Darknet Indicators of Anomalous Health Incidents (AHIs)
The U.S. Department of State and three-letter agencies across the U.S. Intelligence Community – which staffs a mixture of darknet intelligence and open-source intelligence (OSINT) researchers across a variety of security sectors – have had increasing concern by reports of what the U.S. Government identifies officially as “anomalous health incidents” (AHIs). The news media has generally labeled these incidents as reports of “Havana Syndrome,” due to the fact that the location of the first reports originated from diplomats located at the U.S. embassy in Cuba in 2016, but continues today around the globe.
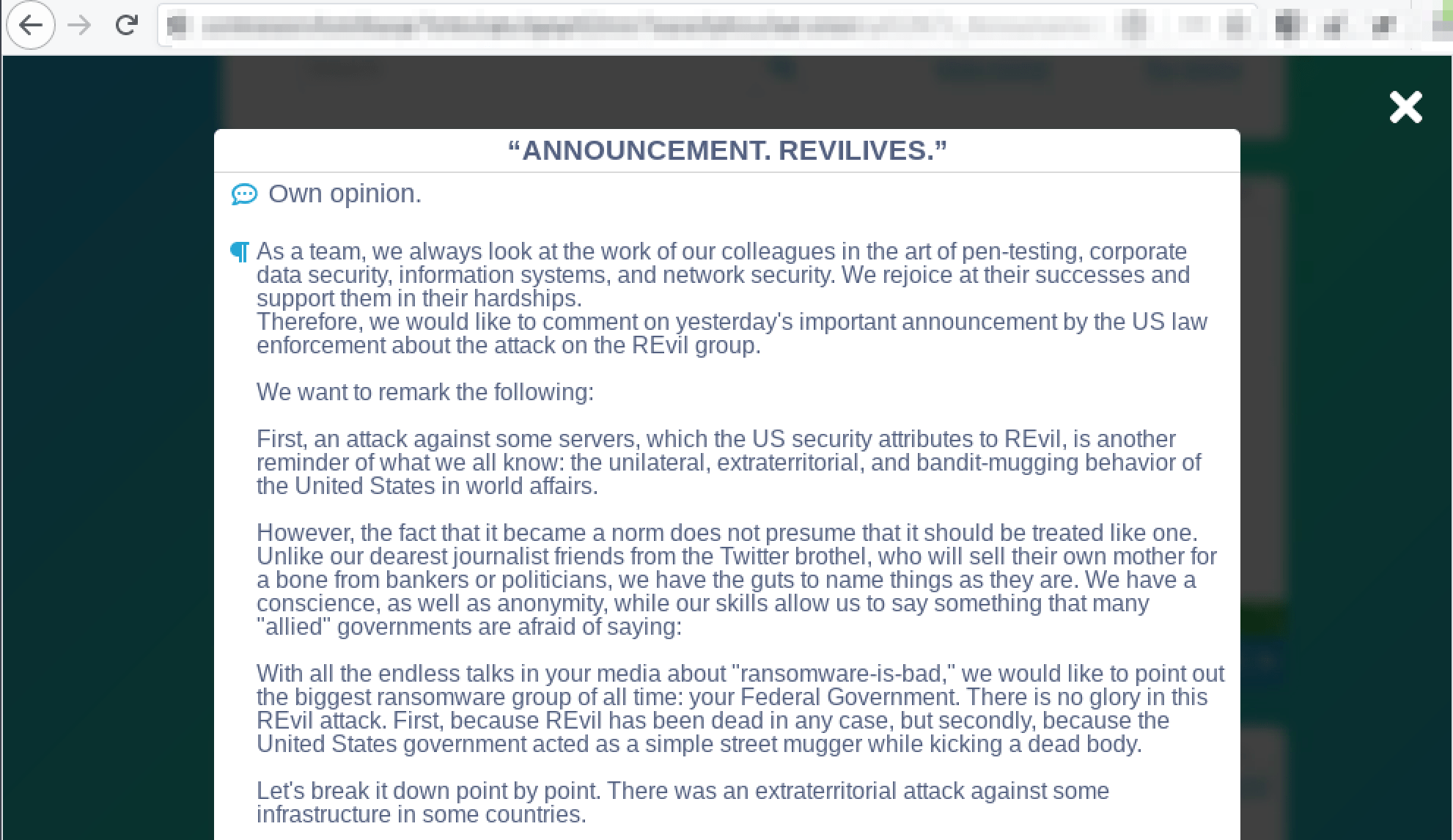
An interim intelligence report on the subject was recently released by the CIA after President Biden’s call for answers as to the cause of the incidents and Congress passed the HAVANA Act last fall to help compensate victims. The report, briefed by government officials to POLITICO in mid-January, has received criticism for its “preliminary” intelligence assessment, which concluded no U.S. foreign adversary nor specific directed energy weapon is likely behind the nearly 1,000 allegedly directed attacks against government personnel stationed in embassies around the world.
Given the lack of inter-agency coordination on the interim report, it’s unclear whether these findings signal a finale to USG’s overarching investigation. According to open source reporting, there are still several cases the CIA could not explain and CIA Director William Burns issued a statement suggesting the agency will continue to look into the matter.
“We have reason to believe the interim report does not even represent the consensus of the full CIA, instead reflecting the views of a subset of officials most interested in resolution and closure.” - Statement from CIA Director William BurnsRecognizing the uncertainty of the findings and widespread outrage from AHI victims, DarkOwl sought out to gather and assess data across the darknet and deep web to provide supplemental indication of the public sentiment regarding AHIs, as well as additional insights into the potential technological sources that may be targeting diplomats and intelligence officials.
