What Black Hat MEA Told Us About Threat Intelligence
December 17, 2024
DarkOwl was delighted to attend the Black Hat Middle East & Africa (Black Hat MEA) conference in November. As the region’s tactical and strategic threat intelligence demands continue to grow rapidly, we take a close look at the reasons behind the sector’s buoyancy and what the success of the conference means for the Gulf’s cyber sector.
Lindsay Whyte, Regional Director and Richard Hancock, Darknet Intelligence Analyst represented the DarkOwl team. Black Hat MEA, describes themselves as a leading cybersecurity conference and exhibition held in Riyadh, KSA. The event brings together cybersecurity professionals, cutting-edge technologies, solution providers, and decision-makers from around the world, condensing several months of networking into just three days.

Background
Saudi Arabia is investing heavily in its cybersecurity industry as part of economic diversification and the Vision 2030 initiative. The Kingdom is funding the cybersecurity sector through several key approaches:
- Government spending: The Saudi government allocated 2.3 billion Saudi Riyals (SAR) ($600 million) to cybersecurity in 2023
- Market growth: The cybersecurity market in Saudi Arabia is valued at 13.3 billion ($3.5 billion) SAR. The cybersecurity sector’s total contribution to Saudi Arabia’s GDP is estimated to represent 0.81% of non-oil GDPin 2024.
- Strategic collaborations: The National Cybersecurity Authority (NCA) is stimulating the market by encouraging innovation and supporting technology transfer.
- Cloud security investment: 60% of Saudi enterprises are planning to increase their cloud security budget by an average of 35% in the next year.
Increased funding in the country fosters a robust cybersecurity ecosystem, attract both local and international investments, and position Saudi Arabia as a leader in the global cybersecurity field. No wonder a Black Hat conference one hour drive into the desert attracted 10,000s of visitors!
Theme: Collaboration
Collaboration around tactical threat intelligence was a major theme at Black Hat MEA.
This was encapsulated by Brett Winterford from Okta, who remarked that OpenID’s Shared Signals Framework is an encouraging step towards inter-organisational data sharing. The Shared Signal Framework (SSF) provides a secure and privacy-preserving way for organisations to share information via events. It uses a standard format for representing these events and a secure transport mechanism for sharing them. This makes it easy for organisations to integrate SSF into their existing security infrastructure and to share signals with a wide range of partners.
Likewise, Ben Collier from Google Cloud spoke of the ‘Sectoral SOC’ model – and SOC of SOCs sitting directly above numerous sub-SOCs (be they in the same umbrella organisation, or not) responsible for threat actor analysis, EDR and creating guidance and recommendations to regulators as a single face.
Theme: AI
When trends towards centrally managed intelligence (as outlined above) combines with growing cloud adoption, the opportunities for effective AI use cases become apparent.
Jennifer Ewbank, former Deputy Director of Innovation at the CIA, talked to the benefits of AI, and the possibility of AGI (‘Artificial General Intelligence’ in which machines develop near-consciousness). Kevin Jones, CISO at Bayer, spoke to the benefits of ‘SecLM’ and applying AI to data, provided robust data security, as a critical condition to seeing tangible benefits at scale.
Theme: Threat Actors
A central theme of Marina Fulwood’s presentation (in capacity of Head of Threat Intelligence at Unilever), was the need for proactive threat intelligence. Especially in an age of industry- and country- level exposures to Nation State actors, Ransomware groups and financially motivated Initial Access Brokers (IABs).
As clearly illustrated by the exhibition hall at Blackhat MEA, the threat intelligence market in the Middle East is growing rapidly.
The region has seen a significant rise in targeted cyber-attacks, particularly against critical infrastructure such as oil and gas industries. The average cost per data breach in the Middle East is $8.07 million, second only to the USA globally. Ongoing conflicts and rivalries in the region have led to an increase in state-sponsored cyber threats, additionally.
