Combat Fraud With DarkOwl Data Products
February 22, 2023



Galway, Ireland – February 9, 2023 – Siren, an industry leader in investigative analytics, on a mission to keep people, assets and networks safe, today announced its strategic partnership with DarkOwl, a Denver based threat intelligence company specializing in dark web data.
By fusing together data from open source, vendor and classified sources, Siren enables investigators and data scientists to analyze risks, including threats to national security, public safety, fraud, and compliance, as well as threats to large enterprise corporations. Using the Siren Graph Browser, researchers can string together findings from previously disparate data sources to conduct robust OSINT investigations.
While much of the power behind Siren’s data products stem from an ability to visualize and integrate data, Siren also curates a strategic selection of Technology Partners that end-users can leverage within their Siren dashboard. Siren has selected DarkOwl as one of these partners as a response to customer needs for cutting-edge data sources, including the darknet and deep web.
DarkOwl is known in the industry for its extensive coverage of near real-time content from the darknet and related sources. This includes Tor, I2P, chat platforms, ransomware blogs, gaming message archives, paste-sites, and darknet marketplaces. Their data offers insight into these high-risk areas of digital activity, including coverage of emerging darknets and forums requiring authenticated access.
“By choosing to integrate DarkOwl’s data into their platform, Siren is making a statement that they understand how crucial the darknet is to modern OSINT investigations,” commented DarkOwl CEO Mark Turnage. “Now, investigators can take information from our data set, such as a bitcoin address or a user alias, and pivot using Siren Graph to turn that data into actionable intelligence.”
“This partnership will offer Siren customers curated access to the dark web,” said John Randles, CEO of Siren. “Now, threat intelligence analysts will have the means to connect DarkOwl data to other forensic, OSINT, company or internal sources of data, to power a variety of Law Enforcement, National Security and Corporate Fraud use cases.”
About Siren
Siren is a complete investigation solution, safeguarding people, assets and networks. Siren fuses data from open source, vendor and classified sources allowing analysts and investigators to analyze risks, threats and crimes for the National Security, Public Safety, Fraud and Compliance, and Cyber Threat communities. Siren’s patented technology is uniquely search based providing the user with easy to use search, analytics, visualization and reporting capabilities for investigations on all data types at all scales of data volume. In 2022, Siren was included in the Deloitte Technology Fast 50. Siren is a Gartner Cool Vendor in an Analytics and Data Science Report in 2020. For more information, visit www.siren.io.
About DarkOwl
DarkOwl uses machine learning and human analysts to collect automatically, continuously, and anonymously collect darkness content. Our products leverage AI to index and rank darknet and deep web data to enhance simplicity in searching. DarkOwl is unique not only in the depth and breadth of its darknet data, but also in its advanced investigation tools and passionate customer service. Our data is ethically and safely collected from the darknet. This allows users secure and anonymous access to information and threats relevant to their mission. For more information, visit www.darkowl.com.
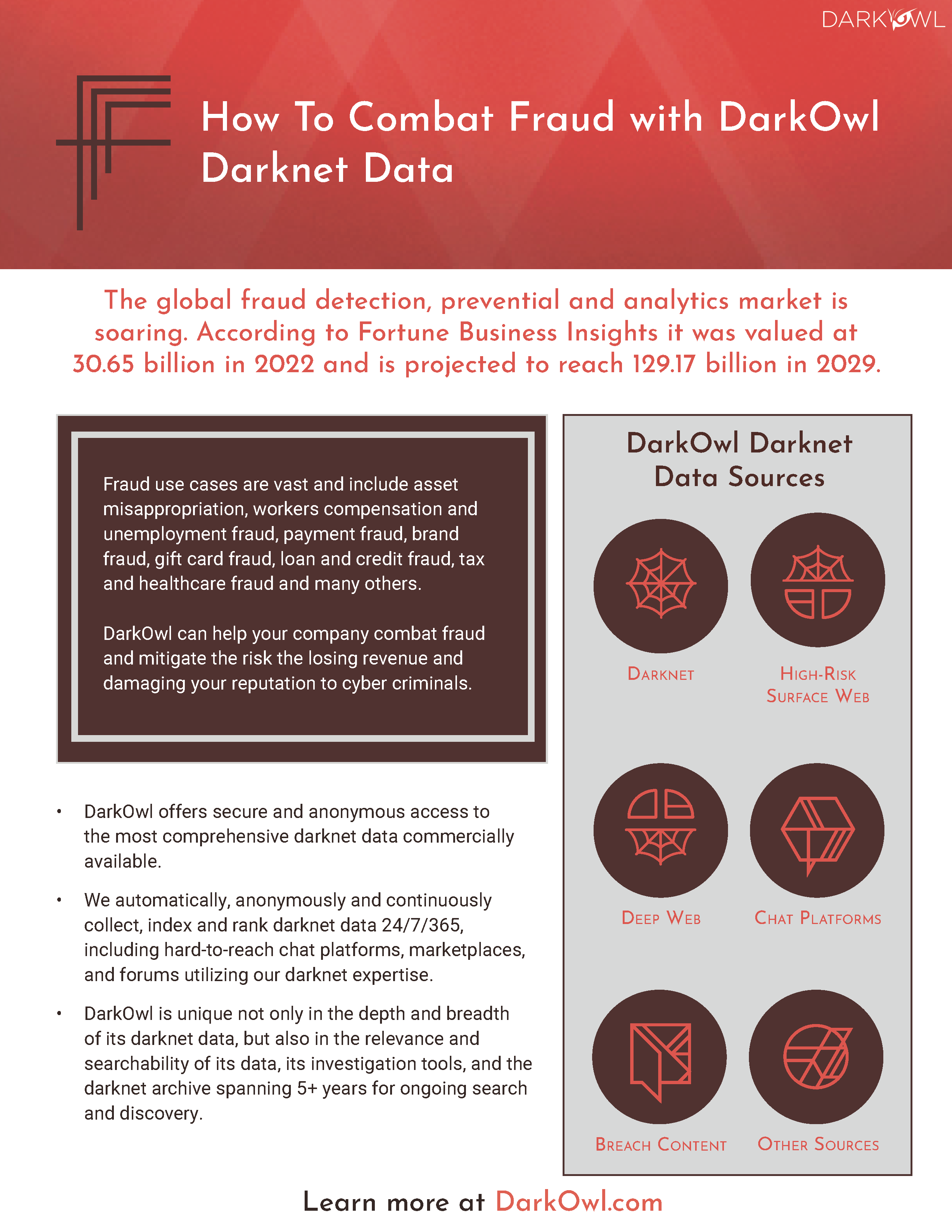
API Security professionals can benefit from darknet data in forming a more comprehensive understanding of malicious threat actor Tactics, Techniques, and Procedures (TTPs) in order to inact effective detailed security recommendations, remediations, and product solutions.
API Security related topics, such as “API hacking”, “stolen API tokens”, and “API MITM attacks” are regularly discussed in detail in darknet forums. Similarly, API tokens are frequently sold and traded in underground digital marketplaces, as is API exploitation code is shared amongst threat actors.