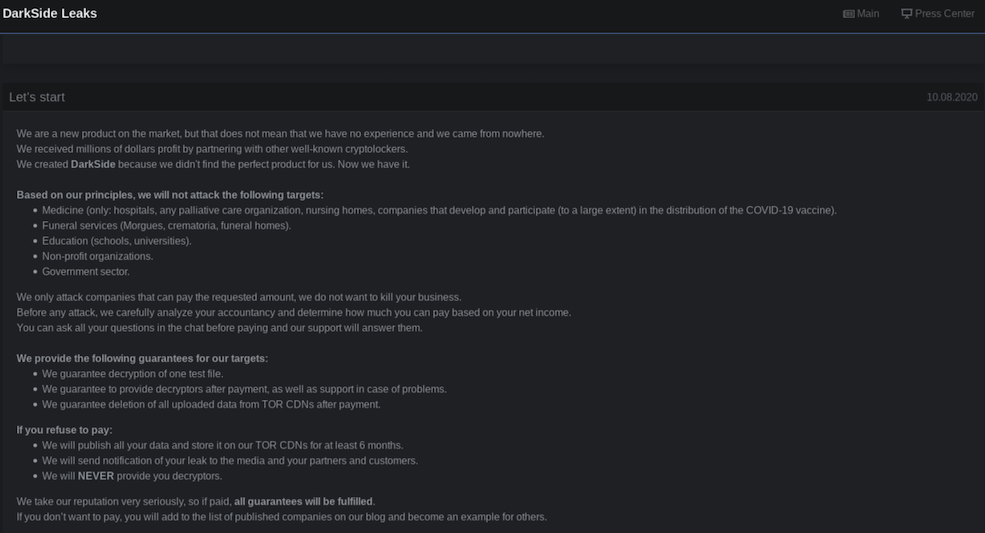
Chatter Spreading Potential Nation-State Sponsored Propaganda
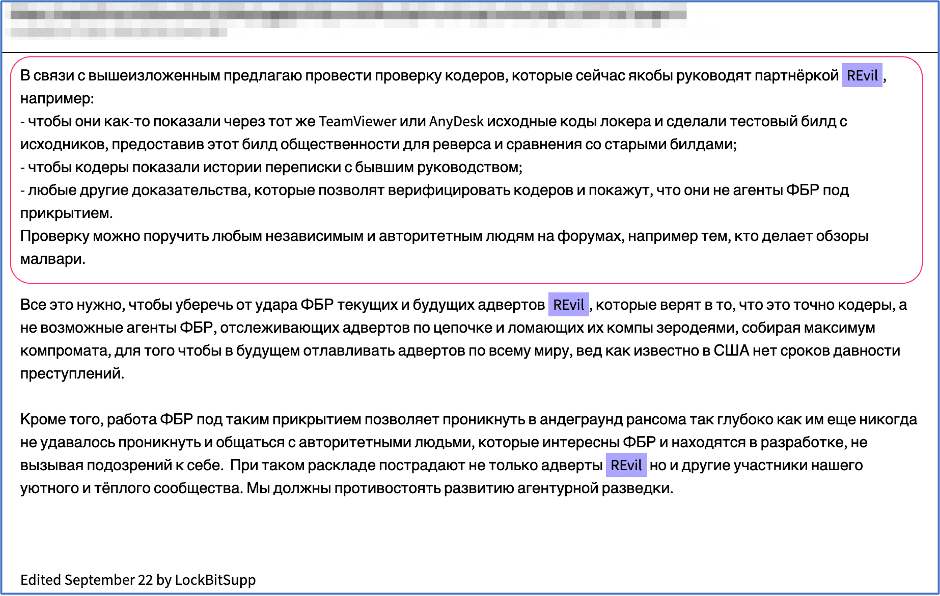
During our research, we discovered indications of deep web users sharing Russia-sponsored anti-US propaganda related to mind-control and directed energy induced schizophrenia. For example, one user shared a link to content of this nature via a WordPress “blog” that directly references and links to an “independent research news website” called “Global Research” (globalresearch.ca). In 2020, the State Department identified the allegedly Canadian news outlet as a Russian controlled propaganda front.
-
According to DNS records, the WordPress blog domain cited (youarenotmybigbrother.blog) on the deep web is hosted on a server located at the IP address: 192.0.78.24/25, located in San Francisco, California.
-
DarkOwl reviewed the “Canadian” Global Research website for mentions of “Havana Syndrome” and surprisingly found no recent mentions of “Havana syndrome” or AHIs or any official neurological research, but instead found multiple re-shares of articles citing a study from the University of Edinburgh directly contradicting the State Department’s 2018 commissioned report from the University of Pennsylvania, peer reviewed and published by the Journal of the American Medical Association (JAMA).
-
The general lack of reporting related to Havana Syndrome on the Global Research website, including disinformation suggesting the incidents are caused directly by the USG or non-foreign directed energy sources, is significant and warrants further analytical review of other known Russian-sponsored propaganda websites.
-
Since the release of the interim CIA report last week, darknet and deep web users are aggressively re-sharing articles and podcasts “debunking” the idea of Havana Syndrome entirely as a mass psychogenic illness resulting from an internal U.S. government propaganda disinformation narrative to demonize Russia and destabilize to US-Cuba geopolitical relations.
Some deep web users hypothesize the remote possibility that US adversarial governments – such as Russia and China – use lower earth orbit satellites and even cellphone towers to direct nefarious RF signals attack targeted individuals.
-
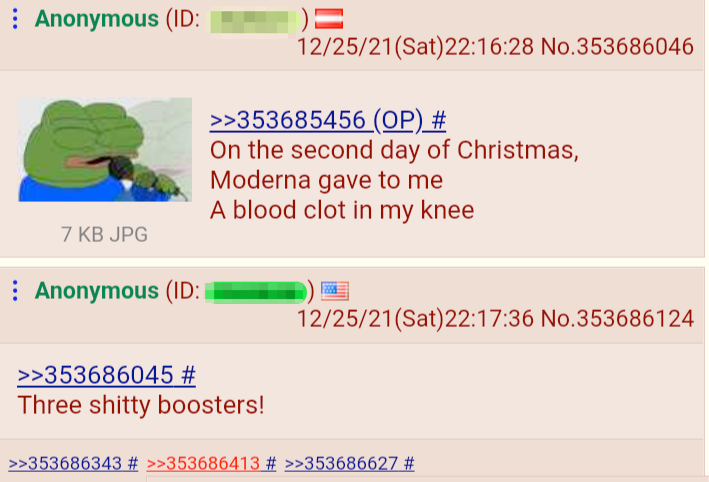
In summer 2021, an anonymous user of the deep web imageboard known as 4chan, theorized that AHIs are caused by Russian space assets or US-based cell phone antennas that have been potentially converted into a microwave microphone to detect speech and inadvertently over-amplifies the signal causing brain damage. Other users of the same forum also imply that these attack vectors could be deployed by the US against their own personnel as part of some sort of covert operation.
