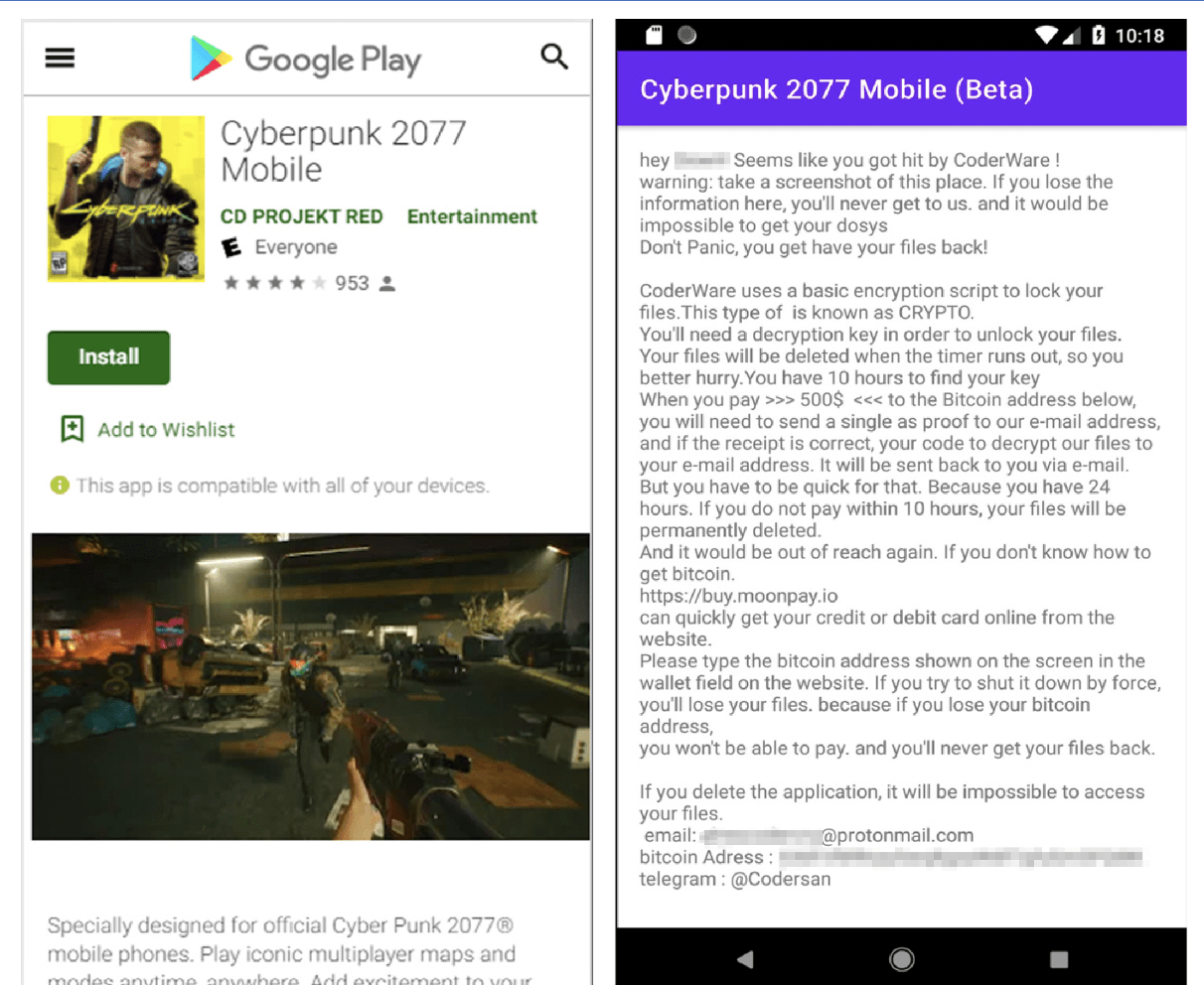
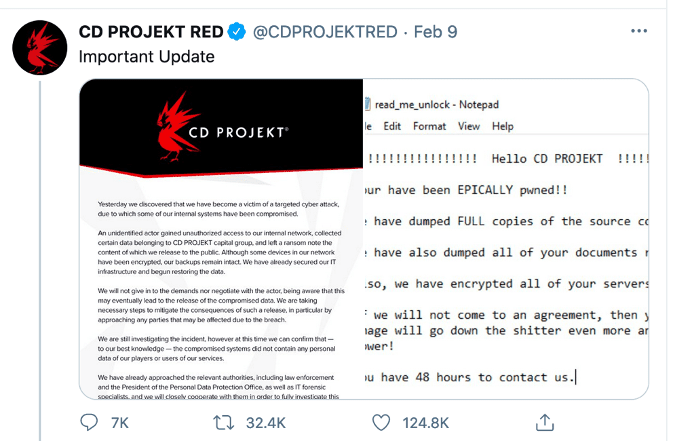
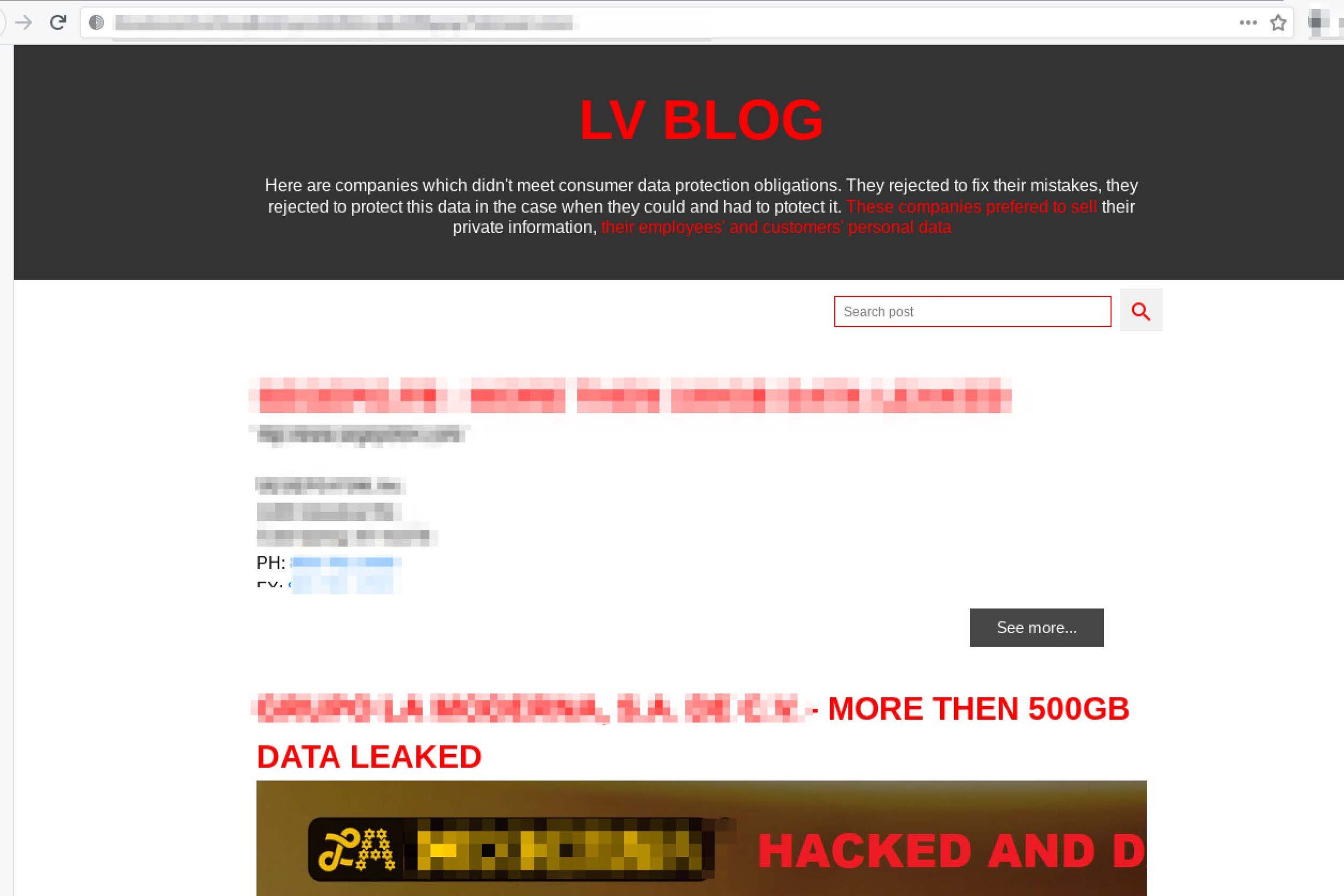
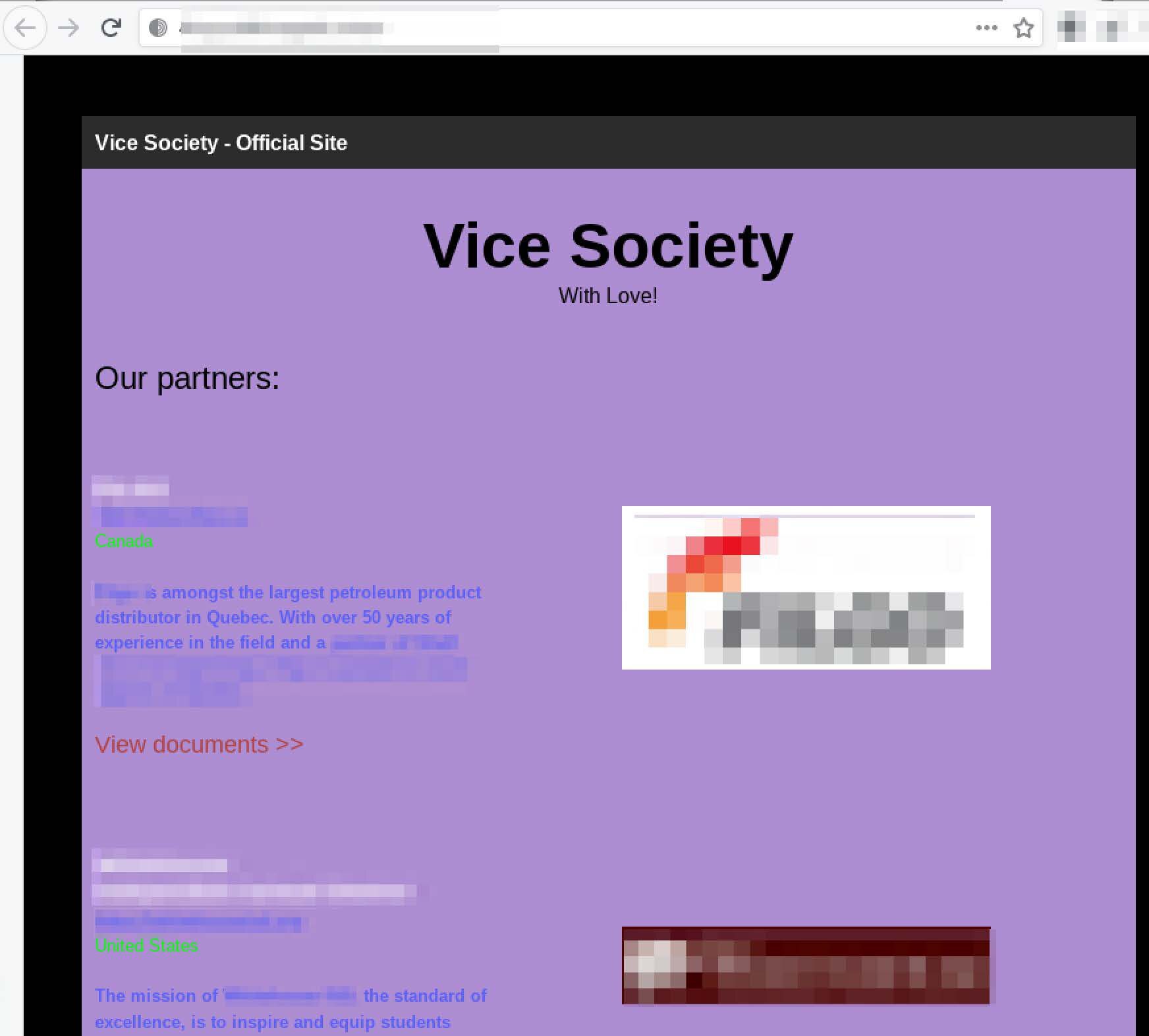
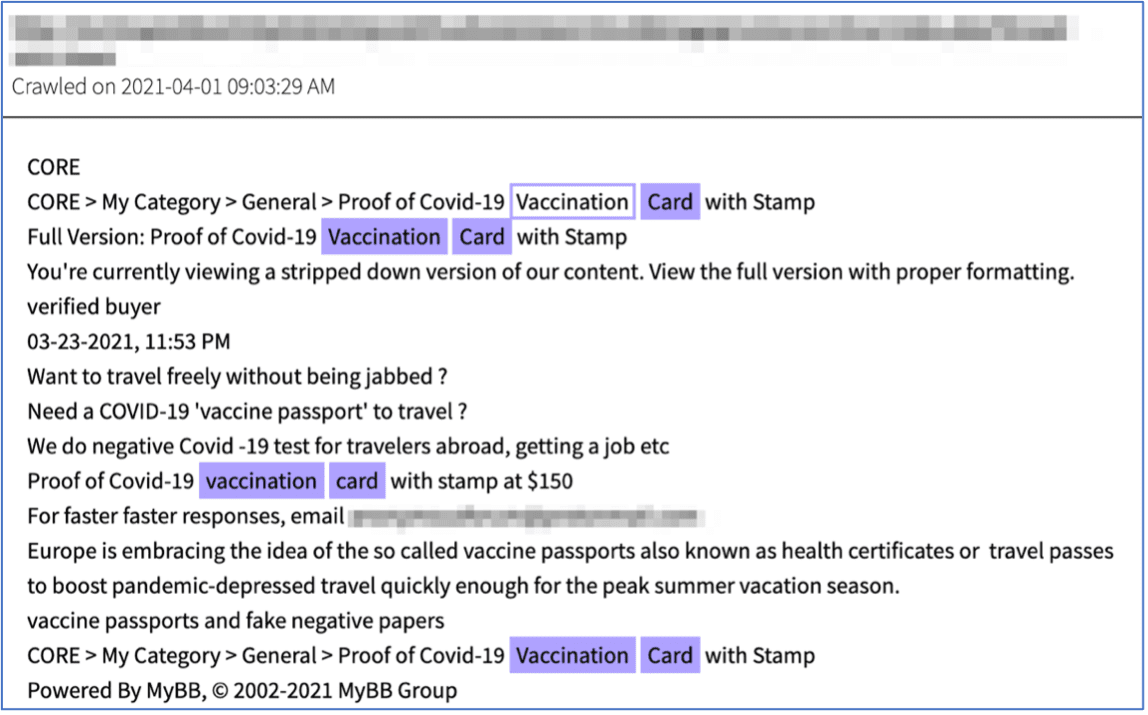
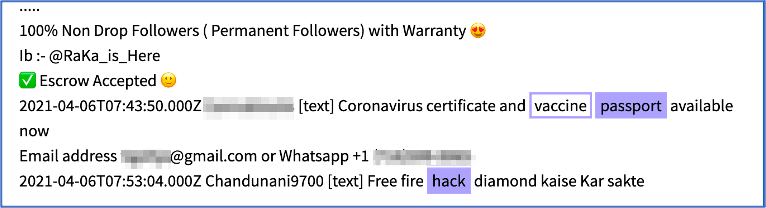
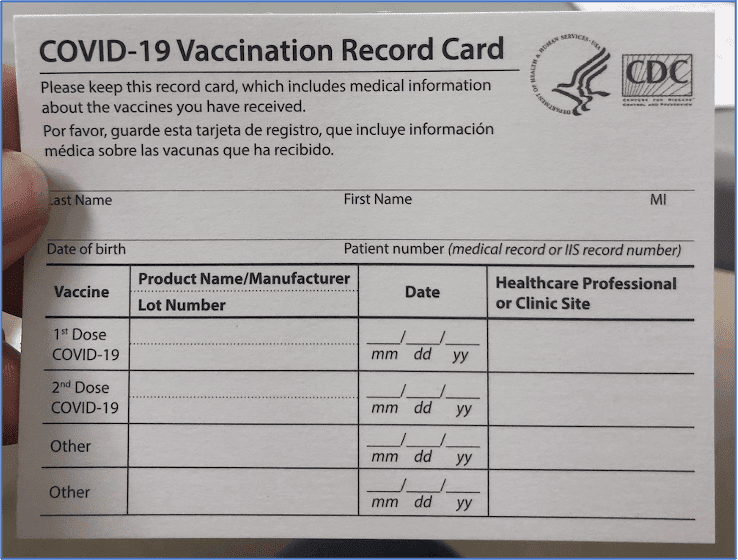
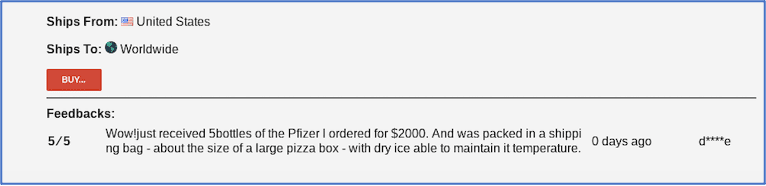
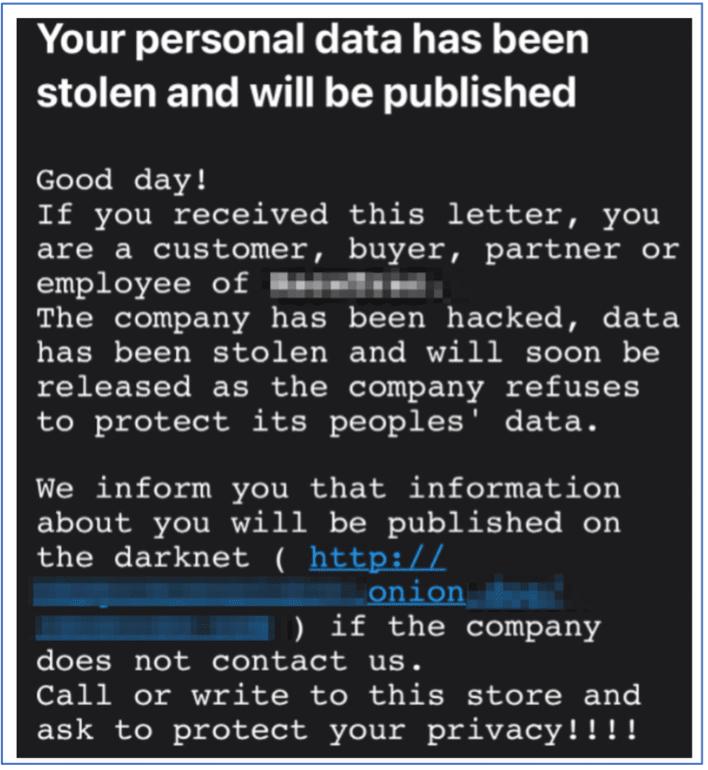
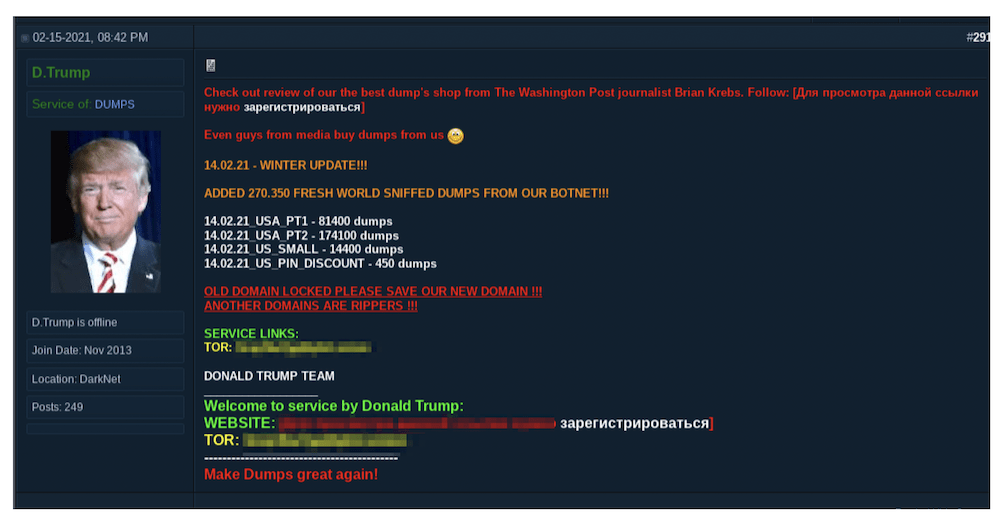
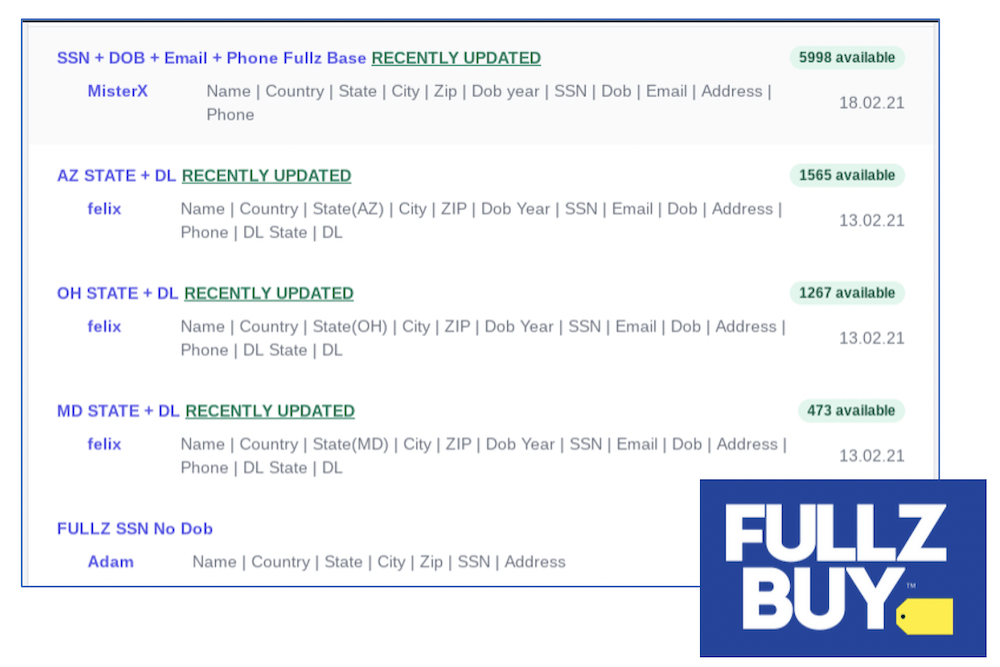
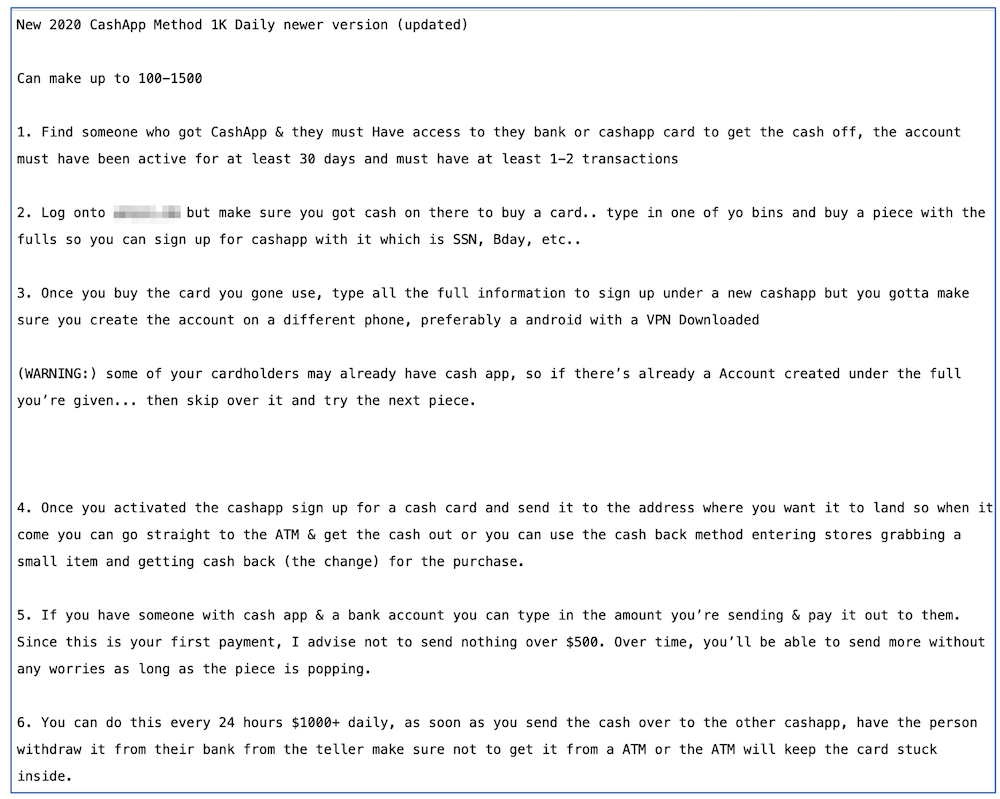
