[Webinar Transcription] Exploring Emerging Trends in Cybersecurity
October 31, 2023
Or, watch on YouTube
As the digital landscape continues to evolve, so do the threats that target it. Staying ahead of cyber adversaries requires a deep understanding of the latest trends and innovations in the cybersecurity space.
In this webinar, DarkOwl CEO, Mark Turnage and Socialgist CRO, Justin Wyman explore a variety of critical topics shaping the cybersecurity landscape:
- Key VC Raises in Cybersecurity: Capturing Industry Attention
- Understanding the Major Players: Who’s Raising the Stakes
- Harnessing Security Solutions: How Organizations Protect Their Assets
- Addressing the Talent Gap: Scaling with Data Aggregators and Services
- Pioneering the Use of AI: How do LLMs and AI Come into Play
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity.
Kathy: Thank you for joining us for today’s webinar exploring emerging trends in cybersecurity. Before we get our topics, begin our topics today, I’d like to turn it over briefly to Mark and Justin to give a brief introduction of themselves and their companies.
Justin: Hi, guys. Nice to meet you. Wyman, Socialgist is the name of my company. I’m the Chief Revenue Officer. We are a provider of open source intelligence. We’ve been doing so for the last 22 years, and I’m excited to be here.
Mark: Hi, I’m Mark Turnage. I’m the CEO and Co-Founder of DarkOwl. We are a company that specializes in the darknet, and specifically in extracting data from the darknet and providing it to our clients and working with partners like Socialgist to provide a broad view of open source intelligence, including that of the darknet.
