Election Disinformation Warnings Prominent
The U.S. government and its intelligence community of agencies publicly acknowledge the active dissemination of, and subsequent impacts caused by sharing, misleading information up until the election date and the days immediately thereafter. In recent weeks, both the CIA and FBI have published warnings in relation to foreign actors spreading disinformation around the imminent 2020 Presidential Election with the intention to discredit the elections’ legitimacy warning the public on sharing online content across social media networks. (Source)
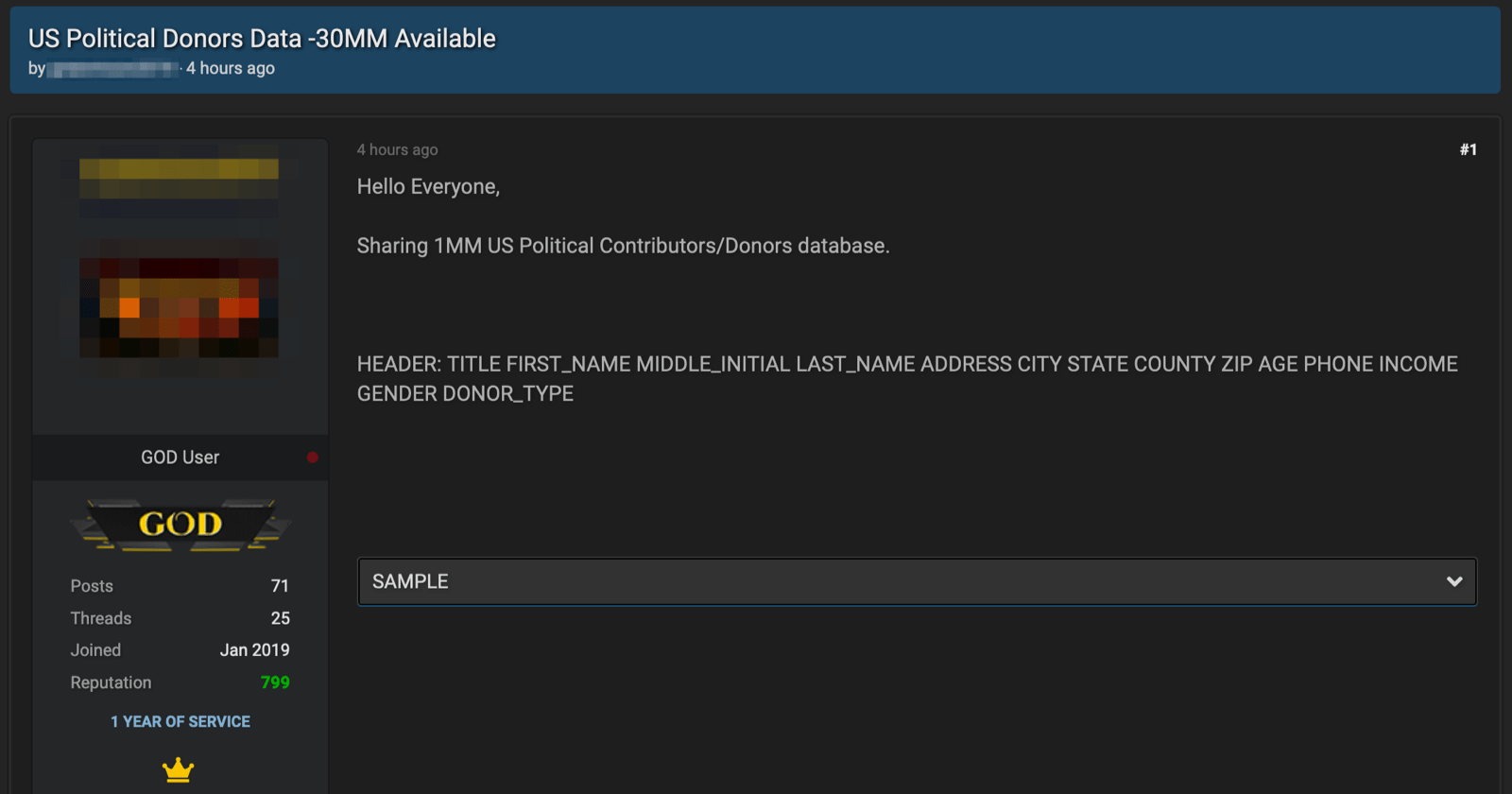
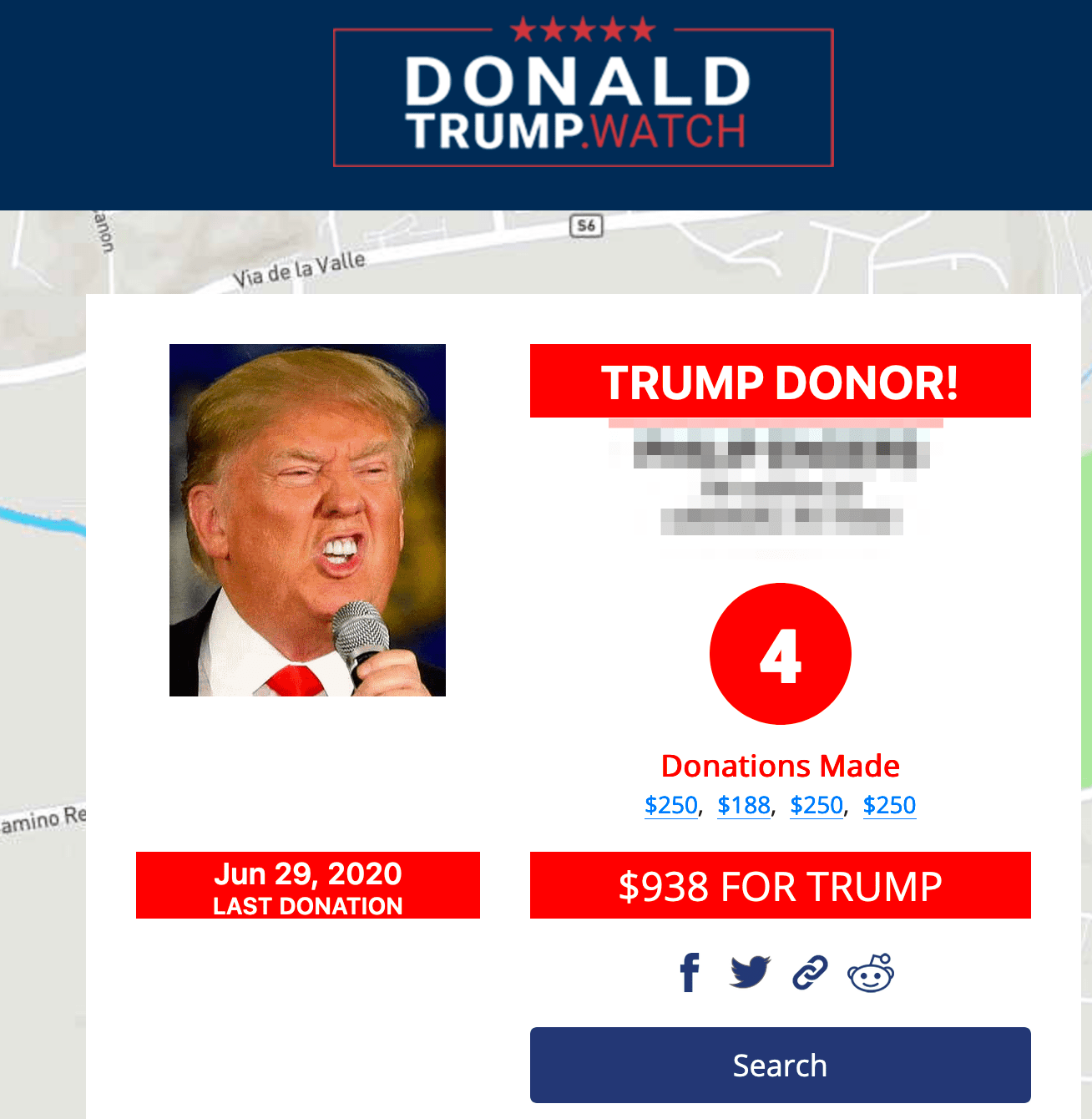
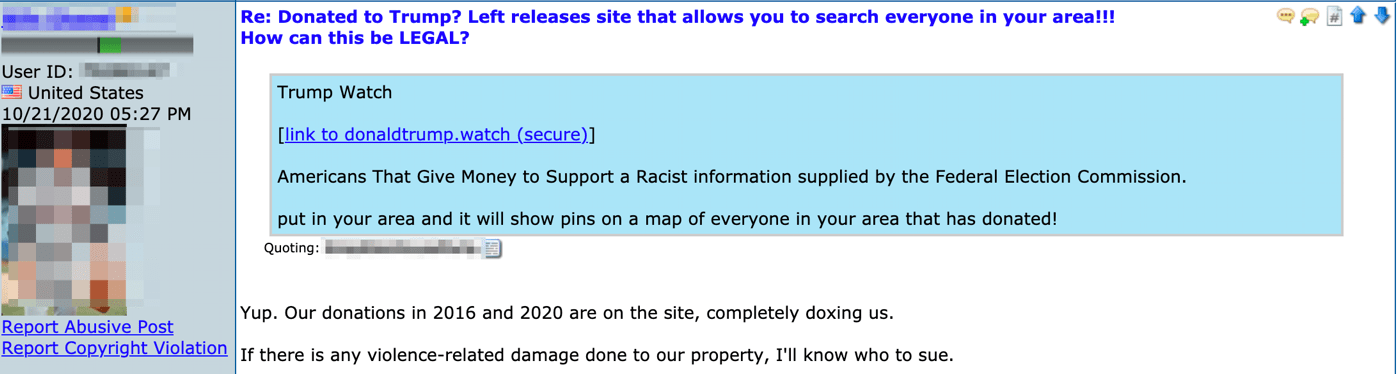
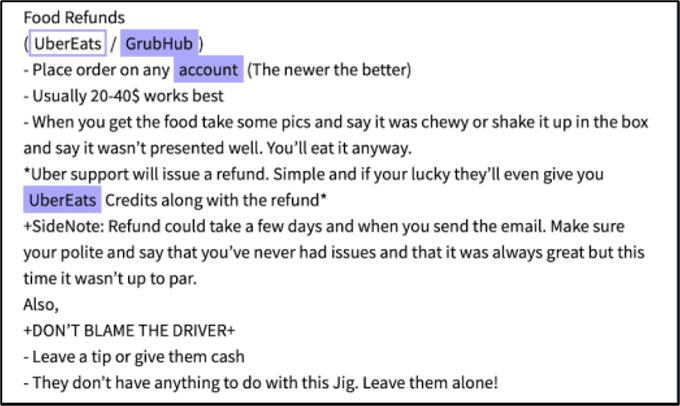
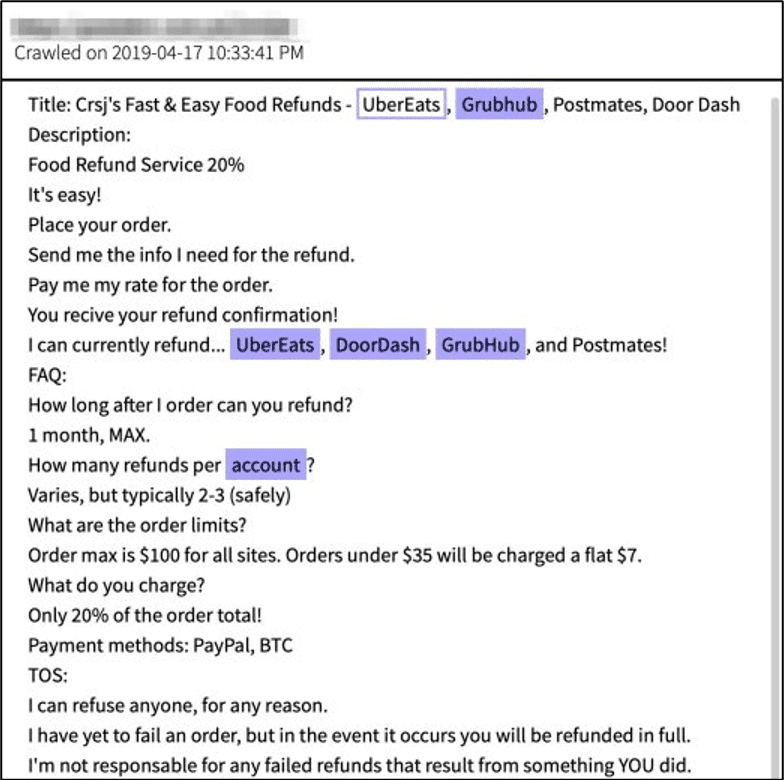