-
On the subreddit /r/TargetedEnergyWeapons, Reddit users shared video from a 1985 CNN news report of a U.S. based RF directed energy weapon called the “Brain Bomb” that the U.S. government reportedly never pursued to discredit the USG.
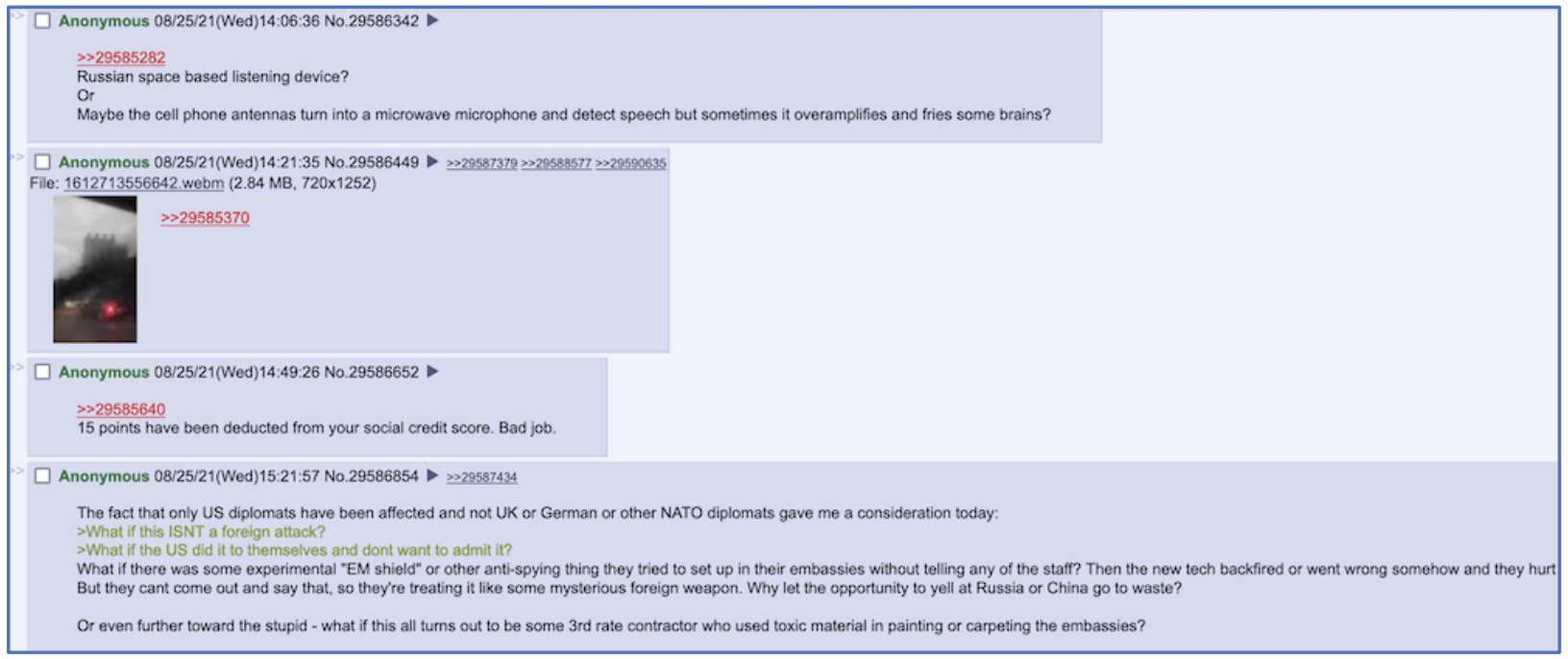
4chan discussion about “Havana Syndrome” being caused by Russian-space listening devices (original thread removed by website since discovery)
Technical Materials Related to AHIs on the Darknet
Our analysts identified numerous mentions of the US government’s historical activities related to psychotronic and psychological warfare. Several deep web users circulated “blogs” – dating back to 2010 – that include a comprehensive archive of information related to potential neurological and psychological weapons developed by DARPA and the US Military as well as similar tools at the disposal of Russian intelligence arms.
The aforementioned blog highlights reports from the early 2000s that Putin supposedly outlawed the use of weapons of psychotronic influence with the intent to cause harm, despite the fact psychotronic weapons were specifically mentioned in open-source reporting of Russia’s advanced weapons state procurement plans outlined for 2011-2020.
“The development of weaponry based on new physics principles; direct-energy weapons, geophysical weapons, wave-energy weapons, genetic weapons, psychotronic weapons, etc., is part of the state arms procurement program for 2011-2020”
DarkOwl analysts also observed numerous darknet and deep web users discussing and resharing a 1976 declassified intelligence report from the Defense Intelligence Agency titled, “Biological Effects of Electromagnetic Radiation (Radiowaves and Microwaves) Eurasian Communist Countries (U).”

Segment from declassified 1976 DIA report shared on the darknet
Another report shared across darknet and deep web users originated from the U.S. Army and dates back to December 13th, 2006 . The report was released through an official Freedom of Information Act request by a Mr. Donald Friedman of California, USA.
The document contains an unclassified addendum to another intelligence assessment, which was developed by the National Ground Intelligence Center (NGIC) and likely originated in the late nineties, based on the document number. The US Intelligence Community downgraded the report from SECRET//NOFORN and details the “Bioeffects of Select Nonlethal Weapons”.
Darknet users referencing this report generally used it as supporting evidence that the US military has extensive research on the effects of microwave radiation for battlefield and crowd control use. Like the March 1976 report, the NGIC intelligence reporting regarding the effects of directed pulsed radio-frequency correlate with the symptoms experienced by diplomats and intelligence personnel reporting AHIs.