Considering that API security incidents affected 95% of organizations in the last year (Source), it is more important than ever that the information security community remain aware of shifts in threat actor discussions regarding APIs and the various TTPs that threat actors use to exploit them.
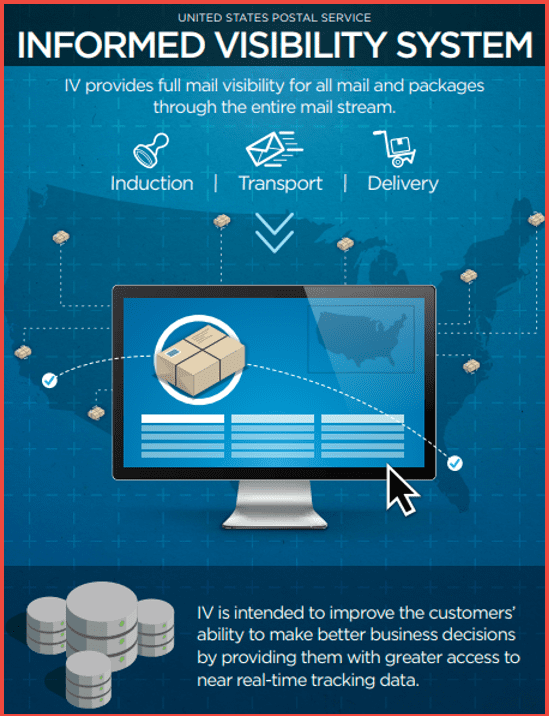
Recent security incidents impacting APIs highlight the need for increased awareness and protection of digital supply chain assets. For example, in 2018, a vulnerable USPS Informed Visibility API endpoint leaked over 60 Million US residents information. USPS performed and published an audit that detailed some of the issues that resulted from the incident, although many of the key data is redacted.
More recently, in April 2022, Github admitted that attackers targeted private repositories using the Github API using stolen OAuth tokens. This was likely via a Microsoft OAuth flaw that occurred in December 2021.
Recently, Toyota was notified of a breach that happened as the result of an API access key for T-Connect, the official Toyota connectivity app, being left publicly available on GitHub. Their T-Connect connectivity app powered utilities like wireless access to vehicles.
Toyota has since announced that over 2,900 records were exposed since then, giving access to customer names, customer information, and so forth. This is one example of what the threat landscape looks like and what the implication can be of API credentials getting into the wrong hands.
Similarly, recently, FTX and 3Commas revealed that an API exploit was used to make illegitimate FTX transactions. This was done using API keys that were obtained from users via phishing attacks that enabled them access to lateral systems. Eventually, the platform 3Commas came forth publicly to admit that the API keys were obtained from outside of their platform, but the implication still posed a risk to their users. Risk of user account exploitation included threat actors being able to make offsite, unauthorized financial transactions.
An investigation revealed that DMG trades were conducted using new 3Commas accounts and that “the API keys were not obtained from the 3Commas platform but from outside of it.” This suggests that cyber criminals likely gained keys from phishing or browser information stealers, which are frequently discussed and advertised on the darknet.
Poor access controls of a United States Postal Service (USPS) API endpoint resulted in a wealth of US persons’ private information available to criminals
In 2018, a vulnerable USPS Informed Visibility API endpoint leaked over 60 Million US residents information. USPS performed and published an audit that detailed some of the issues that resulted from the incident, although much of the sensitive data is redacted.
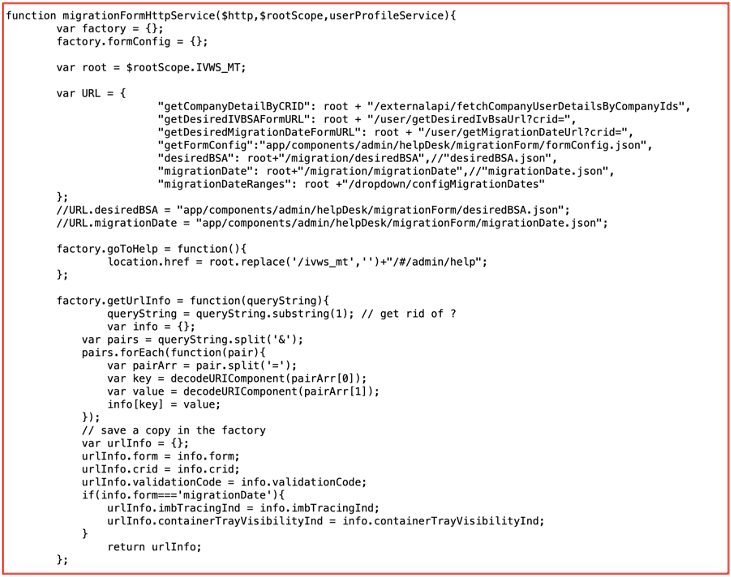
On the darknet, stolen API secrets, keys, and session tokens are shared openly and in closed communities. Authenticated darknet discussion forums on Tor, transient paste sites, and Telegram especially popular with API attack enthusiasts.
Pinnacle, Telnyx, and other API tokens are frequently offered for purchase on darknet forums such as DARKMONEY and similar ‘hacking’ Telegram channels.