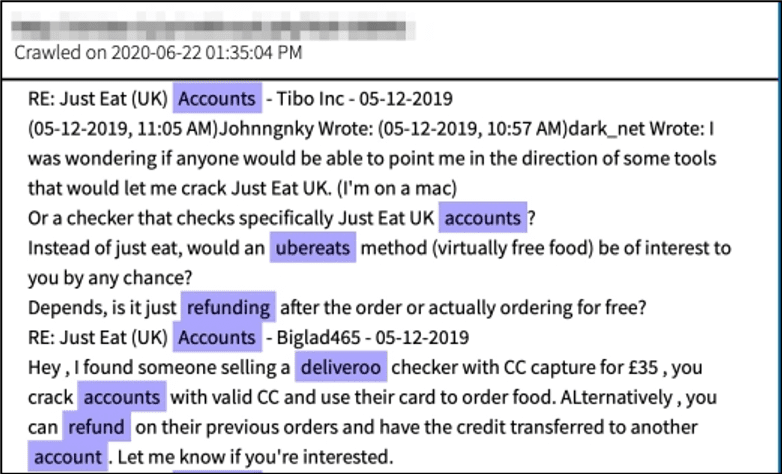
Anonymous networks with digital markets, forums, and image boards, facilitate the spread of such misinformation as apparent with the volume of tools and services on offer, and the number of criminal actors prominent in these sinister underground communities. In 2018, an internal, for-official-use-only, article prepared by the Department of Homeland Security that was subsequently