The report also identifies that the associated technology is readily commercially available, but would need to be customized for intensity variability and targeted use.

US Army response to 2006 FOIA request dated, 13 December 2006.

Segment from the NGIC report detailing the technology’s biological influence on the subject.
The NGIC report further identifies auditory phenomenon experienced by subjects, e.g. “clicking, hissing, ticking, and buzzing” consistent with the 2018 JAMA report consolidating the findings from the University of Pennsylvania clinical study of AHI victims. These symptoms are near identical to symptoms connected with the “Frey Effect,” discussed extensively across chat platform users and Reddit discussion forum participants as well as research conducted by the Robert Lansing Institute.
“Ability to hear the “sounds” depends on high frequency hearing and low ambient noise. Pulsed RF/MW in the 2.4-10,000MHz range produces perceived noises that resemble sounds “such as a click, buzz, hiss, knock, or chirp”–just as diplomats report. ”

Segment from the NGIC report detailing the technology’s biological influence on the subject.
One darknet Tor service we identified has over 1,400 technical documents detailing numerous radio frequency (RF) and directed energy (DE) based technologies utilized for such subjects as: mind control, remote viewing, psychoacoustic effect, and electronic surveillance.
Much of the content includes academic research and intelligence agency and military documentation as well as biographies of key academic and intelligence researchers in paranormal studies and mind control related topics. The originating domain has not been online since November 2018, but all available content from the domain is archived in the DarkOwl Vision database of historical darknet records.

Source DarkOwl Vision (DocID: 68eafa7fafe9be29be48f419d8c1fb89b4fa5707)
On another user on Tor posted a report as recently as late August 2021, describing US Navy sound-based non-lethal weapon program. According to the post, this program utilizes a recording of the target’s own voice, captured with a long-range microphone, that the system distorts by applying phase shifting and auditory track overlay and feedback.
The weapon, called the Acoustic Hailing and Disruption (AHAD) system, then transmits the high intensity auditory signal directly back to the target using a parametric speaker, disorienting them to the point of they are confused and cannot speak.
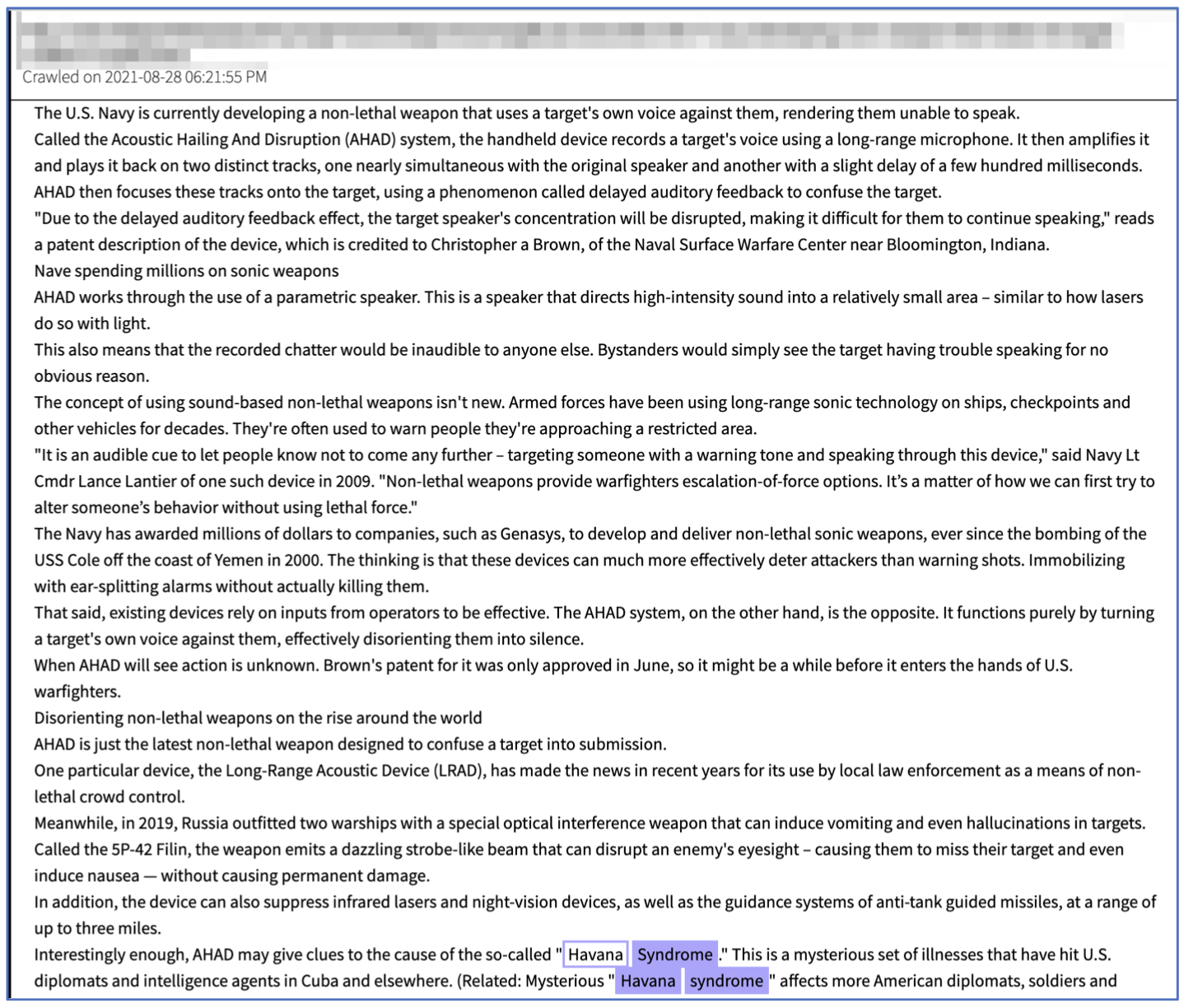
Darknet post detailing US and Russian non-lethal weapon technologies. (Source: DarkOwl Vision – DocID d75544cb73549b3db675562290debec678700692)

A darknet discussion forum user talks of Active Denial Systems (ADS) to cause a sensation of being on fire for crowd control. (Source: DarkOwl Vision – DocID 1b851c844c50ed2099adce8ba48e4963146dc6b3)
The same darknet service also highlights a similar technology called the 5P-42 Filin that has purpotedly been in production since 2019 by the Russian military. This technology allegedly uses a pulsed beam of light to disrupt a target’s vision and cause temporary nausea.