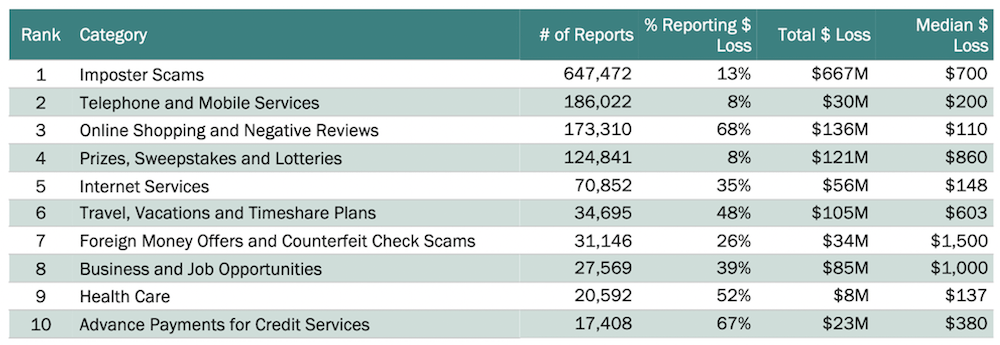
AvosLocker Debuts Service on Tor for Press Releases
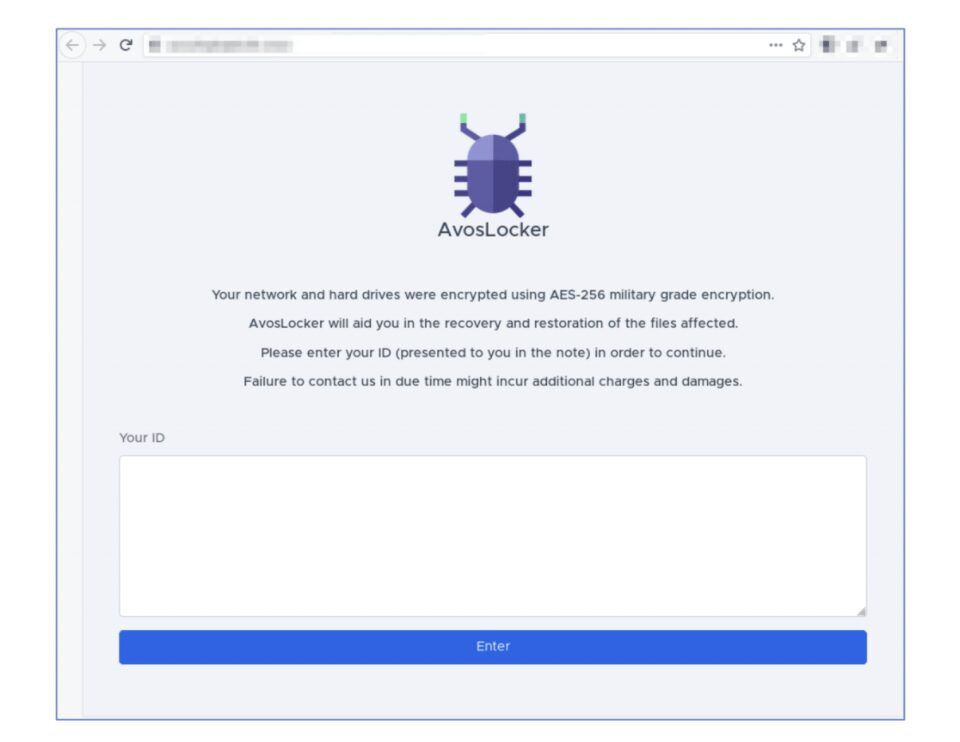
Since the beginning of July, information security researchers who have been keeping up with the darknet ransomware community have been anxiously awaiting the debut of AvosLocker’s official Tor service, which will be used as a forum for the ransomware-as-a-service (RaaS) group to communicate with the public about their victims. In early