Kathy: Great. Thank you both. Prior to diving into our topics today, Justin and Mark wanted to take a moment to comment on the Israeli and Hamas conflict happening presently.
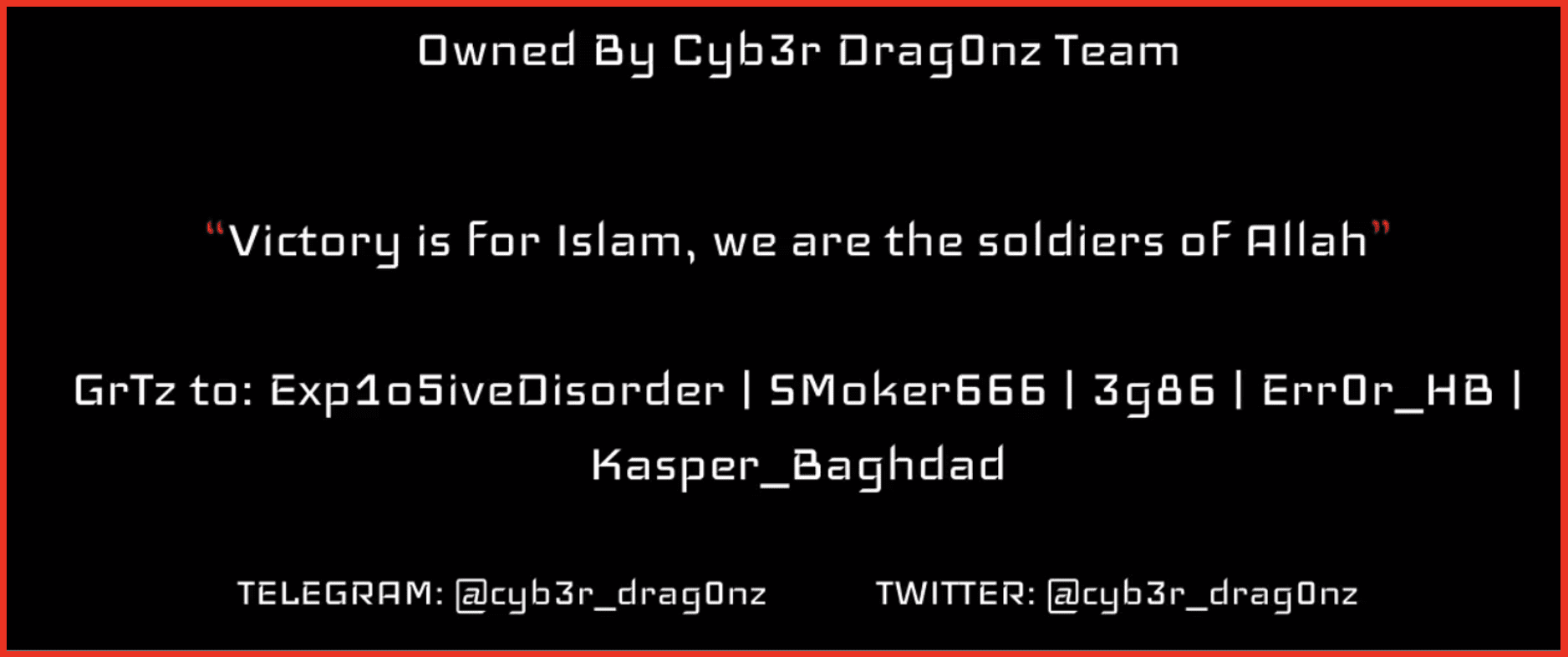
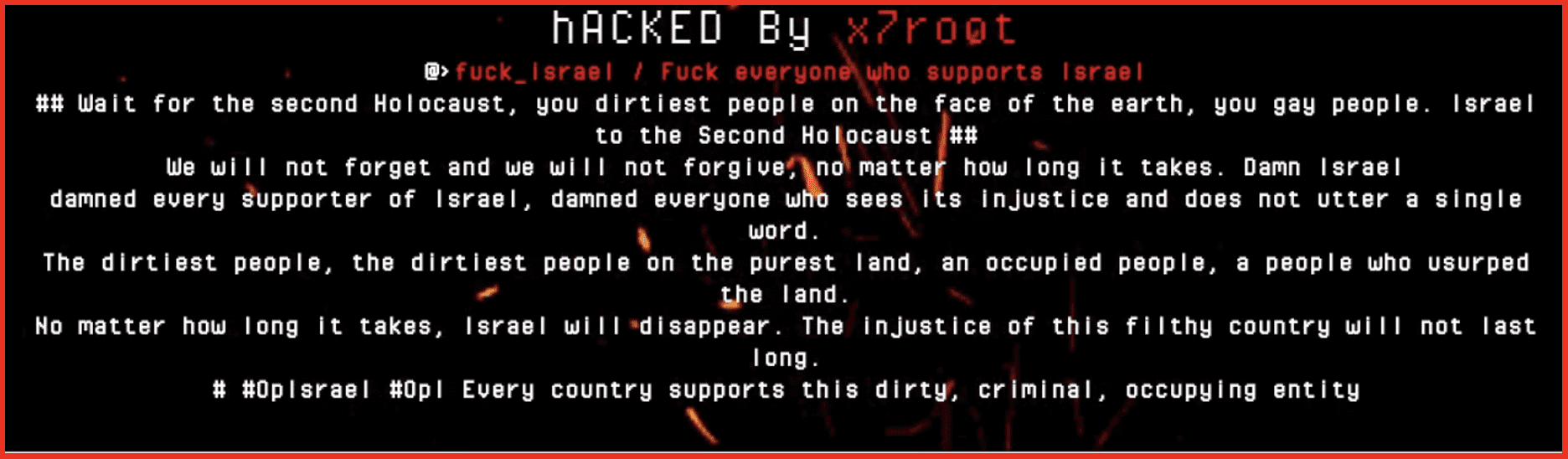
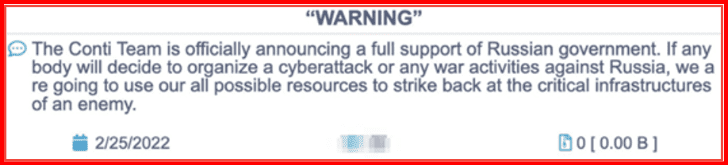
Mark: I’m happy to comment. You know, when the conflict broke out on October the 7th, we immediately started looking at content in DarkOwl’s database that was relevant to the conflict, either pro-Israeli, pro-Palestinian, pro-Hamas, and we pretty rapidly triangulated on about 400 Telegram channels that are actively covering the conflict. And we’ve been monitoring those channels throughout, directly ourselves and generating some content which is available on our website, and also supplying that to our clients. And it gives them a different perspective than what you see on the front page of many of the newspapers. I will comment, we published a blog very early in the conflict that noticed that amongst the most prominent Pro-Hamas Telegram channels, they went quiet for several weeks before the attack. Unusually quiet. We don’t have an explanation other than they were distracted, they were planning, they were getting ready, or they had been told to go offline. But we did detect that in the lead up to the attack, there was considerably less activity on those Telegram channels than was normally the case.