According to additional open-source reporting, the Filin, also known as the “Eagle Owl” in Russian, was originally manufactured for use on large naval warships and frigates by Russian state military contractor, Ruselectronics, and considered a “weapon of mass disorientation.”
A ground-based portable version of the same system is in development (if not already in production) for use by special forces in close-combat anti-terrorism operations.

Brochure detailing technical specifications of the Russian 5P-42 Filin Weapon System. (Source)
AHIs on the darknet and deep web: AHI technologies for sale and hobbyist experimentation
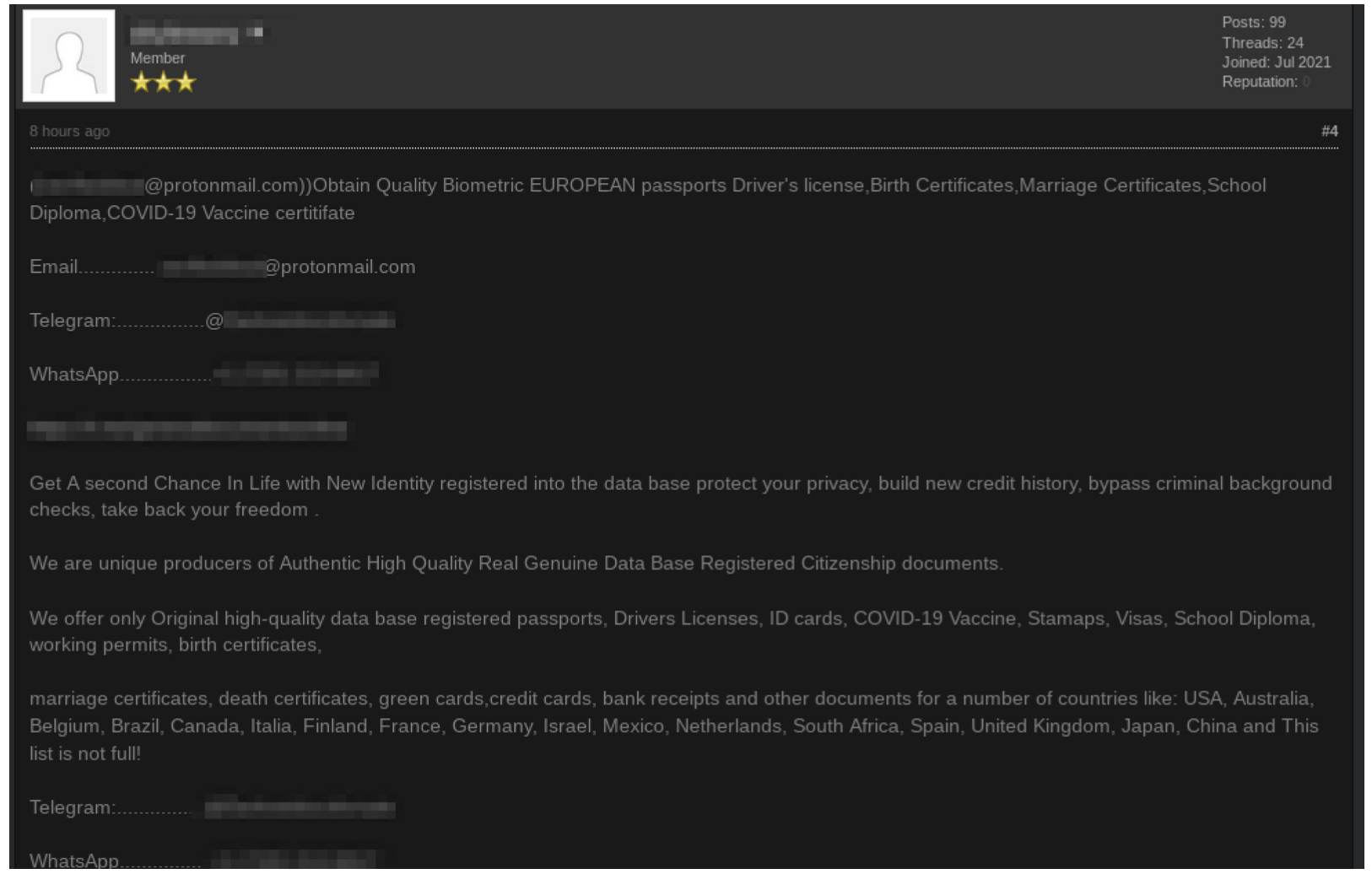
DarkOwl analysts also observed that EMF-based technologies and associated hardware could be purchased from darknet marketplaces and improvised using COTS products to conduct targeted rogue AHIs and human neurological experimentation.
During the course of our investigation, we also uncovered evidence of electromagnetic frequency generators, designed for jamming wideband telecommunications signals such as: GSM, LTE, and GPS for sale on darknet marketplaces for under $500 USD.
With the knowledge provided across other darknet and OSINT sources about ADSs, the device could be easily improvised and repurposed for a malicious objective. DarkOwl detected an advertisement for limited quantities of a military-grade frequency jammer in September 2020 for $1,200 USD.
The documents shared on that darknet domain includes specific frequencies and intensities of unique RF and DE waveforms to cause specific bioeffect and could be easily replicable by hobbyist electrical engineers with access to darknet and deep web content.
In one circumstance, a San Francisco-based Medium user known as “Jay” has purportedly been “targeted by DEW [directed energy weapons] for the last four years” and has since been researching directed energy extensively to better understand the threat. As of November 2018, he had concluded the frequency of the threat fell within the range of 18 and 50 GHZ conducting measurements with commercially off the shelf (COTS) Narda and Trifeld electromagnetic frequency (EMF) meters.