July, DarkOwl observed a v2 Tor onion service branded with AvosLocker’s name and brand logo – a purple bug with green-tipped antennae – stating that the reader’s (victim’s) network and hard drives had been “encrypted using AES-256 military grade encryption.”
The landing page (pictured below) included a simple form where victims with an “ID” could enter the darknet service to begin negotiations with the AvosLocker team on their ransom payment and status of their extorted data. An ID is only available to those who received a ransom note upon encryption of their computer networks.
Figure 1: AvosLocker Victim Onion Service on the Tor anonymous network (captured July 8, 2021)
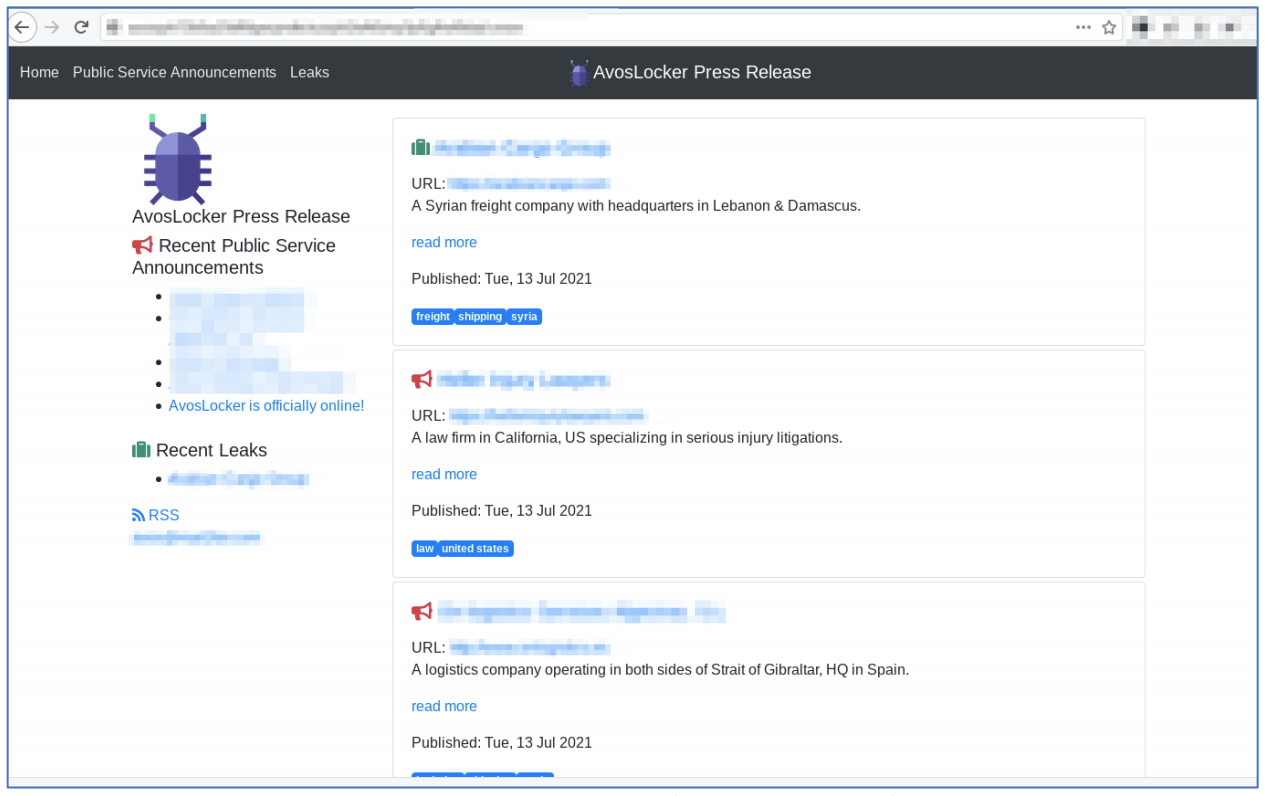
The new onion service – collected by DarkOwl automated crawlers on the Tor anonymous network earlier this week – lists at least six victims consisting of a mixture of transportation and logistics corporations and legal firms across the globe.