Justin: I would say when you see such a horrible thing, it’s really hard to process, especially because in the space that Mark and I occupy, Israel is a big component of it. Technology companies and cybersecurity are founded in Israel all the time. Some of the leaders in the space. So it gave an extra personal feel, if that’s even possible. When you see these types of things, when you know the people that are directly impacted by it at a different level. And then I thought it was it was comforting to see that we could in some way help with our information, help the helpers, essentially. And Mark, I got to say, I thought the Dark Owl content was fantastic. To help show examples of how OSINT intelligence can help prepare for these types of things and deal with them frankly.
Kathy: Thank you both. Now we will begin with our first topic.
Key Raises in Cybersecurity: Capturing Industry Attention
Justin: So let me talk at a high level. What is happening? If you look at VC and cybersecurity over the last couple of years, it’s declining, which normally I think would be a bad thing if you didn’t realize it was declining from a peak bubble that happened during the pandemic. So you can say things are down 30% from last year, which is down another 30% from last year. It really, honestly, to me just seems to be returned back to normal. You see a lot of companies having some very specific raises, we’ll get into and you’ll see some combinations, you’ll see some coverage. But I think that the cybersecurity industry should feel that there’s been a correction that was due because you’re in a bubble. But now we are in a place where things are normally operating. The space is growing and investment is happening as well.
Mark: Yeah, I’ll just echo Justin. The investment into the cyberspace, go back say three years was just red hot. It was at levels that I didn’t think were sustainable. And oftentimes at evaluations that I didn’t think were justified. What has happened as the economy has gone through a fair amount of turmoil over the last year and a half is that those valuations have reset, and the level of investment is what I would normally expect in a pretty healthy sector that is still growing. Overall funding is down. I think it’s down 30% year on year. Valuations are down. The interesting thing is that companies that are still growing and companies that are profitable are still getting healthy inbound investment. Just yesterday, by the way, Censys announced a $50 million dollars raise, a small company out of Israel raised $4 million. I mean the raises come in regularly. They’re not at the valuations that we saw, say 2 or 3 years ago, but they are still happening. And they are particularly happening with very healthy companies.
The other trend, by the way that I’ll mention is any time you have an economic reset, which is what we’re experiencing right now, it forces consolidation in the market. You know, scale matters, size matters, sophistication matters. Go-to-market strategies and the ability to reach your market matters. So whereas before a small startup could have raised successive rounds of value, of money, of capital at ever increasing valuations against, you know, maybe skinny performance – those days are gone and they’re likely to be an acquisition candidate for for another company. And we’re seeing this – large companies are pretty active in the M&A market right now as a result.
Kathy: Based on that, a question has come in. What changes do you foresee over the next coming year?
Justin: Let me start with one of the public markets because that leads things. So in the public markets, you’ll see a lot of leading cybersecurity companies up double digits this year, more than the S&P 500. CrowdStrike is a good example. They’re up 70% year to date. As an example, Tesla is only up 80%. Apple’s only up 36%. So that’s not market forces. That’s industry forces of the problem with cybersecurity is growing so rapidly. The things I think you’ll see over the next year would be companies that have a growth plan, getting more funding and moving into new markets. I saw that already with OSINT Combine. There’s a company with a very good Australian presence going to the North American market. Full disclosure, they’re friends of my company and DarkOwl – so maybe we’re a bit biased there.
You’ll see some people getting acquired by PE firms, which is an idea of, again, operational excellence that might be a different component than things, say, in a bubble where instead of doing a PE acquisition, you would raise a bunch of money and see if you could sell and market your way out of it. The other thing I’ve noticed that I think will come is more legitimacy and standardization. Frost and Sullivan has created industry coverage for the first time on a lot of these companies. You’ll see certification tracks coming out of industry organizations like Osmosis. So I see it as a big step forward in the maturity of this space. There’s always startups, there’s always guys in the middle, and there’s always the big guys, and you want to have enough of them to create an ecosystem where you can ultimately meet the consumer need.
Mark: I couldn’t agree more. The way I would have described the cyber security industry two years ago was an awkward teenager. And it’s moving to young adulthood. It’s maturing. It’s growing up. It’s actually starting to understand what its own limitations are and what it can and cannot do. And I would just echo Justin and say, over the next year, we’re going to continue to see consolidation – more and more mergers, more acquisitions. It has always amazed me, just as an aside, that the largest cybersecurity companies in the world still only measure their revenues in single digit billion dollars. Those are the largest. And then it falls off pretty quickly from there. And given the size and importance of the problem, this is an industry that is ripe for what you just identified, Justin, which is growing up, consolidating, becoming more professional, working against known certifications and known standards. And by the way, known regulations because the regulators have arrived.