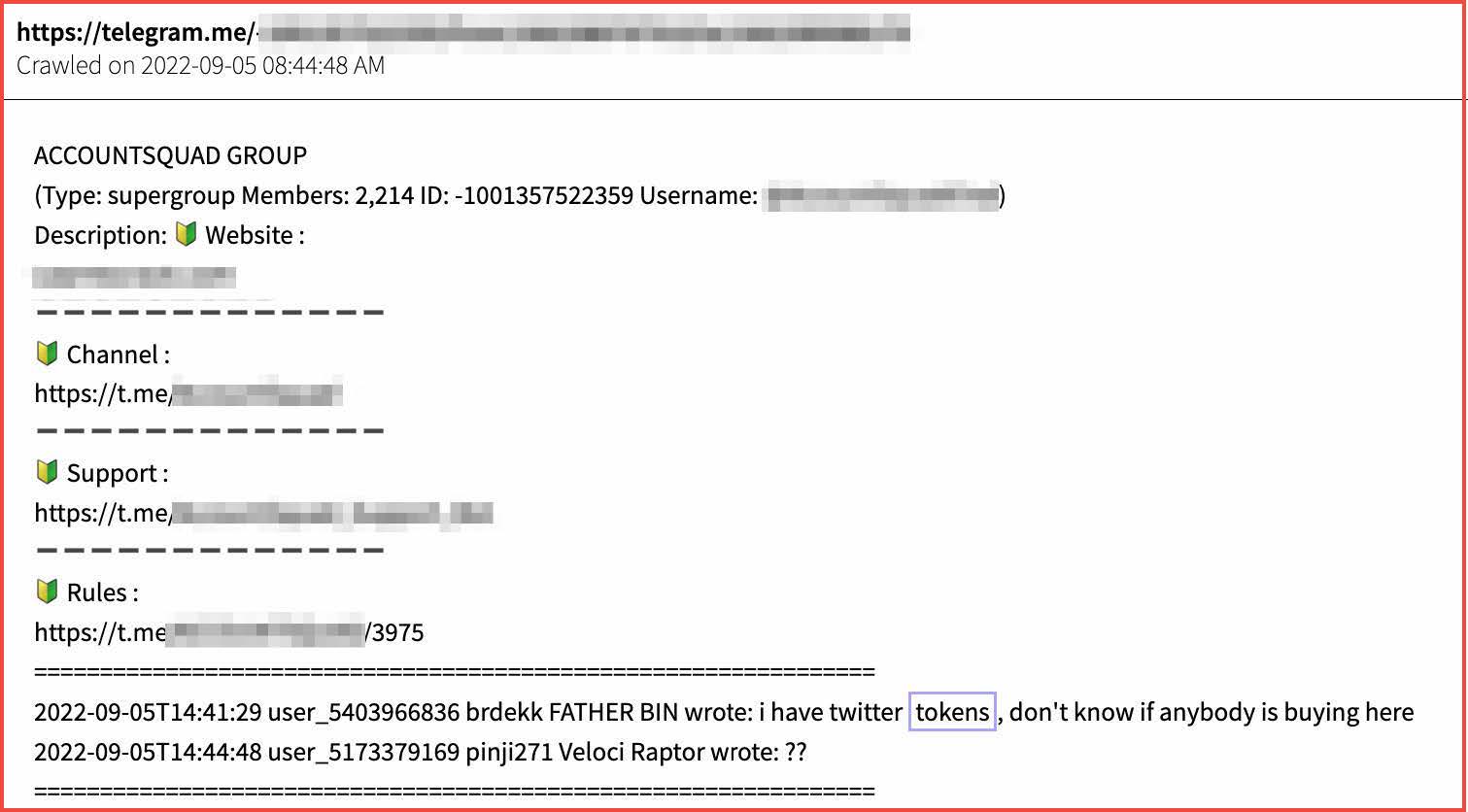
Telegram groups offer ‘key checkers’ – where the API key is tested ahead of time on behalf of the threat actor. Another example shows Twitter tokens being offered for sale on ‘cracking’ Telegram group.
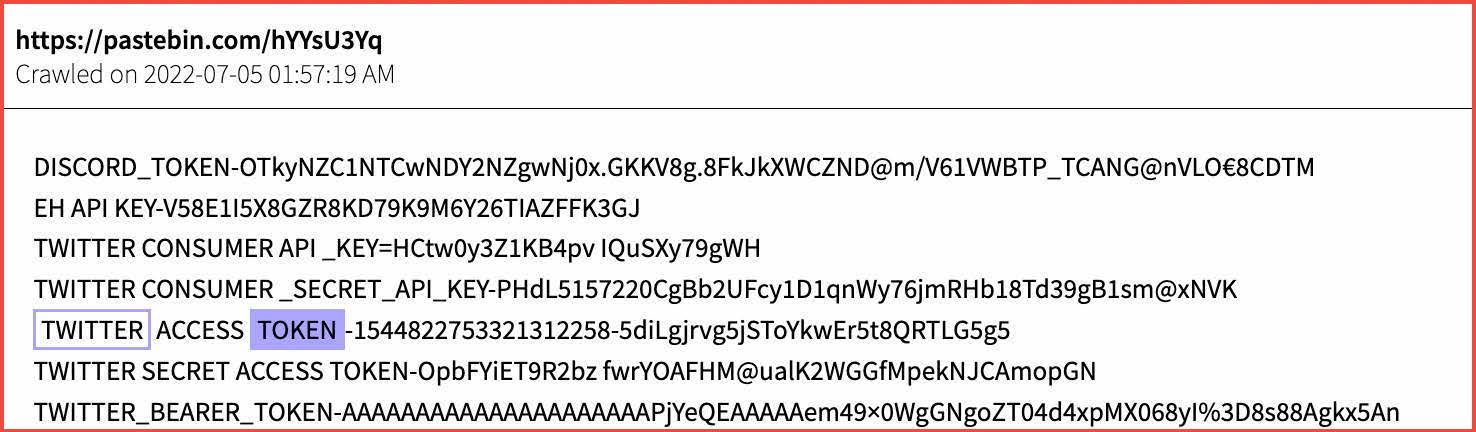
In another example, DarkOwl analysts have observed a TikTok API token generator for username scanning. Below is a translation of the listing:
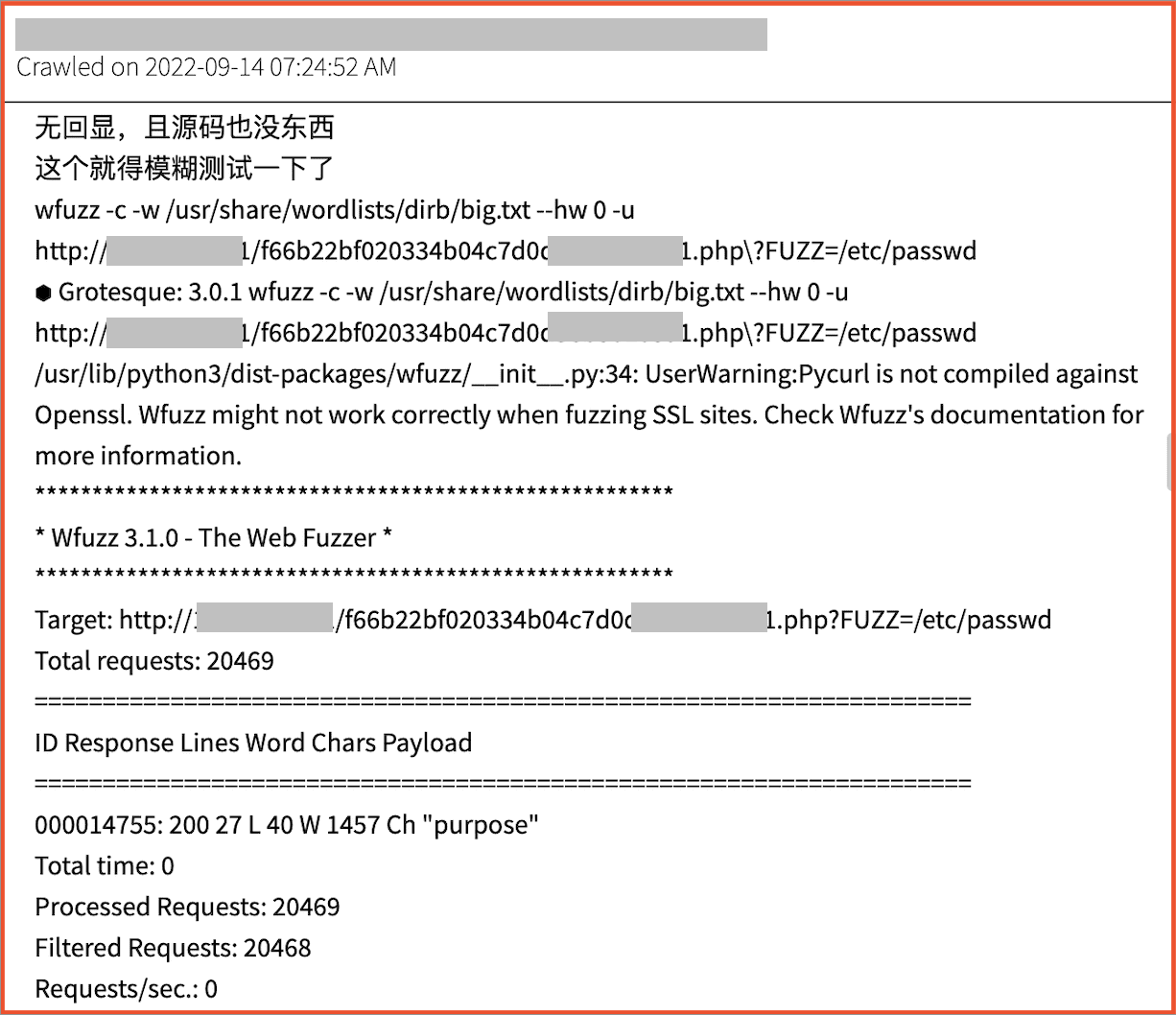
DarkOwl has also increasingly observed API penetration testing utilities – like GoBuster or Wfuzz – discussed in detail by non-english speaking darknet users. Similar technical discussions are now appearing on malware developer centric surface web sites, such as CSDN.