Editors note: DarkOwl has intentionally chosen not to disclose the victims’ names and has sanitized all mentions of victims in the screen captures below included in this piece
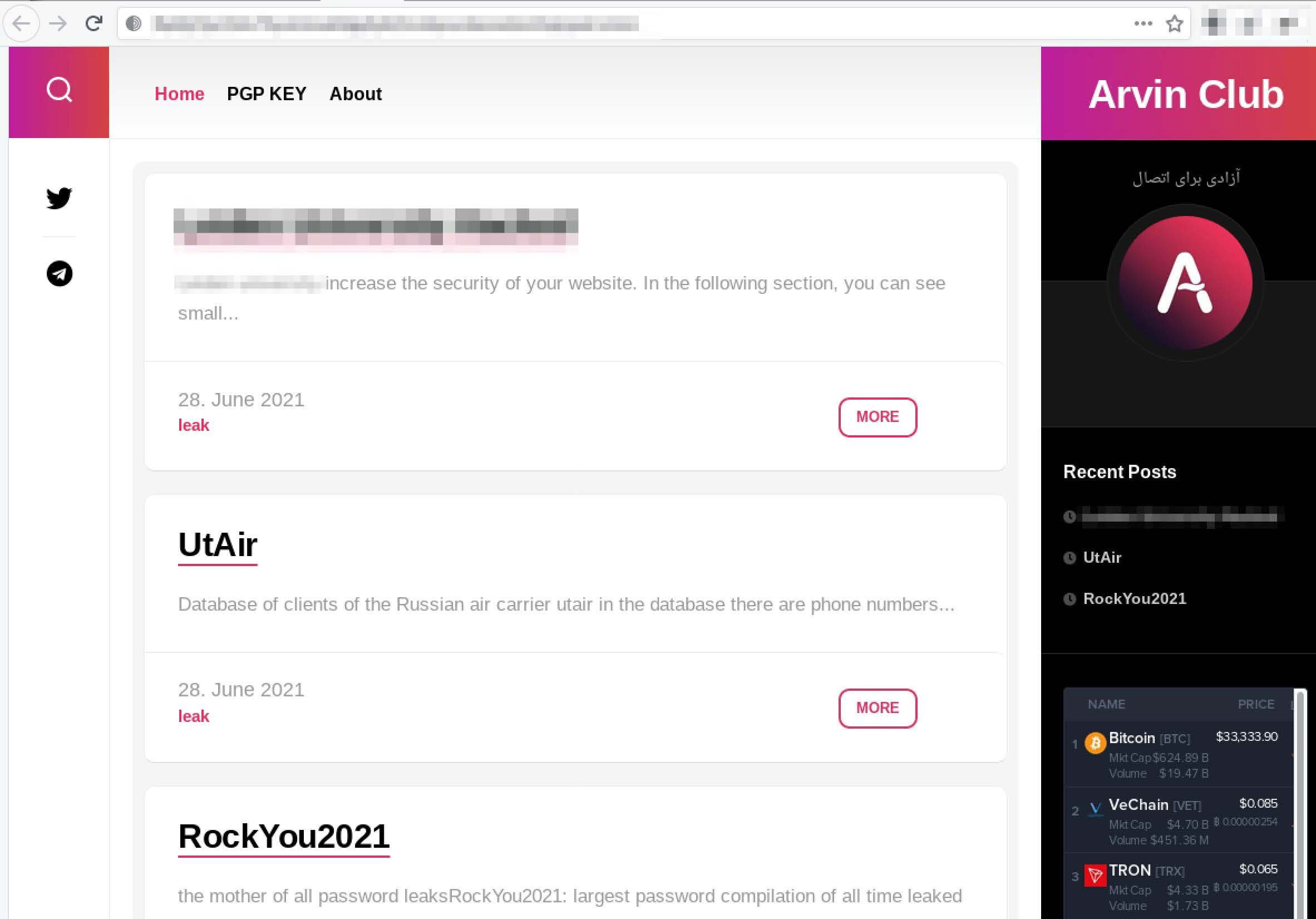
Figure 2: AvosLocker Press Release Onion Service on the Tor network (captured July 13, 2021)
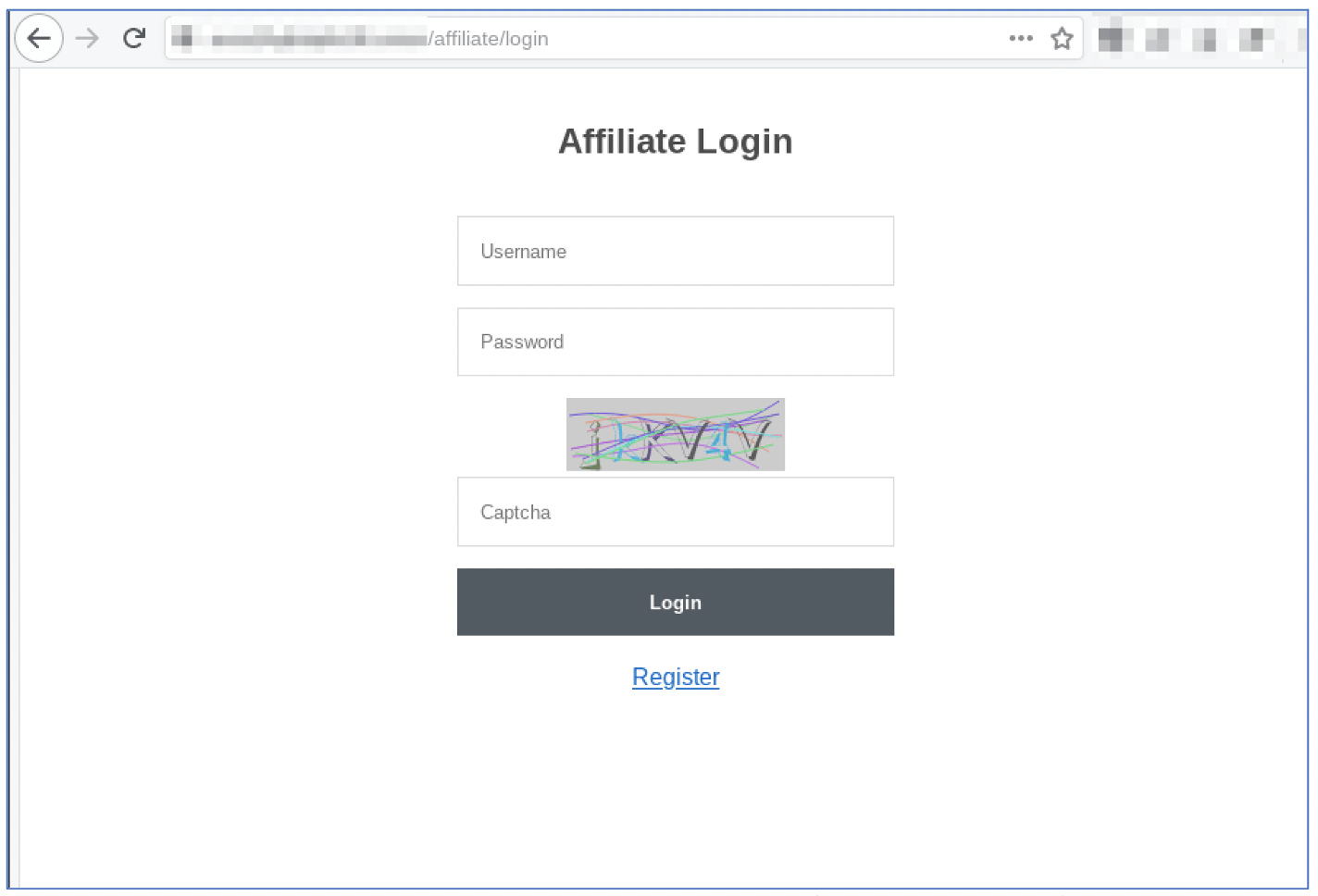
DarkOwl also detected an AvosLocker affiliate registration and login portal on their original v2 Tor service. The registration form indicates AvosLocker issues invitation codes for access to the domain.
There is no mention of AvosLocker or their logo on the affiliate-related portal onion services (pictured below).
Figure 3: AvosLocker Affiliate Login Portal on the Tor anonymous network (captured July 15, 2021)
Returning back to AvosLocker’s debut of their new, branded onion service, it is worth noting that ransomware operators set up public PR-oriented blogs for any number of reasons:
-
They are truly a brand-new ransomware operator conducting ransomware campaigns against victims, employing a unique ransomware encryption cipher, as well as other tactics, techniques and procedures (TTPs);
-
They are an existing RaaS affiliate with enough profitable and successful operations to warrant their own victim shaming Tor service; or
-
They are a seasoned ransomware operator who is intentionally attempting to obfuscate their operation’s identity by rebranding and changing aliases of key members.
The fact AvosLocker is operating as a RaaS gang employing the traditional “affiliate” model – as noted by the login portal above – means it is highly unlikely they are an affiliate of an existing RaaS group and more likely a rebranding of existing RaaS operator.