The Evolving Darknet
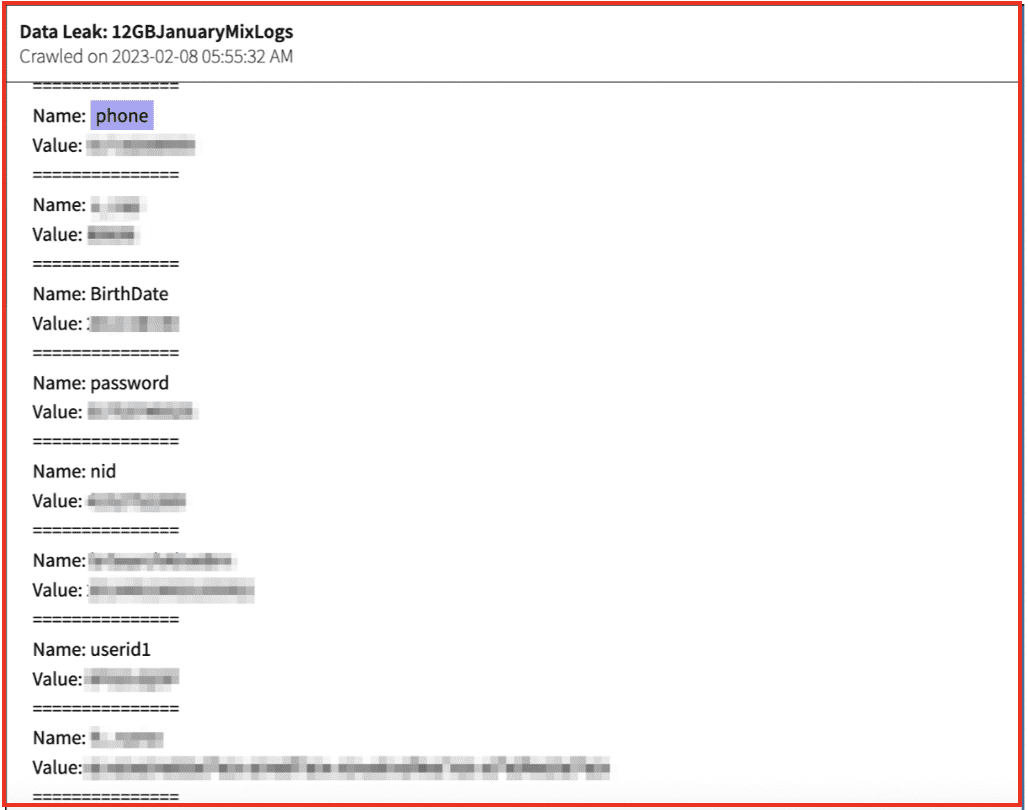
With unification and centralisation comes demands for Dark Web monitoring. Dark Web data is crucial for Security Operations Centers (SOCs):
- Early threat detection: Dark Web intelligence allows SOCs to identify potential risks and data breaches sooner, enabling faster mitigation of threats.
- By monitoring Dark Web activities, SOCs gain valuable insights into emerging threats, cybercriminal strategies, and tactics, techniques, and procedures (TTPs) employed by threat actors.
- Access to Dark Web data helps SOCs understand the scope of cyber threats affecting their organization, leading to more effective incident response (IR) strategies.
- General risk mitigation: By providing ‘atmospheric’ early warnings, SOCs extend the value of the investment to x-functional teams like StratComms, PR and the C-Suite.