leaked on the darknet indicated that the US government has been fully aware of customizable tools available for sale on the dark web that could “enhance a malign influence operation aimed at interfering with the 2018 US midterm elections by creating a seemingly legitimate and professionally made graphics displaying falsified election results.”
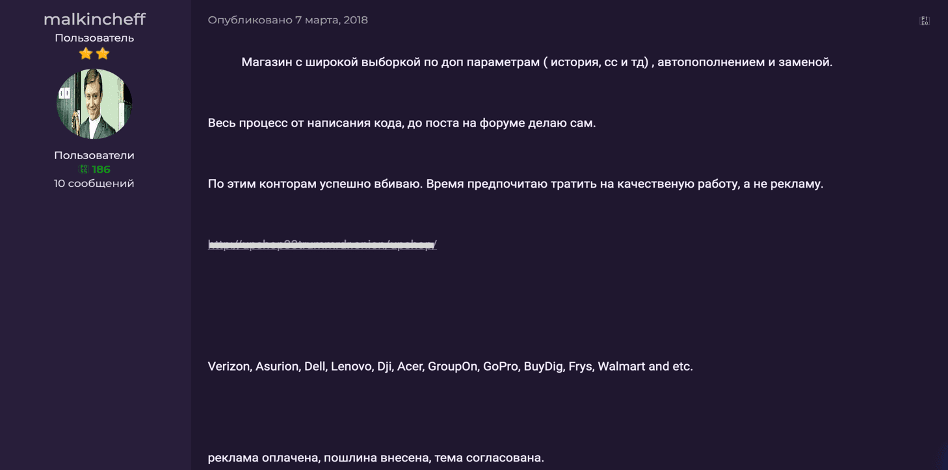