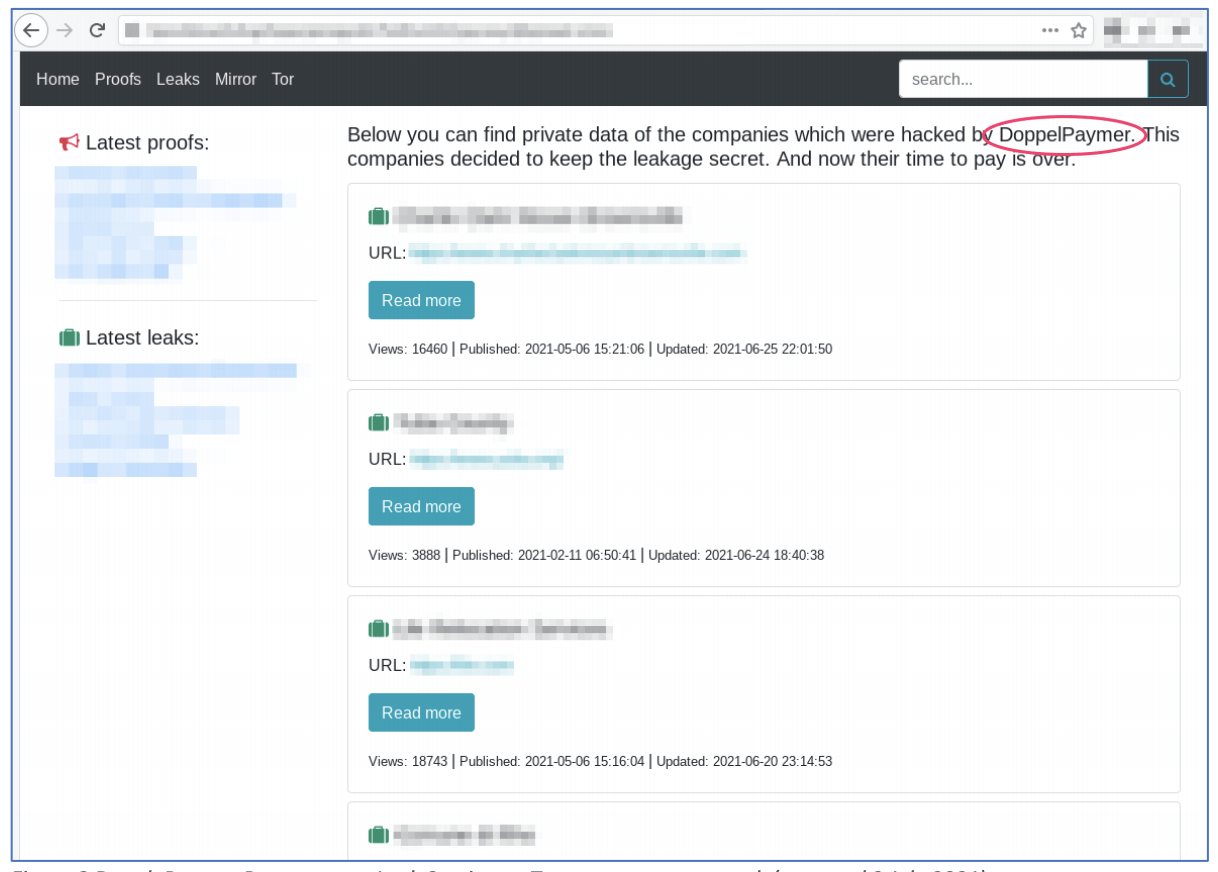
Accompanying this theory, DarkOwl analysts quickly observed that the AvosLocker’s new service has striking resemblance to other websites established on Tor, more specifically the infamous Doppelpaymer RaaS gang.
DarkOwl has no indication that AvosLocker is an affiliate of Doppelpaymer, or if it has merely copied the HTML/CSS templates employed by the Doppelpaymer group; it is not uncommon for hosts of Tor onion services to create websites that look and feel like previously published services.
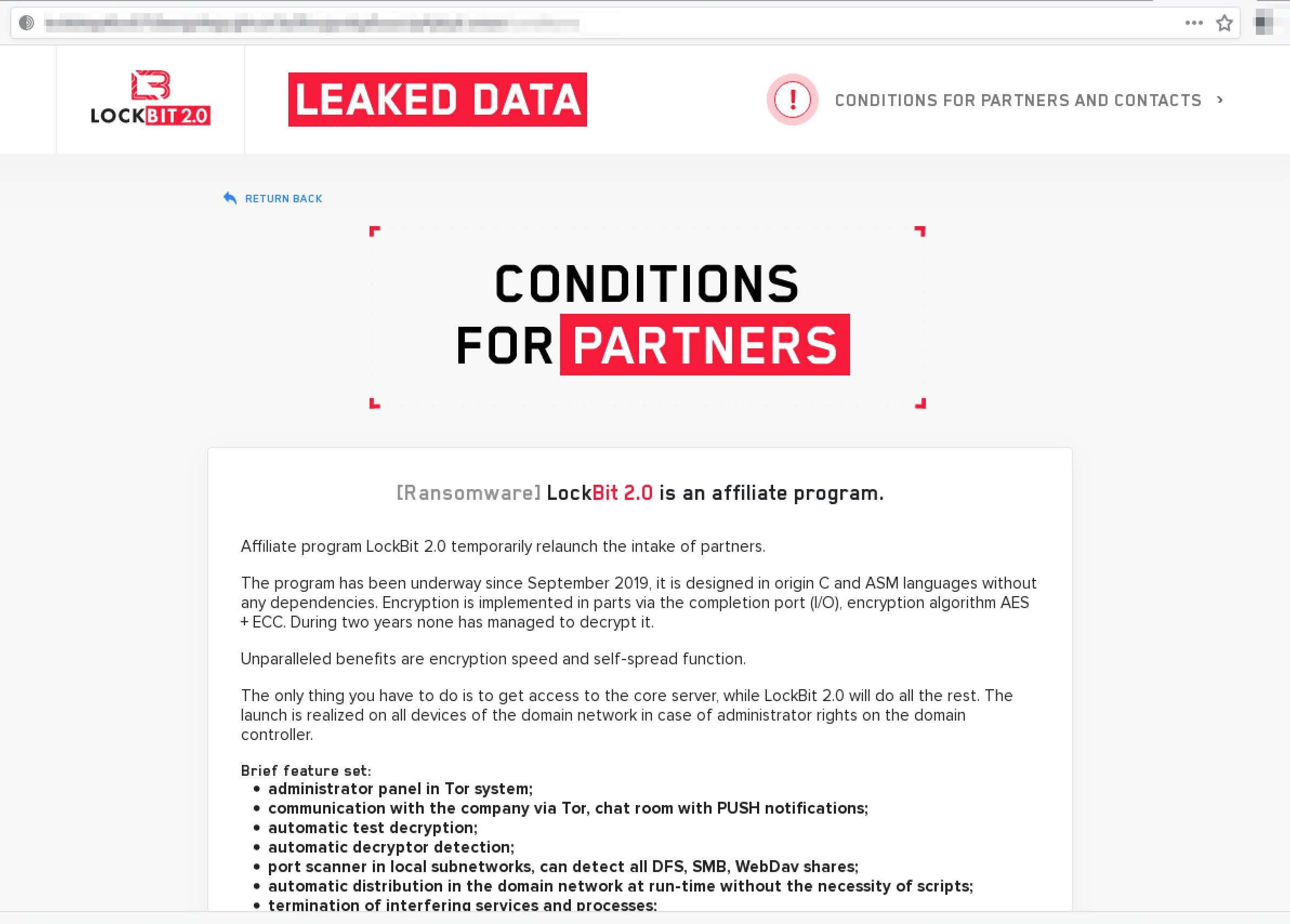
In contrast to the AvosLocker’s service, the Doppelpaymer leaks service on Tor requires the visitor to solve a reCAPTCHA and enable Javascript for the domain to load properly.
Figure 4: DoppelPaymer Ransomware Leak Service on Tor anonymous network (captured July 2, 2021)
Doppelpaymer has plenty of justification to rebrand their operations, but there is insufficient evidence at this time to confirm AvosLocker is their new brand. In December of 2020, the FBI issued a warning against the Doppelpaymer RaaS gang after a series of attacks last fall in Europe resulted in the death of healthcare patient in Germany. (Source)
The last victim posted on the Doppelpaymer leak service is dated back to May of 2021, and the last one before that was in February. This might suggest Doppelpaymer could be slowing down its operations to avoid additional scrutiny from the media and law enforcement.










