October 17, 2023
Homoglyphs are characters from one language set that look like characters of a different language set. Threat actors use different character sets to cause confusion and register domain names similar to legitimate domains, but with one or more characters from another language, for phishing and credential harvesting campaigns.
In this blog, DarkOwl analysts outline several examples, all including an example screenshot of the fake website. Readers will notice that the vast majority of these are cryptocurrency or NFT (non fungible token) phishing scams.
IDN Homograph Attacks
An Internalized Domain Name (IDN) homograph attack, also referred to as “homograph attack,” “homoglyph attack,” homograph domain name spoofing,” and “script spoofing” is a type of spoofing attack in which the cybercriminal deceives their victim with a website that seems real and genuine but is not. To many, this may sound like typosquatting. Typo-squatting, or URL hijacking, differs as it relies on the victim mistyping a URL in the address bar. For example, a user may type in “gooogle.com” instead of “google.com” and the prior domain may be owned by a hacker and used for malicious purposes.
For both IDN homograph attacks and typo-squatting attacks, once the attacker has deceived their victim, they then exploit the victim on the site by asking them to input credit card details, login credentials, and other personal identifiable information (PII) to later use for their own benefit, usually relating to financial gain. In the case of IDN homograph attacks, these fake websites are created and registered using homoglyphs, resulting in a URL that looks very similar, nearly identical if not paying close attention, to the real URL. For example, an attacker may use the number “0” instead of the letter “O”, or vice versa. Common characters come from the English, Chinese, Latin and Greek alphabets.
Examples in the Wild
Cryptocurrency and Cryptowallets
It is no secret that cryptocurrency is often a target of cyber criminals, especially those looking for financial gain. Cryptocurrency wallets have a “veneer of anonymity;” an address owners identity is actually often able to be associated with crypto transactions due to the connections with financial institutions, blockchain addresses and crypto-related service providers. However, hackers do not necessarily need your personal identifiable information (PII) to conduct a successful attack – as long as they are able to infiltrate and gain access to a wallet, they can then transfer crypto from there. Crypto transactions are not able to be cancelled or reversed (unless refunded by the receiver), as transfers take place on a decentralized network.