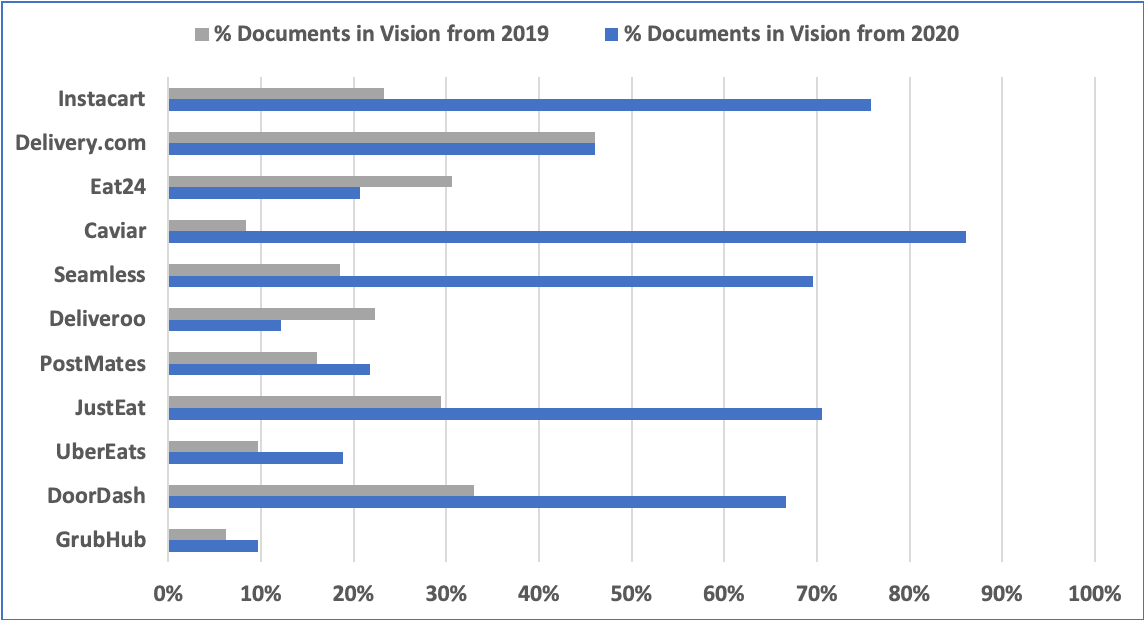
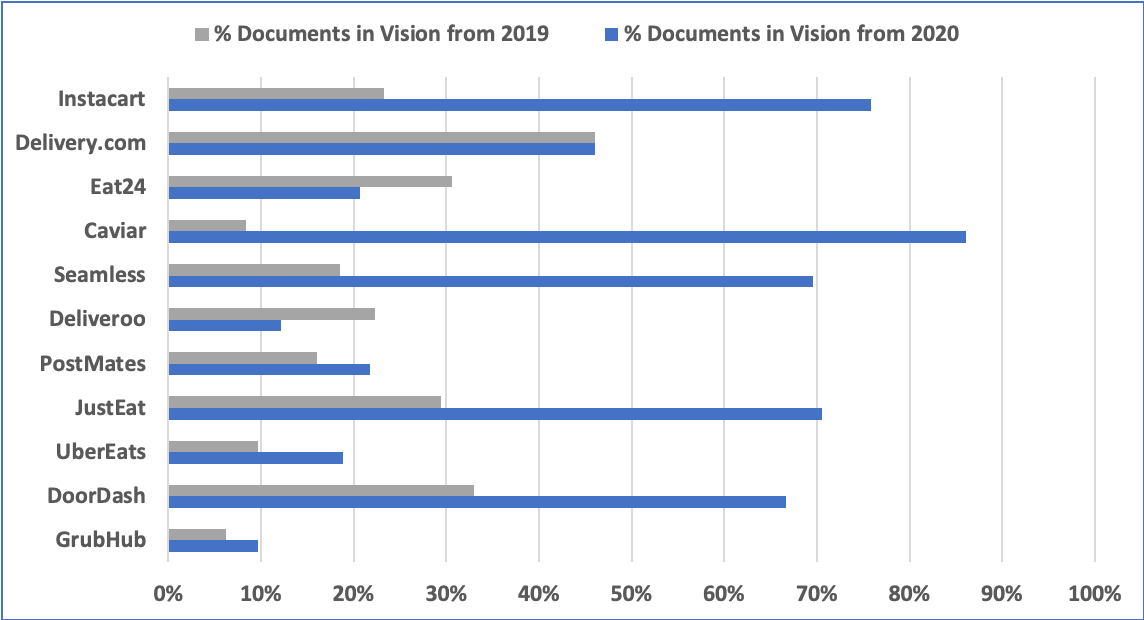
DarkOwl’s Vision system successfully captured the 2018 advertisement, submitted by an anonymous user of the darknet forum with over 10 years forum experience, along with the product’s description detailing the broadcast. Similar offers for Election Night 2020 templates have been spotted, but their proliferation has not been ascertained.