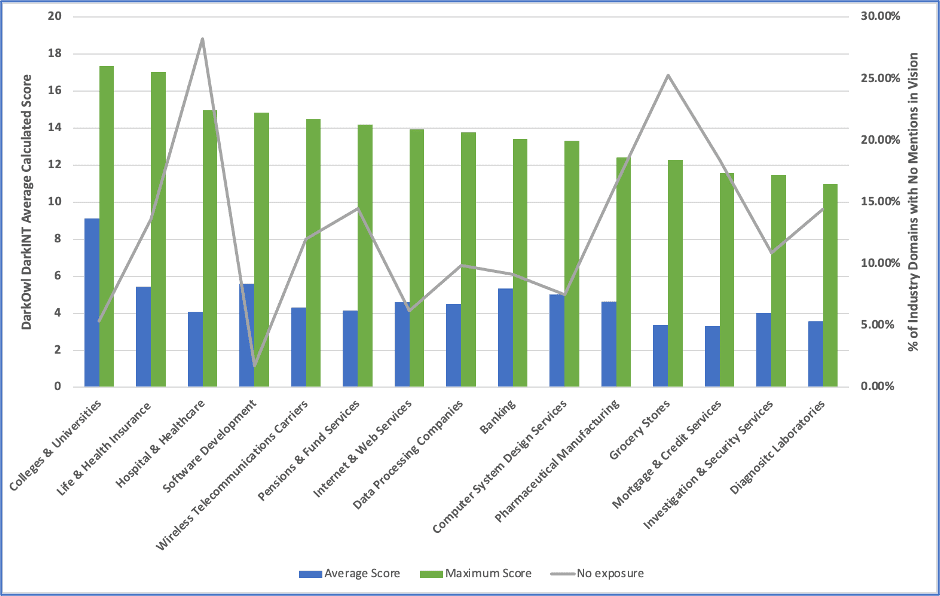
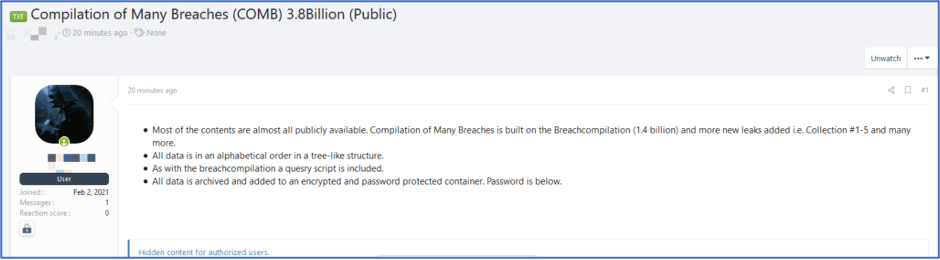
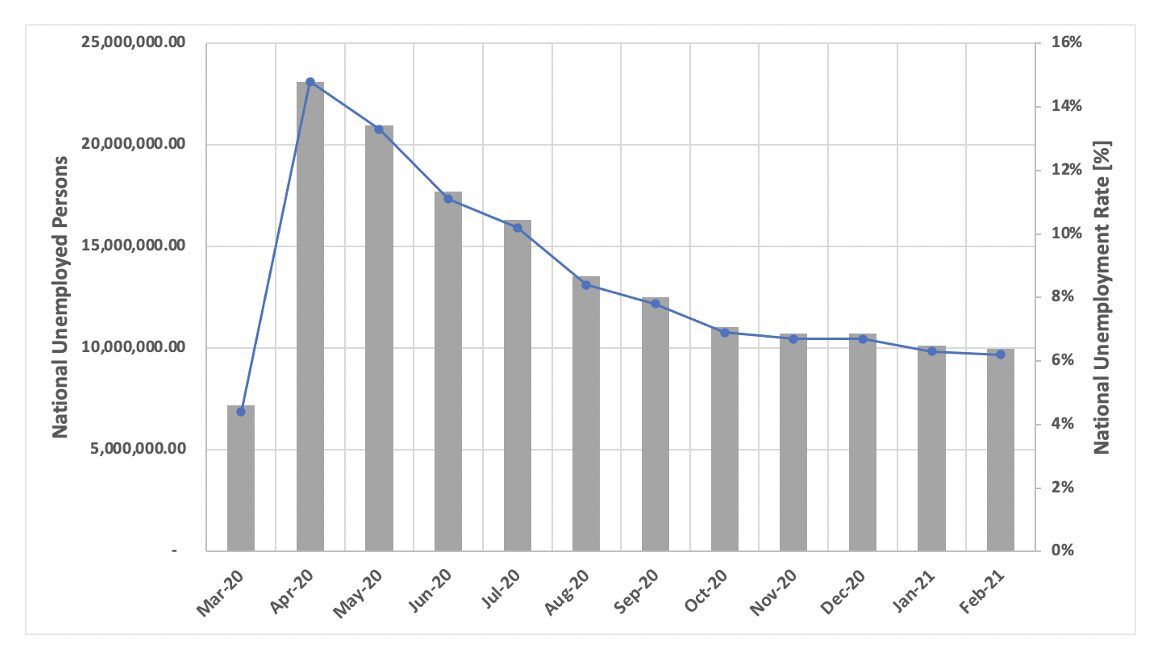
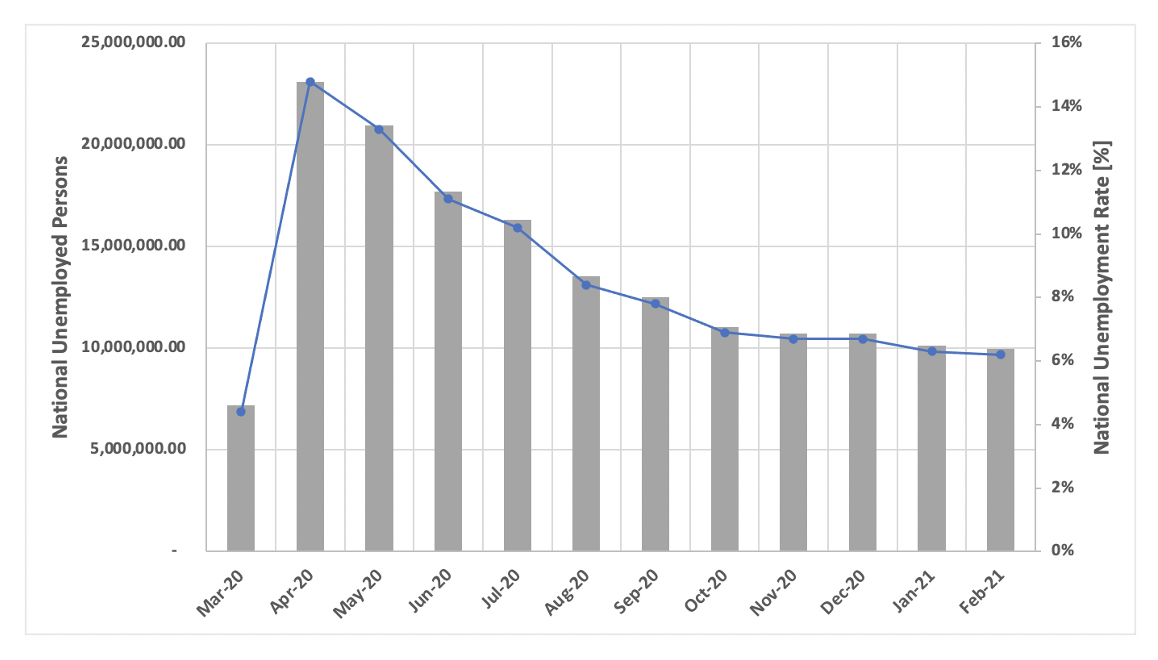

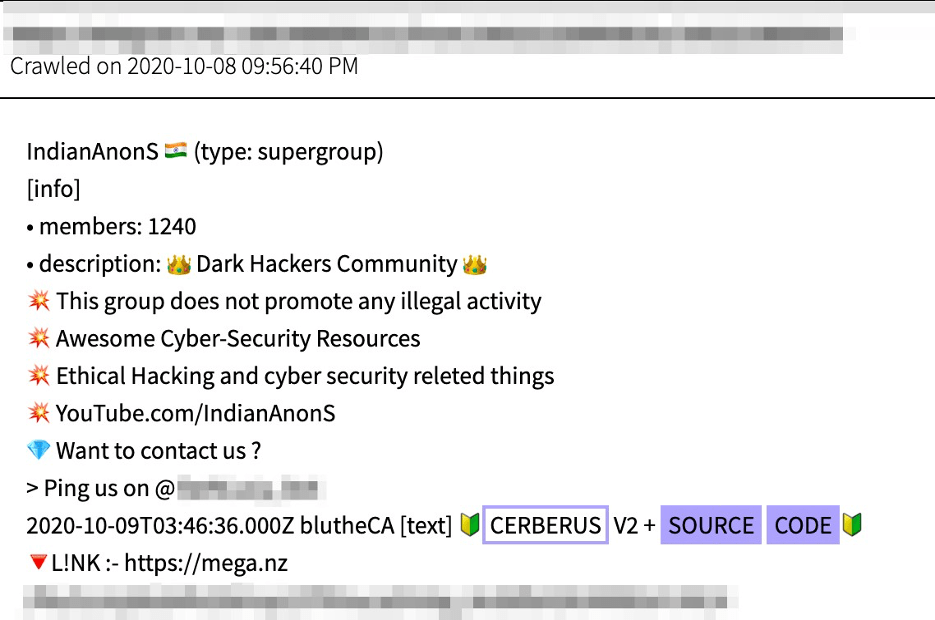