Other deep web sites also include posts with detailed step-by-step instructions for how to make “Home Made” Active Denial Systems using commercially-available 2.4GHz wavelengths using items readily available inside someone’s residence. The author implies the length of the 2.4GHz waveforms can remotely induce headaches, fevers, cataracts, or other chronic-fatigue symptoms in a human target.
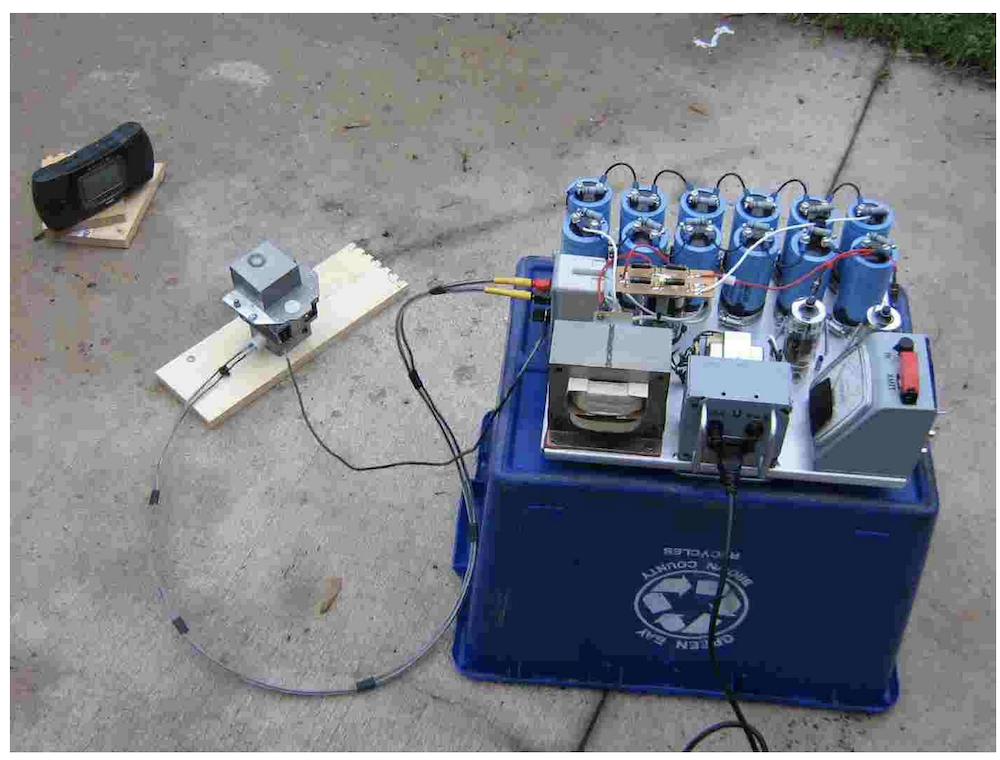
“Home Made” Directed Energy Weapon described on the deep web (Source redacted for security purposes)
AHI conspiracy theories on the darknet and deep web
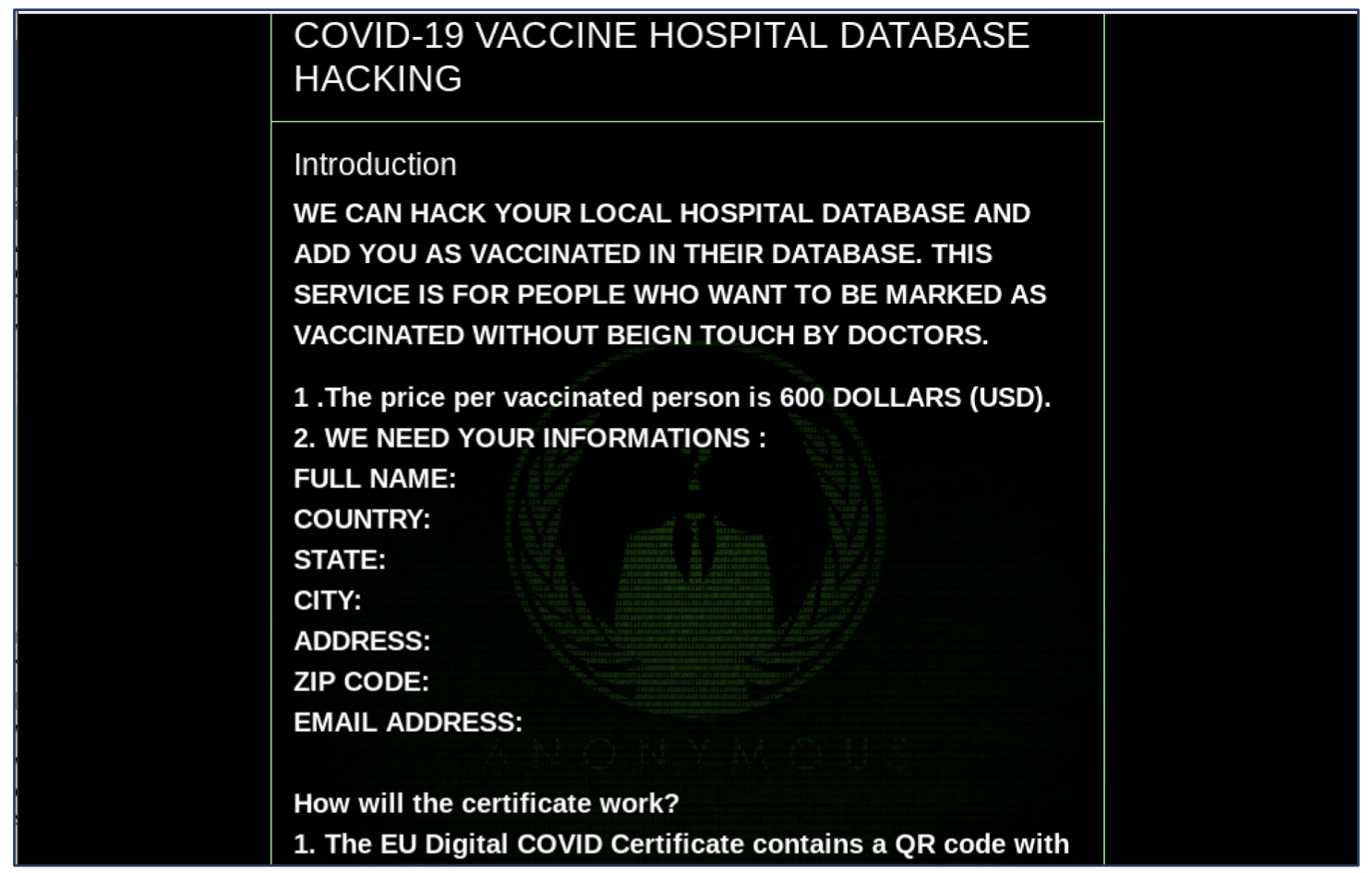
At the conclusion of our analysis, we determined that most of the content related to AHIs from underground darknet and deep web sources is driven by conspiracy theories. For example, in July 2021, one user on a Telegram channel postulated that “Havana syndrome” and “Monkeypox” were a concerted agenda to cover up adverse reactions from the COVID vaccination.