It has been estimated that more than 50% of total cybercrime revenue globally comes from the darknet with Bitcoin being used in 98% of cases and the other 2% being other cryptocurrencies. In the spring of 2023, Kaspersky reported 85,000 scam emails had been delivered to the most popular cryptocurrency hot and cold wallets users, with the scam emails impersonating popular cryptocurrency exchanges and wallet providers. Chainalysis reported that in 2022, cryptocurrency hackers stole $3.8 billion USD, up 5 million from 2021, setting a new record.
Entity API, part of the DarkOwl API product suite, allows users to access highly targeted, structured information from the largest commercially available collection of darknet and deep web sources. This includes Tor, I2P, Zeronet, Data Breaches, encrypted chats, IRC, and authenticated forums. You can check out how to use Entity API to monitor cryptocurrency mentions here.
Below are examples of cryptocurrency wallet websites that have been targets of internalized domain name homoglyph attacks.
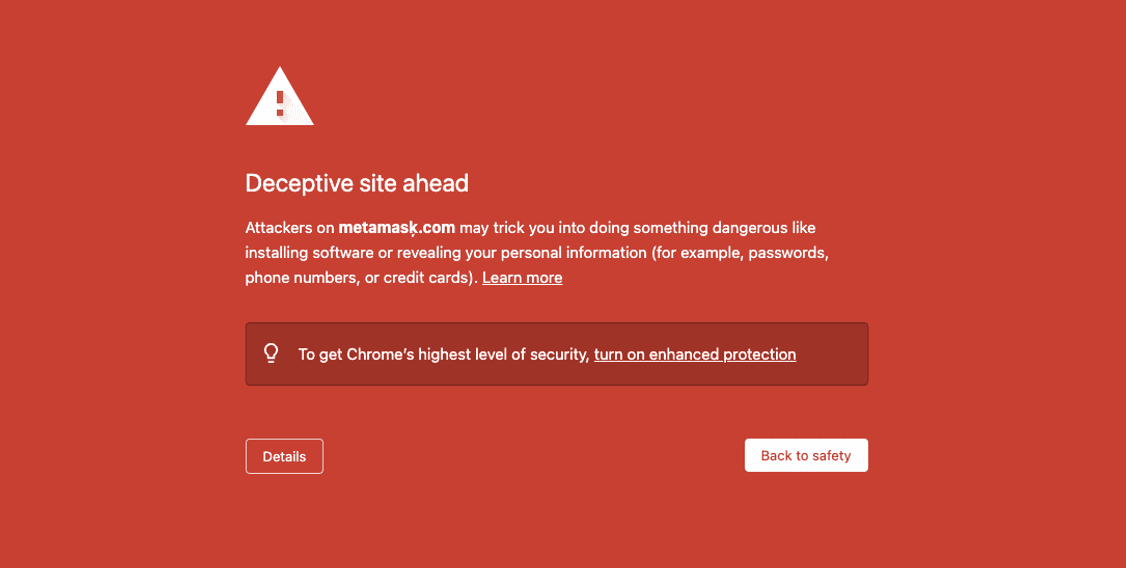
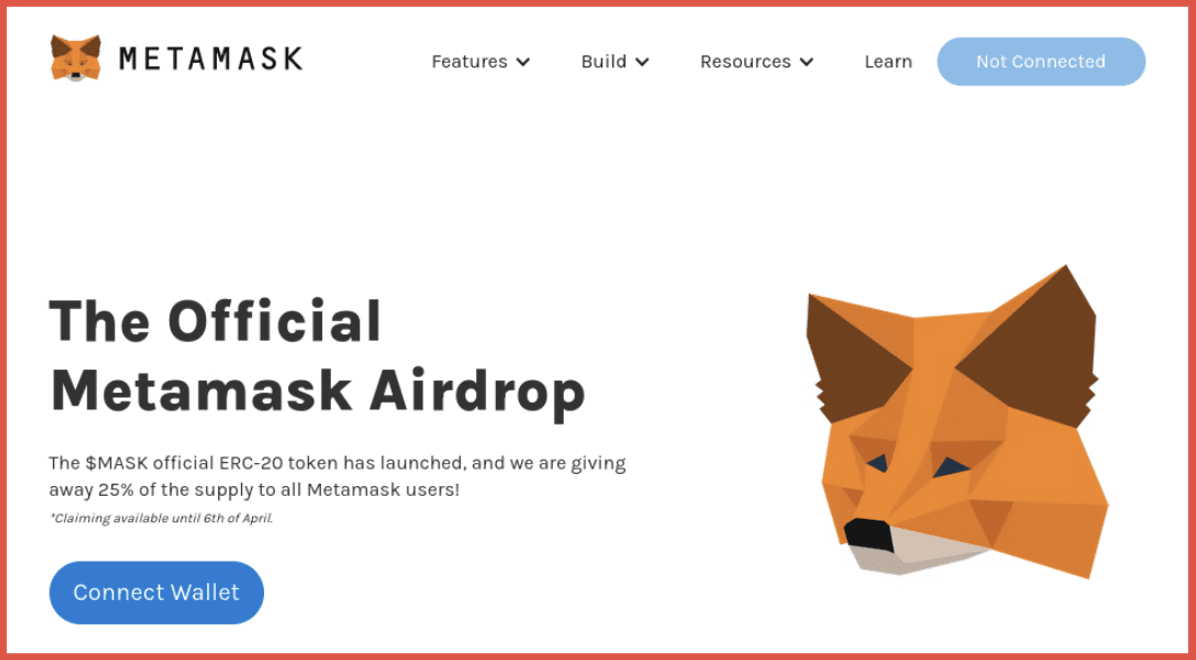
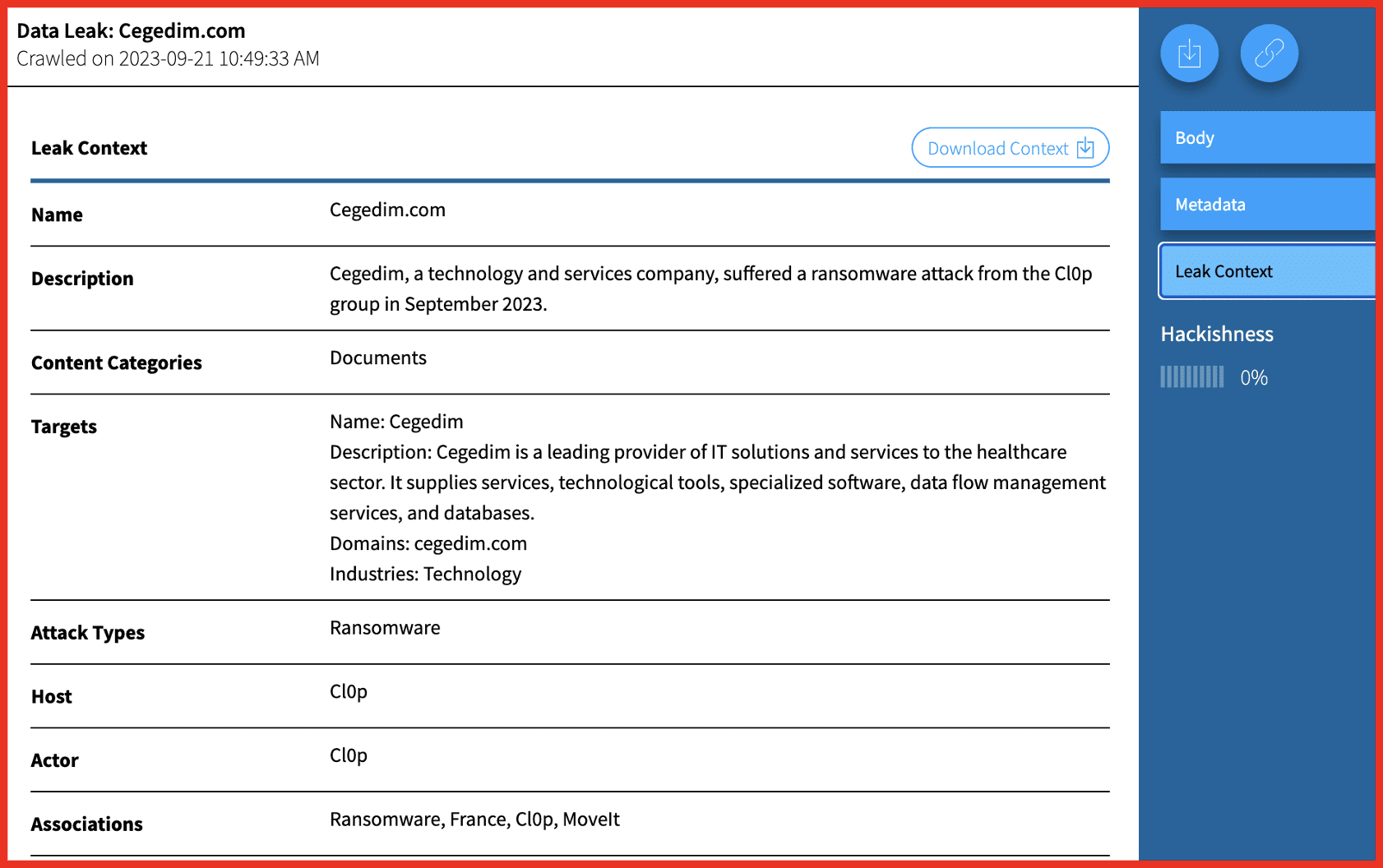