Innovation Cuts Both Ways
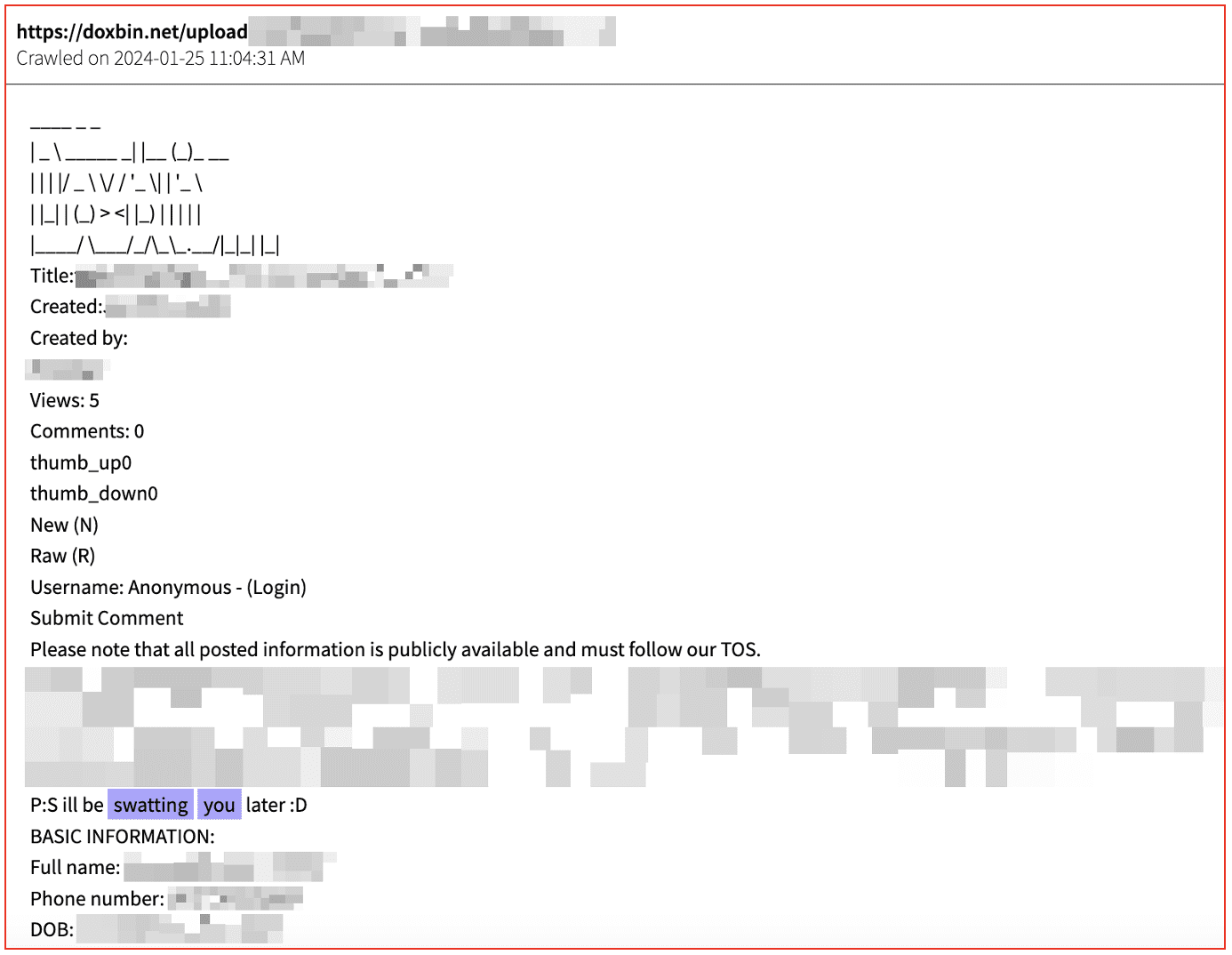
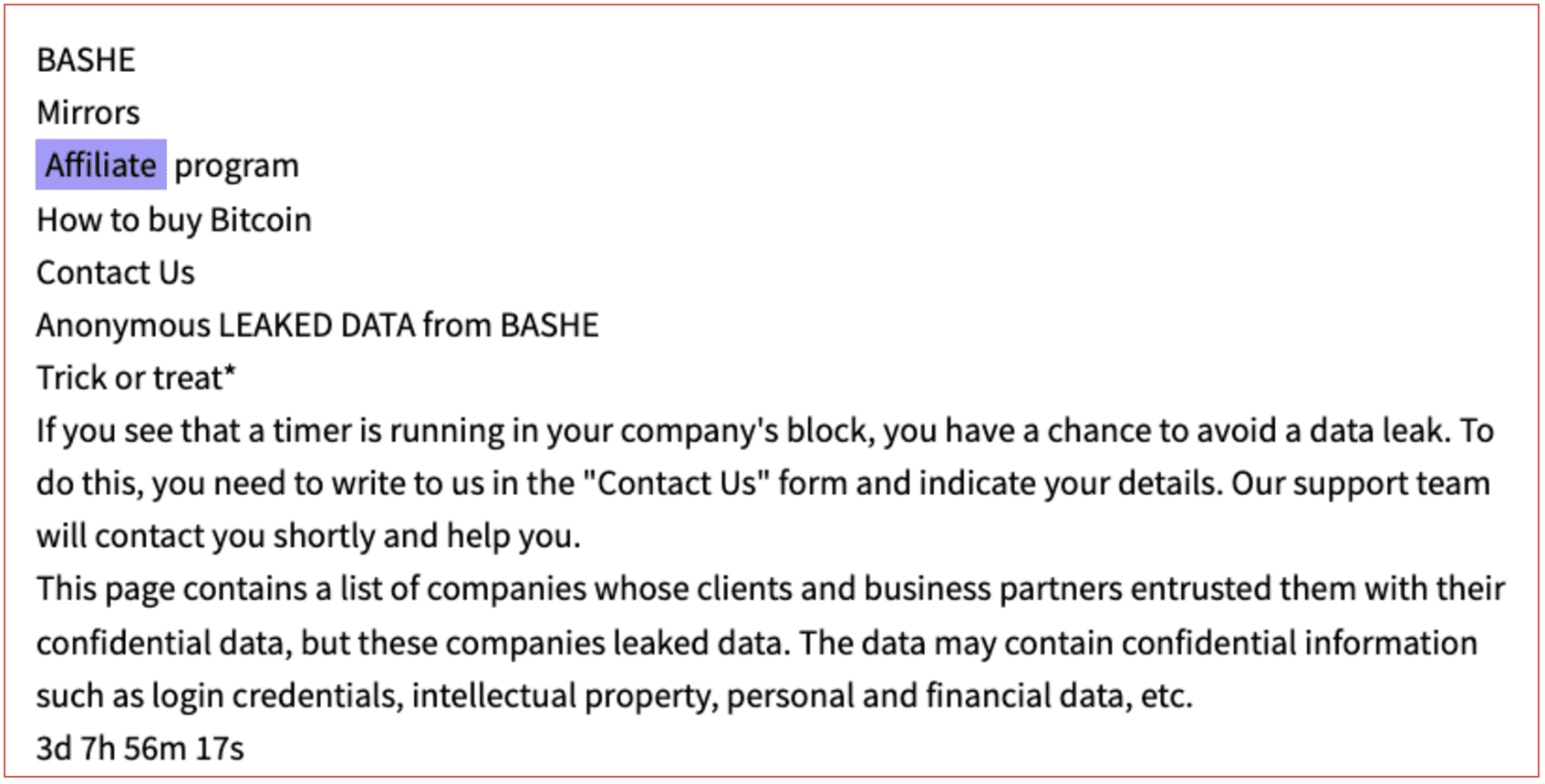
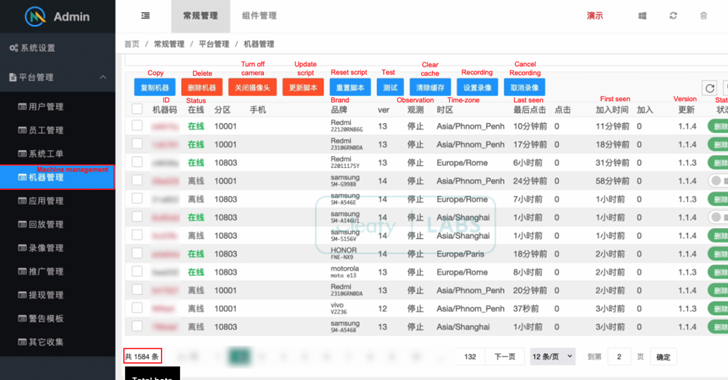
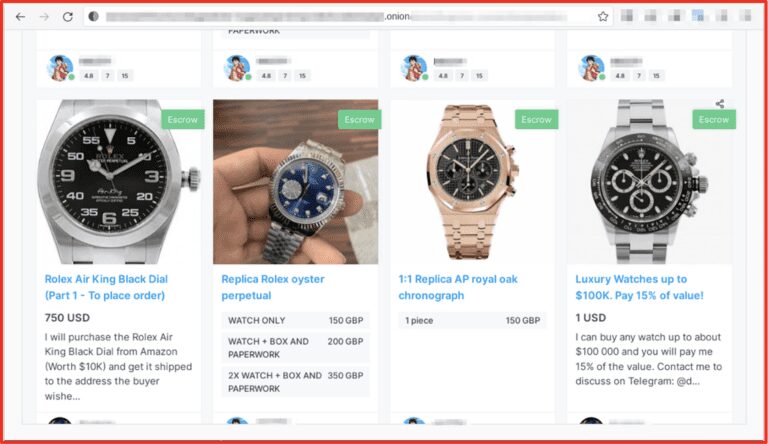
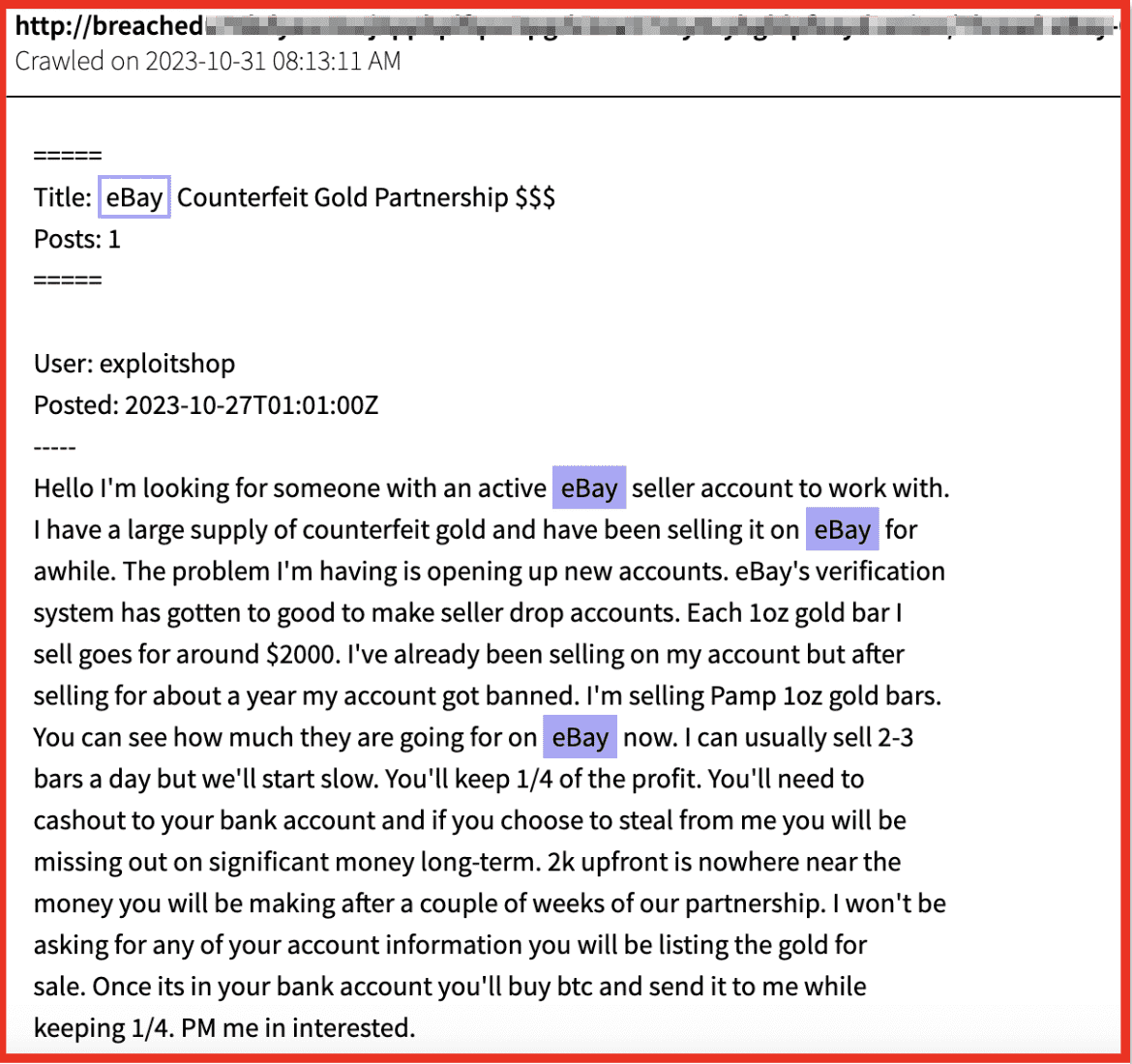