Justin: Mark, that McKinsey report we’re referencing before about just how breaches are supposed to go up 300% from 2015 to 2025 also noted that to your point about revenue, that the vendors in the space right now make up a 10th of what they think the overall revenue is going to be in the next ten years. So yeah, teenager growing up is a great analogy, meaning there’s just so much. There’s some stability being built in, but there’s still so much more to grow up.
Understanding the Major Players: Who’s Raising the Stakes
Mark: Well, I think in the world of threat intelligence broadly, there are a couple of very large players – Recorded Future comes to mind, Flashpoint comes to mind, Intel 471. There are a bunch of these players. Interestingly enough, every single one of those has been acquired over the last 3, 4 or 5 years by large private equity firms that have, as a strategy, explicitly what Justin was talking about, grow these companies up, make them larger, make them professionalize their operations, give them global scale and global reach. And then below that you’ve got a whole range of companies and these are small- to mid-size. Some of them are just start-ups who are looking at problems from a different angle. And there has been a lot of activity, both in terms of fundraising into those companies as well as acquisition. I mean, one that comes to mind is Maltego. Maltego was acquired by a private equity firm at the beginning of this year, and that’s a well known, well established platform that is used across the industry by a number of different companies and users. And in my view, that was a really smart purchase by the private equity firm. What else is going on Justin that you’re seeing?
Justin: A company I recently became familiar with at a conference was Fivecast. They raised 20 million. They were an Australian based company looking to really expand their sales and marketing into North America. They feel their perception, not mine or based on conversations, that they feel they have their product completeness to the point where it’s time to go see if they can compete against the bigger guys in the space. Now Cobwebs, another huge player in the space, just joined Chainlink. Those are other things I’m seeing.
Another one we were talking about, Mark, is Palo Alto Networks buying Dig this morning as a sign of just a major player adding in a feature capability. So, you know, this is following the the classic playbook – where you watch Oracle and Salesforce go after each other and then add on competing bolts. Again, another idea that you have a very well established market that you can operate. If you have operational excellence, you can really succeed.
Mark: Another example of that, by the way, is Proofpoint yesterday announced the purchase of Tessian and we’ll come on to it. Tessian is an AI provider that will significantly enhance Proofpoint’s products. And so you’re starting to see that happen at a pace that I have long predicted. But really I think this economic climate has accelerated.
Harnessing Security Solutions: How Organizations Protect Their Assets
Justin: I’ll start as I always do, with a little bit of data. Fraud is still massive. The biggest issue that every organization is dealing with – it’s coming from social media, it’s coming from internally. I talked a little about this McKinsey report, but again, I’ll say it again because it’s such a massive number. They think that breaches damage is going to increase 300% by 2025. The other one that I looked at was a survey of mid-sized companies suggests that threat volumes will almost double from 2021 to 2022. So that’s 100% growth in one year.
What they’re doing to protect their assets – my concern is with their employees. So I’d love to hear your thought on this, Mark.
Mark: Just a small data point from DarkOwl – we track where visitors to our site go and what pages they dwell on. The most common feature across our website is our fraud webpage and content on fraud. That speaks to the nature of the problem.
I’ll just say two things. One is we are all excited as an industry about AI. We’re excited about new tools, about new capabilities that exist. So are the threat actors. They’re using all of the same tools, all of the same capabilities to actually scale and professionalize their own operations. But, you know, going back to your point, Justin, the biggest threat to many companies is their own employees continues to be their own employees, whether that’s actual outright fraud or just mistakes that employees make that open up the company to potential potential attack and fraudulent attacks.
Justin: I believe that was the logic behind the Tessian acquisition is just the amount of people that have exposed their companies by literally emailing the wrong person. That seems to be a problem that should be quickly solved through some proper technology application.
Mark: I mean, I’m amazed. I’m actually amazed. Look, I mean, CEOs are are susceptible to this as well. And in fact, I mean, go to any OSINT training seminar and they’ll tell you the most vulnerable people or the easiest to attack are the C-suite, because they’re the ones who are the sloppiest or the least attentive to to security. That continues to be the case, but it permeates the entire organization.