(English Translation of original post)
"Election Night 2018" is a fully customizable template that contains everything you need to create a great, bright video dedicated to the election. "Election Night 2018" is incredibly easy to set up, so you can create a professional broadcast show in a very short time, regardless of whether you are creating a show for the presidential election or Federal and regional.”
– Source, DarkOwl Vision: be1fe1114d27b9ab9fd262ca43e4dcf0
Earlier in 2020, the U.S. State Department utilized its “Rewards for Justice” program to solicit any tips from residents of known Eastern-block countries (Russia, Ukraine, Belarus) that could potentially assist authorities prevent possible digital election interference.
Russian-speaking users on a darknet forum, popular for cyber-crime coordination and malware trading, discussed the U.S. diplomats’ targeted request for information in detail, stating it was sent via bulk SMS text-message to residents of Saratov, Krasnodar, Vladivostok, Ulyanovsk, Chelyabinsk, Perm and Tyumen in Russia. One user suggested they should absurdly exploit the program by hiring a random homeless person to pretend to be a KGB or Fancy Bear sponsored hacker, equipping them with a laptop with hacker-like toolkits installed and signs with potential information the department would pay for.
A New Age of Disinformation: State Sponsored Propaganda to Conspiracy Theories
The concept of information operations via state-sponsored propaganda campaigns is hardly novel, but the lack of internet moderation and a mass transition into social media and digital dependent age, especially over the last two decades, has amplified the proliferation of disinformation in mass, especially as related to particular geo-political agendas and mass social ideology construction. Society’s lack of media literacy and critical thinking skills outside one’s personal area of expertise compounds the complexities of navigating the seas of digital propaganda.
In August, the U.S. Department of State Global Engagement Center (GEC) issued a Special Report outlining the Pillars of Russia’s Disinformation and Propaganda Ecosystem that details the complex information network of official government communications, state-funded global messaging, proxy resources, weaponized social media and cyber-enabled disinformation used by the Russian government in its global information operations campaigns.
Notably, the U.S. State Department report highlighted forgeries and cloned websites (URL hijacking) – consistent with DarkOwl and CyberDefenses’ observed research – as key cyber-enabled disinformation methods used by the Russian government.
A key take-away from their report is how a multi-faceted information ecosystem “allows for the introduction of numerous variations of the same false narratives” an approach consistent with the saying “Repeat a lie often enough and it becomes the truth“, assessed as the principle law of propaganda historically attributed to Nazi Germany’s Minister of Propaganda, Joseph Goebbels. This was witnessed most recently with the height of the COVID-19 pandemic where at least four global, “independent” news outlets: Global Research, SouthFront, New Eastern Outlook, and Strategic Culture Foundation – assessed by the GEC as “Kremlin-aligned disinformation proxies” – circulated hundreds of articles stating COVID-19 was a U.S. sponsored bio-weapon deployed against China, including defamation of Bill Gates and the CIA’s involvement. The proxies’ website and social media reach was reported considerable, with the “Canadian” Global Research outlet averaging over 350,000 readers per article during a three month period in early 2020.
Seeing how disinformation campaigns control the narrative by spreading lies across social media and sometimes even trusted internet news outlets, along with our discovery of the prevalence of sophisticated disinformation-as-a-service providers portends that mere content removal to mitigate a disinformation campaign, especially outside of a social media platform, will quickly no longer become an available option. Blockchain-based biorobots and artificial intelligence operating out of Russia and eastern-Europe are just the latest cyber soldiers of the global psychological war of the information age.