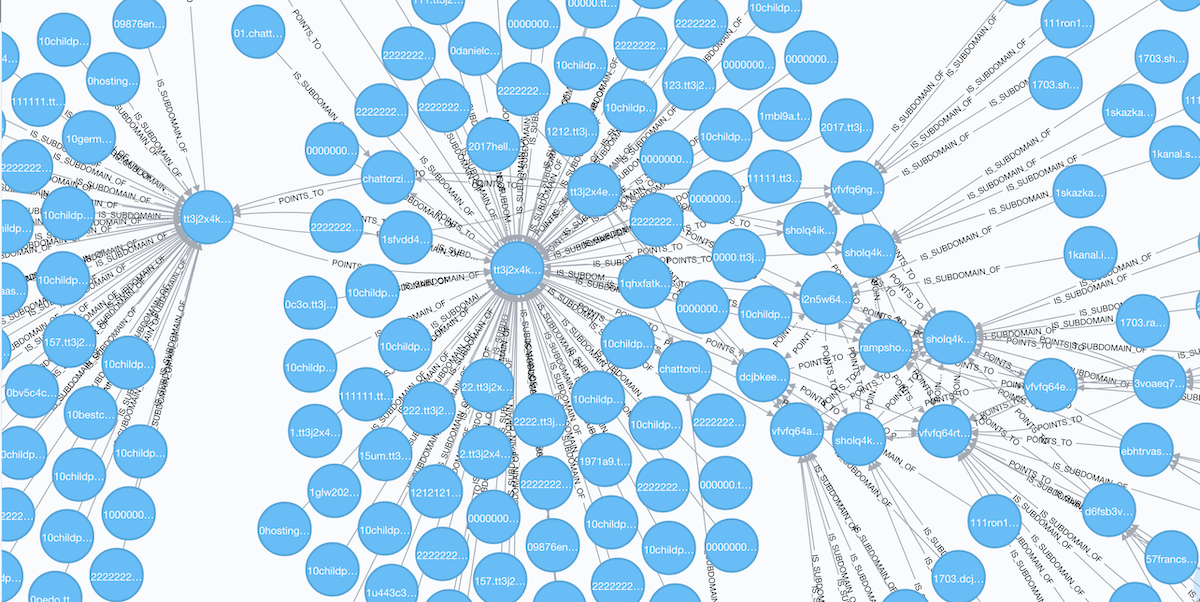
![Galaxy3 Post by user ChatTor (http://galaxy3m2mn5iqtn[.]onion)](https://www.darkowl.com/wp-content/uploads/2021/12/DanPicture4.png)
![Capture of Le-Chat conversation debating the validity of staff with Daniel's services (http://mat32scrdvrn5o4m.onion/neo/uploads/181119/MATRIX_115636_YsP_ChatTorConfession[.]png)](https://www.darkowl.com/wp-content/uploads/2021/12/DanPicture5.png)