metamasķ.com (clone of metamask.com)
Metamask is an Ethereum-based cryptocurrency wallet that allows users to access their Ethereum wallet though a browser extension or their mobile app. The screenshot to the left demonstrates a great example of internet browsers alerting users of potential danger ahead – these should always be paid attention to. The character used in this homoglyph substitution domain is “ķ” in place of the “k” in “metamask,” which comes from the Latvian alphabet.
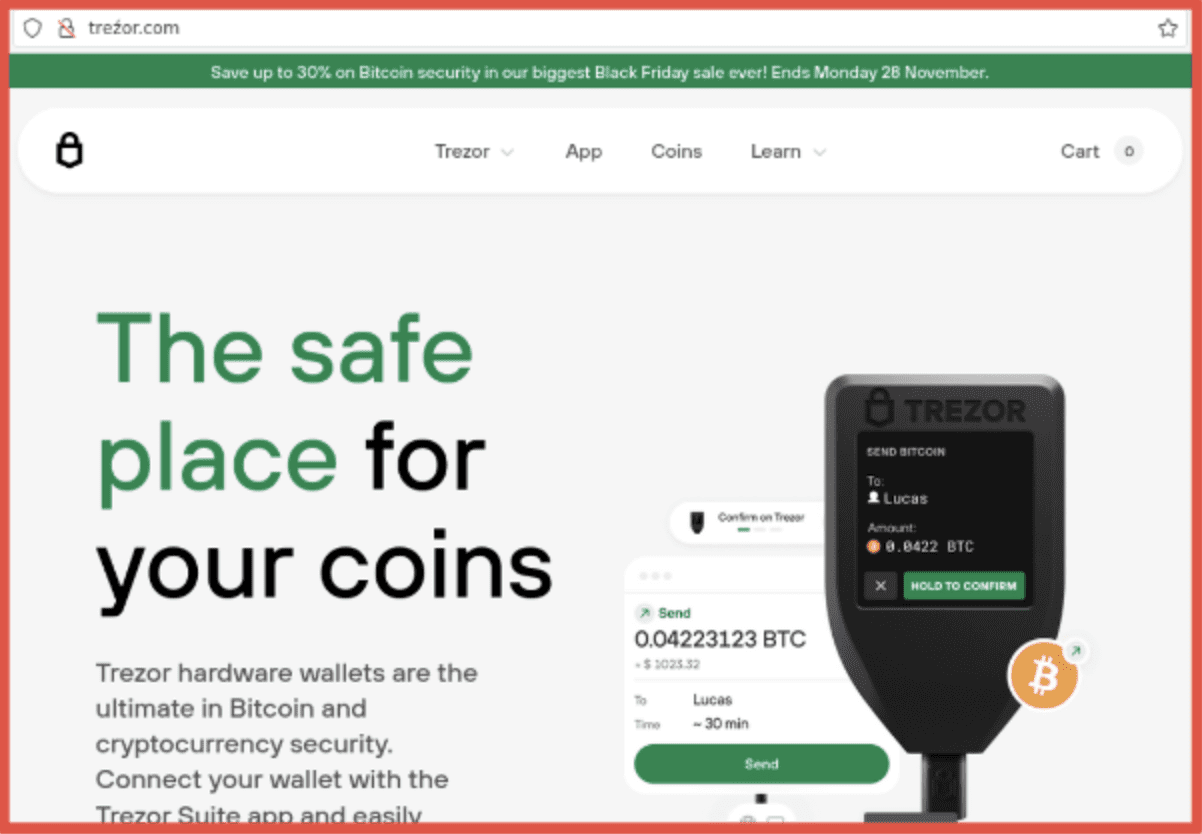
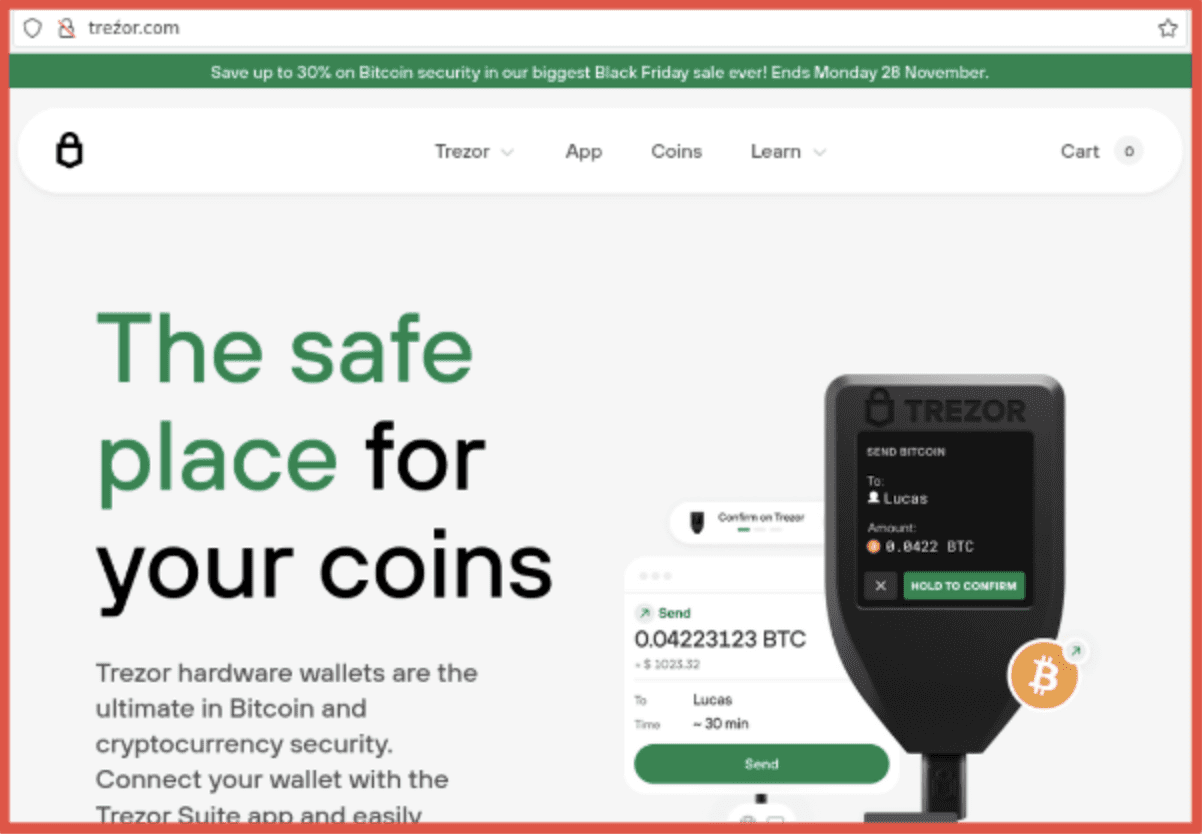
treźor.com (clone of trezor.com)
Trezor is a hardware wallet that securely manages your Bitcoin and other cryptocurrencies. Hardware wallets like this are designed to protect your digital assets from hacks and theft. The character used in this homoglyph substitution domain is “ź” in place of the “z” from the Polish alphabet.
app-uniśwap.org (clone of app.uniswap.org)
Uniswap is a platform to trade, sell and buy crypto and NFTs. It is one of the most popular ways to exchange with the Uniswap Protocol. The Uniswap Protocol is a leading decentralized crypto trading protocol that allows users to swap, earn, and build on it. The character used in this IDN homoglyph is “ś” in place of the “s” from the Latin alphabet.