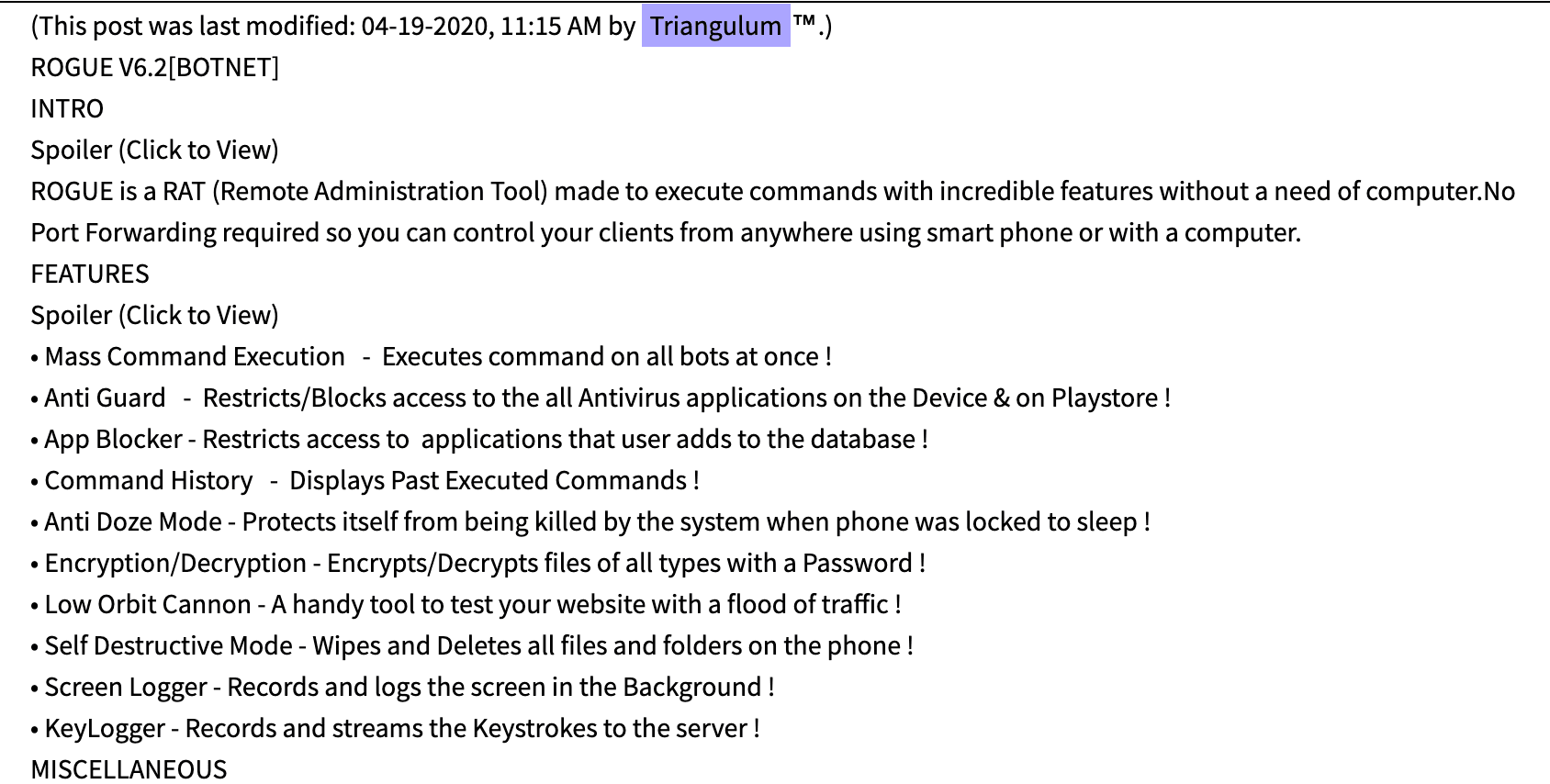
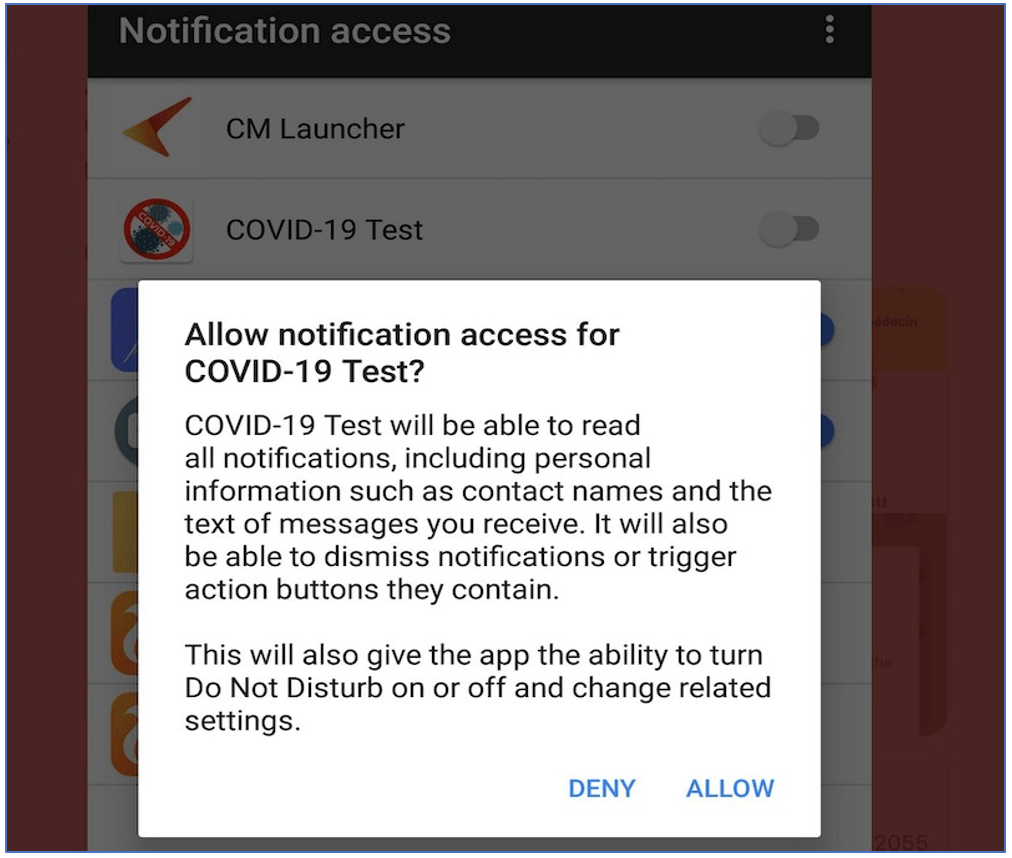

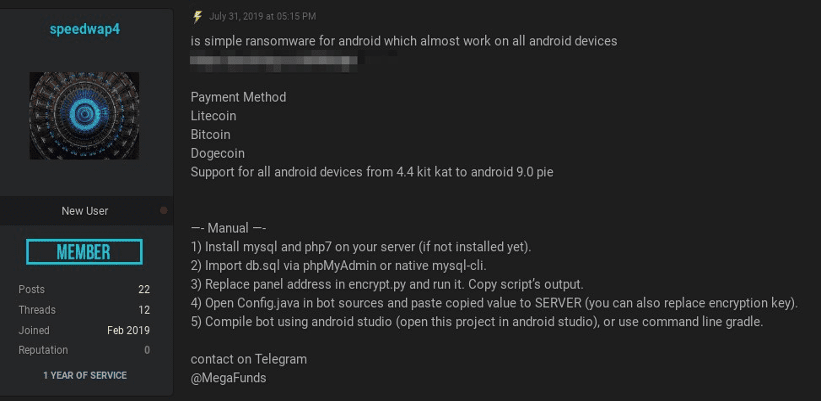
![Figure 11: “[Fud]APK Crypter” for sale (Source -DarkOwl Vision)](https://www.darkowl.com/wp-content/uploads/2021/12/mw11.jpg)