Justin: The other thing I’ve heard is that key figures, usually execs, because there’s so much information, that they’re much more easy to manipulate. Voice manipulation takes a lot of samples of data. So the bigger the sample, the easier it is to manipulate the voice is the other thing I would talk about. And then the last one I noticed was people just kind of really trying to do the best they can to understand their supply chains. If employees are people accidentally sending information out. Supply chains are people sending information in, and these are business partners that you rely on your suppliers. So it’s very easy. Those are very weak points in a system to kind of create havoc if you’re not prepared.
Mark: There’s absolutely no question. The pandemic taught us that supply chains matter and supply chain vulnerability is mission critical. And to to Kathy’s question of how organizations protect their assets, it’s not only protecting your own assets, but protecting those critical assets of your vendors who are critical to the provision of your product or your services as an organization, which is why you’re starting to see these third party and vendor risk management companies come into their own in terms of their level of maturity, because especially very large, complex organizations need to pay attention to their supply chains.
Addressing the Talent Gap: Scaling with Data Aggregators and Services
Mark: The interesting thing about the talent gap is that the cybersecurity industry for years has complained about lack of talent. I think the statistic I continually hear is something like half a million unfilled cybersecurity jobs worldwide. And that number has held pretty steady for the last number of years. We’re in an environment, though, where many of the companies in our sector are actually laying people off. So how do you square those two contradictory statistics? Well, one way to square them is exactly what Justin said earlier, which is many of the companies that are laying people off were hiring at a clip that was unsustainable just as recently as 2 or 3 years ago. So you’re coming back to a sort of a more normal track. My sense is that there is still plenty of demand in the marketplace for people who have cybersecurity experience, whether it’s developers or product people or otherwise. But yes, there is a gap and I think AI is going to help fill that gap. What do you think about that, Justin?
Justin: I absolutely do. Let’s talk about the two things like data aggregators and services. Start with services because Mark and I have a data aggregation stake in this fight. But on the services component, when I work in the space, what is interesting to me is the people come from all different backgrounds military, private, etcetera. There’s no “you don’t go to school to become a cybersecurity expert.” So that’s a very big problem. But it’s a problem that is being solved, I think. When we were all at OsmosisCon, which is a association of these professionals, they’re creating certifications. They’ve created a conference so people can come and share tips and tricks. And that’s just one of many. So I think it’ll get easier and easier to bring people into the space and give them the certifications that show them that they’re qualified, because right now it really is due to the nature of the sensitivity of the issues and how people come. It’s like, who do you know that you can trust? Which makes sense in the beginning. But over time, you have to figure out how to scale your business. So I see a lot of services being created to help with that.
Then on the data aggregation side. As a data provider technology provider in this space, it’s amazing to me how big the problem is, right? These people are searching for needles in haystacks and the haystacks are growing, and so the only way you can solve them is through aggregation. And that’s basically at any point in the value chain. So if you’re creating a piece of software that allows analysts to hunt for threat actors, well, you’re probably going to use data from many different sources because the haystack is too big for you to do it yourself. Then if you’re actually looking and searching and doing the analysis on top of the data, these tools will allow you to search more efficiently. If you go back to Mark’s Telegram example about things going silent before an attack, as these technologies get better, you know you won’t have to go, “Huh? Why are these silent?” These things will go, hey, there’s an interesting activity here. The volume of these things has really dropped off. Why? And that’s a way that people will be able to not only look in the haystack more broadly, but faster, have things suggested to them. So I think ultimately the space will be fine. Again, I can’t stress this enough, we are coming off a bubble, and that generally means people aren’t behaving how they should behave. And so to correct that, you have to lay some people off. But now that we’ve had this baseline, people go back to building their businesses most based off of the value they provide in the market. And as we’ve shown, the value is only growing, meaning the threats are only increasing dramatically.
Kathy: Based on that, we’ve had a question come in: We have seen a lot of layoffs in the space recently. And can you address how this does affect the talent gap?
Justin: Positive half glass full spin would be – when you have layoffs in an industry where it’s growing, it’s because those people are in a place where they weren’t effective. They weren’t doing the things that needed to be done to keep the business on its goals. So when you take an experienced person and you separate them from a business that no longer needs them in a growing space, they should be deployed in a better space where they are more impactful. Right. This is the efficiency of markets happening. So I think these gaps will take the people that were places where they weren’t as useful and put them in places where they will be much more useful and create a world where they’ll be, again, more coverage.