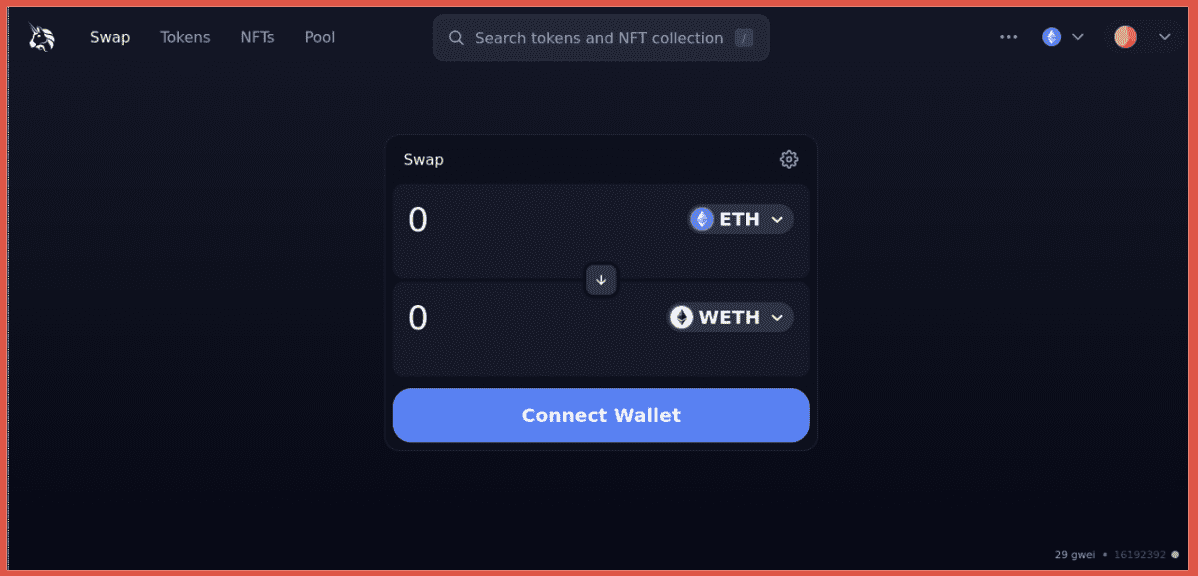
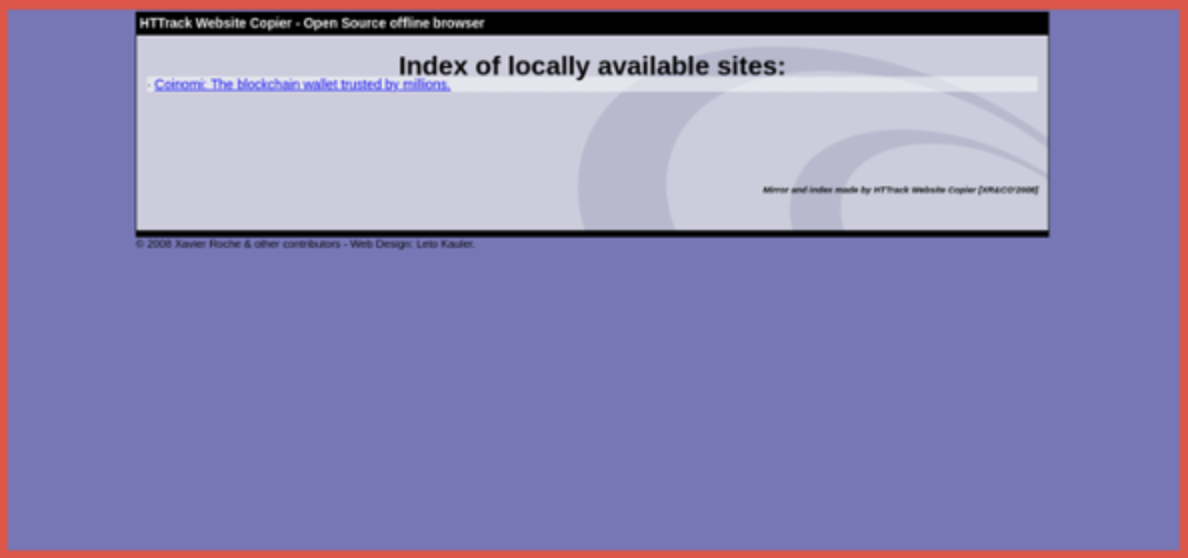
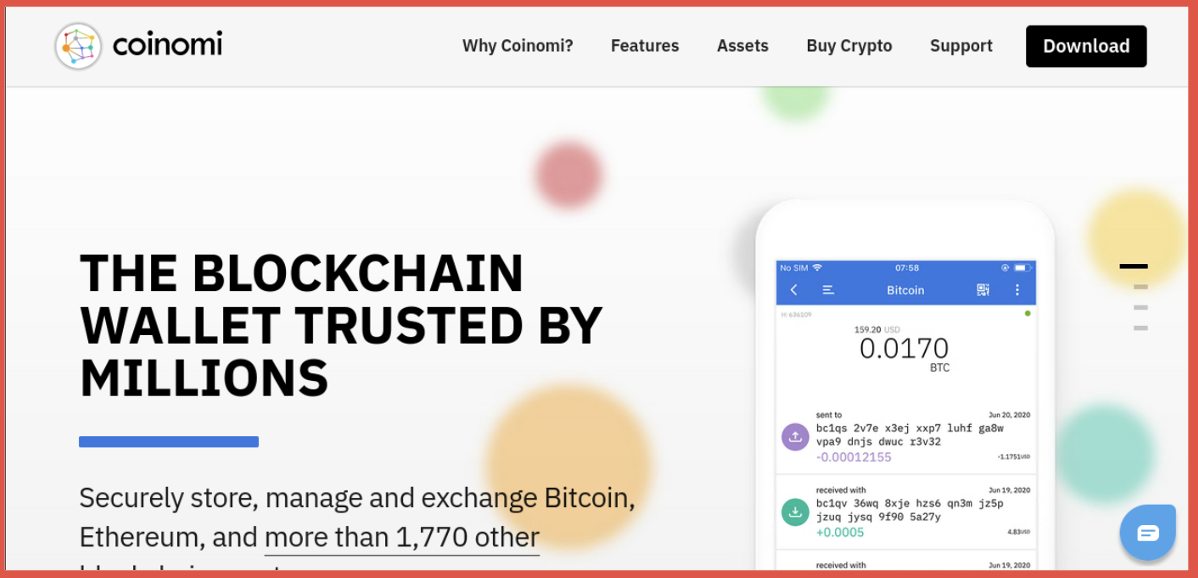
cóinómi.com (clone of coinomi.com)
Coinomi is a blockchain wallet that allows secure storing, managing and trading of Bitcoin, Ethereum and over 1,770 other blockchains. Note on the first image that the IDN homoglyph homepage loads up for a split second before redirecting to the fake page, seen in the second image, which looks identical to the real homepage. The threat actor is using an open-source website clone tool for the campaign but not hiding their tracks very well, this “Index of locally available sites” page should be a clear warning that something is not right and should raise a red flag to users. The character used in this homoglyph substitution domain is “ó” (and 2 of them) in place of the “o” from the Latin and Polish alphabets.
Technology Vendors
The technology vendor examples are quite different than those above. The IDN homoglyph sites examples below were likely used for phishing campaigns. Phishing is a type of fraudulent social engineering for data collection designed to trick users into revealing sensitive information to what appear to be trustworthy sources via email. Earlier this year, DarkOwl analysts created accounts for fake email addresses that were posted on the darknet to learn more about trends in the phishing and spam email landscape. That research can be found here.