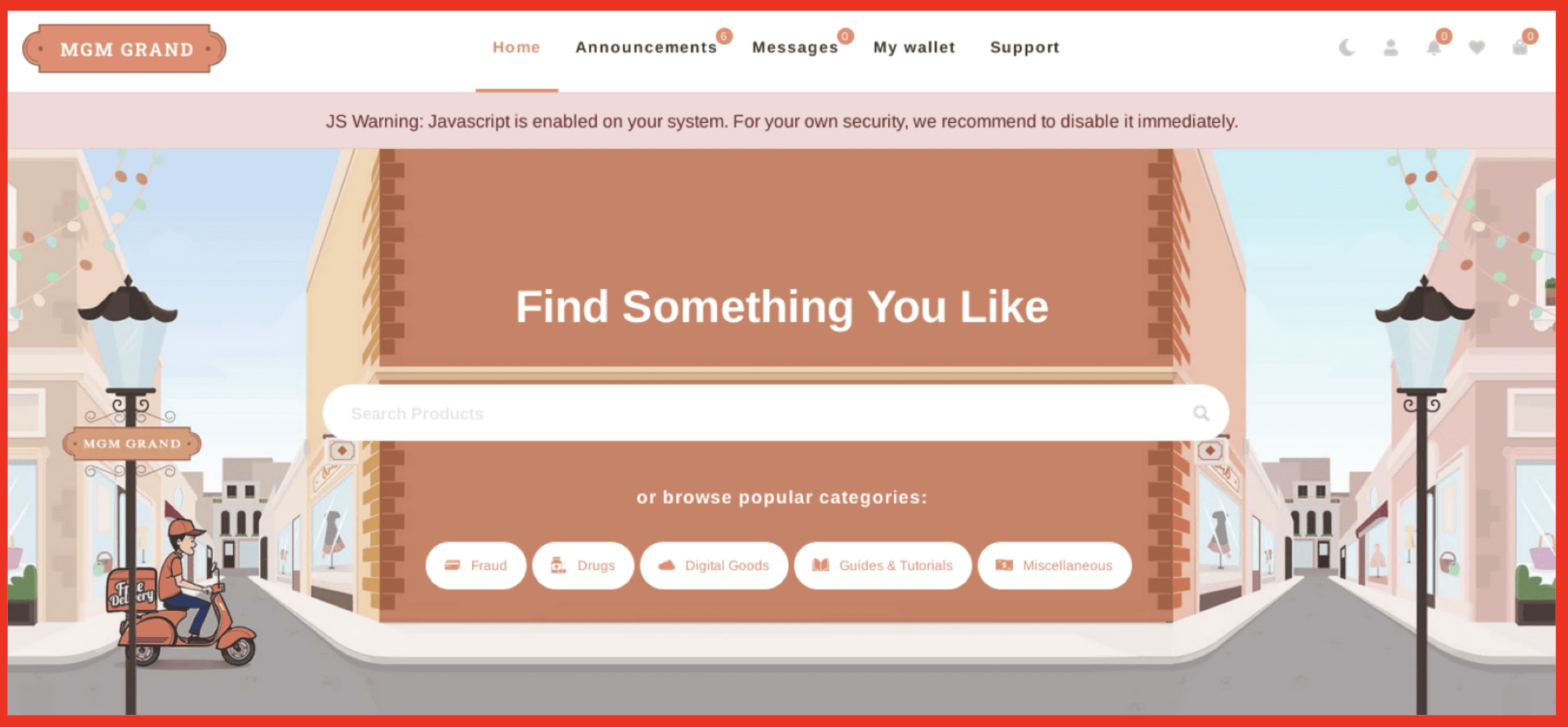
Just as organisations increase their visibility over OSINT sources and dark web marketplaces as part of a maturing Threat Intelligence adoption, so too do threat actors constantly evolve their behaviour to keep private (below).

As Threat Intelligence experts like DarkOwl index new sources of threat actor chatter, so must these actors find new ways to communicate and advertise with the widest possible reach.
With Saudi Arabia’s 2022 Financial Sector Cyber Threat Intelligence Principles containing specific reference to Dark Web monitoring (Principle 5), we anticipate growth in Darknet intelligence and demands in a region growing in geopolitical and economic significance.
See you at BlackHat MEA in 2025!