APIs tend to be an underserved element with respect to cybersecurity postures of most enterprises. However, as organizations continue to make efforts to digitally transform their application ecosystems, enterprise services increasingly rely on APIs. As a result, APIs are emerging as the backbone of modern communication and application ecosystems. As more organizations move towards the cloud and similar API technologies, having visibility into any and all credentials that could be exploited is exceedingly crucial.
This shift towards dependency on APIs in the commercial landscape echoes what DarkOwl analysts are seeing in the darknet. Discussions around API exploits, API keys, stealing API keys, and selling them is a relatively new phenomenon in the darknet over the last couple of years, that we expect to continue to grow.
The annual DoDIIS Worldwide Conference is one of the premier gatherings of threat intelligence technology companies that service national defense initiatives. This year, representing DarkOwl at DoDIIS were Chief Business Officer, Alison Halland, and Director of Strategic Partnerships, Chris Brown.
Per their website, the DoDIIS Worldwide Conference brings “senior decision makers, technical experts, and innovators from across the Department of Defense, Intelligence Community, industry, academia, and FVEY partners will come together to collaborate and share unique insights.

The theme of this year’s conference – Transcending Strategic Competitors through Innovation, Adaptation, and Collaboration – underscores the urgent race to collectively develop and unleash emerging technologies to maintain strategic and tactical advantage. Mission success in an era of strategic competition demands a willingness to embrace disruption and elevating partnerships to serve as overwhelming force multipliers.”
The DarkOwl team reported that, much like years past, attendance at DoDIIS leads to sophisticated conversations about the role of darknet data in threat intelligence technology products serving the defense industry. Through our partner Carahsoft, DarkOwl was given a dedicated monitor to give demos of Vision UI, our darknet search platform.
These conversations also provided the opportunity for the DarkOwl team to share updates on our data collections as our product team has made significant additions over the past year, including the expansion into authenticated forums, and open chat platforms such as Telegram.

In the spirit of this year’s conference theme, the DarkOwl team spent a significant portion of time understanding how we can best optimize and elevate our current partnerships. Present at DoDIIS this year were a number of DarkOwl’s current data platform clients, including Proofpoint and OSINT Combine. The general consensus from these conversations is that their customers are finding significant value in having the ability to access and search DarkOwl’s vast database of darknet and deep web content from within their existing threat intelligence platforms.
This also offered the DarkOwl team the opportunity to see updated demos of our customers’ platforms and gain insight into how their users interact with our data. This feedback enables our collections teams to continue to gather data that is of critical interest to our customers’ users – and is unique to the darknet, such as the activity of certain ransomware gangs.
For nearly 20 years, the DoDIIS Worldwide Conference has served as the premier information technology conference to hear from distinguished speakers, collaborate with trusted partners, and experience ground-breaking technical solutions to support the warfighter. The conference is an immersive in-person event designed to bring together leading subject matter experts, decision makers, and stakeholders to collaborate and partner. Read more about DoDIIS Worldwide 2022 on their website.
DarkOwl looks forward to continuing their presence at DoDDIS. You can see what conferences we will be attending coming up and request time to chat with us.
In the early days of the internet, online communities and internet power users relied on web-based technologies like bulletin board systems (BBS), Usenet newsgroups, and internet relay chat (IRC) to communicate with each other near-real-time. Many of these technologies formed some of the earliest communications avenues for cyber criminals using the internet to hack networks and steal information. Even though many of these chat protocols persist and are still in use today by criminal communities, newer chat platforms, especially those that include privacy-enhanced features like end-to-end encryption or anonymity are preferred by many threat actors that collaborate across the dark web.
Many of the chat platforms and networks we will discuss today include channels and communities that are perfectly legitimate and even could be casually considered a form of ‘social media.’ Despite this, DarkOwl refers to chat platforms such as IRC, Telegram, and qTox that have considerable use by darknet cyber criminals as ‘darknet adjacent’ for their role in persisting illicit goods trade, fraudulent activities, and cybercrime.