cloudfǀare.com (clone of cloudflare.com)
Cloudflare is a content delivery network (CDN) and cloud cybersecurity company that provides services to increase the security, performance, and reliability of websites and web services. This IDN homoglyph website just leads to a blank homepage. This was probably used for phishing campaigns where email victims were tricked into clicking a link that goes to a specific directory on this site. The character used in this homoglyph substitution domain is “ǀ” in place of the “l” which is a “dental click” used to denote the sound “tsk! tsk!”
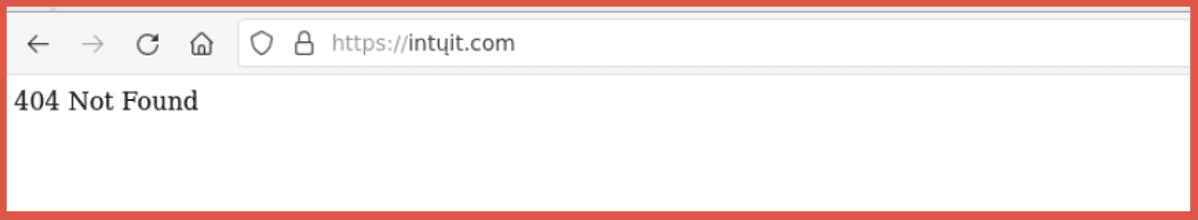
intųit.com (clone of intuit.com)
Intuit is a leading financial software technology company offering numerous products to help businesses and individuals alike. Like the fake cloudflare site in the example above, this has a web server but no default home page and is probably part of a phishing campaign trying to to trick victims into clicking on a link from an email that leads to a deeper directory on the server. The character used in this homoglyph substitution domain is “ų” in place of the “u” which comes from the Latin alphabet.