By and large, this type of fear, uncertainty, and doubt is widely circulated and quite popular across the deep web, in particular, “anti-vax” communities and clearly not remotely accurate, given AHIs were recorded well before the COVID-19 pandemic.
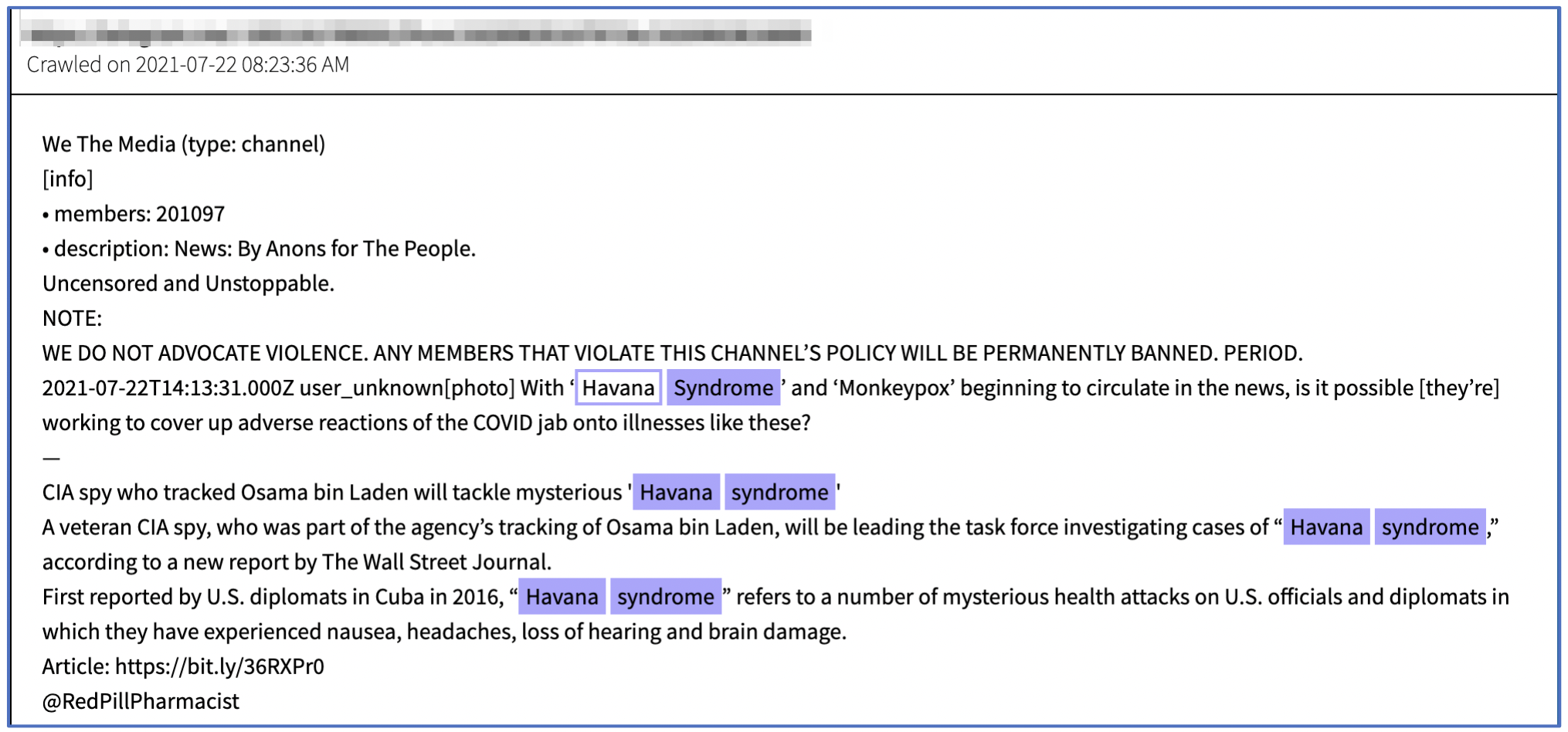
Source DarkOwl Vision DocID: 5c860642d80f221e6a86199fb915877285140bea
Long before reports of AHIs surfaced in public news media, the darknet and its associated underground communities housed a considerable population of anti-government advocates with deep rooted beliefs in a “deep-state” – including the notion that western governments sanction and/or actively conduct non-consensual psychological and neurological experiments on its populations.
Believers are equipped to evangelize other forum and chatroom members, armed with reports relating to government projects like Mk Ultra, NSA’s TEMPEST, and “Silent Talk” and detailed research pertaining to peripheral topics such as synthetic telepathy, active denial systems, and psychotronic influence. Many times, such users are quickly labeled “tin-foiled hats” and easily dismissed; however, DarkOwl analysts have witnessed their influence increase since the Guardian published information leaked by Edward Snowden and increased circulations of reports of AHIs outside of Cuba and China.
Some darknet discussion forum users assert they had been directly attacked with directed energy attacks in a similar fashion to AHIs of deployed State Department personnel. There is no way to confirm the veracity of such statements.