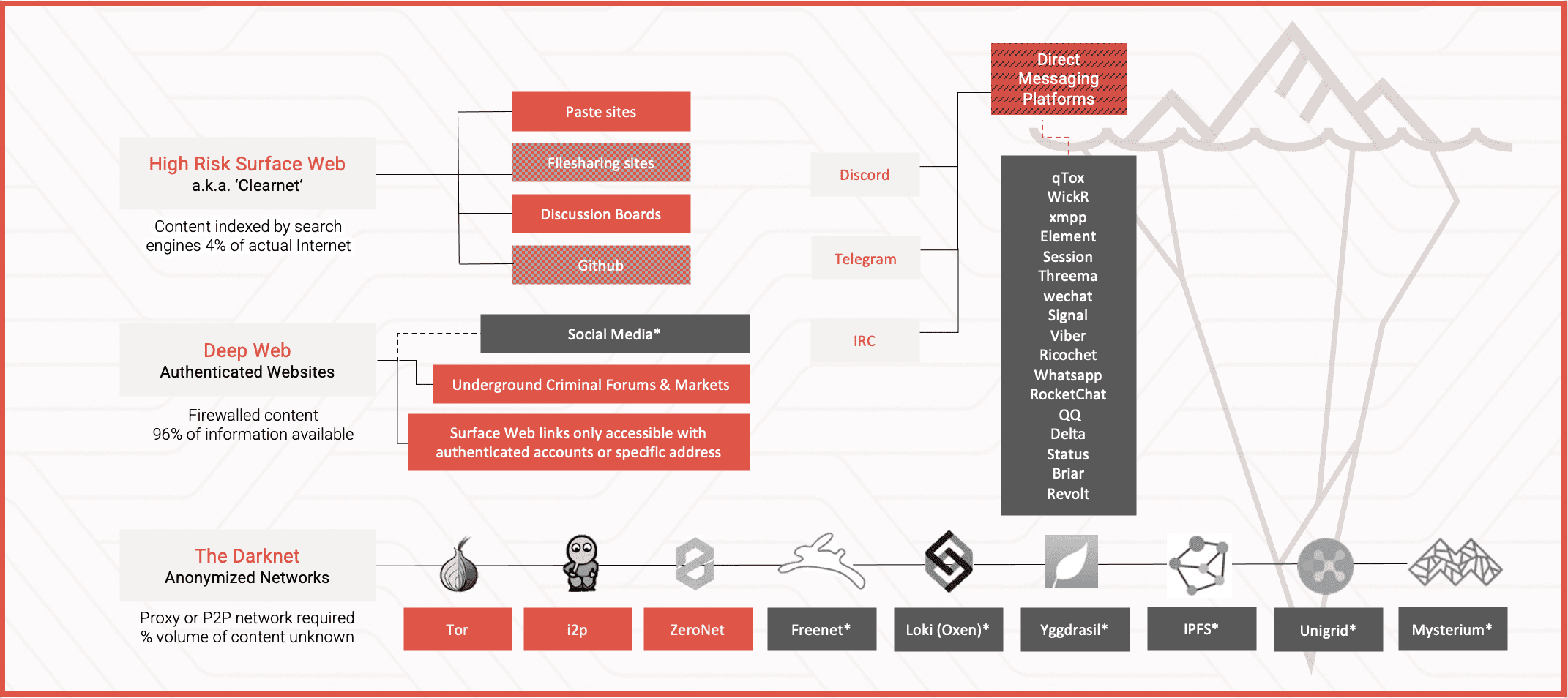
In the late 1980s, IRC was the protocol of choice for communicating real-time with others across the internet. Shortly after, AOL’s instant messenger and their associated chat rooms skyrocketed in popularity as widespread use of the internet spread around the US and abroad. IRC was codified in 1993 as RFC 1459 as an open-source networking protocol, and even though it was originally developed by the Finnish software developer, Jarkko Oikarinen, a.k.a “WiZ”, IRC does not belong to any specific person or group. As use of AOL’s platform diminished in the 2000s, IRC persisted in use, especially amongst technology-savvy and privacy conscious internet users. The size and volume of content distributed via IRC is unknown as there are hundreds of IRC servers and thousands of channels available to connect to at any given time. IRC severs with malicious conversations are often hosted on Tor. Many IRC clients like HexChat support traffic over SOCKS5 proxy for enhanced privacy and security. A virtual private network (VPN) is often recommended to provide additional security protection to IRC server nicks.
In 2013, the Russian-born French Emirati entrepreneur, Pavel Durov, launched Telegram messenger. Pavel had established his leadership in Russian-internet technologies, founding the Russian Facebook equivalent social media conglomerate, VKontakte (VK), six years before debuting Telegram. Pavel advocates for personal data privacy in its public advertising of Telegram, stating that selling user data is not a core feature of its software business model nor is user information shared with marketers, advertisers, or third parties — a stark contrast to similar services offered by Facebook’s (Meta’s) Whatsapp and Google Hangouts. Telegram also features a ‘secret chats’ option where all messages are end-to-end encrypted and impossible to screenshot by the chat participants on their device.
Most Telegram channels are public and open for any Telegram user to join. Others are only accessible by invitation. Channels are typically ‘read only’ with the channel owner posting most of the messages and content where Telegram groups allow participants of the groups to start the conversations more akin to a live chat format with dynamic activity from the members of the channel.
In recent years, Telegram channels promoting cybercrime and fraud have surged in volume and usage. The Ukraine-Russia military conflict increased popularity in Telegram considerably with thousands of channels – for both countries – sharing live updates from the battlefield and cyber targets for hacktivism and military cyber campaigns. Information operations campaigns have leveraged right-wing extremism Telegram channels for circulating anti-US and anti-NATO related dis[mis]-information since the war began.
Telegram has historically required a phone number, e.g. SIM or VoIP, to join the application as Telegram levied OTP and multi-factor authentication for the account security. In recent news, Telegram officially announced they would no longer require SIMs for account activation, but users could instead register using ‘blockchain-powered’ phone numbers sold for $16 USD per account by Fragment — another entrepreneurial endeavor by Durov. Conveniently, payments for the anonymous phone numbers are possible through Telegram’s own cryptocurrency token known as The Open Network(TON).
In addition to the no-SIM sign-up, there are several other features in Telegram’s latest release (V9.2) including Topics 2.0, custom emojis and a emoji search feature for iOS, temporary QR codes, and a global auto-delete timer for destroying chat messages for both users.
While Telegram was created with user’s privacy in mind, Discord was developed with the intent to facilitate open and fast Internet-based communication across online communities, content creators, and friends. Discord developers designed the platform with video gaming communities as its targeted userbase and the application has been publicly available since 2015. Since its growth in popularity, the application hosts servers and channels where private and public users are invited to talk openly about any topic imaginable; many Discord servers support voice and video communications as well. Such deanonymizing features of Discord are a serious red flag for serious darknet users tempted to use the Discord platform although many users suggest simply using a voice changer to obfuscate the sound of one’s voice.
In 2017, Discord allowed for publishers and developers to have their servers verified using social media or other verification methods to receive a Discord badge – like the Twitter blue checkmark – to designate them as official communities. Each server can host hundreds of channels that users utilize to instantly message or share files between channel members. In 2021, Discord launched a new feature called ‘Threads’ which are temporary text-only based channels that have an auto-destruction feature, like Signal’s self-destruct message feature. In late 2022, Discord debuted “Forum Channels” which mirror the format used across Tor or deep web criminal forums where discussions are organized by a topic with an original post and subsequent posts/comments on the original poster’s message are listed sequentially below in a thread like format. This feature was clearly designed to keep users on platform to facilitate the demand for highly structured, and organized discussions instead of freestyle chat.
Another privacy-first focused darknet adjacent chat platform is qTox. Also simply called “Tox” this chat platform is built by and for the users, meaning the source code is a free and open source (FOSS) project without any centralized servers or protocols that could be compromised. The platform forces perfect forward secrecy (PFS) as default – meaning a unique session key is generated with every chat. qTox also employs curve25519 for its key exchanges, xsalsa20 for symmetric encryption, and poly1305 for MACs.