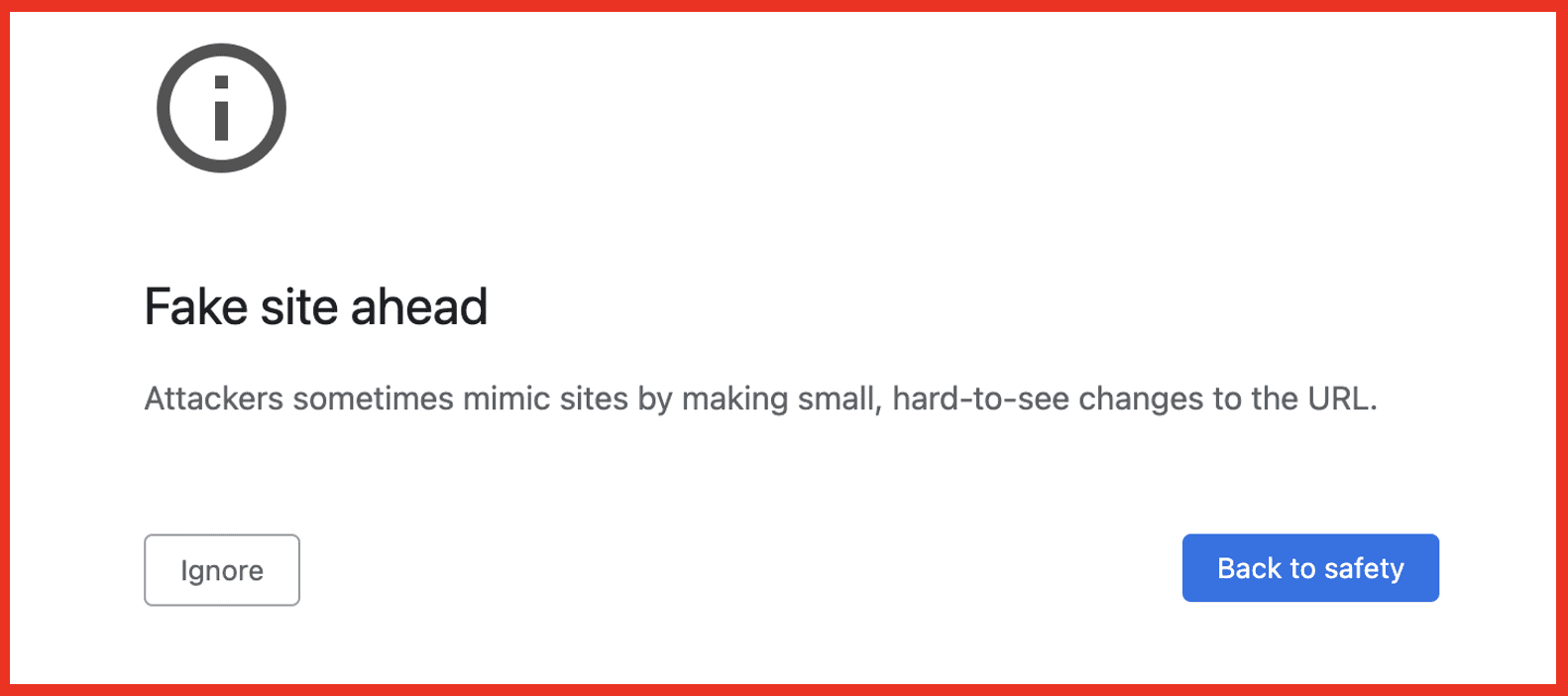
flaṣh.com (clone of flash.com)
Flash.com leads to an Abode site, but if you land on the IDN homoglyph “flaṣh.com” you will see the warning below. This is a great example of an internet browser warning users before entering a potentially dangerous site and even explains what triggered the fake site warning. The character used in this homoglyph substitution domain is “ṣ” in place of the “s” which comes from the Latin alphabet.