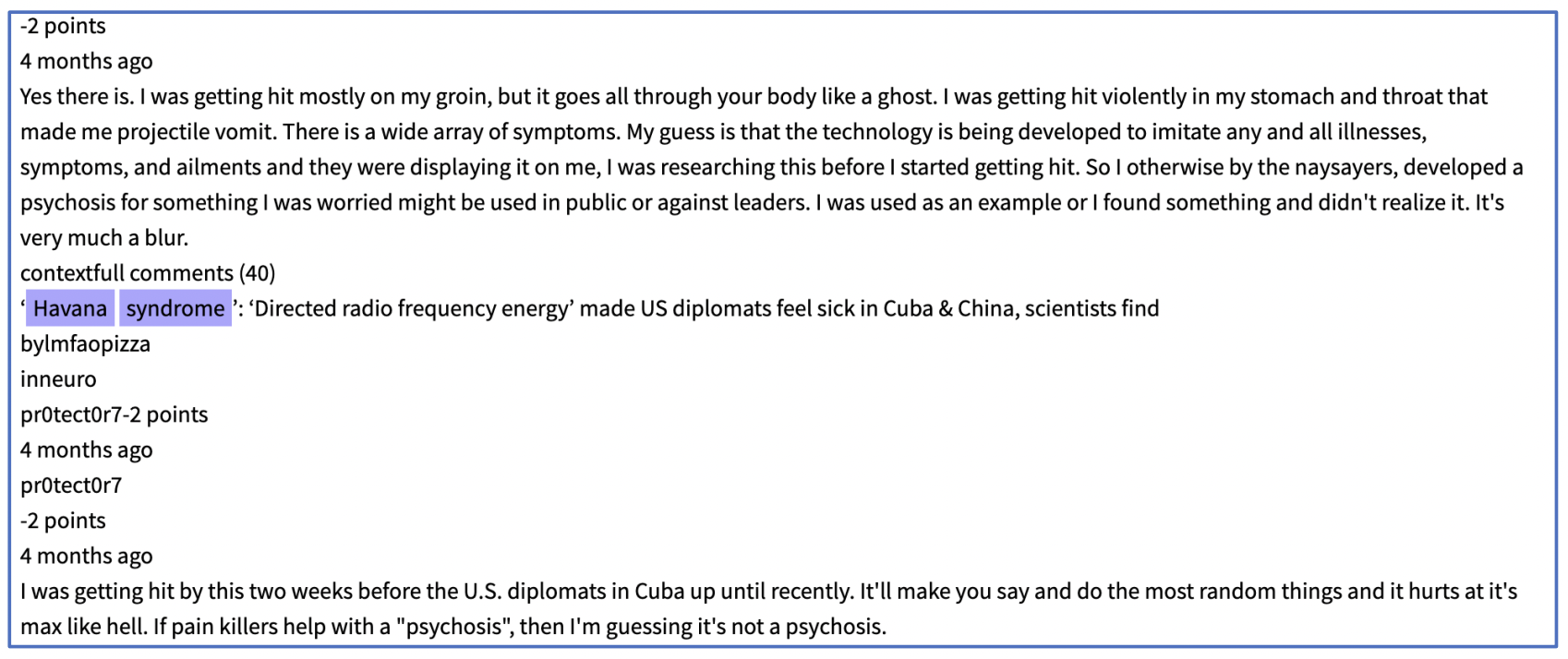
Darknet users discussing the Havana Syndrome (Source: DarkOwl Vision -DocID: 47c5b3b89f1176fe6f025b3346af860fcb680d49)
Some deep web users have also been circulating blog content from the surface web that supports the idea of a global New World Order with the ability to control mass populations and targeting individuals with AHI for a specific and often nefarious agenda. Users point to the persecutory delusion known as “gang stalking” and associated websites replete with technical and academic content in attempt to legitimize their conspiracy theory and their perception of being targeted directly by the government.
-
According to DNS records, the blog referenced above (gangstalkingmindcontrolcults.com) is hosted on a server at the IP address: 192.124.249.178 and is located in Menifee, California.
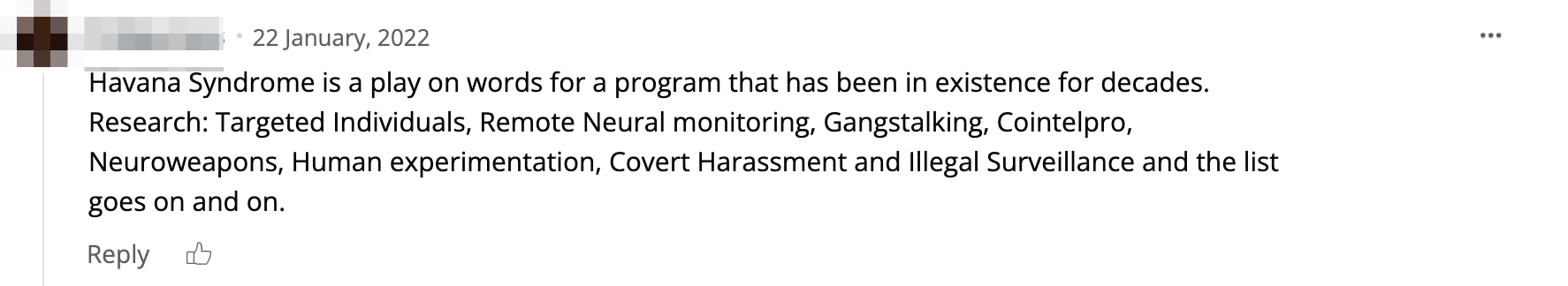
Conclusion
During the course of our research, our analysts identified a significant quantity of Havana Syndrome-related information across numerous sources in the underground. Much of this information is directly tied to anti-US propaganda, disinformation campaigns, and baseless conspiracy theories. However, there is also legitimate information on active denial directed energy weaponry circulating in a violence-inciting atmosphere on the deep and dark web, which can easily enable and embolden an ordinary person’s ability to successfully carry out sinister attacks using AHI technology.