Instead of registering with a phone number or an email address, qTox are assigned a unique 76-character Tox ID. The Tor onion routing protocol is used to store and locate Tox IDs increasing the security of linking users to their other OSINT personas or accounts. Deanonymization of Tox IDs and qTox users without using direct, advanced social engineering methods is impossible.qTox developers have recently formalized the TokTok project with Tox protocol documentation where they clearly state their mission – to promote universal freedom of expression and to preserve unrestricted information exchange – which in addition to the privacy-conscious nation state actors and cybercriminals also benefit from.
One of the most predominant social applications in China is WeChat, also known as Weixin (微信). WeChat is often confused with its sibling microblogging site, Sina Weibo which is also widely used across the country. Where Weibo features content for mass distribution and behaves more like a social media platform like Twitter, WeChat is designed as a ‘semi-closed’ platform facilitating more direct 1-1 communications and smaller group conversations, which is why it has increased in popularly across Mandarin-speaking cybercriminals. Similar to Discord, WeChat offers instant messaging, voice, and video calls over the internet. Open source information detailing the technical specifications of WeChat is limited since the platform is owned by Tencent and use of the application is restricted to users located in mainland China. The app is leveraged heavily by the Chinese government for digital surveillance of their citizens’ online behavior and the app’s user’s device data.
Both WeChat and Weibo are considered social media so any data collected from WeChat, should be targeted to those specifically linked or referenced by darknet forum and marketplace users.
Interested in reading more content like this? Stay tuned for Part 2 where we will dive into even more Darknet adjacent platforms. Sign up to our newsletter below to be the first to know when it goes live.
In this whitepaper, DarkOwl Analysts break down the various layers of the internet, from “regular” search engine-compatible websites to complex hidden networks.
This dark web data provider partnership will enhance Aditinet customers’ insight into to Supply Chain and Third-Party risk.
[Read this release on Webwire]
Denver-based dark web data provider, DarkOwl, and Italy-based cyber security services company, Aditinet Consulting SpA, are pleased to announce their formal strategic partnership. As part of their curated Cyber Security Posture Solutions, this agreement enables Aditinet’s clients to have access to DarkOwl’s near real-time collection of dark web data and make more-informed threat intelligence decisions.
Aditinet Consulting SpA supports private and public organizations to achieve their business goals through a variety of channels. These include cybersecurity resilience, risk-based consulting, identification and delivery of optimal solutions and fully managed security services, and testing of new solutions and integrations through laboratory and market audits. Aditinet plays an important role in the ongoing scouting of new and emerging cyber security technologies and implementation of in-house best practices at customer sites.
“We are extremely proud to include DarkOwl as one of Aditinet’s main technology data providers and partners,” says Marco Gornati, Sales Director of Aditinet. “Thanks to the important amount of information present in the dark web and analyzed by the DarkOwl platform, we are now able to significantly increase the quality of Supply-Chain Security Posture services that we offer to our customers.”
Aditinet Consulting’s SpA’s decision to invest in access to DarkOwl’s dark web data – which is known for its exclusive access to authenticated marketplaces and forums – is a response to an evolving cyber threat landscape. Cybersecurity incidents such as malware, ransomware, or insider threats can have massive economical and reputational damages. These incidents, which can often be the result of human error or exposure (such as credentials), impact not just the targeted company, but the entire ecosystem of all involved partners and suppliers.
“To maintain a full picture of their company’s cyber threat landscape, IT security teams need to have awareness of the risks facing not only themselves, but also their third-party vendors and other members of their organization’s supply chain,” said DarkOwl CEO Mark Turnage. “DarkOwl is proud to work with security services providers who recognize this and choose to add superior darknet offerings to their clientele.”
About Aditinet Consulting SpA
Aditinet Consulting SpA is an Italian company established in 2004, two major hubs in Milan & Rome and a Service center in Kosovo. Provider for the best blend of best-of-breed Solutions and Services, both pre & post sales, across all the systems lifecycle. Nationwide footprint among the major organizations in CyberSecurity, in mission critical enterprise Network and Data Center infrastructures, supporting new strategic Transformation initiatives.
Major Key Services are on: Technology Consultancy, Design of Systems architecture, Delivery in critical environments, Professional Services for migrations, Assessment (Network-Security), Troubleshooting. 24/7 Assistance Service and NOC/SOC Service. For more information, visit us at Azienda | Aditinet: networking, security, mobility e cloud
About DarkOwl
DarkOwl enables organizations to fully understand their security posture, detect potential breaches and violations of the law and mitigate them quickly. DarkOwl turns the dark web data into a tool for our customers, enabling them to quantify risk at scale in order to make decisions that increase business success. By delivering the most prolific, relevant and timely darknet data available, our products ensure that our customers can find the exact data they need. DarkOwl’s robust ecosystem of products turns the dark web into a powerful tool to identify risk at scale and drive better decision making. We offer a variety of options to access our data, please visit us at www.darkowl.com
As part of our continued effort to enhance our dark web data products with features geared towards analyst and threat intelligence teams, DarkOwl is excited to announce our newest product feature, Entity Explore. Launched in the form of a new dashboard within Vision UI, Entity Explore shows results for queries around tokenized objects with critical contextual information.
The dashboard also incorporates new features geared toward increasing analyst efficiency and functionality, enabling things such as ease of exporting and parsing of information to best lead users towards actionable intelligence.
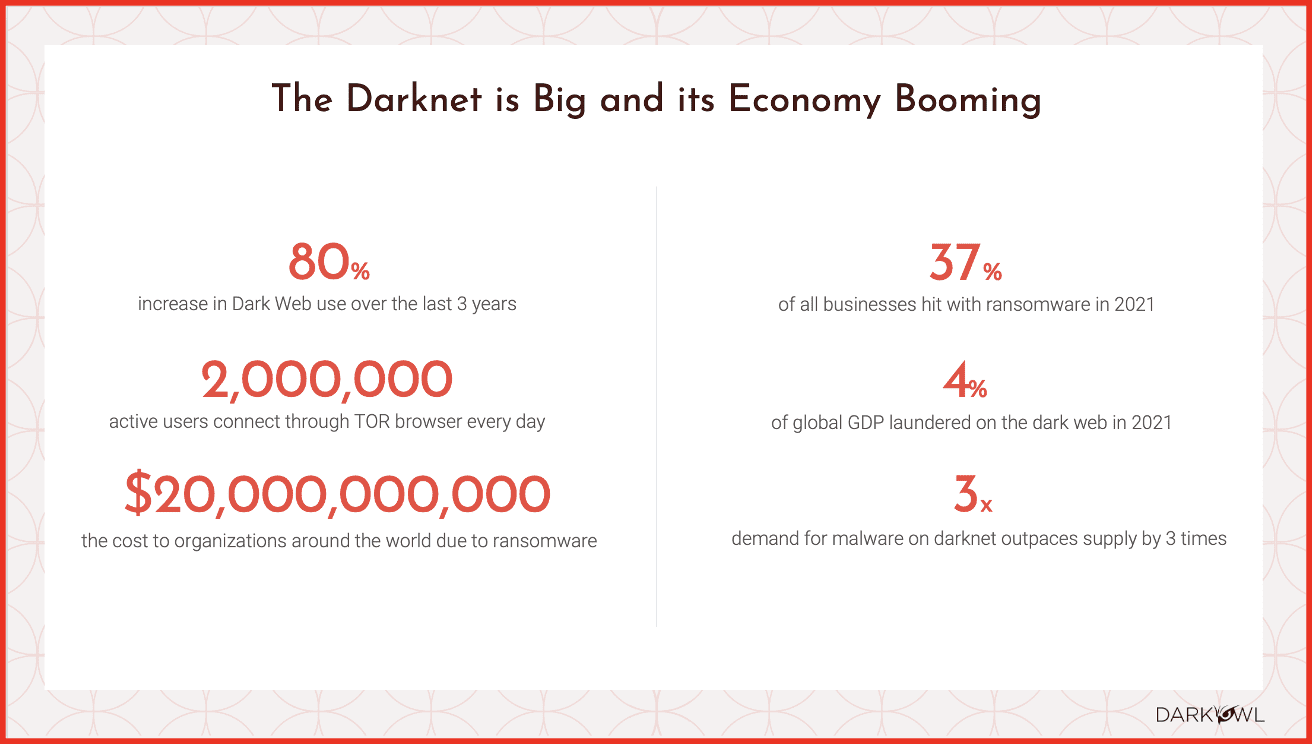
One of the most prevalent use cases for insight into the DarkOwl’s data is the recent persistent rise in ransomware activity, which largely presents itself on the dark web. In 2021, 37% of all business were hit with ransomware – the vast majority of which likely had their sensitive information leaked on underground forums. That same year, over 535M breached credentials associated with Fortune 1000 companies were reportedly circulated on the darknet.