Retail
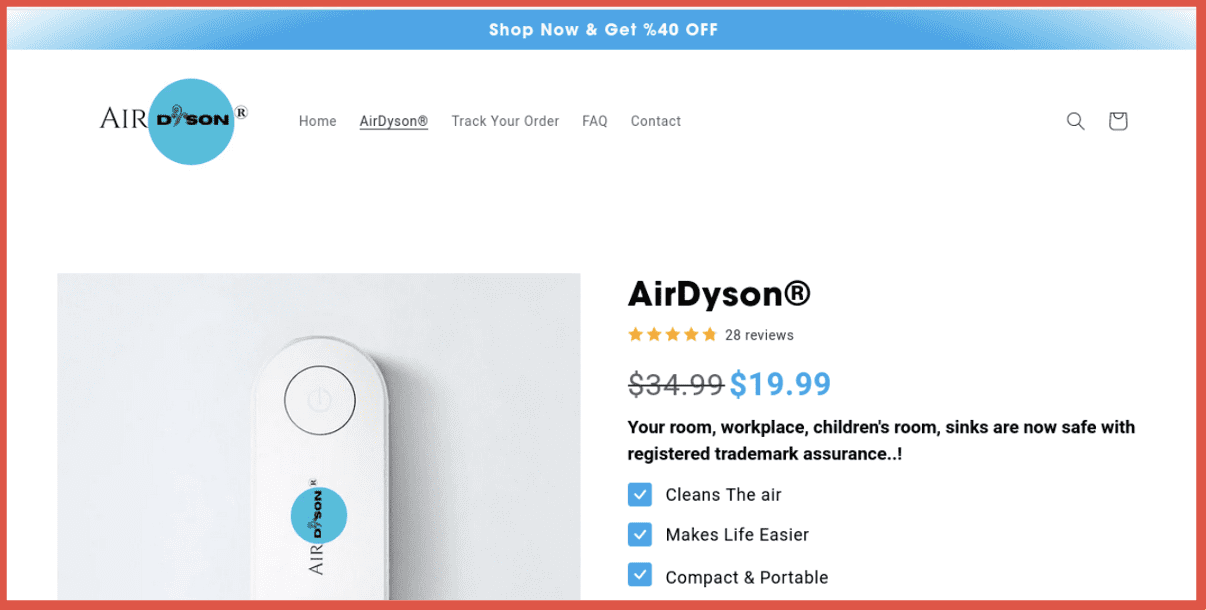
aırdyson.com (clone of airdyson.com)
Airdyson is a very popular hair styler. This site is seems to be either selling counterfeits or just harvesting credit card info. The character used in this homoglyph substitution domain is “ı” in place of the “i” which is called a “dotless i” and comes from used in the Latin-script alphabets of Azerbaijani, Crimean Tatar, Gagauz, Kazakh, Tatar, and Turkish.
The List Goes On…
Other homoglyph substitution domains DarkOwl analysts found, most of which were able to process email but either had no website or a missing default index page, include:
- baɾclays.com (clone of barclays.com)
- crypţo.com (clone of crypto.com)
- dişcord.com (clone of discord.com)
- freshmań.com (clone of freshman.com)
- opènsea.com (clone of opensea.com)
- polygoñ.com (clone of polygon.com)
- applẹ-icloud.com (clone of apple-icloud.com)
- bítfinex.com (clone of bitfinex.com)
- pornĥub.com (clone of pornhub.com)
- unıvısıon.com (clone of univision.com)
- zeǁepay.com (clone of zellepay.com)
- bmobạnking.com (clone of bmobanking.com)
- mėgạ.com (clone of mega.com)
- dỉscovercard.com (clone of discovercard.com)
- cỉtynationalbank.com (clone of citynationalbank.com)
- crawfordandcoproductíons.com (clone of crawfordandcoproductions.com)
- zỉonsbank.com (clone of zionsbank.com)
Takeaways
Our analysts note that threat actors are not leveraging homoglyphs as much as was previously seen. Homograph attacks have declined but this does not mean that cybercriminals will not create more complex spoofing domains. Security measures are in place among web browsers to detect and alert users when they suspect they may be entering a fake site that they thought was legitimate, as seen in the Flash example above. It is important for users to pay attention to URLs and always exercise caution.
Steps to protect yourself from IDN homograph attacks:
- Regularly update your browser for the latest security updates and patches.
- Confirm the legitimacy of the website by making sure it has an Extended Validation Certificate (EVC), especially before sharing on sensitive information.
- Avoid clicking suspicious links from emails, chat messages, publicly available content, and social media sites, and verify that the visible link matches the real destination.
- When in doubt, there are several browser tools such as Punycode Alert and Quero Toolbar help sus out potential danger.
If you do find a phishing domain or IDN homoglyph site, there are several ways to report it. DarkOwl analysts found hostinger.com to be the fastest responding registrar in shutting them down, and you can always report to Google, the Federal Trade Commission and the Internet Crime Complaint Center.