Mark: Not to disregard the dislocation that necessarily occurs when that when that happens, if you’re the individual who’s affected, it can be quite difficult. But I agree with Justin that on aggregate we’re not seeing employment in the cyberspace decline. It still continues to increase.
Pioneering the Use of AI: How do LLMs and AI Come into Play
Mark: The big issue that both Justin and I have discussed in the past is anytime you bring an end to a problem, it needs a data set to sit on, to learn, to learn that problem in order to be effective. And so what becomes the most critical in that is the data we aggregate – darknet data. Socialgist aggregates open source data across a variety of different platforms. Those data sets become extremely valuable and extremely important in the application of an LLM to address or learn about a specific problem. And you know, in the case of DarkOwl, I can speak to that, our data set has been aggregated over 5 or 6 years. That’s not something that you can just recreate overnight. If you’re a new company coming into this space or somebody looking to utilize AI, the same I’m sure is true for Socialgist. So it’s a very interesting insight into the power of the underlying data that that any organization can has in terms of addressing the problem via an LLM.
Justin: And I totally agree with everything Mark just said. I think the other thing to think about is, how much easier it is to get things out of the data value, out of the data with LLMs, and how in general, the biggest thing you’re going to see in the software world, the biggest constraint is going to be software engineering capacity. Every company in the world wishes they had more software engineers because it’s hard to do things like connect a data set into an analytics platform. It’s a very technical work. These engineers now are doing work 40% faster, so it’ll be easier to make progress and solve problems when you put these types of applications together. What that should mean is that you should have in the long run, and again, marginal like dislocation is hard and things need to change and we have to cross the chasm and all these sayings, but what we’re really talking about is in the long run, things should get cheaper with technology and things should also get better. So the data sets that we ship to our clients that are working very hard to get incredible data out, get incredible insights out of it, should be able to get insights out of it faster and better and cheaper because they need less engineers. And then the tools to analyze these data sets should only get more powerful as well. I really see there will be an area where, you know, there’s different segments in our space, right? There’s the people that are at these big companies, and they have all the budgets in the world, and they have the fanciest tools, and there’s people below that, and there’s people literally using their cell phones to track people doing medical research. Those people should get increasingly better tools that will make them much more effective. So we’re talking about the capability of people with less budget getting much more effective, which I think really creates a much better world.
With the caveat that the other guys have it too. So there’s always a push and pull, but I see a lot of positive headwinds in the in the long run with AI.
Mark: I mean look, you know it’s going to increase, as Justin said, productivity per worker significantly. And the comment that I heard recently in a conference was, you know, AI will be tremendously dislocating of many types of employees and many types of groups, but the world’s going to divide itself into to two camps. Those people who know how to use AI to make themselves more productive and those who don’t. And that’s the digital divide that we’re actually hurtling towards. I’m deeply optimistic, personally, about what I can do across multiple different fields, but starting with our own field in cybersecurity – I’m very optimistic about it.
Kathy: We’ve had another question come in and an attendee is interested to know “Will DarkOwl and its peers sell their data sets to companies?”
Mark: Good question. We’ve been approached by a couple of companies, and we’ve done our own early work on putting an LLM onto our own dataset. I suppose I should put on my businessman’s hat and say it depends on the price. Yes, it depends on the price. But it’s not something that we’re going to do loosely or without a lot of thought. Because once that data is out there under somebody else’s LLM, obviously the data is available to whoever has access to that platform.
Justin: It depends, I think is a good answer. I think the thing to understand about perhaps my company, Mark’s company, is like, you know, our mission is to extract information from the world’s online conversations and if you can help us with that mission, because we’re very serious about it for the reasons we’ve discussed throughout this whole thing, we’re seriously going to talk about it. Now, there’s sometimes choices that make decisions. There’s sometimes choices that make that not the case. And there’s always a lot of nuance. But at a high level, if you help us with our mission and the business makes sense, then that would seem something that should happen. But also, Mark, you touched on a really interesting point of, you know, I do think data companies like ourselves are also going to explore training with our own LLMs too. to have the full picture. So I think the key is as long as LLMs capability is used on these data sets to make the world a better place, we’re for it. The machinations, I don’t know. There could be a world where two data providers do one together, etcetera, but the technology should make the data more useful, and that is our goal.
Mark: I will point out we’re in discussion right now with our first client who wants to put in on a subset of our data. It’s exciting.