Other recent reporting from Kaspersky maintains that the most common attack vector for all ransomware attacks continues to be via account takeover utilizing stolen or brute forced credentials. The launch of Entity Explore will empower threat intelligence teams with the tools to determine when such account information has been compromised, and take remediation steps accordingly.
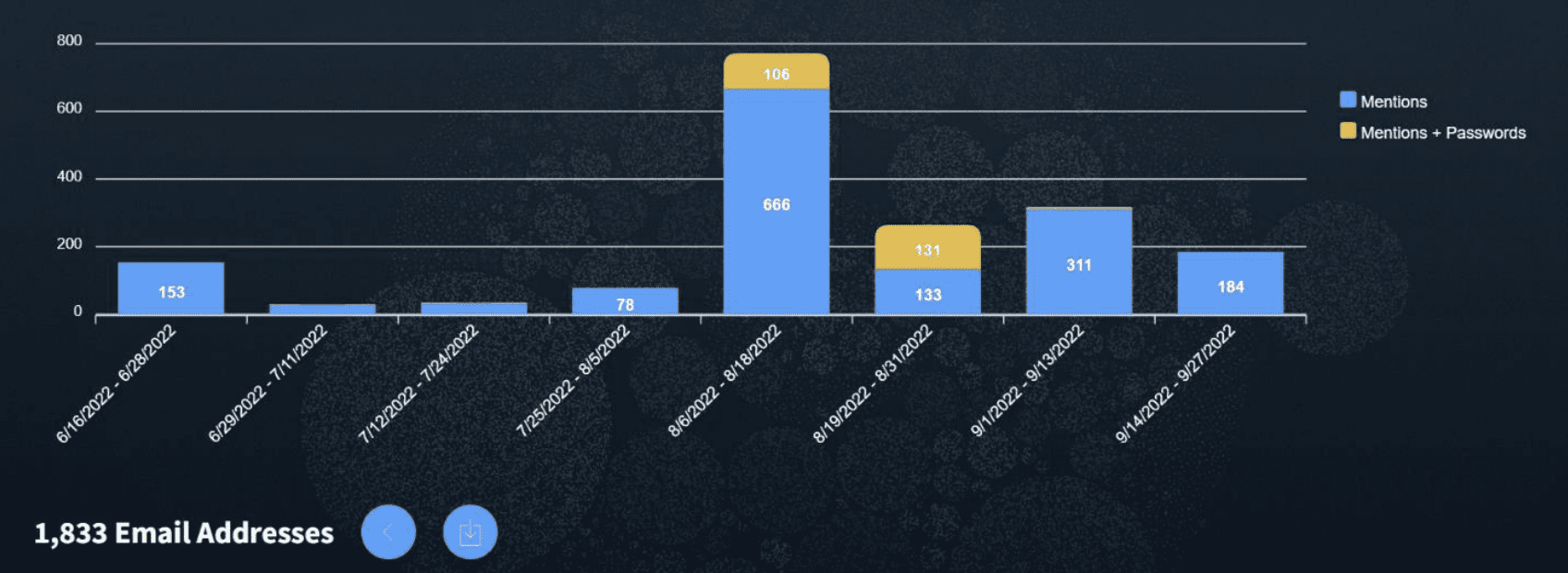
Entity Explore was developed as the result of feedback from DarkOwl’s clients, who were seeking an easier way to drill into the dark web exposure and easily export that information for reporting and further analysis. In particular, a number of DarkOwl customers indicated that knowing whether or not a password was identified in tandem with an exposed email address – and having that information returned in the format it appears in its original source – would add value to what they return to their customers.
With Entity Explore, users are now able to extract data from DarkOwl’s collection in a format that has mainly been limited to DarkOwl’s API Customers, such as:
Per DarkOwl’s CEO Mark Turnage, “Today’s cybersecurity analysts have the burden of juggling a growing number of potential threat vectors that could pose a risk to their organization. Entity Explore makes it simpler to assess what information has been exposed, and what remediation is required as a result.”
Like other functionalities based on DarkOwl’s Entities, users are able to explore information from the dark web regarding six distinct tokenized objects: Email Domain, Email Address, Credit Card, Bank Identification Number, IP Address, or Cryptocurrency.
Additional highlights from Entity Explore include:
As of early October, DarkOwl Entity API uncovered and archived over 9 billion emails, 16 billion credit card numbers, almost 2 billion IP addresses and over 390 million cryptocurrency addresses in the past year.
Ultimately, the DarkOwl product team understands that our end users need an overall situational awareness of their business’ and client’s dark web footprint. Now, by adding this new explorer feature, threat intel teams can better understand when immediate action needs to be taken on specific accounts, or when they need to triage and flag other related items of importance.
For those in charge of monitoring for critical information regarding their business or their customers, having access to DarkOwl data means access to near real-time data from exclusive dark web sources including authenticated forums and emerging chat networks. For more information about our data or data products, contact us today.
To round out Cybersecurity Awareness Month, we’ve gathered some of the hottest cybersecurity topics being discussed amongst actors on the darknet and deep web.
Cybersecurity awareness month has been enlightening for consumers and businesses alike. Many information security professionals and vendors have shared many guides this October on topics like multi-factor authentication, zero-trust, and other cyber resilience measures to hopefully help soften the impact of a significant corporate cybersecurity incident. The adage, ‘it’s not a matter of if you will be breached, but when…” might feel more and more realizable as the list of ransomware and corporate network attack victims continue to grow.
So, before the month’s end – in the spirit of spreading collective awareness – our analysts took a closer look some of the most popular cybersecurity threats and threat actor attack vectors discussed on the darknet.
There’s no question that ransomware continues to be one of the most popular threats utilized against commercial organizations, especially small and medium sized businesses that lack the enterprise-level information security budgets. Threat actors are increasingly interested in exploiting Linux-based systems and servers, and, lately, DarkOwl analysts have directly witnessed an increase in technical conversations related to the subject. Lockbit was one of the first ransomware strains to specifically target virtual Linux-based VMware ESXi servers, encrypting the vCenter infrastructure and virtual machines (VMs). Other ransomware gangs like BlackBasta have followed suit using SSH vulnerabilities and compromised credentials to deliver the ransomware to the server.
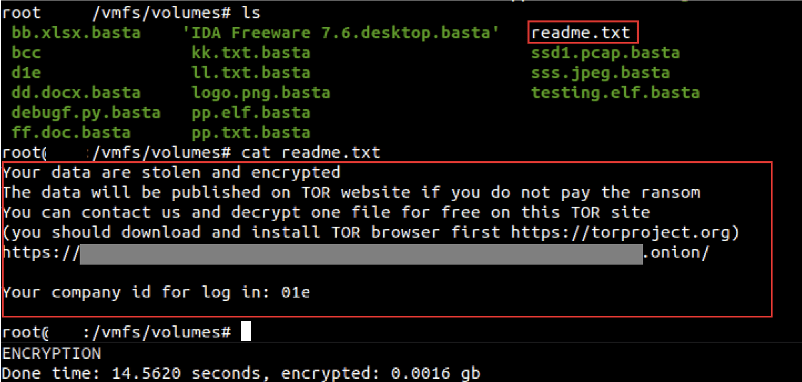
While many corporations run Windows or Mac client machines, Linux servers are the predominant server of choice for backend operations in enterprise commercial systems, hosting critical intellectual property and sensitive data. The type of data available in a ransomware campaign involving Linux servers attracts ransomware groups for the higher probability of ransom payment and the potential exploitation of sensitive information for cyber espionage.
Phishing is still a widely utilized and prominent attack vector discussed on the darknet for gaining unauthorized access corporate networks. Threat actors discuss phishing methods, offer “MASTERCLASSES” on the subject for sale in decentralized marketplaces, and regularly advertise phishing email templates for major commercial entities like Google, Apple, and Microsoft.
Some commonly discussed phishing methods are designed to target corporations’ social media accounts held by marketing departments. Others intentionally leverage social media relationships like employees’ LinkedIn connections to trick the victim into clicking on a document shared by a ‘friend.’
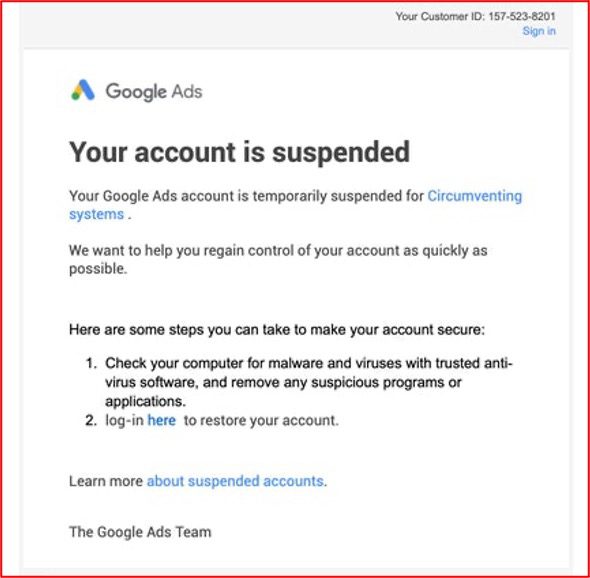
In the example below, threat actors directly leverage Google ADSENSE Adwords for serving up phishing URLs. These are deployed to unsuspecting victims who inadvertently select the malicious URL because it appears at the top of their search.
These elaborate phishing campaigns frequently result in successful corporate email compromise and occur daily. What’s more, they are getting increasingly sophisticated with targeted spear-phishing methods employed.
Phishing via SMS, (a.k.a smishing) has increased in popularity.
One example of a successful smishing campaign we’ve seen discussed on the darknet has been a fake emergency ‘smishing’ text from executives sent to employees in the organization, designed to not only confirm the phone number of the employee, but potentially drop malware via a follow-up malicious link.
DarkOwl IT provided the example to the right, which depicts an attempted smish of a DarkOwl employee using an executive’s identity.
Like the Linux server ransomware strains, darknet threat actors active seek server-specific vulnerabilities for potential exploitation and server data compromise. DarkOwl analysts have lost count of the number of Microsoft Exchange-related compromised organizational data leaks that surfaced by hacktivists participating in the Ukraine-Russia cyberwar. Over a dozen exchange vulnerabilities added to the NVD in 2022 and even more in 2021, provide threat actors plenty of opportunity for remote code execution (RCE), privilege escalation, file read-write access and arbitrary file deletion on a compromised Exchange server.
Most of the RCE vulnerabilities include malware delivery via PowerShell. Microsoft security advisories strongly suggest that Exchange Server customers disable remote PowerShell access for non-administrative privileged users in their organizations.
While ProxyNotShell is getting lots of recent attention, some of the Exchange vulnerabilities DarkOwl has captured discussed do not always require authentication to execute malicious code. Proof of concept code is also often referenced on darknet discussion forums and Telegram channels, making the vulnerabilities even easier for less adept cybercriminals.
Several of the large database leaks observed by DarkOwl because of a successful Exchange server attack are dumps of every email and attachment from every inbox on the compromised on-prem server. These vulnerabilities do not apply to Microsoft Online or Microsoft 365 cloud mail services.
Another server vulnerability that is being discussed in darknet discussion forums is a remote code execution vulnerability that affects Confluence Server and Data Center (described as CVE-2022-26134 by the NVD).
As of this summer, the vulnerability has reportedly been patched by Atlassian with the release of versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1; however, the vulnerability is still explored by cyber criminals.
In fact, multiple threat actors – with varying motivations and intentions – have expressed specific interest in Confluence-related security vulnerabilities. Another, tagged 26138, involved a hardcoded password for the user account, disabledsystemuser. Threat actors believed to be likely associated with nation state actors and users with specialties in cryptomining have indicated this vulnerability allows for production environments to be compromised, new administrator accounts created, and malicious access to corporate networks granted.The ransomware gang, AvosLocker targeted vulnerable Confluence servers with their command and control at scale earlier this summer.
DarkOwl is an open-source intelligence (OSINT) platform that aggregates information from various underground sources. Monitor for information critical to your organization, clients, and customers to discern actionable and meaningful intelligence from things like cyber breaches and ransomware attacks.